ATM virus post
Guys, I could not stand it. We are now talking about the ATM virus found more than a year ago in Diebold ATMs, and the basic principle of its operation. This ancient topic, the peak of hysteria, has long passed, but the public hasn’t found out what really happened, which is why even IT managers build a lot of guesswork and tell myths. Many articles have been written about this virus, from technical descriptions to political education of housewives , but the main trick was never revealed to us. I will try to explain more simply, because it is important for us to understand the essence, and not to delve into the details of the concrete implementation of something.
Picture to attract attention:

')
Start over. A year ago, there was a panic in the media: “ATMs are viruses!”, As a result of which all self-respecting bank managers supported this panic and began to try to do something. Panic arose for good reason: there are many freebie lovers in the world, so-called carders whose purpose is to get your bank card details, including the PIN code, in order to duplicate it and withdraw all money or purchase something. For this purpose, various methods of deception are invented, but before the appearance of the virus, they were all physical. But the virus is very interesting, because it brought the technology to a new level in essence - PIN codes began to be installed at the program level. It should be noted that the virus is still able to issue cash in unlimited amounts on a special card, but we, as clients, don't care, the bank gets into the money, not us.
Now let's make a superficial excursion into the ATM itself, and see where the viruses can come from. I will reveal the secret: the vast majority of ATMs running under Windows XP. The quick-witted reader will understand that in this case there is a threat, and we must begin to be afraid. But not everything is as bad as it seems. First, bona fide suppliers of ATM software, this Windows is severely curtailed, disabling everything that is possible in it, protecting ports, closing access, and so on. And secondly, the ATM never looks directly into the Internet - it is either in a dedicated segment of the corporate network, or connected through some encryption, such as Cisco or Checkpoint, and the virus gets there, to put it mildly, without options. Accordingly, the exit here is only an insider, because from the outside it is problematic to slip something into an ATM.
And what is a typical ATM software? And that's what. The architecture of this software is similar to the client-server. The server in this case is able to work with a specific hardware (of which in an ATM in bulk) and publishes outside the program interfaces common to each type of hardware (dispenser, card reader, printer, keyboard, etc.). The client, that is, the business application itself, in turn, using these interfaces, shows us advertising, issues a long-awaited salary, prints checks and blinks joyfully with lights. All this economy is called the standard CEN / XFS. I, perhaps, will attach a picture.

Having learned this news, we immediately start writing our ATM softwarewith blackjack and whores , since there are no secrets here, and no one hides all the emulators and specifications from us. We will read the magnetic strip from the card reader when the customer inserts the card, and the PIN code from the PIN keyboard when the customer dials it. Here it is, as they say, profit. And in appearance, it seems, everything is fine. But it's too early to rejoice, a small bummer awaits us. The fact is that the PIN code from the keyboard cannot be read in its pure form. It can only be encrypted.
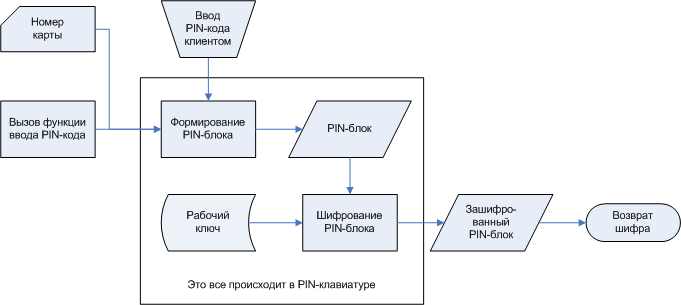
Let us make a digression, for the general development of those interested. The PIN-code in its pure form does not walk anywhere, except the keyboard itself and the special HSM device, which is in processing. The process of entering a PIN code is as follows. The software transmits the card number and the command to enter the PIN code to the keyboard. Further, in the process of entering, the keyboard returns only the fact of the keystroke, but does not indicate which one. Then the keyboard forms a construction from the two-digit length of the PIN code, the PIN code itself, then finishes up to 16 characters with the F number and makes an “exclusive” number with the right 12 digits of the card number, except for the last check digit. For example, for PIN-code 1234 and card 4987.6543.2109.8765 we take 04.1234.FFFFFFFFFF, make XOR over this with 0000.765432109876 and get 0412.42AB.CDEF.6789. And then this last number is encrypted with a working key that is already in the keyboard, and the cipher is returned to the application that ordered the PIN code entry operation.
Now let's deal with encryption keys, since we started talking about them. These keys are located in the keyboard itself and cannot be read from there. As a rule, prior to the operation of an ATM, bank security officers manually enter a so-called master key (MK) into the keyboard. Then, periodically, a special working key (WK) arrives from the processing into the ATM, encrypted with the master key, which, apart from the keyboard and the special HSM device mentioned above, nobody knows (the officers enter their own components and also do not know the full key) . Total in our keyboard sit MK and MK (WK).
Let's start a smooth approach to the climax. In fact, many different keys can be written to the keyboard. You can also feed it a PIN block, force it to decrypt it with a working key, encrypt it with another key and return the result. That is, we will never receive the key in its pure form, but please encrypt it in any key encrypted. So why don't we write down our well-known master key and not give the keyboard a command to encrypt the PIN block for them, and not for some other? And then we will decipher it, since the key is already known to us. This is exactly what our virus does.
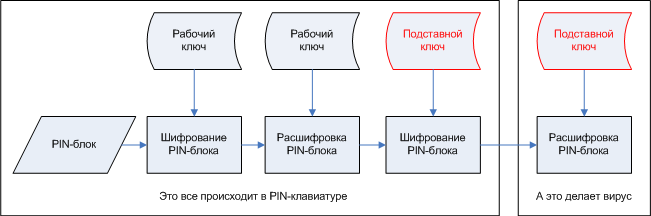
That's the whole trick, guys. Nothing complicated, right?
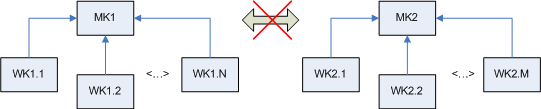
Finally tell you what's the catch. It is no coincidence that the virus was operating on Diebold ATMs. The fact is that some Diebold ATMs have installed old keyboards that do not meet modern security requirements. And modern security requirements state that keyboards in ATMs must provide a hierarchy of keys. This means that if we give the keyboard command to decrypt the PIN block with a working key, then we can encrypt it only with the master key with which the worker was encrypted. This is logical, because if we managed to load the working key, then we know this master key (we encrypted the worker) and we can be trusted. But if we ask to encrypt a PIN-block with a key from a neighboring branch, we will not be given - there are signs of evil intentions.
That's all. It was a long time, it was not necessary to write about PIN blocks, but oh well. I hope I clarified the situation a bit, and different myths and interpretations in famous circles will begin to walk less. This is especially true for large bank managers who dream of putting antiviruses on ATMs, not realizing that they will get hemorrhoids many times more than good. Normal guys have long enjoyed solutions a la Solidcore and live in peace.
Picture to attract attention:

')
Start over. A year ago, there was a panic in the media: “ATMs are viruses!”, As a result of which all self-respecting bank managers supported this panic and began to try to do something. Panic arose for good reason: there are many freebie lovers in the world, so-called carders whose purpose is to get your bank card details, including the PIN code, in order to duplicate it and withdraw all money or purchase something. For this purpose, various methods of deception are invented, but before the appearance of the virus, they were all physical. But the virus is very interesting, because it brought the technology to a new level in essence - PIN codes began to be installed at the program level. It should be noted that the virus is still able to issue cash in unlimited amounts on a special card, but we, as clients, don't care, the bank gets into the money, not us.
Now let's make a superficial excursion into the ATM itself, and see where the viruses can come from. I will reveal the secret: the vast majority of ATMs running under Windows XP. The quick-witted reader will understand that in this case there is a threat, and we must begin to be afraid. But not everything is as bad as it seems. First, bona fide suppliers of ATM software, this Windows is severely curtailed, disabling everything that is possible in it, protecting ports, closing access, and so on. And secondly, the ATM never looks directly into the Internet - it is either in a dedicated segment of the corporate network, or connected through some encryption, such as Cisco or Checkpoint, and the virus gets there, to put it mildly, without options. Accordingly, the exit here is only an insider, because from the outside it is problematic to slip something into an ATM.
And what is a typical ATM software? And that's what. The architecture of this software is similar to the client-server. The server in this case is able to work with a specific hardware (of which in an ATM in bulk) and publishes outside the program interfaces common to each type of hardware (dispenser, card reader, printer, keyboard, etc.). The client, that is, the business application itself, in turn, using these interfaces, shows us advertising, issues a long-awaited salary, prints checks and blinks joyfully with lights. All this economy is called the standard CEN / XFS. I, perhaps, will attach a picture.

Having learned this news, we immediately start writing our ATM software

Let us make a digression, for the general development of those interested. The PIN-code in its pure form does not walk anywhere, except the keyboard itself and the special HSM device, which is in processing. The process of entering a PIN code is as follows. The software transmits the card number and the command to enter the PIN code to the keyboard. Further, in the process of entering, the keyboard returns only the fact of the keystroke, but does not indicate which one. Then the keyboard forms a construction from the two-digit length of the PIN code, the PIN code itself, then finishes up to 16 characters with the F number and makes an “exclusive” number with the right 12 digits of the card number, except for the last check digit. For example, for PIN-code 1234 and card 4987.6543.2109.8765 we take 04.1234.FFFFFFFFFF, make XOR over this with 0000.765432109876 and get 0412.42AB.CDEF.6789. And then this last number is encrypted with a working key that is already in the keyboard, and the cipher is returned to the application that ordered the PIN code entry operation.
Now let's deal with encryption keys, since we started talking about them. These keys are located in the keyboard itself and cannot be read from there. As a rule, prior to the operation of an ATM, bank security officers manually enter a so-called master key (MK) into the keyboard. Then, periodically, a special working key (WK) arrives from the processing into the ATM, encrypted with the master key, which, apart from the keyboard and the special HSM device mentioned above, nobody knows (the officers enter their own components and also do not know the full key) . Total in our keyboard sit MK and MK (WK).
Let's start a smooth approach to the climax. In fact, many different keys can be written to the keyboard. You can also feed it a PIN block, force it to decrypt it with a working key, encrypt it with another key and return the result. That is, we will never receive the key in its pure form, but please encrypt it in any key encrypted. So why don't we write down our well-known master key and not give the keyboard a command to encrypt the PIN block for them, and not for some other? And then we will decipher it, since the key is already known to us. This is exactly what our virus does.

That's the whole trick, guys. Nothing complicated, right?
Finally tell you what's the catch. It is no coincidence that the virus was operating on Diebold ATMs. The fact is that some Diebold ATMs have installed old keyboards that do not meet modern security requirements. And modern security requirements state that keyboards in ATMs must provide a hierarchy of keys. This means that if we give the keyboard command to decrypt the PIN block with a working key, then we can encrypt it only with the master key with which the worker was encrypted. This is logical, because if we managed to load the working key, then we know this master key (we encrypted the worker) and we can be trusted. But if we ask to encrypt a PIN-block with a key from a neighboring branch, we will not be given - there are signs of evil intentions.

That's all. It was a long time, it was not necessary to write about PIN blocks, but oh well. I hope I clarified the situation a bit, and different myths and interpretations in famous circles will begin to walk less. This is especially true for large bank managers who dream of putting antiviruses on ATMs, not realizing that they will get hemorrhoids many times more than good. Normal guys have long enjoyed solutions a la Solidcore and live in peace.
Source: https://habr.com/ru/post/93507/
All Articles