Wardriving in Mac OS X

The de facto standard in wardriving is usually considered the Linux system (modified drivers, Kismet in conjunction with aircrack-ng ). But few people know that the poppy has powerful tools for
UPD: The tools described in the article are now obsolete. Linux recommended
To familiarize yourself with the general concepts of wardriving, it is recommended to read this article.
')
Kismac - Powerful all-in-one program. A big advantage over Linux is that the wi-fi card drivers are integrated directly into the program and there is no need to install additional modules. All network scanning, collecting and analyzing traffic (in Linux, the commands airdump, airmon, airplay) are performed in one place from the graphical interface, which greatly simplifies the process.
Program features:
- passive scanner / sniffer
- packet injection
dumping in standard PCAP format, understandable for all packet analyzers (for example, Wireshrak )- with GPS module can mark found networks on the map
- sound indication of signal strength (as a metal detector)
- dump from kismet drone server
Kismac also has tools for decoding WEP / WPA algorithms, but the program's authors say that they have not been developed for a long time and recommend using the latest version of aircrack-ng, which can be installed from source or using the port fink system .
Choice of equipment
The Airport Extreme card built into the MacBook is not suitable for wardding. It cannot inject packets, and because of the low sensitivity of the receiver, it is necessary to collect traffic for analysis in close proximity to the source of the signal. The only thing for which it is suitable is the initial inspection of networks: you can find out the type of encryption used, the presence of clients at points, etc.
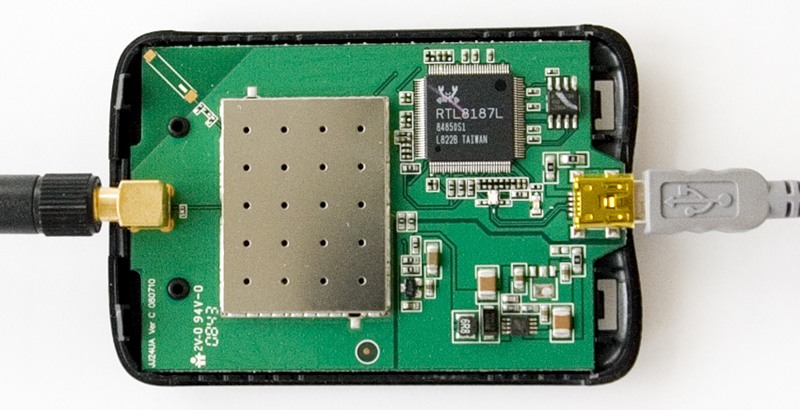
For more in-depth study, a map is needed that supports packet injection (see the list of devices ). The best choice would be the Alfa AWUS036H card on the RTL8187L chipset. It is recommended by the developers of kismac and aircrack-ng. Supported by all software programs in all operating systems, it has a very sensitive receiver. The power transmission is 500 milliwatts. Equipped with RP-SMA plug for connecting external antennas.
The Chinese make these cards under different names, for example G-SKY or IDU-2850UG-8G or Kinmax .
In principle, you can choose any of the supported cards, but this one has the best characteristics, it is cheap and easy to find.
To get started, you need to select a driver for your device:
KisMac => Preferences ... => Driver
To get acquainted with the program and in the absence of other cards, select Airport Extreme Passive mode.
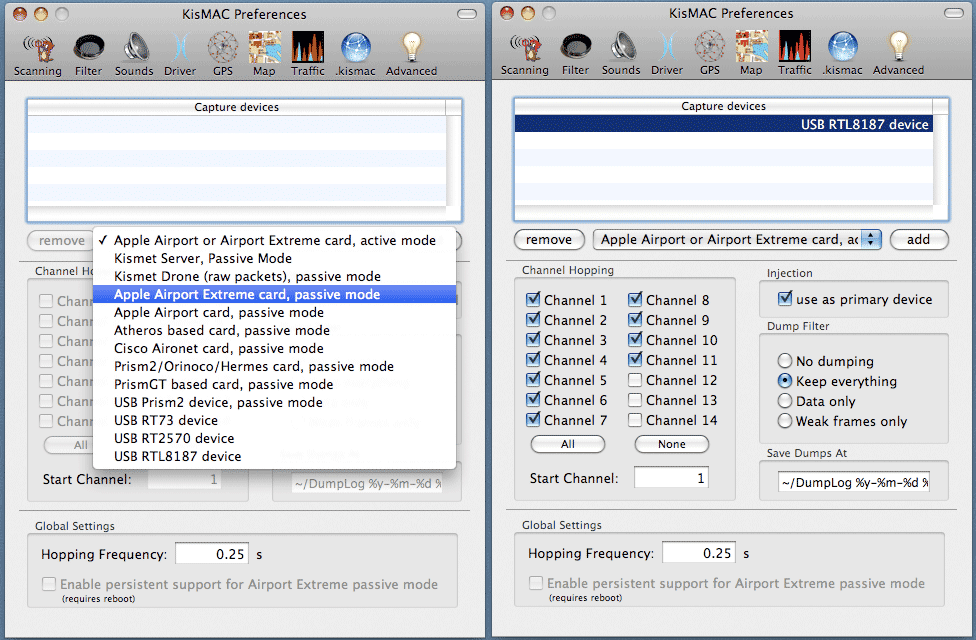
Channel Hopping - select all European channels 1-11.
Use as primary device - to activate the package injection function (not possible at the Airport)
Dump Filter - what data to write to the dump file, select "Keep everything".
Save Dumps At - path and name of the dump file.
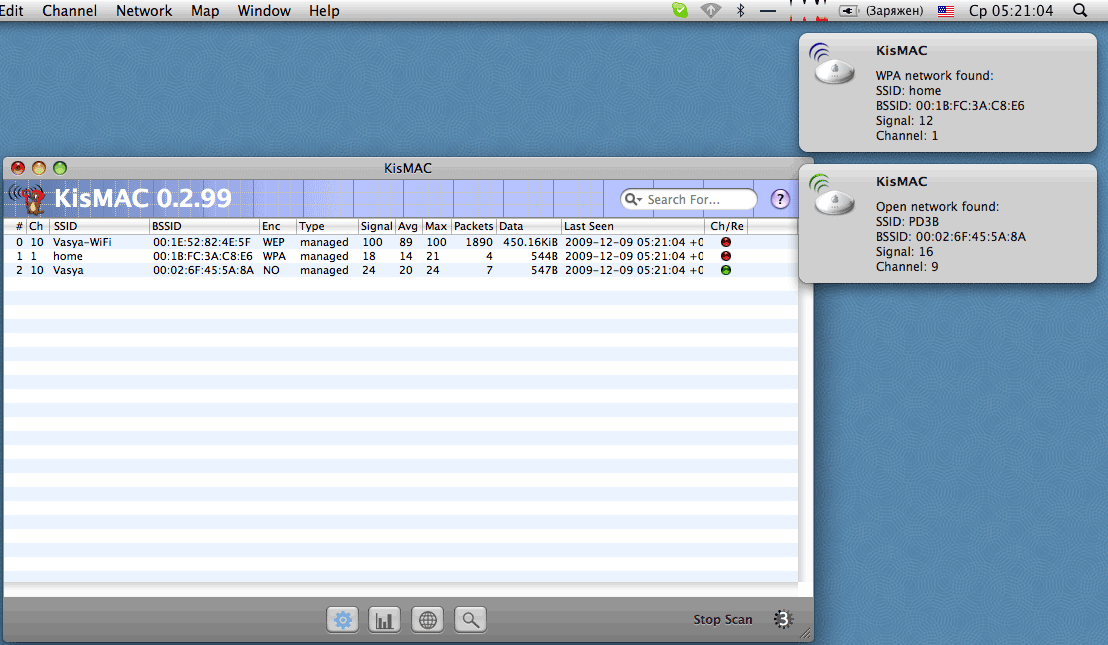
Now you can start scanning. The program will report on all found networks. Changing numbers in the lower right corner means that the device is in Channel Hopping mode, jumping on frequencies to find networks running on all channels. It is also necessary to keep in mind that the card jumps through the channels very quickly (the speed is adjusted when the driver is selected), so there is a possibility that some networks may not be detected. To eliminate this, you can go through each channel separately. When you have selected the network of interest, you must stop Channel hopping and set the channel on which the selected network is running.
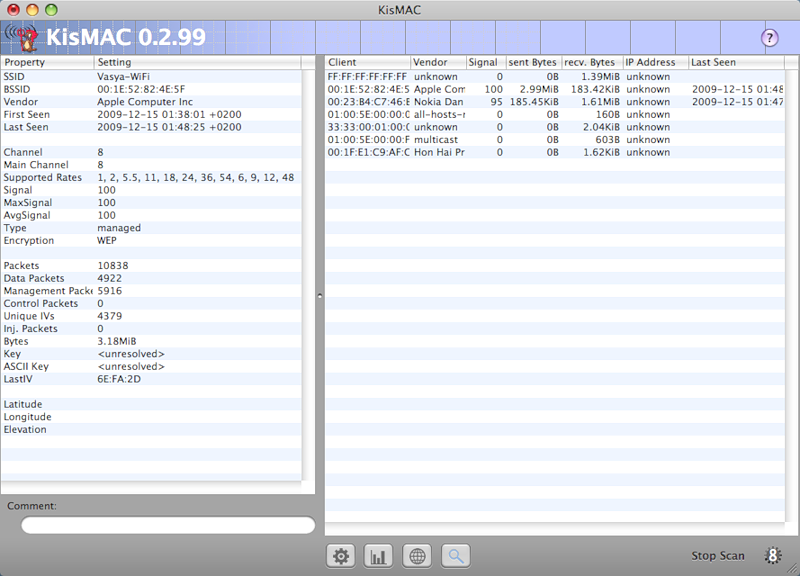
Double-clicking on the selected network will show detailed information.
On the left - technical information, on the right - a list of clients connected to a point. Really connected clients have Last Seen value.
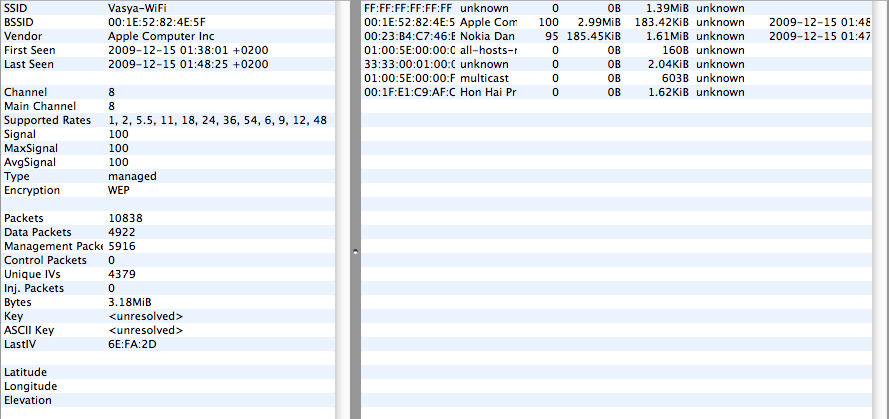
An important factor is the signal level.
Signal - signal power
AvgSignal - signal quality (useful signal considering interference)
MaxSignal - the maximum recorded signal level
For successful packet injection, the signal point and the client signal must not be lower than 40-50. It is necessary to find the optimal position of the antenna at which the signal will be at its maximum. Sometimes changing the position by even one centimeter can significantly affect the signal level. You can also turn on the sound indication of the signal strength in the “Network => Monitor Signal Strenght” menu, depending on the signal level, the tone of the sound will change.
Sniffing in open networks
On networks without encryption, all traffic can be freely viewed. To do this, simply configure the card to listen to the frequency on which the network is running (Main channel), and collect all traffic into a file. Then the dump can be viewed with a packet analyzer.
For example, at the next table in the cafe Vasya! * SuPeR-ViP *! Pupkin logged in contact:
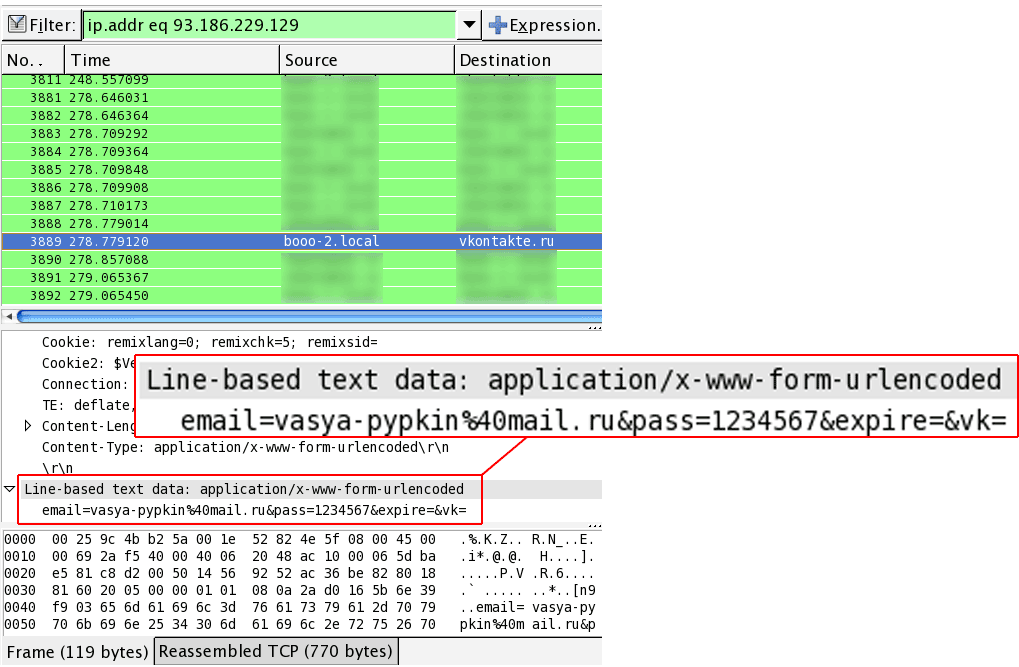
In loaded networks, dumps are filled very quickly, and filters can be used to speed up the opening of wireshark dumps. For example, do a sample only by protocol or IP. You can also disable rezolv addresses.
Hacking WEP
The bottom line is to collect a large number of service packets containing the Initial Vector (Initial Vector), and from them to decrypt the network key. Initialization vectors are transmitted to control the connection of the point with the client, respectively, the attack is feasible only when there are connections to the point.
For the successful finding of the key, it is necessary to collect more than 70 thousand packages (in practice, 20 thousand is sufficient) It is not possible to collect such a number, passively listening to the broadcast. To speed up the process, there is a packet injection method to force hosts to generate a large number of IV packets. To start the injection, you need to have a certain amount of Initial Vectors, so you can just wait or catch up with traffic by authorization flood: Network => Authentication Flood (DoS attack similarity. Be careful with this option, the access point may hang). After that, you can start the injection: Network => Reinject Packets .
If the injection attempt was successful, the number of packages we need (Unique IV's) will begin to increase dramatically.
Let's start parallel key decryption using the program aircrack-ng.
In the terminal we enter:
aircrack-ng /path/to_dump.file
If you do not specify the mac-address of the attacked access point, the program will suggest that you select from all points found in the dump. You can specify the mac address with the -b option:
aircrack-ng -b 00: 00: 00: 00: 00: 00 /path/to_dump.file
Hacking WPA / WPA2
To date, the WPA algorithm is fairly reliable. The only possibility of hacking is brute force (dictionary search).
The task is to intercept the “handshake” (handshake) at the time of authorization of the client at the access point and the subsequent search of passwords in the dictionary. To do this, we need to either wait for the moment when the client comes to log in or try to break the existing connections in order to provoke a reconnection:
Network => Deauthenticate
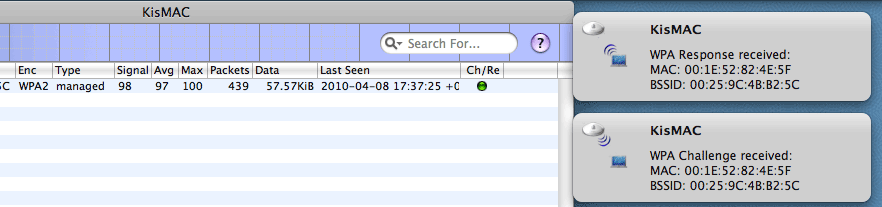
It is important to catch both sides of the handshake: Challenge and “Response. If successful, the red dot Ch / Re will turn green.
It often happens that you can only catch the answer point (Challenge), and the answer is a low-power client (such as a mobile phone) fails. In this case, you need to find the position of the antenna, which will be the maximum client signal
Looking through the key looks like this:
aircrack-ng -w keys.txt -b 00: 00: 00: 00: 00: 00 dump.file
where keys.txt is the path to the dictionary, 00: 00: 00: 00: 00: 00 is the mac-address of the attacked point, dump.file is the path to the file with handheld.
Having an encryption key, you can listen to all traffic passing through the network. To do this, use the decryptor dump:
For WEP encryption, the key is specified with the -w option:
airdecap-ng -w 12345678 /path/to/wep.dump.file
for WPA / WPA2 with the -e netname option -p network_key:
airdecap-ng -e 'Cool-WiFi' -p 12345678 /path/to/wpa.dump.file
As a result, a decrypted dump file will be created that can already be viewed by the packet analyzer.
Source: https://habr.com/ru/post/90307/
All Articles