Hackers have access to the database of users of The Pirate Bay
Argentine hacker Ch Russo reported that he and two partners discovered numerous vulnerabilities on thepiratebay.org related to the ability to inject SQL code. Using these vulnerabilities, they gained access to the database of site users and thus gained the ability to create, delete, modify and view all information about users, including the numbers and names of file trackers or torrents downloaded by users.
Screenshot of The Pirate Bay administrative panel showing recently registered users:

Ch Russo claims that neither he nor his partners have changed or deleted information in The Pirate Bay database. But he admits that they realize how valuable this access and the obtained information can be for anti-piracy organizations supported, for example, by the RIAA (American Recording Companies Association) or MPAA (American Film Companies Association).
')
In a telephone interview, Ch Russo told Brian Krebs, the author of KrebsOnSecurity.com, that these groups are likely to be very interested in this information, but he and his partners are not going to sell it. Instead, they would like to tell people that their information may not be protected very well.
Ch Russo showed Krebs usernames and password hashes in MD5 administrators and site moderators. Also, Ch Russo was able to send an e-mail and Krebs password hash, having learned from him only a username.
On Monday, Krebs attempted to contact the administrators through thepiratebay.org/contact, but he was never answered. He wrote to them on the official IRC channel, but after the publication of usernames and password hashes, he was simply banned.
According to Ch Russo, administrators have already deleted a component of the site, which facilitated access to the user database, stating that it did not contact administrators directly.
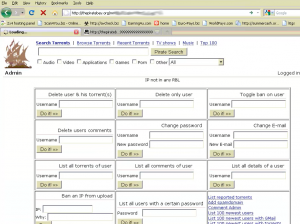
Screenshot of The Pirate Bay administrative panel showing recently registered users:

Ch Russo claims that neither he nor his partners have changed or deleted information in The Pirate Bay database. But he admits that they realize how valuable this access and the obtained information can be for anti-piracy organizations supported, for example, by the RIAA (American Recording Companies Association) or MPAA (American Film Companies Association).
')
In a telephone interview, Ch Russo told Brian Krebs, the author of KrebsOnSecurity.com, that these groups are likely to be very interested in this information, but he and his partners are not going to sell it. Instead, they would like to tell people that their information may not be protected very well.
Ch Russo showed Krebs usernames and password hashes in MD5 administrators and site moderators. Also, Ch Russo was able to send an e-mail and Krebs password hash, having learned from him only a username.
On Monday, Krebs attempted to contact the administrators through thepiratebay.org/contact, but he was never answered. He wrote to them on the official IRC channel, but after the publication of usernames and password hashes, he was simply banned.
According to Ch Russo, administrators have already deleted a component of the site, which facilitated access to the user database, stating that it did not contact administrators directly.

Source: https://habr.com/ru/post/98601/
All Articles