We pull out a bunch of passwords from peer-to-peer networks
 There was this idea for a long time - ever since when I learned about wand.dat. Until recently, all did not reach the hands.
There was this idea for a long time - ever since when I learned about wand.dat. Until recently, all did not reach the hands.So what do we have
- Opera browser. It stores all memorized passwords from sites in the open file wand.dat. True in the open only if it is not worth the master password, which of course no one puts. What made the developers save passwords in an unencrypted form, if there is no master password? Unknown. It would be logical to forcefully not save passwords at all until the user sets the master password.
- Direct Connect. "Partially Centralized File Sharing (P2P) Network." A user shares folders / files on his computer, enters hubs, downloads / distributes. Search works within connected hubs. The uniqueness of the files is determined by Tiger Tree Hashing. People who have nothing to share (many hubs are not allowed without balls at a minimum of 10-15 GB), share Program Files, Windows, and others like them.
- / dev / hands . Well, without this in any way.
What was the idea: to write a bot sitting on hubs and regularly searching and swinging wand.dat. I wrote a program on your favorite Delphi.
Actually, the algorithm of the bot:
- The bot scans the folder for the saved files, enumerates the files by the specified name pattern, saves the TTH files (the TTH removal module for Delphi is written by MetalFan and taken from here ) in memory. At the same time, a batch script is created to process all existing wands in one double click. For example, this is used as a parser.
- A pre-prepared list of hubs in the format "one line - one hub." For each hub, a separate thread is created.
- Where to get a list of hubs? The bz2-file with hubs is downloaded , unpacked, parsed with anything you like (below is an example of a parser in php).
- Go to the hub. We are looking for wand.dat size of at least kilobyte. Repeat the search every 20 minutes.
- We download every wand.dat found if there is no such TTH in the internal database of the program. We save in the folder to the rest. Add a TTH of the new file to your list, update the batch script to handle the inflated.
- When you get tired of downloading, turn off the bot, run the script, we get one final file with all the passwords
Well, the parser list of hubs in php here:
<? php
header( 'Content-type: text/plain' );
$f_name = './hublist.xml' ;
$f =fopen( $f_name , 'r' );
$buf =fread( $f ,filesize( $f_name ));
fclose( $f );
preg_match_all( '|address="dchub://([a-z0-9:.-]+?)"|i' , $buf , $a ); #-, ,
$f =fopen( './hublist.txt' , 'w ' );
for ( $i =0; $i <count( $a [ 1 ]); $i ++){fwrite( $f , $a [ 1 ][ $i ]. "\r\n" );}
fclose( $f );
echo 'done ' .count( $a [ 1 ]);
?>If necessary, the pattern can be corrected, for example, on exclusively .ru-hubs.
')
Test
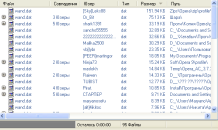
I tested the program from April 25 to April 28, 2010. During this time, 232 wand.dat has been pumped. The fattest was 129 kilobytes. What found in these vandah? I did not even open them , because it is already not good. Yes, and no passwords from contact were the goal. The purpose of writing a bot was to check for the difficulty of automating the stealing of passwords lying in a prominent place unattended.What to do with inflated wealth
And what could be in these vands?- First, a list of valid email addresses. Can be used for spam. (In fact, the cost of extracting them in this way does not pay off at all; it’s easier to use MailAgent’s built-in search).
- Passwords from all contacts / classmates / Facebook - values for hackers no.
- Access to ftp sites is more dangerous - from the inscription "Haxored by xakep Vasya666" to an exploit on the main hacker, only a fiction separates.
- List of mail accounts with passwords. In my opinion, this is the most dangerous. Mail, as we all know, no one deletes from the servers.
- Passwords from the accounts of your provider. The truth for such a provider will definitely punish you. A cruel oh-oko will punish.
Result
Passwords A lot of passwords for a fairly small period of time with minimal one-time effort.Conclusion
Conclusion? What else could be the new conclusion? Again, remind you that you need to put master passwords on browsers, if you save passwords in a browser? To remind you to keep track of what you share? BUT WHY?! Nobody will listen to this anyway. Just do not cry when the roasted rooster pecks in one place.Source: https://habr.com/ru/post/92343/
All Articles