Generate a chain of certificates with elliptic curves using OpenSSL
 I think many have heard of cryptography of elliptic curves, about
I think many have heard of cryptography of elliptic curves, aboutthat it works many times faster than RSA and, with a disproportionately shorter key length, provides an incomparably greater resistance to cracking. If you have not heard, then you can look at the wiki or read in the books by A.A. Bolotov.
Unfortunately, this type of encryption is weak. I will try to explain how to use it and help me with this OpenSSL.
Not to be unsubstantiated, I will give a comparison of the necessary key lengths to ensure comparable resistance to cracking for various algorithms. We are interested in the right side.
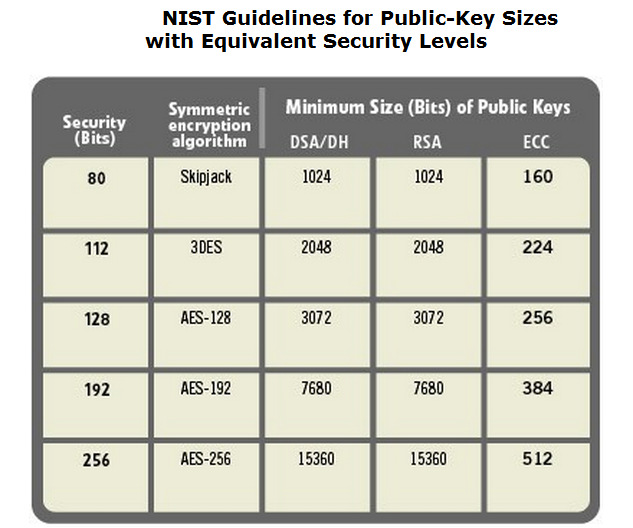
It can be seen that today’s popular RSA keys with a length of 1024–2048 bits only correspond to a 160-224bit ECC key (Elliptic Curve Cryptography)
Well, to understand what RSA brake is enough to try to generate the longest of the keys suggested in the table (and go take a nap):
')
openssl genrsa 15360
Those wishing to touch the "next gen" of cryptography, invented already in 1985, please under the cat.
First of all, we first determine how long the key is needed. In ECC, certain curve parameters correspond to a specific key length. But we don’t have to pick them up; NIST smart guys have done it for us.
You can see the list of available curves with the command
openssl ecparam -list_curves
The list this command gives impressive, and if you do not have certain preferences, choose the one that you like and more than 160 bits, for example one of the longest:
secp521r1 : NIST / SECG curve over a 521 bit prime field
Create a folder, for example c: \ ec \ and add everything there. In the CA folder everything for the root certificate, in the Client folder - everything for the client certificate.
We need
- Generate a root self-signed certificate (CA)
- Generate client certificate
- Sign the client certificate root
1) We generate the root certificate.
1.1) Generating the key for the root certificate:
openssl ecparam-name secp521r1 -genkey-out c: \ ec \ CA \ CA.key
We get something like
----- BEGIN EC PARAMETERS -----
BgUrgQQAIw ==
----- END EC PARAMETERS -----
----- BEGIN EC PRIVATE KEY -----
MIHcAgEBBEIBrtyWCH0 + OAZqbr84CLFvsxbB2 / AfjKD6 + fpXQF5qs7n1yRmxItRH
vNlylh7dNZEwYwleI5RLQV3pz6p06hgo6c2gBwYFK4EEACOhgYkDgYYABAEx + OTa
s3 / djxFMW7GNcWWVGv5Y7Vwvr2k00gXVyUpSySSudXKSaWYrblBtPKOWRcuHzkq5
tks3vTKclq3NgPpdjgAPk4ha68UTdX + JI / oK + EMUwCdaCuIYMDeRO1VHByEx + 3/1
XlkYPvEKRkQDLJP22vXE / NEirdZ / WzO6QTWku5q0UQ ==
----- END EC PRIVATE KEY -----
First, there are the parameters of the curve (its name is secp521r1), and then the key already generated on its basis.
1.1.1) If desired, we protect it with a password (encrypted using the AES algorithm with a key length of 256 bits):
openssl ec -in c: \ ec \ ca \ ca.key-out c: \ ec \ ca \ ca.protected.key -aes256
We get just such beauty (password - qwerty ):
----- BEGIN EC PRIVATE KEY -----
Proc-Type: 4, ENCRYPTED
DEK-Info: AES-256-CBC, E34E27512B4DCB01524A5F17937DA7D5
xF7XZyLtpqofqkl0PVCf / 1cOEygL82itDrz7k5tVqJLMDYzG9RnTTPwJgOXsZkV1
dk5MQe9h / ixPkFE / B / Ox1OH5SI4Frb8dgS8mT9mq620A4RJdD6yAZcpicnuyyXma
1dZ + xoyRiGeHxcnErDJpvA7H6BpIAzinz4lMzY1pz2TXTdGLU + 0bK1bMiDFxRvwA
jyUEsrZA2kZ5v ++ MZzmxTsJZ6XTCRzeUPhhvNE0VKF8xPSWMEB6WeJPr + rl3zBZ7
sE71UwiaIddFHkOe3UnlAxjohABpZytUud8uS0Wi + 5E =
----- END EC PRIVATE KEY -----
2) Generate a certificate request. A request is a structure of the public key, its hash, and information about the owner of the certificate. Key hashing algorithm choose SHA512 :
openssl req -new -key c: \ ec \ CA \ ca.protected.key -sha512 -out c: \ ec \ CA \ CA.req
We get another beauty:
----- BEGIN CERTIFICATE REQUEST -----
MIIBrzCCARACAQAwazELMAkGA1UEBhMCUlUxDzANBgNVBAgMBk1vc2NvdzEPMA0G
A1UEBwwGTW9zY293MRIwEAYDVQQKDAloYWJyYWhhYnIxCzAJBgNVBAsMAklUMRkw
FwYDVQQDDBB3d3cuaGFicmFoYWJyLnJ1MIGbMBAGByqGSM49AgEGBSuBBAAjA4GG
AAQBMfjk2rN / 3Y8RTFuxjXFllRr + WO1cL69pNNIF1clKUskkrnVykmlmK25QbTyj
lkXLh85KubZLN70ynJatzYD6XY4AD5OIWuvFE3V / iSP6CvhDFMAnWgriGDA3kTtV
RwchMft / 9V5ZGD7xCkZEAyyT9tr1xPzRIq3Wf1szukE1pLuatFGgADAKBggqhkjO
PQQDBAOBjAAwgYgCQgHa0d5nc9UX41jj42lOnv0Hh9EXfROFm7QoUSoKdye7s7uE
nZPmGTM + h5bRG8Y + hHD3QQyM8vY9TnMVVp0r2xmYHwJCAbE5CTRDoeXf3ZpKUW77
SpXtPgYEEelkOm3Ua + / 0XVoZviBT7wF5nrqTYnMJ2MQtyvKKMCO74qqUiMoudZ7z
MSgO
----- END CERTIFICATE REQUEST -----
3) The final step. We sign our request with our private key. Not the entire request will be signed, but only its hash, so we indicated at the previous step which hashing algorithm to select
For this we will need
3.1) Change in openssl.cfg in the [CA_default] dir section to “c: / ec” instead of ./DemoCA by default
3.2) In the c: \ ec folder, create 2 files: an empty index.txt and a serial file, in which to write 01 without spaces or line breaks .
3.3) Run a magic command
openssl ca -days 365 -policy policy_anything -keyfile c: \ ec \ CA \ CA.protected.key -in c: \ ec \ CA \ CA.req -selfsign -out c: \ ec \ CA \ ca.crt -outdir c: \ ec \ CA
At the entrance, we submit a certificate request, the path to the private key and say that the certificate will be self-signed ( -selfsign ). At the output we get a real beautiful certificate (save as ca.crt, then you can view it using windows):
Certificate:.
Data:
Version: 3 (0x2)
Serial Number: 1 (0x1)
Signature Algorithm: ecdsa-with-SHA1
Issuer: C = RU, ST = Moscow, L = Moscow, O = habrahabr, OU = IT, CN = www.habrahabr.ru
Validity
Not Before: Jun 11 05:12:03 2010 GMT
Not After: Jun 11 05:12:03 2011 GMT
Subject: C = RU, ST = Moscow, L = Moscow, O = habrahabr, OU = IT, CN = www.habrahabr.ru
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public Key: (521 bit)
pub:
04: 01: 31: f8: e4: da: b3: 7f: dd: 8f: 11: 4c: 5b: b1: 8d:
71: 65: 95: 1a: fe: 58: ed: 5c: 2f: af: 69: 34: d2: 05: d5:
c9: 4a: 52: c9: 24: ae: 75: 72: 92: 69: 66: 2b: 6e: 50: 6d:
3c: a3: 96: 45: cb: 87: ce: 4a: b9: b6: 4b: 37: bd: 32: 9c:
96: ad: cd: 80: fa: 5d: 8e: 00: 0f: 93: 88: 5a: eb: c5: 13:
75: 7f: 89: 23: fa: 0a: f8: 43: 14: c0: 27: 5a: 0a: e2: 18:
30: 37: 91: 3b: 55: 47: 07: 21: 31: fb: 7f: f5: 5e: 59: 18:
3e: f1: 0a: 46: 44: 03: 2c: 93: f6: da: f5: c4: fc: d1: 22:
ad: d6: 7f: 5b: 33: ba: 41: 35: a4: bb: 9a: b4: 51
ASN1 OID: secp521r1
X509v3 extensions:
X509v3 Basic Constraints:
CA: FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
3D: FF: 46: 92: 1C: 7E: C1: F3: 84: D0: 26: BA: CD: 5D: AD: 25: B8: CC: DE: 44
X509v3 Author Key Key Identifier:
keyid: 3D: FF: 46: 92: 1C: 7E: C1: F3: 84: D0: 26: BA: CD: 5D: AD: 25: B8: CC: DE: 44
Signature Algorithm: ecdsa-with-SHA1
30: 81: 88: 02: 42: 01: bf: ca: f1: 4c: 51: 85: b4: 65: 26: de: eb: 14:
ee: 07: a1: 1f: 97: 1d: 35: 1a: c3: 61: 8a: 82: 97: 96: 7b: f4: d4: 95:
73: 4d: 84: d2: 78: b2: 35: fd: 72: 05: ea: 6d: a4: 49: e1: 18: a0: ff:
13: 60: 7e: b0: 67: ba: 7f: cd: 8b: ef: 15: a6: 5d: 30: a3: 48: 9c: 02:
42: 01: 53: 27: 2c: 2c: b9: 79: b1: 0f: 9a: c3: f6: a0: c9: dc: 82: cb:
2f: 3c: d8: 0a: c1: 53: d7: 3c: 37: af: 54: 39: 78: de: ae: d9: d7: 55:
6f: de: cc: 9c: 75: cf: d5: 8e: 8e: cc: 2d: 0c: da: d1: be: c5: 8d: 2d:
2b: 68: 94: 9d: 0d: 8c: 89: aa: b9: 1d: e8: a2: 05
----- BEGIN CERTIFICATE -----
MIICxjCCAiigAwIBAgIBATAJBgcqhkjOPQQBMGsxCzAJBgNVBAYTAlJVMQ8wDQYD
VQQIDAZNb3Njb3cxDzANBgNVBAcMBk1vc2NvdzESMBAGA1UECgwJaGFicmFoYWJy
MQswCQYDVQQLDAJJVDEZMBcGA1UEAwwQd3d3LmhhYnJhaGFici5ydTAeFw0xMDA2
MTEwNTEyMDNaFw0xMTA2MTEwNTEyMDNaMGsxCzAJBgNVBAYTAlJVMQ8wDQYDVQQI
DAZNb3Njb3cxDzANBgNVBAcMBk1vc2NvdzESMBAGA1UECgwJaGFicmFoYWJyMQsw
CQYDVQQLDAJJVDEZMBcGA1UEAwwQd3d3LmhhYnJhaGFici5ydTCBmzAQBgcqhkjO
PQIBBgUrgQQAIwOBhgAEATH45Nqzf92PEUxbsY1xZZUa / ljtXC + vaTTSBdXJSlLJ
JK51cpJpZituUG08o5ZFy4fOSrm2Sze9MpyWrc2A + l2OAA + TiFrrxRN1f4kj + gr4
QxTAJ1oK4hgwN5E7VUcHITH7f / VeWRg + 8QpGRAMsk / ba9cT80SKt1n9bM7pBNaS7
mrRRo3sweTAJBgNVHRMEAjAAMCwGCWCGSAGG + EIBDQQfFh1PcGVuU1NMIEdlbmVy
YXRlZCBDZXJ0aWZpY2F0ZTAdBgNVHQ4EFgQUPf9Gkhx + wfOE0Ca6zV2tJbjM3kQw
HwYDVR0jBBgwFoAUPf9Gkhx + wfOE0Ca6zV2tJbjM3kQwCQYHKoZIzj0EAQOBjAAw
gYgCQgG / yvFMUYW0ZSbe6xTuB6Eflx01GsNhioKXlnv01JVzTYTSeLI1 / XIF6m2k
SeEYoP8TYH6wZ7p / zYvvFaZdMKNInAJCAVMnLCy5ebEPmsP2oMncgssvPNgKwVPX
PDevVDl43q7Z11Vv3sycdc / Vjo7MLQza0b7FjS0raJSdDYyJqrkd6KIF
----- END CERTIFICATE -----
Done! Now let's generate a client.
Steps 1-2 are very similar. Only the paths differ:
openssl ecparam -name secp521r1 -genkey -out c: \ ec \ Client \ Client.key
openssl ec -in c: \ ec \ Client \ Client.key-out c: \ ec \ Client \ Client.protected.key -aes256
openssl req -new -key c: \ ec \ Client \ Client.protected.key -sha512 -out c: \ ec \ Client \ Client.req
Step 3 differs besides the paths in that we log in a CA certificate, CA private key, client request and remove -selfsign
openssl ca -days 365 -policy policy_anything -keyfile c: \ ec \ CA \ CA.protected.key -cert c: \ ec \ CA \ CA.crt -in c: \ ec \ Client \ Client.req -out c: \ ec \ Client \ Client.crt -outdir c: \ ec \ Client
Everything! You can install CA.crt in the trusted root certificate store, open Client.crt and enjoy the fact that everything works (do not pay attention to a minor abuse about the root certificate, you probably still need to specify some extensions there)
Now a little about the cons:
- Default is not supported in XP. Perhaps there are alternative security providers
- Not all browsers all curves are supported even on Vista \ 7. IE can do almost everything, Chrome is everything, but Opera is nothing.
You can test your browser for compatibility with such certificates, for example, on the Fedora website .
Have fun!
UPD:
Archive of the contents of the ec folder is available here.
Source: https://habr.com/ru/post/96190/
All Articles