Difficult password does not need to be remembered
All passwords for different resources should be long, complex, personal and not similar.

But how to come up with so many different passwords? Suppose we have found on the vast expanses of the Internet we need a program that generates the number of characters we need. But how to remember all this riot of letters, numbers, punctuation marks, and not afraid to utter this phrase, not at all understandable characters in the form of emoticons, arrows, houses and Chinese characters? And how not to confuse some “unreadability” from which site?
')
I can not remember exactly. I even forget the four-digit PINs of plastic cards the next day. It is possible to write down passwords and at the most necessary moment to lose everything that has accumulated over many years. And if you have paranoia? You also have to put your cipher-notebooks in a bank cell. But you will forget the next password from the next armored door almost immediately.
And what if there is a way to not invent, not memorize and not write down the keys to our secrets? I suggest a way to invent such passwords.
We need only three things.
1. "Magic" plate (about it further) with the help of which we will create passwords,
2. Individual key phrase,
3. The name of the resource for which we will create a password.
And nothing more. Intrigued?
To begin, I will present you the "magic" table. This is a key element of this method of inventing passwords. Immediately, I note that this is not my invention. At school I encrypted my secret records using such a table. I just modified it a bit.
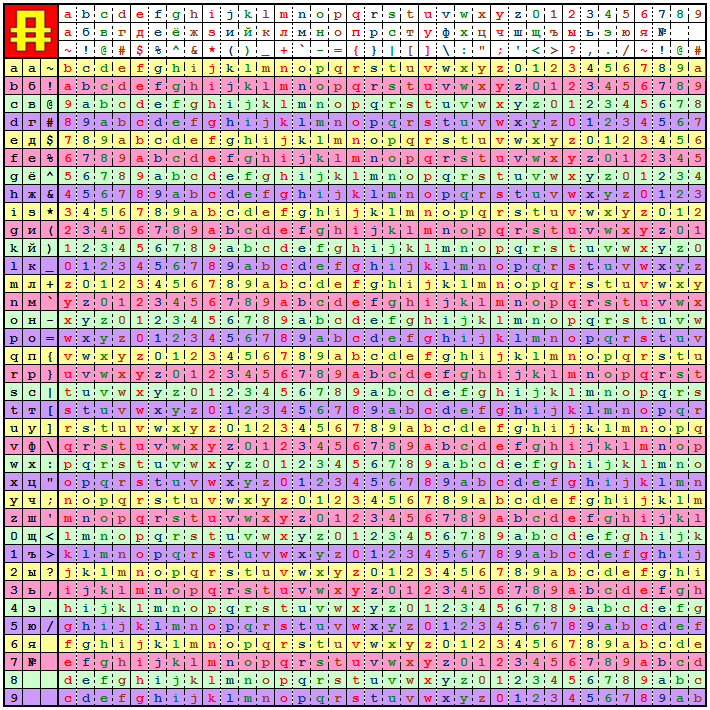
Yes, and not so magical. In the three left columns (left field) are non-repeating characters. In a large square field (main field), Latin characters and numbers are periodically repeated horizontally and vertically. In the top three lines (top field) any characters, it is from them that passwords will be obtained.
Well, we have a table. It remains to come up with a key phrase and find a resource to which we will come up with a password. Let the first be the word password , and the second - mysite . The password will come up with sixteen characters. Go.
Take the first letter of the key phrase ( p ) and find it in the left margin. Found? Now in the same line in the main field, find the first letter of the resource name ( m ). Also found? Climb up the column and find the first character of our password (number 0 ). And then repeat the same for each subsequent pair of characters. Did the word run out of letters? Do not worry, start from the beginning of the word. You will see the result in table 1.1.

Not bad. There are even numbers in the password.
How the result of making a password for Habrahabr will look is visible in table 1.2. We changed only the resource name ( habrahabr ), and the password has changed.

I know that there are willing to see in the password capital letters and punctuation marks. Let's draw them.
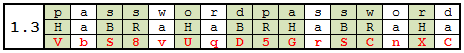
The word HaBRaHaBR has consonants. Have you noticed too? Then let's replace the letters with capital letters in the same positions of the password. The result is in table 1.3.
Now let's replace the password characters 4, 8 and 16 with punctuation marks (table 1.4), for this they are needed in the upper field of the “magic” plate.

I want to note that if the number of characters in the key phrase and in the name of the resource is the same, then the characters of the password will start to repeat. To avoid this, you can, for example, add letters to the resource name. For example, so habrahabr + dobivka = habrahabrdobivka (table 1.5).

As a key phrase, you can use whatever you want. Even a quadratic equation will do (table 1.6).

You can use your favorite character from a children's book (table 1.7)

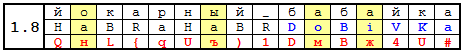
And for variety, you can insert Cyrillic characters into the password. In Table 1.8, they are inserted where and in the key phrase and in the name of the resource are vowels.
While preparing materials for publication came up with another way to use this method. The fact is that I am also annoyed with test questions in password recovery systems. Who else besides you knows your mother's maiden name? I think everything. Here you have another weak point in security. Your mother will not be offended if you encrypt her name? Then you can safely use the principle from table 1.9.

If everyone uses the same "magic" table, then I think it will not be good. Here is another one.

What is it different? The left margin is the same. In the central field, I changed the sequence of characters. And the top field was arranged by Russian and Latin characters not quite in alphabetical order.
In general, you can create your table by following four simple rules.
1. You must remember by what principle you make a table.
2. In the left field the characters should not be repeated.
3. In the main field, characters should not be repeated in columns and rows.
4. In the upper field, you can place any characters in any order.
And now we will try to create a password with a key phrase and the name of the resource from our first example, but already using the second code table. What happened can be seen in table 2.1. Feel the difference.

And in order that you could create a personal table with less effort, here I posted the source in .xls format.
Suppose you went to your favorite Habrahabr, Vkontakte or to the site where in all details and with pictures it is told how to use the cabbage in which children are found and trying to remember the password? And the password is not necessary to remember. It generally can not remember. How is this possible?
1. You have compiled a personal encryption table according to a principle that you understand and understand. Then even her loss will not be a big problem. Restore it.
2. You remember your personal key phrase. But you remember the number π to the fourteenth decimal place.
3. You are sane and well aware of which site you have visited.
This is all you need. Create a password again, it will be exactly the same.
Does this phrase annoy you too? Even enrages? As I understand you. It is necessary to make as many extra gestures. What if…
You have a key phrase. And your “forgetful co-workers” have a personnel number or login. Let's use it for its intended purpose.

Do your work rules require you to change your password once a month? More often? Then, under the same conditions, change the key phrase and re-create the passwords.

And of course, no one will forbid you to automate the process.
I understand that using a piece of paper and even a picture of the encryption table on a computer is not very convenient. Therefore , I have a request . If you like the idea and you can create an application for a PC, phone, smartphone or communicator, then go ahead. I myself am not local, my hands are not sharpened ...
Thanks, iFaTaL1Ty , for the link to Habrahabr with a similar idea.
Thanks, VasyaMobile , for almost the same idea from Yandex.
Thank you very much, jursovet . Here is not only a similar idea, but also a practical way to implement it.
Transferred to the thematic blog.
A topic on Habrahabr where critical comments are made to this method of inventing passwords. And this is my response to criticism.
I quote my comment :
rbJJkjwqmIyLm7er is the password for the site mojdomen. Recover the key phrase, and I confess that I am an idiot.

But how to come up with so many different passwords? Suppose we have found on the vast expanses of the Internet we need a program that generates the number of characters we need. But how to remember all this riot of letters, numbers, punctuation marks, and not afraid to utter this phrase, not at all understandable characters in the form of emoticons, arrows, houses and Chinese characters? And how not to confuse some “unreadability” from which site?
')
I can not remember exactly. I even forget the four-digit PINs of plastic cards the next day. It is possible to write down passwords and at the most necessary moment to lose everything that has accumulated over many years. And if you have paranoia? You also have to put your cipher-notebooks in a bank cell. But you will forget the next password from the next armored door almost immediately.
And what if there is a way to not invent, not memorize and not write down the keys to our secrets? I suggest a way to invent such passwords.
We need only three things.
1. "Magic" plate (about it further) with the help of which we will create passwords,
2. Individual key phrase,
3. The name of the resource for which we will create a password.
And nothing more. Intrigued?
Magic table
To begin, I will present you the "magic" table. This is a key element of this method of inventing passwords. Immediately, I note that this is not my invention. At school I encrypted my secret records using such a table. I just modified it a bit.

Yes, and not so magical. In the three left columns (left field) are non-repeating characters. In a large square field (main field), Latin characters and numbers are periodically repeated horizontally and vertically. In the top three lines (top field) any characters, it is from them that passwords will be obtained.
Well, we have a table. It remains to come up with a key phrase and find a resource to which we will come up with a password. Let the first be the word password , and the second - mysite . The password will come up with sixteen characters. Go.
Password creation
Take the first letter of the key phrase ( p ) and find it in the left margin. Found? Now in the same line in the main field, find the first letter of the resource name ( m ). Also found? Climb up the column and find the first character of our password (number 0 ). And then repeat the same for each subsequent pair of characters. Did the word run out of letters? Do not worry, start from the beginning of the word. You will see the result in table 1.1.

Not bad. There are even numbers in the password.
How the result of making a password for Habrahabr will look is visible in table 1.2. We changed only the resource name ( habrahabr ), and the password has changed.

I know that there are willing to see in the password capital letters and punctuation marks. Let's draw them.
The word HaBRaHaBR has consonants. Have you noticed too? Then let's replace the letters with capital letters in the same positions of the password. The result is in table 1.3.

Now let's replace the password characters 4, 8 and 16 with punctuation marks (table 1.4), for this they are needed in the upper field of the “magic” plate.

I want to note that if the number of characters in the key phrase and in the name of the resource is the same, then the characters of the password will start to repeat. To avoid this, you can, for example, add letters to the resource name. For example, so habrahabr + dobivka = habrahabrdobivka (table 1.5).

As a key phrase, you can use whatever you want. Even a quadratic equation will do (table 1.6).

You can use your favorite character from a children's book (table 1.7)

And for variety, you can insert Cyrillic characters into the password. In Table 1.8, they are inserted where and in the key phrase and in the name of the resource are vowels.

While preparing materials for publication came up with another way to use this method. The fact is that I am also annoyed with test questions in password recovery systems. Who else besides you knows your mother's maiden name? I think everything. Here you have another weak point in security. Your mother will not be offended if you encrypt her name? Then you can safely use the principle from table 1.9.

Create your "magic" table
If everyone uses the same "magic" table, then I think it will not be good. Here is another one.

What is it different? The left margin is the same. In the central field, I changed the sequence of characters. And the top field was arranged by Russian and Latin characters not quite in alphabetical order.
In general, you can create your table by following four simple rules.
1. You must remember by what principle you make a table.
2. In the left field the characters should not be repeated.
3. In the main field, characters should not be repeated in columns and rows.
4. In the upper field, you can place any characters in any order.
And now we will try to create a password with a key phrase and the name of the resource from our first example, but already using the second code table. What happened can be seen in table 2.1. Feel the difference.

And in order that you could create a personal table with less effort, here I posted the source in .xls format.
"Remembering" the password
Suppose you went to your favorite Habrahabr, Vkontakte or to the site where in all details and with pictures it is told how to use the cabbage in which children are found and trying to remember the password? And the password is not necessary to remember. It generally can not remember. How is this possible?
1. You have compiled a personal encryption table according to a principle that you understand and understand. Then even her loss will not be a big problem. Restore it.
2. You remember your personal key phrase. But you remember the number π to the fourteenth decimal place.
3. You are sane and well aware of which site you have visited.
This is all you need. Create a password again, it will be exactly the same.
"Seryenka, and again I forgot the password from corporate soap"
Does this phrase annoy you too? Even enrages? As I understand you. It is necessary to make as many extra gestures. What if…
You have a key phrase. And your “forgetful co-workers” have a personnel number or login. Let's use it for its intended purpose.

Do your work rules require you to change your password once a month? More often? Then, under the same conditions, change the key phrase and re-create the passwords.

And of course, no one will forbid you to automate the process.
Instead of an epilogue
I understand that using a piece of paper and even a picture of the encryption table on a computer is not very convenient. Therefore , I have a request . If you like the idea and you can create an application for a PC, phone, smartphone or communicator, then go ahead. I myself am not local, my hands are not sharpened ...
PS I know that the keyword is in English keyword. I used the word password specifically to confuse the special services of all countries, times and peoples.
Updated after publication
Thanks, iFaTaL1Ty , for the link to Habrahabr with a similar idea.
Thanks, VasyaMobile , for almost the same idea from Yandex.
Thank you very much, jursovet . Here is not only a similar idea, but also a practical way to implement it.
Transferred to the thematic blog.
Critical remarks
A topic on Habrahabr where critical comments are made to this method of inventing passwords. And this is my response to criticism.
I quote my comment :
rbJJkjwqmIyLm7er is the password for the site mojdomen. Recover the key phrase, and I confess that I am an idiot.
Source: https://habr.com/ru/post/92033/
All Articles