Problem-game method of motivating a student of the specialty "Information Security"
The first article already mentioned the problem of lack of motivation among students. About trying to deal with them and will be discussed further.
Presence of a problem
I recall the main problems associated with the lack of motivation of students in the field of information security:
- the lack of a meaningful connection between general disciplines (first of all, mathematics for technical specialties) and special ones, due to the difficulty of coordinating topics between departments and the maximum unification of courses for the maximum number of specialties taught at the university;
- lack of motivation to study (I came across the following students' motivation: “retract from the army”, “find a husband”, “what you have enough money for”);
- lack of motivation from teachers to teach those who do not want to learn.
The fact that this problem is systemic, recognized at the state level, is also indicated by the presence of relevant sections in the “Main areas of research in the field of information security of the Russian Federation” of the Security Council of the Russian Federation.
')
List of directions
3. Problems of staffing information security of the Russian Federation.
3.1. General methodological problems of staffing information security and development of the content of vocational education in this area.
3.1.3. Methodological problems of using modern information technologies for training specialists in the field of information security.
3.1.4. Problems of scientific and educational support of the system of continuous training in the field of information security.
3.2.1. Problems of organizational support of the training system in the field of information security.
3.3. Problems of technological support training in the field of information security.
3.3.1. Problems of improving technology and teaching and methodological support of the process of training in the field of information security.
3.3.2. Problems of technical and software use of modern information technologies in the educational process.
3.1. General methodological problems of staffing information security and development of the content of vocational education in this area.
3.1.3. Methodological problems of using modern information technologies for training specialists in the field of information security.
3.1.4. Problems of scientific and educational support of the system of continuous training in the field of information security.
3.2.1. Problems of organizational support of the training system in the field of information security.
3.3. Problems of technological support training in the field of information security.
3.3.1. Problems of improving technology and teaching and methodological support of the process of training in the field of information security.
3.3.2. Problems of technical and software use of modern information technologies in the educational process.
Formulation of the problem
Ideally, to solve these problems, it is necessary to create a motivation system that includes state policy, the education system, patriotic education and, most importantly, serious financing of all these issues. It is along this path, and for the sake of the money mentioned, those who speak on television, at various meetings and public councils.
We (with one of the teachers of the department) tried to solve this problem on our own and with minimal time and financial costs. Naturally, in the conditions of a separate study group, in a single period of time, without the above training and environment, and even 4-5 year students, who have already been thoroughly demotivated by the ideological and educational vacuum around them, it seems that it is already impossible to interest students in the topic information security, to make it interesting to them, they wanted to learn and learn.
By joint efforts, it seems to us, we managed to solve the task set, we managed to find a form of conducting classes, which prompted further study of both special and general disciplines.
Refusal to consider all pedagogical (didactic) methods and technologies
In the process of selecting an educational (didactic) technology, a huge amount of relevant literature was reviewed. In addition, this consideration itself, as a matter of fact, began long before the problem arose and lasted, perhaps, a couple of years (at least).
In this article, the process of studying, selecting, and actually choosing didactic technologies will not be considered, nor will they be reviewed. The situation with the synthesis of this topic is a separate serious problem and a separate article on the development of the methodological segment of the educational program on information security will be devoted to this.
An approach
As a pedagogical device, a set of play, role and problematic didactic technologies was selected, which can act as a motivating factor in teaching information security in the existing environmental “environment” conditions. The discipline on which it was planned to work out the technique - “IS management in the organization”. It was necessary to develop a model of some level of abstraction, which would:
- was interesting as a game;
- a team about the size of a study group could take part in it;
- the duration of the game should not exceed the duration of the training pair (or better, half of it),
- informative and educational content of the game must comply with existing regulations on information security;
- the lesson should be as visualized as possible, on the one hand, to use the most developed information receiving systems for students, and on the other hand, to highlight the issue in the most comprehensive and complex way.
At the same time, our programming skills are almost zero, the order is impossible - due to the lack of funding for such experimental activities (or difficult and time-consuming under the conditions of our grant system).
As tools were available: a computer with standard office software and a projector.
Prototypes
Life has already taught that before inventing a bicycle, it is worth looking around, looking for a ready-made solution. There are about 2 dozen computer games that immerse the player in the world of information security on the market. Standing ( Overview ) attention - 2-3. In addition, computer, there is also real quests ( Cicada 3301: secret hacker community or just a game? ), Card games ( Card game "Outsourcer" or "Loka. Interrupted sysadmin sleep" ) and other forms of games.
There are two more games ( Plague Inc. and Bio Inc. ) that are interesting from the point of view of building the gameplay - “attack-defense”, and which prompted the principle of creating the described motivation technique.
Unfortunately, all these games (omitting the copyright issues, their availability on the Internet, the impossibility of their purchase due to their relative "old age" or the complexity and duration of procurement by a state organization) are focused on the individual player; be used in face-to-face classes, although it is highly desirable as a “homework” or “mandatory reading / viewing” element of the educational process.
Igrodel (informative modeling)
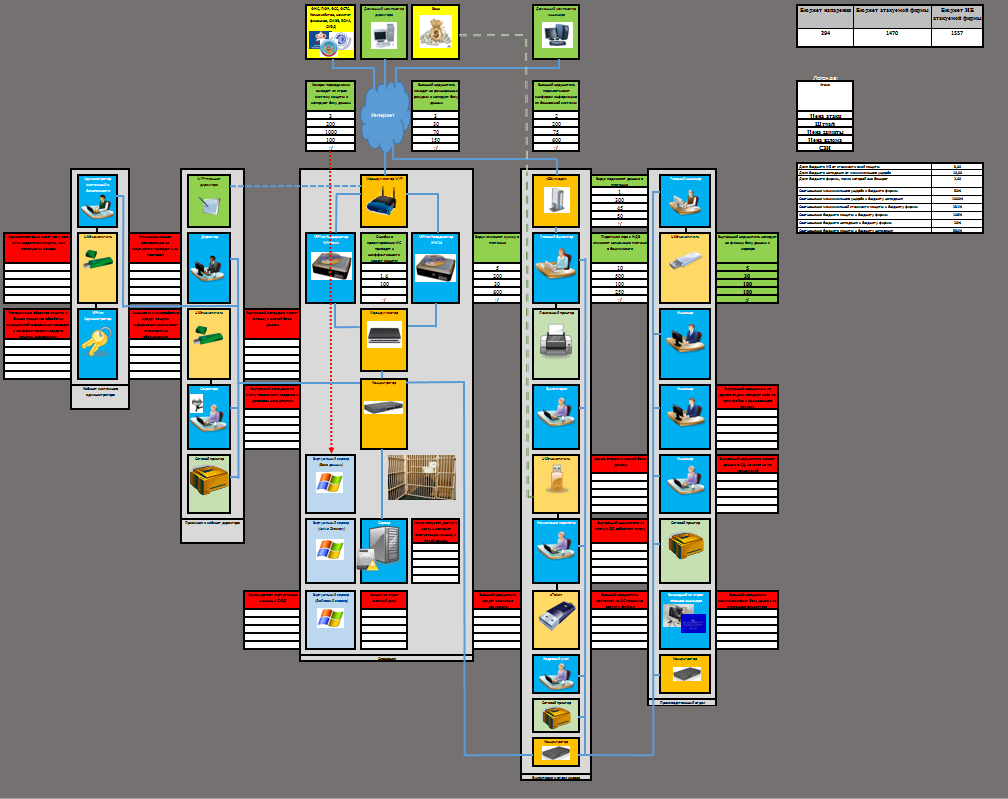
MS Excel was chosen as a modeling tool, a small organization's information system (~ 9 workstations and 1 server with virtual machines) was chosen as a modeling object, threats were modeled, information protection systems were built and managed under financial constraints as an object of research. For maximum compatibility and use on machines with limited rights, it was decided not to use scripts, everything should be modeled using Excel’s standard capabilities (some of the rules and restrictions in the Game are associated with this, for example, reducing or increasing the cost of attacks or GIS are recalculated even by attacks and defenses, but since "the world is not perfect", these restrictions are explained as "the inevitable physical laws of the game world").
The idea of the game was as follows: an attack is carried out on the organization’s information systems (ordered by a third party allocating a budget for the attack, specified as part of future profits), the IS service blocks the existing threats by acquiring various information protection tools. Both sides have their own budget, the attacker's goal is to “destroy” the organization, the goal of the defenders is to prevent this. The organization has a budget, the theft of which “bankrupt” it. The game goes on until the parties exhaust their budgets, or until the organization is “ruined”.
As the source data were selected:
- FSTEC 's normative document “The Basic Model of Personal Data Security Threats when Processing the Information Systems of Personal Data (extract)” ;
- the NSD threat formula from page 16 of the specified document (unauthorized access threat: = <source of threat>, <software or hardware vulnerability>, <threat realization method>, <target object>, <unauthorized access>);
- a part of the elements from Figure 3 “Elements of the description of threats to unauthorized access to information in the ISPD” on page 22 of the specified document;
Threat Description Items

- Appendix No. 2 to the “Requirements for the Protection of Information Not Constituting a State Secrecy Contained in State Information Systems” , approved by order 17 of the FSTEC.
I will make a reservation that not everything that was planned was implemented and brought to the end, for example, it was stipulated that students should collect information about the cost of information protection tools themselves, assess the damage caused and the “cost” of the attack. This is partially implemented on the first page of the game.
A few more assumptions:
- All SZIs are “independent” and neutralize only one threat;
- added an imaginary “Next-Generation unauthorized access system”, by analogy with the Next-Generation Firewall, which is a mounted GIS from an unauthorized access system of the level of applications or services;
- the number of vulnerabilities and threats accordingly reduced to save time.
Selection of examples of GIS was carried out from the register of certified FSTEC and FSB GIS.
Interface description
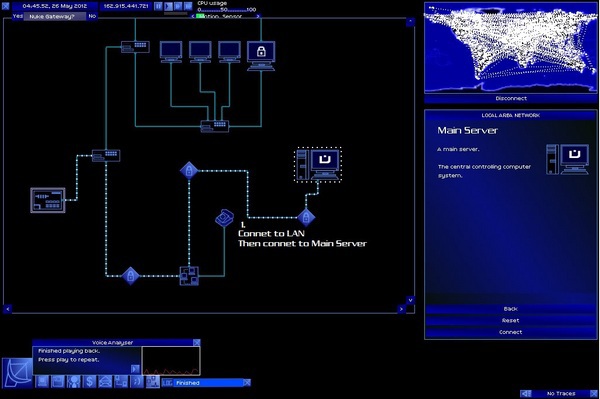
The game ( Zip-archive with the Game ) begins with an acquaintance with the organization's information systems, existing vulnerabilities, possible threats, methods of their implementation and information protection tools.
It also provides information on available budgets and some analytical information.
On the second tab of the Game, types of SZI, examples of real SZI, “measures” under the 17th order of the FSTEC, objects of attack, threats, methods of their implementation and various costs of attacks and defense are given.
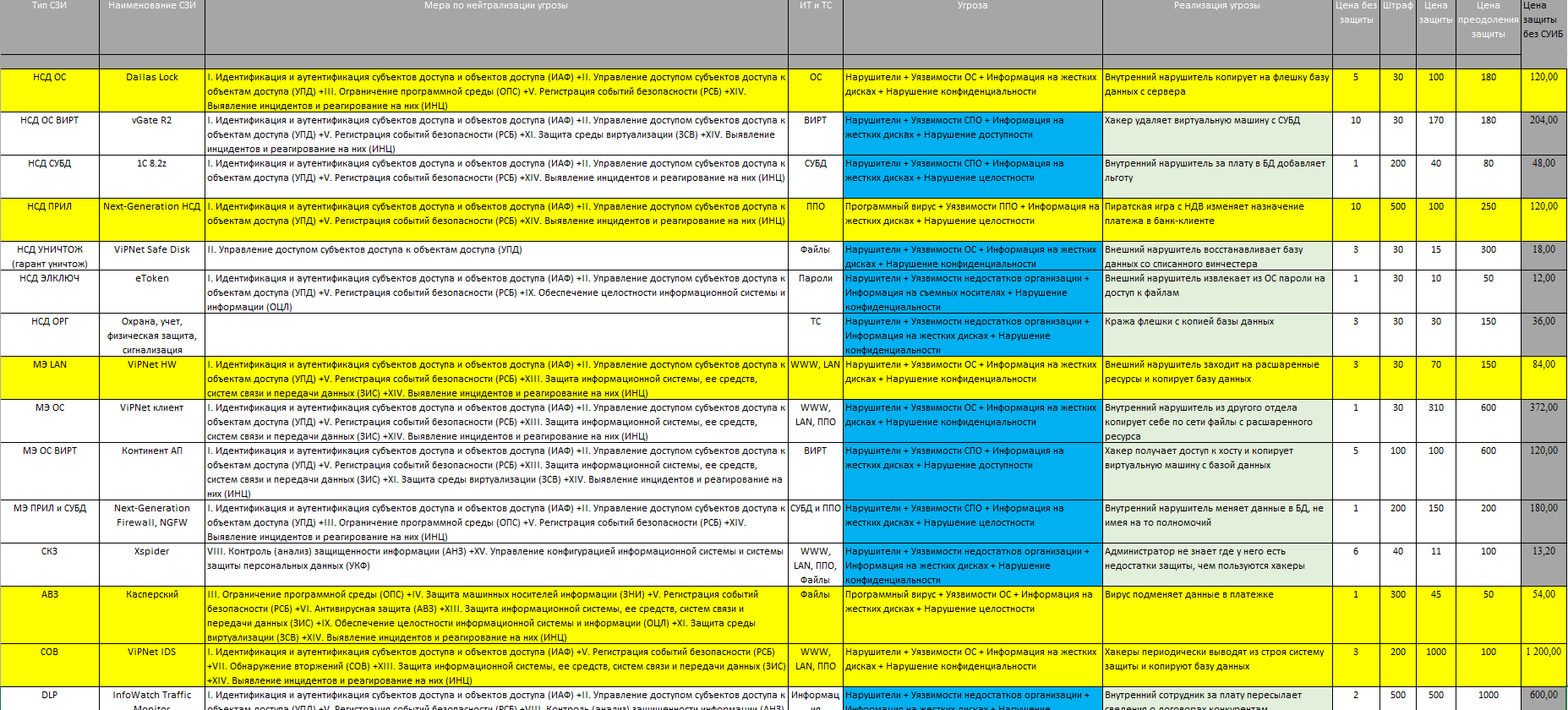
The third tab presents the information security service interface. The “purchase” of a GIS is carried out by answering the question in the appropriate line. The "Budget Information" column shows the remaining budget. The column “Damage to the company ...” shows the organization’s remaining budget after the theft.
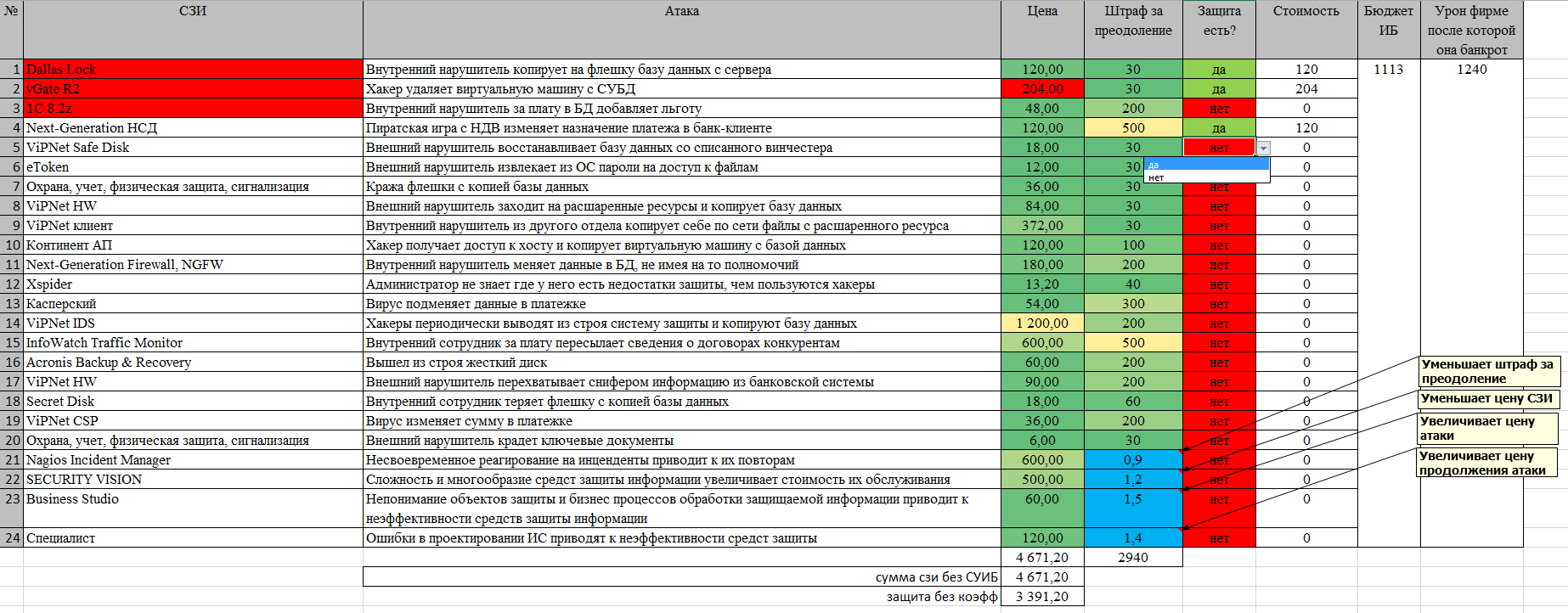
The fourth tab presents the interface "hacker". He has the opportunity to realize the threat, and in case of failure to spend a significant budget and "hack" protection. Continuing an attack in the event of a primary success does not make sense, does not increase damage, and senselessly increases the cost of an attack. In case of successful realization of a threat or hacking protection, the corresponding damage value appears in the “Fine Protection” column, the damage amount increases and the corresponding budgets decrease.
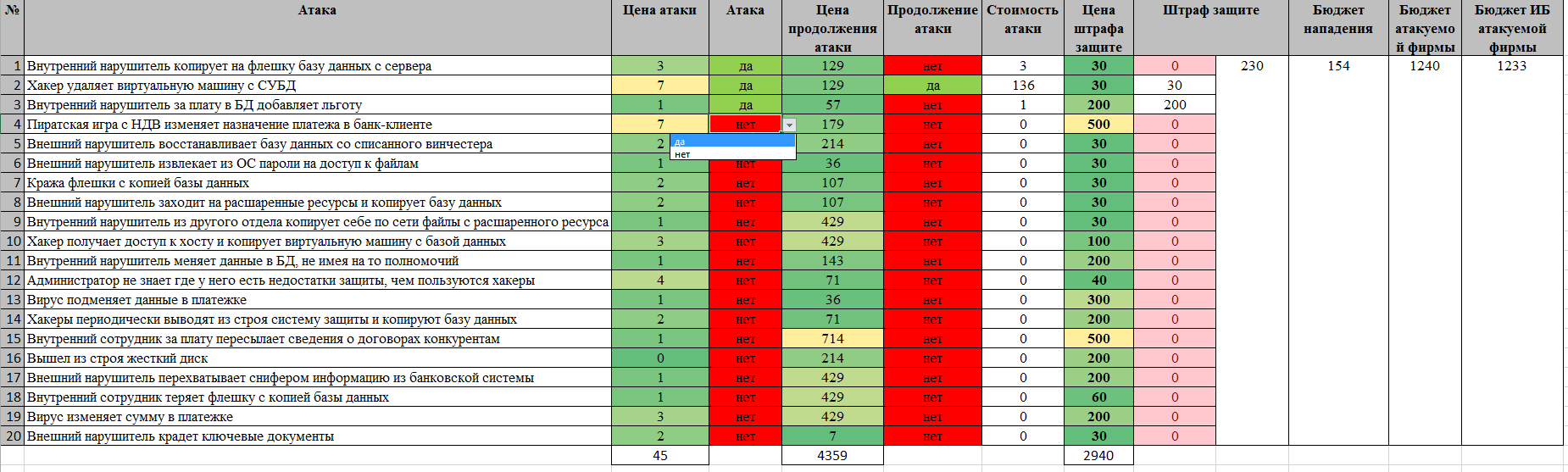
For ease of sorting, all prices are highlighted from yellow to green downwards.
The interface for each player in general corresponds to the available real information for each of the roles.
All prices quoted are based on various reports and reports on real hacks, my expert evaluation and real retail GIS prices (with some generalizations and divided by 1000). I note that these figures were not selected and not corrected - after they were entered into the Game, only the ratios of the allocated budgets were corrected.
Examples of losses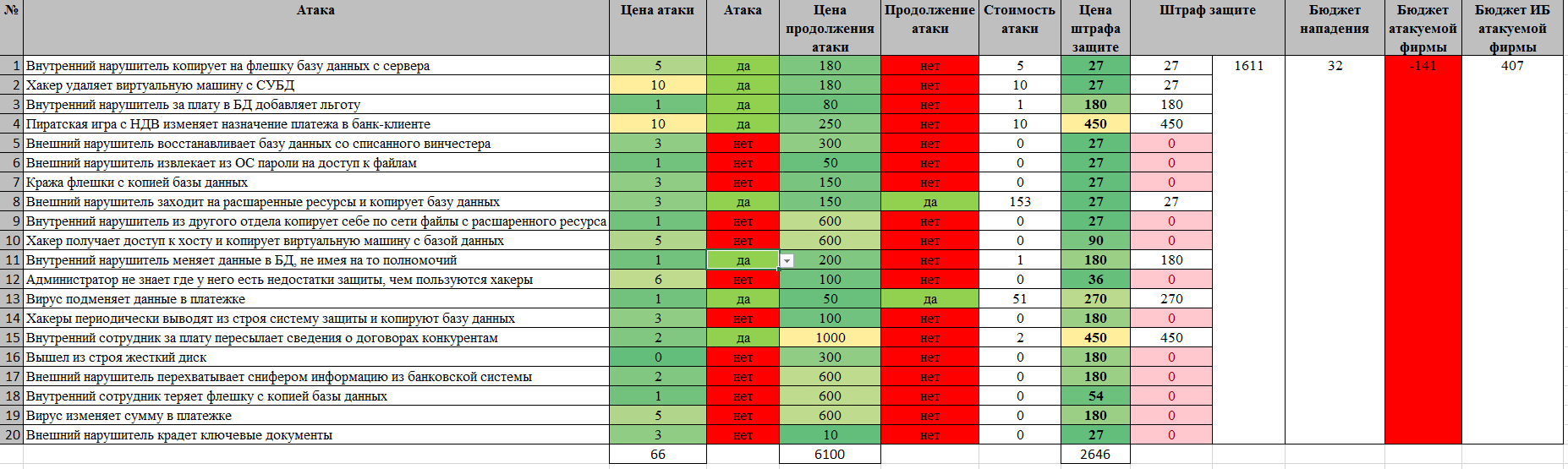
This is how the organization loses.
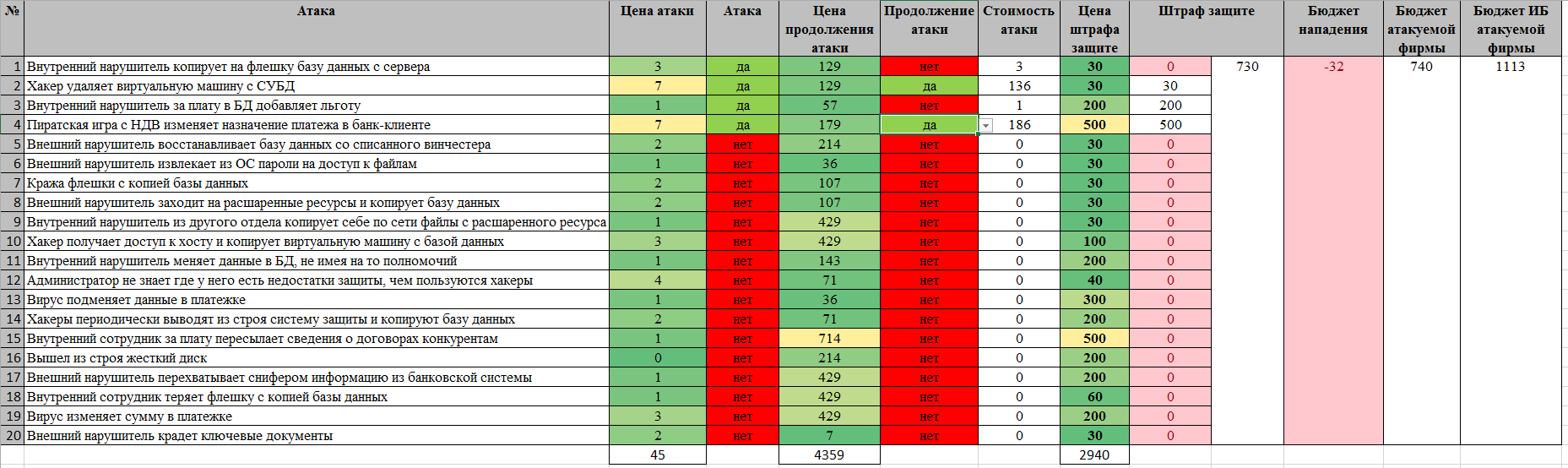
It looks like losing a striker.

This is how the organization loses.

It looks like losing a striker.
Game rules and options
There were 2 options for the game:
- the defenders acquire all SZI within their budget, after that the attackers try to “ruin” the organization until they win or their budget is exhausted (the continuation of the attack is not considered a separate move and can be carried out at any time during the game during the attacker's turn);
- the defenders acquire 3 SZIs in a row, then the attacker and the defenders take turns each in turn, in the case of the budget being defended by the defenders, the attacker walks in a row until winning or running out of his budget (in this case, a successful attack (GIS is highlighted in red), protection on this line is prohibited) .
In both cases, the attacker must not see the interface of the defenders.
In a real learning setting, the game was as follows:
- one student was chosen to play the role of "hacker";
- the rest of the students played the role of the organization’s information security department, of which the head of the department was chosen, whose word was final in determining the next step;
- selection and switching of interfaces was carried out by the teacher;
- the attacker leaves the classroom and the defenders make decisions about protection, the teacher makes the decisions, switches the interface and calls the attacker;
- the attacker makes his move or moves and in the second version of the Game again leaves the class.
Following the results of the Game, it is mandatory for students to make general conclusions, for example, the presence of very expensive hacks or the ratio of budgets.
results
Involvement in the game was almost one hundred percent. Students, and then really working specialists (for the sake of comparing strategies we gave to play and them) played with great interest, selected strategies, argued, played in a team, leaders were determined.
After a large number of games, players have a question about the withdrawal of a universal strategy that guarantees a win or a desire to “improve” the Game.
This moment is the key in the transition from the game to the training of professional disciplines, which allow to solve the (real) situations modeled by the Game in the best way:
- risk theory;
- game theory;
- Database;
- programming;
- modeling;
- situation modeling
- probability theory;
- theory of collecting and analyzing information;
- statistics;
- metrology;
- microeconomics;
- project and process management.
The selected problem-gaming technique based on the results of multiple experiments was recognized successful and adopted by the teaching staff.
In addition to this application (role, model, motivation, problem statement, visual demonstration of the complexity and volume of information security tasks), this technique can be used in the work on diploma theses or dissertations, including in defining their topics - areas of scientific research.
Applicability of the model in non-educational activities
The results of using the Games prompted several possible non-learning situations of its use:
- in the case of developing the Game for a specific information system of a real organization and its complication (increasing the volume of used vulnerabilities and threats), you can get a model that describes the real situation with information security quite accurately, which in turn will allow to conduct training (cyber draw) and simulation testing of the protection system information, assess risks and verify such assessments, justify the budgets of information security departments;
- carry out comprehensive testing of regulatory documents (so an attempt to combine “vulnerabilities” and “objects of attack” with “threats,“ threats ”with“ measures ”, and then with their implementation through regulatory requirements for SIS and an attempt to select real SIS for these requirements, showed real the impossibility of completing this process in its entirety without any simplifications and assumptions that reduce the volume and, consequently, the complexity of the resulting system, and leading to the omission of the unauthorized access to information used in reality).
Gaming model development
And, as usual, I will call for the development of the described technique and for writing the Game in “normal” programming languages. Looking ahead, I will say that this technique is planned to be used as a problem setting with a transition to the implementation of the specified information system scheme, information protection system and information "retrieval" system in practical and laboratory work in the specialty "Information Security".
Link to Zip-archive with the Game .
Source: https://habr.com/ru/post/286114/
All Articles