LNKpokalipsis or a new bug from MS (CVE-2010-2568)
On Habré already wrote about Win32 / Stuxnet and the vulnerability revealed together with it. But for some reason, little attention is paid to the vulnerability itself, basically all the noise around Win32 / Stuxnet and the valid certificates used to sign the components of this malware. Meanwhile, this vulnerability has already appeared in public access. First in the form of PoC , and then in the form of a module for Metasploit. MS, as in other, and usually, do not care about the criticality of this vulnerability and it is likely to release the patch no earlier than August 10th. And for WinXP SP2 there will be no patch at all, although it’s not strange that there are still users on it and there are not as few of them as we would like. Confirmation of the distribution of threats by window versions from Symantec , where exactly WinXP SP2 has a large proportion of recorded incidents.

As vectors for the use of this vulnerability can be not only USB-accumulated, but also network resources. For example, in Metasploit, exploitation occurs via WebDAV.
Vulnerability works like this:
')
This is not about a banal overflow or an unnamed pointer, everything is much worse, because vulnerability by design so to speak (all versions of Windows are vulnerable). Those. developers have missed their ears, that such a way can be used by attackers to install any malware. Although it may be much worse, and this is just another backdoor left in the system at the request of the NSA? I'm afraid of the truth, we will never know. Now let's talk directly about the technical details of the work of this vulnerability.
CVE-2010-2568 - a vulnerability is found in the handler of LNK files, which is more precisely related to the Control Panel shortcuts display process when they are loaded into memory by the Explorer.exe process. Vulnerable is the shell32.dll library in which incorrect processing takes place. The diagram below illustrates the flow of data between the called functions during the operation of the exploit (peeped here ). Successful execution of an exploit is loading a third-party dynamic library using the LoadLibraryW function using WinAPI.

The call sequence looks like this:
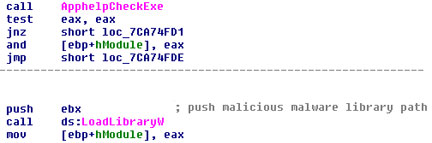
Actually, it is the code below that causes the malicious DLL to run, this code is in the _LoadCPLModule function, which is called from CPL_LoadCPLModule .
The exploit in the Metasploit for exploiting the vulnerability generates the following URL " {webdav} {exploit_base} \\ {exploit_dll} ", this approach to exploiting this vulnerability greatly expands its use beyond the limits of USB-drives. What to do and how to protect yourself from this vulnerability can be read here . More on the topic of countering this vulnerability can be found in the blog of the independent researcher Didier Stevens. It describes two ways:
1) Prevent autorun and execute executables from external media. But this will not save you from the possibility of infection from the network balloon and WebDAV links.
2) Installing Software Restriction Policies (SRP)

As vectors for the use of this vulnerability can be not only USB-accumulated, but also network resources. For example, in Metasploit, exploitation occurs via WebDAV.
Vulnerability works like this:
')
This is not about a banal overflow or an unnamed pointer, everything is much worse, because vulnerability by design so to speak (all versions of Windows are vulnerable). Those. developers have missed their ears, that such a way can be used by attackers to install any malware. Although it may be much worse, and this is just another backdoor left in the system at the request of the NSA? I'm afraid of the truth, we will never know. Now let's talk directly about the technical details of the work of this vulnerability.
CVE-2010-2568 - a vulnerability is found in the handler of LNK files, which is more precisely related to the Control Panel shortcuts display process when they are loaded into memory by the Explorer.exe process. Vulnerable is the shell32.dll library in which incorrect processing takes place. The diagram below illustrates the flow of data between the called functions during the operation of the exploit (peeped here ). Successful execution of an exploit is loading a third-party dynamic library using the LoadLibraryW function using WinAPI.

The call sequence looks like this:
SHELL32!CRunnableTask::Run
SHELL32!CGetIconTask::RunInitRT
SHELL32!SHGetIconFromPIDL
SHELL32!CFSFolder::GetIconOf
SHELL32!SHGetIconFromPIDL
SHELL32!_GetILIndexGivenPXIcon
SHELL32!CShellLink::GetIconLocation
SHELL32!CExtractIconBase::GetIconLocation
SHELL32!CCtrlExtIconBase::_GetIconLocationW
SHELL32!CPL_FindCPLInfo
SHELL32!CPL_LoadAndFindApplet
SHELL32!_LoadCPLModule
SHELL32!_imp__LoadLibraryW
Actually, it is the code below that causes the malicious DLL to run, this code is in the _LoadCPLModule function, which is called from CPL_LoadCPLModule .

The exploit in the Metasploit for exploiting the vulnerability generates the following URL " {webdav} {exploit_base} \\ {exploit_dll} ", this approach to exploiting this vulnerability greatly expands its use beyond the limits of USB-drives. What to do and how to protect yourself from this vulnerability can be read here . More on the topic of countering this vulnerability can be found in the blog of the independent researcher Didier Stevens. It describes two ways:
1) Prevent autorun and execute executables from external media. But this will not save you from the possibility of infection from the network balloon and WebDAV links.
2) Installing Software Restriction Policies (SRP)
Source: https://habr.com/ru/post/99732/
All Articles