War bots, or how to make cybercriminals?

We have long been watching the development of the situation associated with the Win32 / TrojanDownloader.Bredolab malware , popularly known as Zeus bot, or even simpler, Zeus. This is quite a successful malicious area (it doesn’t turn a language to call it a product) of virus makers, it has long been rooted in the malicious software market, and is very popular among cybercriminals. The ZeuS Tracker resource still records a large number of active control centers created due to the distribution of this Trojan. Each such center can manage a huge number of bots. But in order not to concentrate control of a large botnet in one place, the attackers split it up into several smaller ones, in case one of them fails for some reason.
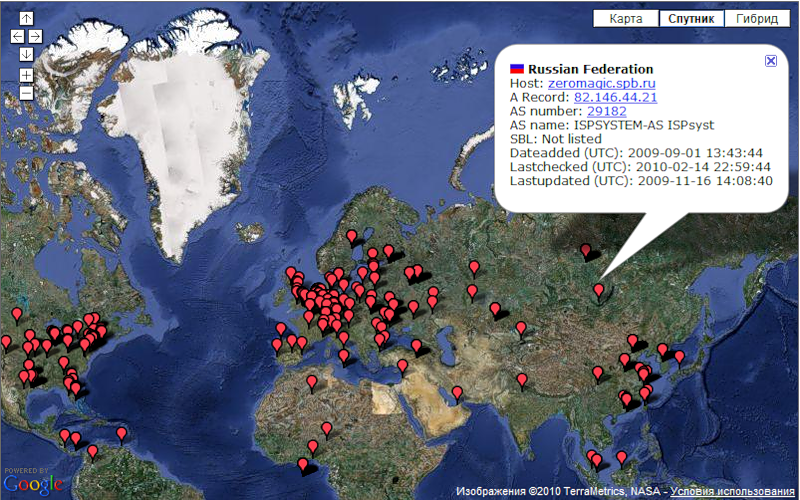
According to statistics from ZeuS Tracker, today there are 1296 command centers of this botnet, of which only 697 are active now.
But according to our measurements, the concentration of these Trojans in the general flow of malicious traffic is still very high.
The success of Zeus in the cybercrime community is primarily associated with a sound business model. Its creators are spreading their criminal offspring as part of several components - it is a bot / trojan generator and a bots control center that is fully ready for use. Actually, the bot generator itself is needed to set various parameters of the Trojan's operation, for example, the target settings for theft of various kinds of personal data.

The second component is the control center, which allows cybercriminals to track the distribution statistics of their bots, as well as remotely update the configuration parameters of bots.
')

Zeus was actively spreading throughout the whole of 2009, although there were also recorded moments of his highest activity, such as the middle of last summer. It was at this time that information emerged about several open vulnerabilities in Adobe products, which served as a catalyst for increased activity on the part of cybercriminals. Nothing foreshadowed problems for the seemingly well-thought-out Zeus bot distribution strategy, but at the end of 2009 a new “product” appeared on the cybercriminal scene with a similar target audience, and its name was SpyEye, or, according to our classification, a Trojan program that belongs to to the Win32 / Spy.SpyEye family. It is also distributed with a set of components for generating bots and a command center.
Win32 / Spy.SpyEye is aimed at the same buyers as Zeus, but the question arises, how can opposing groups divide this market among themselves? And the creators of SpyEye have chosen the most unceremonious way possible - simply to remove their competitor from the computers of their victims.
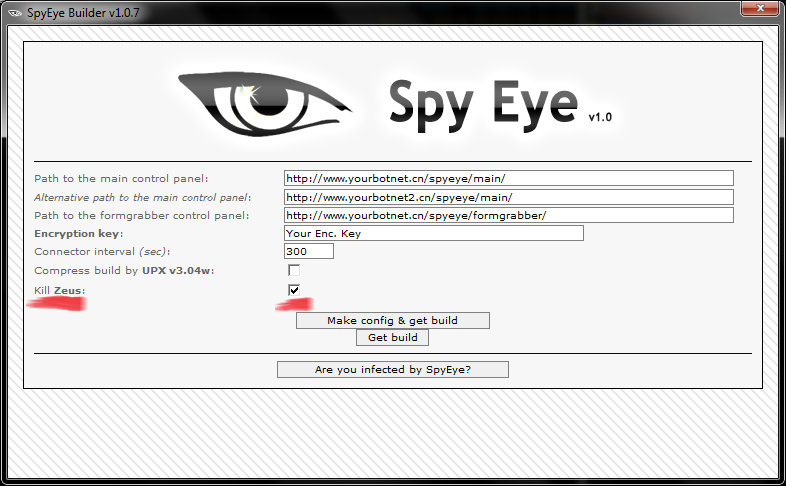
Thus, cybercriminals want to seize part of the market that belongs to Zeus, and, moreover, hard and unceremoniously. In this case, you can put forward several versions of such a struggle. Perhaps the creators of Zeus themselves are trying to spread a new malicious program and in such a brutal way to replace their outdated brainchild, since SpyEye has a more sophisticated remote control and management mechanism.
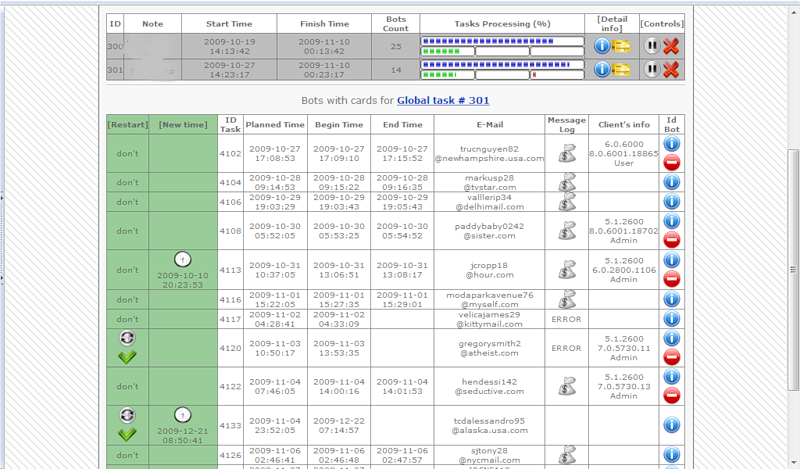
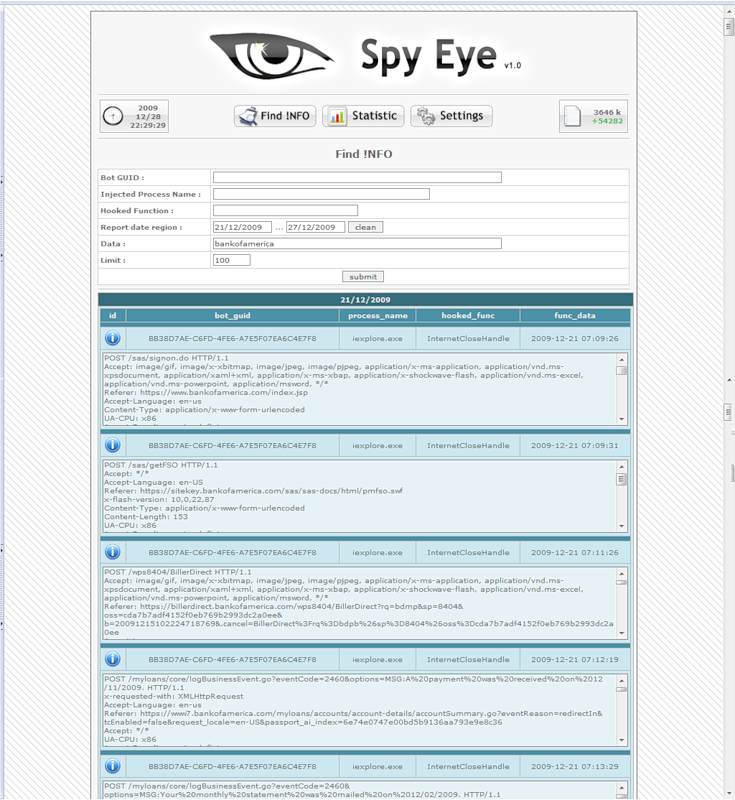
By the way, it is appropriate to recall the events of 2004, when there was fierce competition between the three cybercriminal groups: Bagle, Mydoom and Netsky. And Netsky unceremoniously removed his rivals. Competition in business is always there, and in the criminal business it takes on particularly tough outlines.
As for Win32 / Spy.SpyEye, it is also aimed, first of all, at stealing personal data. The Trojan has a keylogger on its board, features for stealing FTP passwords and POP3 passwords, as well as functionality for tracking data entry in popular web browsers (IE, FF). If this data is of commercial interest, the malware sends it to attackers. As in the case of Zeus, the bots communicate with the command center using the HTTP protocol. If we consider the implementation of the malicious functionality, this Trojan does not represent anything of interest from an analytical point of view, since it uses completely standard methods that have previously been encountered in other malicious programs.
Today we are witnessing the evolution of the so-called “kits” for conducting cybercriminal business. Obviously, the creators of this malware infection take care of their criminal customers, and each of them is trying to offer a better quality area. I wonder what happens next ...
Source: https://habr.com/ru/post/84452/
All Articles