New 0-day or feature from Microsoft?
It all started with the fact that on July 9, specialists of the Belarusian antivirus company VirusBlokad discovered an interesting malware whose drivers had a legal digital signature from Realtek. The surprises did not end there, since this malware used a previously unknown vulnerability in the processing of LNK files (Shell Link) for unauthorized distribution from various USB-drives. Having seen this informational message, we also paid attention to this threat, and noticed a rather interesting landscape of its distribution (data obtained through our system of early detection of threats ThreatSense.Net ).
')
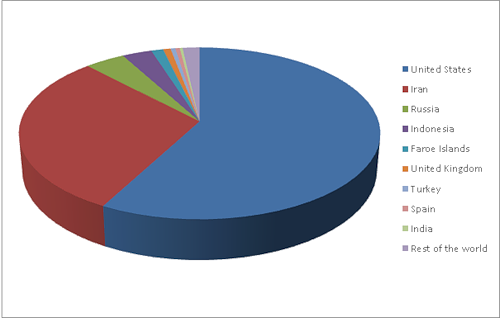
According to the statistics we obtained, it is clear that the United States is clearly the leading region in the number of infections. Further, with a double separation comes Iran, followed by Russia.
In part, this distribution of data is confirmed by statistics from Microsoft, but it is possible that it deliberately omitted data for the United States, since an active investigation is under way related to the appearance of this threat. MS only on Saturday July 16th MS released Security Advisory , which officially confirmed the presence of this vulnerability. So let's talk now about the technical details of this threat.
Method of distribution: 0-day or feature?
The only way to spread this malicious program is to infect USB drives. Interestingly, the way to launch a malicious program uses a previously unknown vulnerability in the processing of LNK files contained on a USB drive. Malicious code execution occurs due to a Windows Shell vulnerability related to the display of specially prepared LNK files. The contents of the infected drive look like this:

You can see that in the root directory there are two hidden files that are installed during the system infection. The LNK files themselves contain the following:

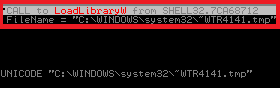
The figure shows the part that actually contains the data that allow
unauthorized executable file. When viewing the contents of a USB drive in Windows Explorer or any other file manager, LNK files are automatically loaded into memory. Vulnerability allows to execute arbitrary dynamic library, in our case it is ~ WTR4141.tmp.
All operating systems ranging from Windows XP and including Windows 7 are vulnerable. We detect LNK files that exploit this vulnerability as LNK / Autostart. And now let's talk about the actual malicious components that are installed in the system.
Win32 / Stuxnet
The most insidious and unexpected for the antivirus industry turned out that some components of this malicious program have a legitimate digital signature (at the moment this certificate has already been revoked ). And even more interesting was the fact that the certificate was issued to Realtek.
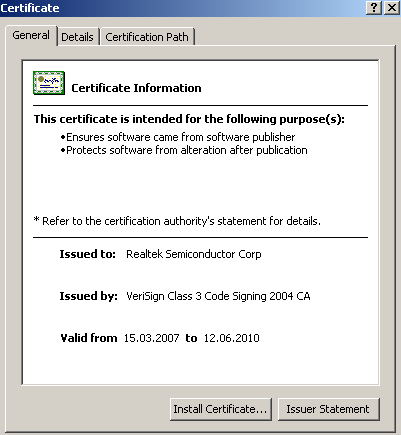
In particular, he signed the library that runs in connection with the vulnerability of processing LNK files. Also, the two drivers have signatures installed in the system. All this makes it possible to bypass most HIPS systems, since the presence of a digital signature on many systems is considered a sign of a legal program.
In the process of analyzing this malware, no obvious ways of cybercriminal monetization were identified. But the possibilities of collecting information from SCADA systems were found, which, as a rule, are used at large industrial enterprises. And the hidden possibilities of network interaction, give every reason to believe that Win32 / Stuxnet is aimed at industrial espionage. While the investigation is underway, we were forbidden to make public some of the details associated with this malware, so for now we will limit ourselves to this information only.
In the meantime, we recommend that you familiarize yourself with information on infection prevention using this 0-day, published by independent researcher Didier Stevens.

| United States | 57.71% |
| Iran | 30.00% |
| Russia | 4.09% |
| Indonesia | 3.04% |
| Faore islands | 1.22% |
| United kingdom | 0.77% |
| Turkey | 0.49% |
| Spain | 0.44% |
| India | 0.29% |
| Rest of the world | 1.73% |
')
According to the statistics we obtained, it is clear that the United States is clearly the leading region in the number of infections. Further, with a double separation comes Iran, followed by Russia.
In part, this distribution of data is confirmed by statistics from Microsoft, but it is possible that it deliberately omitted data for the United States, since an active investigation is under way related to the appearance of this threat. MS only on Saturday July 16th MS released Security Advisory , which officially confirmed the presence of this vulnerability. So let's talk now about the technical details of this threat.
Method of distribution: 0-day or feature?
The only way to spread this malicious program is to infect USB drives. Interestingly, the way to launch a malicious program uses a previously unknown vulnerability in the processing of LNK files contained on a USB drive. Malicious code execution occurs due to a Windows Shell vulnerability related to the display of specially prepared LNK files. The contents of the infected drive look like this:

You can see that in the root directory there are two hidden files that are installed during the system infection. The LNK files themselves contain the following:

The figure shows the part that actually contains the data that allow
unauthorized executable file. When viewing the contents of a USB drive in Windows Explorer or any other file manager, LNK files are automatically loaded into memory. Vulnerability allows to execute arbitrary dynamic library, in our case it is ~ WTR4141.tmp.

All operating systems ranging from Windows XP and including Windows 7 are vulnerable. We detect LNK files that exploit this vulnerability as LNK / Autostart. And now let's talk about the actual malicious components that are installed in the system.
Win32 / Stuxnet
The most insidious and unexpected for the antivirus industry turned out that some components of this malicious program have a legitimate digital signature (at the moment this certificate has already been revoked ). And even more interesting was the fact that the certificate was issued to Realtek.

In particular, he signed the library that runs in connection with the vulnerability of processing LNK files. Also, the two drivers have signatures installed in the system. All this makes it possible to bypass most HIPS systems, since the presence of a digital signature on many systems is considered a sign of a legal program.
In the process of analyzing this malware, no obvious ways of cybercriminal monetization were identified. But the possibilities of collecting information from SCADA systems were found, which, as a rule, are used at large industrial enterprises. And the hidden possibilities of network interaction, give every reason to believe that Win32 / Stuxnet is aimed at industrial espionage. While the investigation is underway, we were forbidden to make public some of the details associated with this malware, so for now we will limit ourselves to this information only.
In the meantime, we recommend that you familiarize yourself with information on infection prevention using this 0-day, published by independent researcher Didier Stevens.
Source: https://habr.com/ru/post/99506/
All Articles