The story of one exploit or “endless” 0-day: CVE-2010-1297
This story began more than ten days ago, when it became aware of another vulnerability in Adobe products, leading to the possibility of remote execution of malicious code. The active spread of this infection began, in particular, the exploit became part of many exploit packs that are actively spreading at a given time. But the most interesting thing began after the public exploit code appeared in the Metasploit on June 10 in the evening.
Now there are already several modifications of this exploit, but fundamentally they are no different. Basically, the changes affected the shellcode, which is executed immediately after successful heap-spray and the payload, which is executed after successful exploitation of the vulnerability. The heap-spray attack is performed using a javascript script:
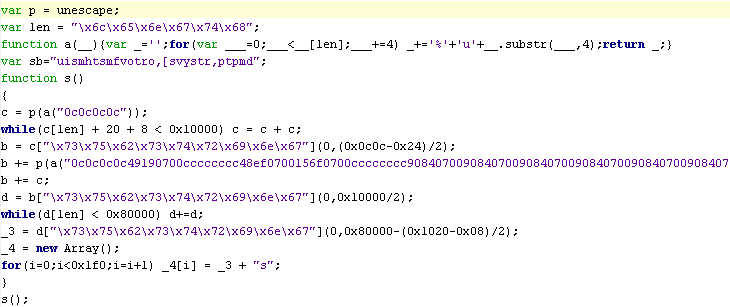
')
For successful exploitation of the vulnerability, the authors actively use techniques of return-oriented programming (popularly just ROP (Return-Oriented Programming)). On the topic of ROP there is a good fact - finding material from the famous researcher Dino Dai Zovi.

If you look at the memory card at the time of the heap-spray active attack, you can see a large number of allocated memory blocks of the same type with read and write attributes. But at the very end of this block chain, you can see two blocks of memory that have an attribute to execute. Actually, this is where the shellcode is located, which will be executed later.
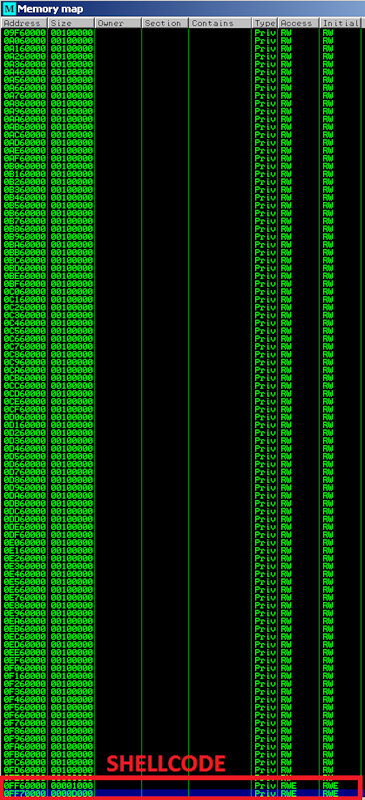
After successful application of heap-spray equipment, control is transferred to a shell code, which consists of several levels. Each level decodes the next.

As a result of the execution of this string of shell-code, the executable file and the pdf-file are reset to the temp directory. The executable file is a Trojan downloader detected by us as Win32 / Small.NEM. Interestingly, in the resources section it contains the following information:
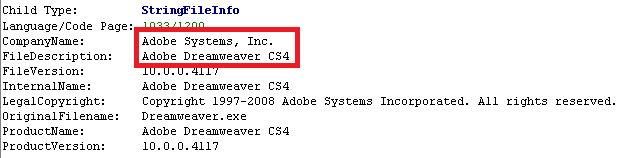
Thus, he tries to disguise himself as a legal program.
After the successful launch of the malicious program, the Adobe Reader is restarted and the previously prepared pdf file is opened.
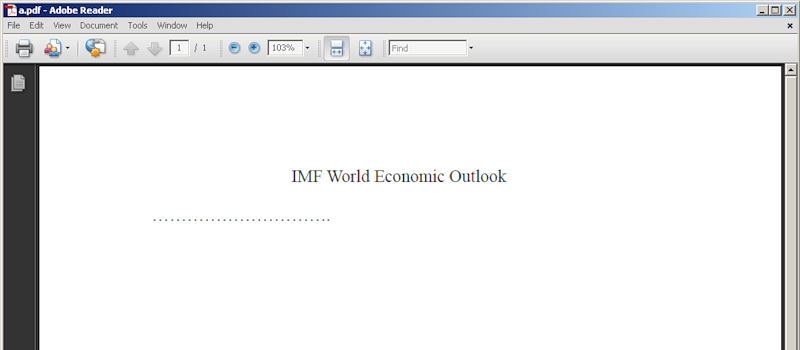
This pdf-file does not contain malicious content and is intended to bring down the user who has opened the file containing the exploit before.
Finally, I would like to note that the vulnerability for Adobe Reader has not yet been eliminated and can be successfully exploited. An update for Adobe Reader that resolves this vulnerability is scheduled only for the end of the current month. Be carefull!
Now there are already several modifications of this exploit, but fundamentally they are no different. Basically, the changes affected the shellcode, which is executed immediately after successful heap-spray and the payload, which is executed after successful exploitation of the vulnerability. The heap-spray attack is performed using a javascript script:

')
For successful exploitation of the vulnerability, the authors actively use techniques of return-oriented programming (popularly just ROP (Return-Oriented Programming)). On the topic of ROP there is a good fact - finding material from the famous researcher Dino Dai Zovi.

If you look at the memory card at the time of the heap-spray active attack, you can see a large number of allocated memory blocks of the same type with read and write attributes. But at the very end of this block chain, you can see two blocks of memory that have an attribute to execute. Actually, this is where the shellcode is located, which will be executed later.

After successful application of heap-spray equipment, control is transferred to a shell code, which consists of several levels. Each level decodes the next.

As a result of the execution of this string of shell-code, the executable file and the pdf-file are reset to the temp directory. The executable file is a Trojan downloader detected by us as Win32 / Small.NEM. Interestingly, in the resources section it contains the following information:

Thus, he tries to disguise himself as a legal program.
After the successful launch of the malicious program, the Adobe Reader is restarted and the previously prepared pdf file is opened.

This pdf-file does not contain malicious content and is intended to bring down the user who has opened the file containing the exploit before.
Finally, I would like to note that the vulnerability for Adobe Reader has not yet been eliminated and can be successfully exploited. An update for Adobe Reader that resolves this vulnerability is scheduled only for the end of the current month. Be carefull!
Source: https://habr.com/ru/post/96879/
All Articles