We learn passwords of users 1C
The opportunity was tested on the 1s version 8.1.13.41 and 8.2.10.82 platform (I think the situation is the same at 8.0) on the Windows Server 2008 operating system both 32 and 64 bit under local administrator rights in a terminal session. In fact, you can also find out the password on the operating systems “faster”, just not as trivial as on the OS under test.
For a successful test, it is necessary that at the terminal server there should already be at least one user who successfully logged into the 1C information database (in the configurator or enterprise mode).
Start the task manager and click on the “Display processes of all users” button, then in the appeared window click on the “Continue” button. After we select the menu item: “View” -> “Select columns ...” and in the appeared window put a check mark in front of the item “Command line” and press the button “OK”. We are looking for the process 1cv8.exe and see something like this:
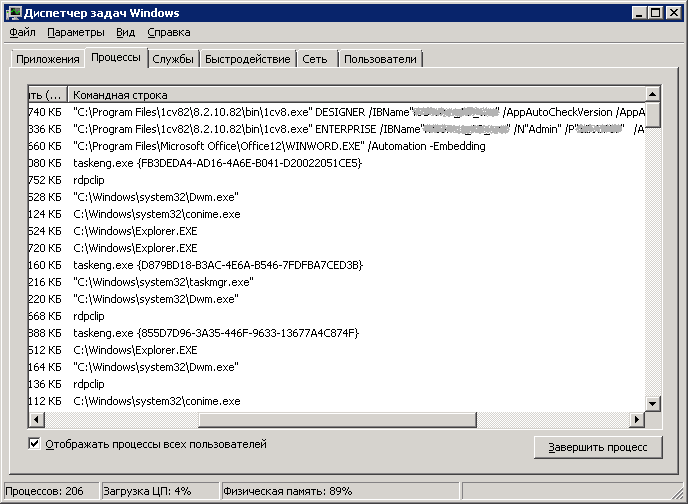
')
It became a revelation to me that by running 1C without such command line parameters as login and password, the current process starts a new one with authorization parameters of the command line, and then completes itself.
I will not emphasize that in many mortals the same password is used not only for access to IB 1C and what consequences can the fact of having a password have on the other side. I just want to note that all attempts by 1C itself to use AES encryption algorithms, Triple DES, SSL protocol for accessing information security, storing user passwords in a database table in a special format are crossed out by the above authorization method.
UPD:
Transferred to the blog "Information Security"
For a successful test, it is necessary that at the terminal server there should already be at least one user who successfully logged into the 1C information database (in the configurator or enterprise mode).
Start the task manager and click on the “Display processes of all users” button, then in the appeared window click on the “Continue” button. After we select the menu item: “View” -> “Select columns ...” and in the appeared window put a check mark in front of the item “Command line” and press the button “OK”. We are looking for the process 1cv8.exe and see something like this:

')
It became a revelation to me that by running 1C without such command line parameters as login and password, the current process starts a new one with authorization parameters of the command line, and then completes itself.
I will not emphasize that in many mortals the same password is used not only for access to IB 1C and what consequences can the fact of having a password have on the other side. I just want to note that all attempts by 1C itself to use AES encryption algorithms, Triple DES, SSL protocol for accessing information security, storing user passwords in a database table in a special format are crossed out by the above authorization method.
UPD:
Transferred to the blog "Information Security"
Source: https://habr.com/ru/post/94151/
All Articles