Remove trojan winlock
I know that in Habré such posts are not very fond of, nevertheless, I think that this method may be useful to some or just save time. The trojan that I got fresh and is determined by just a few antivirus. The results of the virus test. I could not find the unlock code either. Therefore, in order not to bore me with a description of how I was looking for it, I will make a post in the form of a brief guide.
So, after infection, such disgusting appears on the desktop:
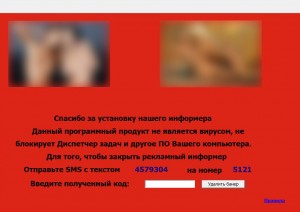
')
The Trojan prohibits the launch of most programs (browsers, regedit, processexplorer), although for some reason it leaves msconfig unattended. To unlock, ask to send SMS to number 5121 with text 4579304. The steps for deleting are as follows:
1) Go to the directory C: \ Program Files \ Common Files \ Office \ and delete the file exel.exe this is the ill-fated shell.
There are several notes to the deal: perhaps the location is chosen randomly, unfortunately there is no possibility to check And one more thing: I deleted via linux, but in my opinion it is not protected, so it can be removed from under Windows.
2) Reboot. Run regedit. In contrast to this case, my Trojan registered itself in the shell. Therefore, in the HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon branch, we only set Explorer.exe
View before change:
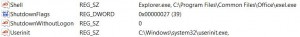
3) Check the hosts file (C: \ Windows \ System32 \ drivers \ etc \). The default should be one uncommented line:
127.0.0.1 localhost
That's basically it. Be careful. Hope to post someone save your time.
PS: Naturally, I sent the infected file to scan for antivirus companies that did not detect it.
P.S2: While writing the text came a response from Kaspersky Lab:
"Exel.exe - Trojan-Ransom.Win32.PinkBlocker.bmu
Currently, this file is determined by the antivirus with fresh anti-virus databases. "
Update databases.
So, after infection, such disgusting appears on the desktop:

')
The Trojan prohibits the launch of most programs (browsers, regedit, processexplorer), although for some reason it leaves msconfig unattended. To unlock, ask to send SMS to number 5121 with text 4579304. The steps for deleting are as follows:
1) Go to the directory C: \ Program Files \ Common Files \ Office \ and delete the file exel.exe this is the ill-fated shell.
There are several notes to the deal: perhaps the location is chosen randomly, unfortunately there is no possibility to check And one more thing: I deleted via linux, but in my opinion it is not protected, so it can be removed from under Windows.
2) Reboot. Run regedit. In contrast to this case, my Trojan registered itself in the shell. Therefore, in the HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon branch, we only set Explorer.exe
View before change:

3) Check the hosts file (C: \ Windows \ System32 \ drivers \ etc \). The default should be one uncommented line:
127.0.0.1 localhost
That's basically it. Be careful. Hope to post someone save your time.
PS: Naturally, I sent the infected file to scan for antivirus companies that did not detect it.
P.S2: While writing the text came a response from Kaspersky Lab:
"Exel.exe - Trojan-Ransom.Win32.PinkBlocker.bmu
Currently, this file is determined by the antivirus with fresh anti-virus databases. "
Update databases.
Source: https://habr.com/ru/post/95715/
All Articles