Patch rootkit is not a friend!
On Tuesday, last week, there was an unplanned update from Microsoft, number MS10-015 . This patch eliminated a vulnerability that allows you to locally enhance your privileges, and made modifications directly to the OS kernel. This update had rather unexpected consequences - some users experienced problems after installing it. More specifically, after rebooting the system, which is required to install this update, a critical error began to appear in one of the system drivers, which was further demonstrated by BSoD.
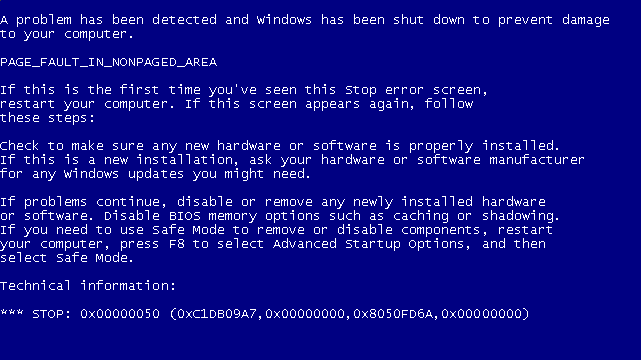
On the part of Microsoft, this situation caused some confusion, since before the release of the update they undergo a rather rigorous testing. But, as it turned out during the internal investigation, the culprit was the TDSS rootkit in its latest reincarnation, which infected the driver, and due to incompatibility with the modifications made to the kernel, a critical error occurred. By the way, the rootkit could infect other system drivers.
')
Let's take a closer look at what happened and for what reason BSoD arose. So, we are talking about the latest modification of the TDSS rootkit, which has long been actively distributed on the Internet. But why does this error occur?
The answer turned out to be quite simple: the rootkit uses implicit calls to the WinAPI functions and searches for them by a memory offset, but when updating, modifications occurred that changed the code that was located at different memory addresses. This was the reason for the critical error.


According to Microsoft, the problem with this error manifested itself exclusively on 32-bit operating systems. And as arguments, information was given about the impossibility of loading unsigned drivers in 64-bit versions of Vista and Win7. All this is also explainable, since the rootkit makes modifications directly to the driver, the digital signature no longer passes the verification, and the driver cannot be loaded.
According to our data, the activity of infected users with a TDSS rootkit after the release of this update subsided quite strongly, which made the attackers release an updated version with the correction of this error. The attackers approached with an irony to update their offspring, and in one of the configuration files we encountered the following line of obscene content: “F * ck damnation, man! F * ck redemption! We are God's unwanted children! ”
The situation has shown that the number of users infected with this rootkit is quite large. Moreover, the concentration of victims in the United States is by no means small. Perhaps this is what caused the rapid response and investigation of the incident by Microsoft.

On the part of Microsoft, this situation caused some confusion, since before the release of the update they undergo a rather rigorous testing. But, as it turned out during the internal investigation, the culprit was the TDSS rootkit in its latest reincarnation, which infected the driver, and due to incompatibility with the modifications made to the kernel, a critical error occurred. By the way, the rootkit could infect other system drivers.
')
Let's take a closer look at what happened and for what reason BSoD arose. So, we are talking about the latest modification of the TDSS rootkit, which has long been actively distributed on the Internet. But why does this error occur?
The answer turned out to be quite simple: the rootkit uses implicit calls to the WinAPI functions and searches for them by a memory offset, but when updating, modifications occurred that changed the code that was located at different memory addresses. This was the reason for the critical error.


According to Microsoft, the problem with this error manifested itself exclusively on 32-bit operating systems. And as arguments, information was given about the impossibility of loading unsigned drivers in 64-bit versions of Vista and Win7. All this is also explainable, since the rootkit makes modifications directly to the driver, the digital signature no longer passes the verification, and the driver cannot be loaded.
According to our data, the activity of infected users with a TDSS rootkit after the release of this update subsided quite strongly, which made the attackers release an updated version with the correction of this error. The attackers approached with an irony to update their offspring, and in one of the configuration files we encountered the following line of obscene content: “F * ck damnation, man! F * ck redemption! We are God's unwanted children! ”
The situation has shown that the number of users infected with this rootkit is quite large. Moreover, the concentration of victims in the United States is by no means small. Perhaps this is what caused the rapid response and investigation of the incident by Microsoft.
Source: https://habr.com/ru/post/84957/
All Articles