Who is to blame or / and what to do for Dummies (about “winlockers”)
Having accumulated some experience in helping the "reckless" and summarizing it, he decided to write a brief review article on the problem of various SMS extortionists aka informers. An experienced IT person is unlikely to find something new in it, but most ordinary users will probably find something useful or just interesting for themselves in it.
Call it "Who is to blame or / and what to do for Dummies."
Handles playful ...

As practice shows, for most ordinary users, the fact that the system is infected does not cause any particular concerns - everything seems to work somehow, it slows down the system a little, and occasional errors pop up from time to time, but in general this does not prevent us from meeting our modest daily needs - to communicate in social networks, listen to music and watch a movie. So taking care of some kind of protection does not seem so important. And at that time, the infected computer worked for days on end for the benefit of DiDosers, spammers and the rest of other dishonest comrades ...
Then, at some point, the relationship changes drastically when the system is locked, and your blood-stakes are asked to unlock. Here begins the search for the culprit. And go and find it - who admits to installing a “special codec” to watch a certain video or to visit another entertainment portal?
Viewing your browsing history helps determine approximate sources of infection, but you will not expose the culprit in front of everyone. Alas, only units are directly recognized. Although just curious enough ...
')
Based on my experience of helping to get rid of the infection, I can say that you can see something like the following historical way of becoming blockers.
Not so long ago, when the banners (“Vinlock” in the future) were fairly simple and were only an add-on (BHO) for IE, the whole struggle with them was to disable this add-on itself. In principle, the problem was solved elementarily - a three-minute consultation by telephone - and everyone is happy.
Time later, "extortionists" began to appear, blocking not only IE, but also other browsers, using, say, the same JS. The first Trojans began to appear, which without the presence of an antivirus program, it was almost impossible to overcome for an ordinary user, which was confirmed by mourning the victims in the phone.
And at that time almost all programs still allowed themselves to be removed by means of a code received via SMS. Moreover, SMS were an order of magnitude less than at present.
But the phenomenon still did not lead users into indescribable horror, because only the browser was blocked. Having closed it, it was possible to forget about “troubles” and continue to do favorite things.
Later, the informers evolved and turned first from an annoying and interfering window hanging in the middle of the desktop into a real Achtung (translation from it is vile garbage extorting money), which, when the OS was loaded, blocked the entire desktop, an attempt to launch the Task Manager does not need anything resulted, in addition to the appearance of sad physiognomy on the user's face, and the locked registry and “safe mode” finally put an end to the attempt to solve the problem on their own. And although sometimes tricky tricks helped, such as repeatedly pressing the "shift", or using "win + u" and then launching the required software through the browser, over time this trick has lost its relevance.
The bollards have grown from the category of "sticker" to the category of "super-limited account." Soon, the developers of informers finally became brutalized, and even methods with changing extensions in com, pif, cmd, bat types stopped helping to launch the software - the livecd was no longer indispensable.
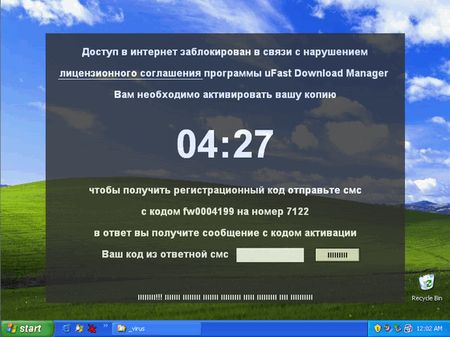
The informer, which received the most widespread in December last year - uFast Download Manager, became the apogee.
How?
If the standard launch of the antivirus for some reason did not help (the pest is either not detected, or AV does not start at all), you have to use additional utilities.
The standard set for restoring users to the system from under the most infected system is standard - here everyone knows AVZ, and not less popular HiJackThis, some programs from SysInternals, which allow you to track the activity of various subsystems, as well as, of course, the anti-virus scanners like CureIt, AntiViral Toolkit , NOD32 and other less known.
It should be noted that code generators (sort of keygens for viruses) from antivirus vendors are sometimes useful for unlocking the system, which create services that allow you to select codes to unlock the system, but recently they lose their relevance because the blockers no longer contain the unlock function itself based on the received SMS code - they are simply not designed for it.
A couple of useful references are listed below, it can be useful:
The penultimate page even has a futuristic flash design in order to emphasize the importance and uniqueness of the project, I suppose.
It should also be noted that, sometimes on the forums there are algorithms for manual selection of the code. Sometimes it helps, it happens not. It is necessary to try.
Some of the victims turn to their operator, who gives unlock codes, again, if the informer supports this function.
Taken as a pest search, in the first place (after a failed / unsuccessful scan with antivirus tools, which I will not describe because of its simplicity), you should take AVZ Oleg Zaitsev. The program has a truly broad capabilities. You can download it from the website of the author z-oleg.com .
AVZ allows you to detect malicious files and remove them from the system by analyzing the operation of files, and a large number of heuristic firmware, a large database of signatures, neuroanalyzers, troubleshooting programs, a large number of auxiliary routines are supported. Moreover, if there is an advanced pest in the system that does not allow the program to be started, then you can use the launch from the console with the key ag = y.
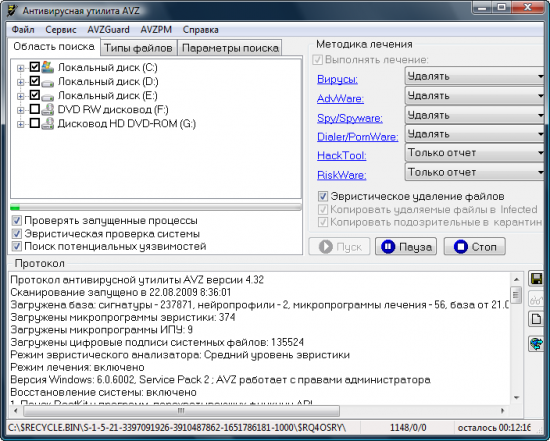
At the same time, AVZGuard (a driver that delimits the access of running applications to the system) starts up in the system, which prevents the program from closing (if the console does not start, you can try to create a bat-file). And then add to the trusted applications you need the program and continue to clean the system. And in case of need to reboot to prevent re-infection, it is recommended not to unload AVZGuard, but to reboot with it. This technique helps to get rid of a lot of problems. A reset of various system locks helps to get rid of the effects of pests. For example, a frequent victim is a network stack, the damage of which leads to disruption of the network. With this utility you can restore the integrity of the stack. (It should be noted that it can often be restored on your own, using the netsh winsock reset command. You can read more here support.microsoft.com/kb/817571 and here support.microsoft.com/kb/811259 ).
Under AVZ, there are already ready-made scripts (which the user can write himself) helping to get rid of certain types of pests. By the way, on the website virusinfo.info, experts can also help with solving a problem after you provide them with a log collected after analyzing the system.
It should be noted a number of small, but extremely useful utilitok from the company SysInternals, now bought by Microsoft, without which it is extremely difficult to do, using the "manual" method of searching for pests.
Using the ProcessMonitor utility, you can use the convenient “Include Process from window” function, specify the element of interest on the screen (for example, a banner) and find the process on which it hangs. Then it can be analyzed by the database of safe AVZ files and identify a potential intruder.
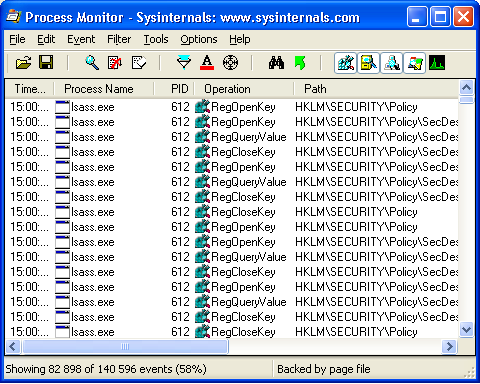
It also allows real-time tracking of changes in the file system and registry.
Processes affecting network activity are also visible in real time.
With Autoruns and Sigcheck, you can verify the digital signatures of files and sort them as safe.
An excellent scanner from Dr.Web in beta has got a special interface to counteract programs that block the launch of the anti-virus scanners themselves. First, it activates protected mode, then loads all other services. Sometimes it is the most effective option.
Another well-known program HiJackThis allows you to find suspicious objects in autorun, keys in the registry, as well as delete them later.
In addition, you can use the service, such as www.hijackthis.de/en , where you can download a log, you can get a beautiful report on the likely danger of a particular file or record.
And in order to finally make sure that the file is “unclean”, the file can be downloaded at www.virustotal.com , where you will learn about the subject’s fame in particularly “narrow” circles.
In any case, always after treatment / reinstallation, change the passwords stored on the computer. For stealing.
What to do?
When ensuring security, you should always keep a balance - to provide more or less reliable protection and not to put the user in a straitjacket (although it would be necessary).
The safest option is to change the OS to a less traditional one. However, not all are satisfied for a number of well-known reasons.
An effective antivirus with up-to-date databases, coupled with an updated OS - great increases the chances of not picking up something, but as practice shows, this is not enough for users with long hands. Climb to where it is necessary and not necessary, and at the same time do not confess.
Various firewalls did not find love with the average user due to the need for constant monitoring. And since sometimes there is not enough knowledge to make decisions, even the user who uses the firewall either blocks the necessary process, which often leads to the loss of the network and disruption of the programs, or vice versa - allows the malicious code. The most favorite thing is to block everything and delete the program, as "interfering" ...
Alas, most often it happens.
Of course, it is recommended to use a non-standard browser due to its inferiority and binding to the system kernel.
The weakest link is the pad between the chair and the PC. So to strengthen the link - hands should be shortened (c) Popular wisdom.

One of the most effective measures is to limit the rights of the user in the system itself, however, most often users are too lazy to spend time creating a separate account. And a number of programs refuse to be installed, configured, or simply run under limited profiles.
In this case, the well-known utility DropMyRights will be useful, limiting the rights of the application being launched.
It supports 3 access levels. The lower the rights, the lower the possibilities of the program. Let's say for the same IE at the lowest such functions are not available, say, as active-x.
This method has proven itself well with clients from the “high risk” group. And although some of the sites are not displayed correctly, for the sake of security, this moment can be neglected.
As an option, also use programs that do a full rollback of the system after the end of the session, but they, as practice shows, are not very suitable for home use.
And although recently there has been a sharp decline in the activity of the Winlockers, it is likely that in the near future we can still expect new, varied modifications of various types of ransomware, and therefore new epidemics. Ensuring complete security without pulling the user's hands behind his back is impossible and until the user, taught by bitter experience, listens to the advice of his more experienced counterparts, and millions of infected computers will work to the detriment, and hundreds of millions of rubles will go to the pocket of virus writers.
And the problem must be solved, most likely, in a complex way:

Well, on your part I am glad to hear your wishes, criticism and just share your experience.
Call it "Who is to blame or / and what to do for Dummies."
Handles playful ...

As practice shows, for most ordinary users, the fact that the system is infected does not cause any particular concerns - everything seems to work somehow, it slows down the system a little, and occasional errors pop up from time to time, but in general this does not prevent us from meeting our modest daily needs - to communicate in social networks, listen to music and watch a movie. So taking care of some kind of protection does not seem so important. And at that time, the infected computer worked for days on end for the benefit of DiDosers, spammers and the rest of other dishonest comrades ...
Then, at some point, the relationship changes drastically when the system is locked, and your blood-stakes are asked to unlock. Here begins the search for the culprit. And go and find it - who admits to installing a “special codec” to watch a certain video or to visit another entertainment portal?
Viewing your browsing history helps determine approximate sources of infection, but you will not expose the culprit in front of everyone. Alas, only units are directly recognized. Although just curious enough ...
')
Based on my experience of helping to get rid of the infection, I can say that you can see something like the following historical way of becoming blockers.
Not so long ago, when the banners (“Vinlock” in the future) were fairly simple and were only an add-on (BHO) for IE, the whole struggle with them was to disable this add-on itself. In principle, the problem was solved elementarily - a three-minute consultation by telephone - and everyone is happy.
Time later, "extortionists" began to appear, blocking not only IE, but also other browsers, using, say, the same JS. The first Trojans began to appear, which without the presence of an antivirus program, it was almost impossible to overcome for an ordinary user, which was confirmed by mourning the victims in the phone.
And at that time almost all programs still allowed themselves to be removed by means of a code received via SMS. Moreover, SMS were an order of magnitude less than at present.
But the phenomenon still did not lead users into indescribable horror, because only the browser was blocked. Having closed it, it was possible to forget about “troubles” and continue to do favorite things.
Later, the informers evolved and turned first from an annoying and interfering window hanging in the middle of the desktop into a real Achtung (translation from it is vile garbage extorting money), which, when the OS was loaded, blocked the entire desktop, an attempt to launch the Task Manager does not need anything resulted, in addition to the appearance of sad physiognomy on the user's face, and the locked registry and “safe mode” finally put an end to the attempt to solve the problem on their own. And although sometimes tricky tricks helped, such as repeatedly pressing the "shift", or using "win + u" and then launching the required software through the browser, over time this trick has lost its relevance.
The bollards have grown from the category of "sticker" to the category of "super-limited account." Soon, the developers of informers finally became brutalized, and even methods with changing extensions in com, pif, cmd, bat types stopped helping to launch the software - the livecd was no longer indispensable.

The informer, which received the most widespread in December last year - uFast Download Manager, became the apogee.
How?
If the standard launch of the antivirus for some reason did not help (the pest is either not detected, or AV does not start at all), you have to use additional utilities.
The standard set for restoring users to the system from under the most infected system is standard - here everyone knows AVZ, and not less popular HiJackThis, some programs from SysInternals, which allow you to track the activity of various subsystems, as well as, of course, the anti-virus scanners like CureIt, AntiViral Toolkit , NOD32 and other less known.
It should be noted that code generators (sort of keygens for viruses) from antivirus vendors are sometimes useful for unlocking the system, which create services that allow you to select codes to unlock the system, but recently they lose their relevance because the blockers no longer contain the unlock function itself based on the received SMS code - they are simply not designed for it.
A couple of useful references are listed below, it can be useful:
- support.kaspersky.ru/viruses/deblocker - unlocker from Kaspersky.
- esetnod32.ru/support/winlock.php - Nod32
- www.drweb.com/unlocker - the same from Dr.Web.
- www.drweb.com/unlocker/mobile - and the mobile version of the service.
- virusinfo.info/deblocker - deactivation from Virusinfo.
The penultimate page even has a futuristic flash design in order to emphasize the importance and uniqueness of the project, I suppose.

It should also be noted that, sometimes on the forums there are algorithms for manual selection of the code. Sometimes it helps, it happens not. It is necessary to try.
Some of the victims turn to their operator, who gives unlock codes, again, if the informer supports this function.
Taken as a pest search, in the first place (after a failed / unsuccessful scan with antivirus tools, which I will not describe because of its simplicity), you should take AVZ Oleg Zaitsev. The program has a truly broad capabilities. You can download it from the website of the author z-oleg.com .
AVZ allows you to detect malicious files and remove them from the system by analyzing the operation of files, and a large number of heuristic firmware, a large database of signatures, neuroanalyzers, troubleshooting programs, a large number of auxiliary routines are supported. Moreover, if there is an advanced pest in the system that does not allow the program to be started, then you can use the launch from the console with the key ag = y.

At the same time, AVZGuard (a driver that delimits the access of running applications to the system) starts up in the system, which prevents the program from closing (if the console does not start, you can try to create a bat-file). And then add to the trusted applications you need the program and continue to clean the system. And in case of need to reboot to prevent re-infection, it is recommended not to unload AVZGuard, but to reboot with it. This technique helps to get rid of a lot of problems. A reset of various system locks helps to get rid of the effects of pests. For example, a frequent victim is a network stack, the damage of which leads to disruption of the network. With this utility you can restore the integrity of the stack. (It should be noted that it can often be restored on your own, using the netsh winsock reset command. You can read more here support.microsoft.com/kb/817571 and here support.microsoft.com/kb/811259 ).
Under AVZ, there are already ready-made scripts (which the user can write himself) helping to get rid of certain types of pests. By the way, on the website virusinfo.info, experts can also help with solving a problem after you provide them with a log collected after analyzing the system.
It should be noted a number of small, but extremely useful utilitok from the company SysInternals, now bought by Microsoft, without which it is extremely difficult to do, using the "manual" method of searching for pests.
Using the ProcessMonitor utility, you can use the convenient “Include Process from window” function, specify the element of interest on the screen (for example, a banner) and find the process on which it hangs. Then it can be analyzed by the database of safe AVZ files and identify a potential intruder.

It also allows real-time tracking of changes in the file system and registry.
Processes affecting network activity are also visible in real time.
With Autoruns and Sigcheck, you can verify the digital signatures of files and sort them as safe.
An excellent scanner from Dr.Web in beta has got a special interface to counteract programs that block the launch of the anti-virus scanners themselves. First, it activates protected mode, then loads all other services. Sometimes it is the most effective option.
Another well-known program HiJackThis allows you to find suspicious objects in autorun, keys in the registry, as well as delete them later.
In addition, you can use the service, such as www.hijackthis.de/en , where you can download a log, you can get a beautiful report on the likely danger of a particular file or record.
And in order to finally make sure that the file is “unclean”, the file can be downloaded at www.virustotal.com , where you will learn about the subject’s fame in particularly “narrow” circles.
In any case, always after treatment / reinstallation, change the passwords stored on the computer. For stealing.
What to do?
When ensuring security, you should always keep a balance - to provide more or less reliable protection and not to put the user in a straitjacket (although it would be necessary).
The safest option is to change the OS to a less traditional one. However, not all are satisfied for a number of well-known reasons.
An effective antivirus with up-to-date databases, coupled with an updated OS - great increases the chances of not picking up something, but as practice shows, this is not enough for users with long hands. Climb to where it is necessary and not necessary, and at the same time do not confess.
Various firewalls did not find love with the average user due to the need for constant monitoring. And since sometimes there is not enough knowledge to make decisions, even the user who uses the firewall either blocks the necessary process, which often leads to the loss of the network and disruption of the programs, or vice versa - allows the malicious code. The most favorite thing is to block everything and delete the program, as "interfering" ...
Alas, most often it happens.
Of course, it is recommended to use a non-standard browser due to its inferiority and binding to the system kernel.
The weakest link is the pad between the chair and the PC. So to strengthen the link - hands should be shortened (c) Popular wisdom.

One of the most effective measures is to limit the rights of the user in the system itself, however, most often users are too lazy to spend time creating a separate account. And a number of programs refuse to be installed, configured, or simply run under limited profiles.
In this case, the well-known utility DropMyRights will be useful, limiting the rights of the application being launched.
It supports 3 access levels. The lower the rights, the lower the possibilities of the program. Let's say for the same IE at the lowest such functions are not available, say, as active-x.
This method has proven itself well with clients from the “high risk” group. And although some of the sites are not displayed correctly, for the sake of security, this moment can be neglected.
As an option, also use programs that do a full rollback of the system after the end of the session, but they, as practice shows, are not very suitable for home use.
And although recently there has been a sharp decline in the activity of the Winlockers, it is likely that in the near future we can still expect new, varied modifications of various types of ransomware, and therefore new epidemics. Ensuring complete security without pulling the user's hands behind his back is impossible and until the user, taught by bitter experience, listens to the advice of his more experienced counterparts, and millions of infected computers will work to the detriment, and hundreds of millions of rubles will go to the pocket of virus writers.
And the problem must be solved, most likely, in a complex way:
- AV software developers to improve their products;
- Users to be more educated and less “curious”;
- Providers to deploy services that allow you to make the network more secure;
- Aggregators complicate the procedure for registering rooms for all sorts of crooks;
- And the security authorities are more specifically to take on fraudsters and conduct explanatory moral and cultural conversations with them, so that they should think again and do not repay those who are disagreeable ...

Well, on your part I am glad to hear your wishes, criticism and just share your experience.
Source: https://habr.com/ru/post/93152/
All Articles