Win32 / Olmarik or TDL3 study in detail
Recently, many have begun to talk a lot about the TDSS rootkit, and more specifically about its latest modification TDL3. According to ESET, this rootkit belongs to the Win32 / Olmarik family of malicious programs. According to our statistics, he is most active in the United States. Other antivirus companies also confirm this fact.
It should be noted that in a fairly short period of time, several independent studies have already appeared on this topic: one , two , three . Today, the Center for Virus Research and Analysis of the Russian representative office of ESET released its analytical report “Win32 / Olmarik Rootkit: Work and Distribution Technologies” , which was prepared following a long-term monitoring and analysis of various modifications of this rootkit. Below we provide excerpts from this document.
In our study, there is a description of not only the technologies of introduction and operation, but also the ways to monetize distribution. In our report, there are a number of technological issues not covered in other analytical papers.
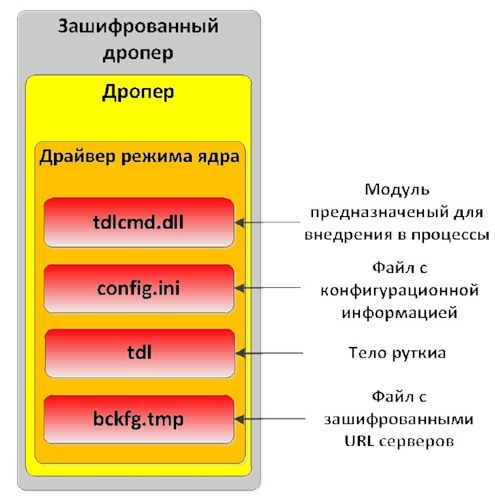
WIN32 / OLMARIK is distributed through a special program, the droper, whose task is to install a hidden rootkit. The droper body is encrypted and obfuscated in order to make it difficult for antivirus software to detect it. During decryption, the droper uses some techniques to counteract debugging, emulation, and determine execution in a virtual machine environment.
')
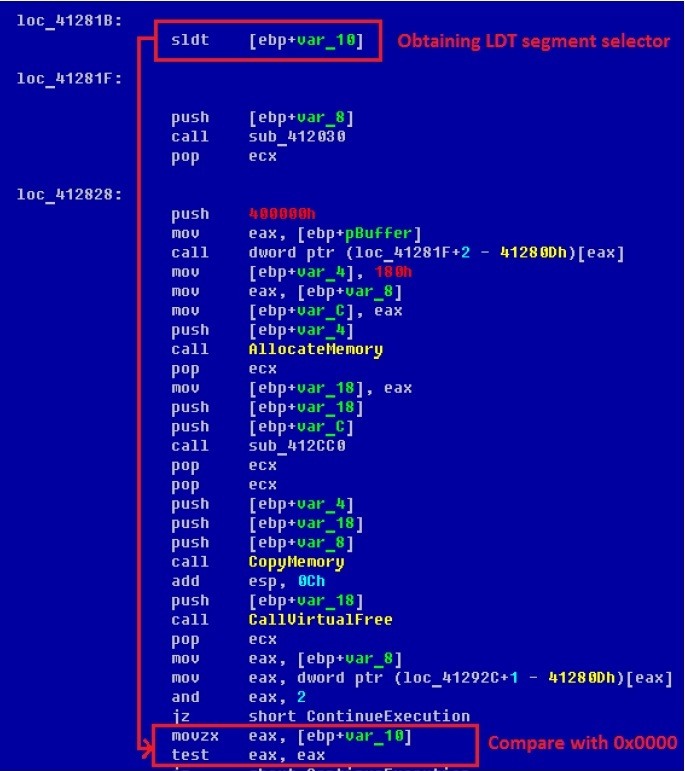
Droper checks whether it runs in the virtual machine environment by reading the contents of the LDTR register containing the segment selector in which the local segment descriptor table is located. This table is used to calculate a linear address from a pair of selector_segment: offset. Microsoft Windows operating systems do not use local segment descriptor tables and initialize the LDTR register to zero. At the same time, most modern virtual machines (VMware, Virtual PC, etc.) use them and, therefore, initialize the LDTR register with a nonzero value. This fact is used by malware to detect execution in a virtual environment. The contents of the LDTR register can be obtained using the instruction sldt (store local descriptor table), which is not privileged and can be executed in the 3rd protection ring. The figure below shows a code snippet performing a similar check.
Some types of rootkits of this family are specially designed for distribution in certain countries. For example, a sample that is widely used in the UK performs a locale with values from the following list before installation:
• Azerbaijan;
• Belarus;
• Kazakhstan;
• Kyrgyzstan;
• Russia;
• Uzbekistan;
• Ukraine;
• Czech Republic;
• Poland.
If a match is found, the dropper exits without installing a rootkit.
Read more in our analytical report “Win32 / Olmarik rootkit: technologies of work and distribution”
It should be noted that in a fairly short period of time, several independent studies have already appeared on this topic: one , two , three . Today, the Center for Virus Research and Analysis of the Russian representative office of ESET released its analytical report “Win32 / Olmarik Rootkit: Work and Distribution Technologies” , which was prepared following a long-term monitoring and analysis of various modifications of this rootkit. Below we provide excerpts from this document.
In our study, there is a description of not only the technologies of introduction and operation, but also the ways to monetize distribution. In our report, there are a number of technological issues not covered in other analytical papers.
WIN32 / OLMARIK is distributed through a special program, the droper, whose task is to install a hidden rootkit. The droper body is encrypted and obfuscated in order to make it difficult for antivirus software to detect it. During decryption, the droper uses some techniques to counteract debugging, emulation, and determine execution in a virtual machine environment.
')

Droper checks whether it runs in the virtual machine environment by reading the contents of the LDTR register containing the segment selector in which the local segment descriptor table is located. This table is used to calculate a linear address from a pair of selector_segment: offset. Microsoft Windows operating systems do not use local segment descriptor tables and initialize the LDTR register to zero. At the same time, most modern virtual machines (VMware, Virtual PC, etc.) use them and, therefore, initialize the LDTR register with a nonzero value. This fact is used by malware to detect execution in a virtual environment. The contents of the LDTR register can be obtained using the instruction sldt (store local descriptor table), which is not privileged and can be executed in the 3rd protection ring. The figure below shows a code snippet performing a similar check.

Some types of rootkits of this family are specially designed for distribution in certain countries. For example, a sample that is widely used in the UK performs a locale with values from the following list before installation:
• Azerbaijan;
• Belarus;
• Kazakhstan;
• Kyrgyzstan;
• Russia;
• Uzbekistan;
• Ukraine;
• Czech Republic;
• Poland.
If a match is found, the dropper exits without installing a rootkit.
Read more in our analytical report “Win32 / Olmarik rootkit: technologies of work and distribution”
Source: https://habr.com/ru/post/97674/
All Articles