Remove the Trojan that requires sending SMS from the computer
This morning, at work, an employee caught a trojan requiring an SMS to be sent to a short number.
There should be a picture with a trojan, but what is most funny, I could not run it on a virtual machine. Even in autoload I wrote it, well, he does not want to work and that's all. In general, if anyone wants to make a screenshot, it will be very good. The experience trojan itself can be downloaded from here . At the same time, I saw the window only briefly, but it looked beautiful :) They sent me a picture :.
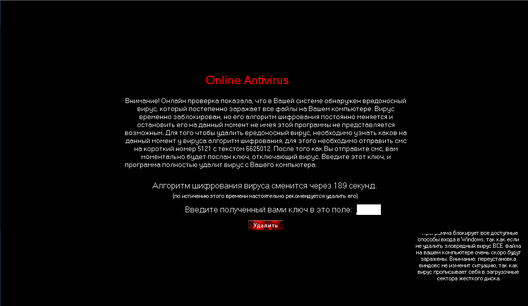
Regarding the mechanism of infection, Olegas wrote very well; By the way, there was initially a suspicion that this is a hole in IE8, in practice it turned out that the virus most likely penetrated a hole in Java or Flash. So, in principle, none of the browsers are protected. Analysis of the logs showed that the sites were visited fairly innocuous, which of them started the iframe with the dropper, it was not possible to find out (not all the same, in fact).
')
Now, about the treatment itself. There are a lot of ways, but I will tell you how to do it over the network, without approaching the victim and without being bothered with how to deal with this window (this, by the way, helps against other viruses).
All further actions are done from another computer:
In general, everything is simple, and most importantly from your workplace. Naturally, the remote access should not be filed on the computer, the remote registry should not be disabled.
And finally, a little from another area: in case of computer virus infection, I recommend, if possible, to scan it from another machine, also over the network. Repeatedly, there were precedents when the virus powdered antivirus brains by portraying its absence, and naturally it didn’t work for another computer.
PS: Surely for administrators this method will be trivial and obvious, but on Habré there are not only Windows administrators, but also ordinary users who will probably find this method useful (I hope so :)).
UPD: In the comments they wrote many other ways, using special programs and ways to find the code. I can only insert my 5 kopecks, that if there is no special LiveCD, the installation disc from Vista and above is well suited for this purpose. At the beginning of the installation, press Shift + F10, the console opens, and from it you can run a lot of programs (for example, from a flash drive), in particular, Far and the registry editor work well.

Regarding the mechanism of infection, Olegas wrote very well; By the way, there was initially a suspicion that this is a hole in IE8, in practice it turned out that the virus most likely penetrated a hole in Java or Flash. So, in principle, none of the browsers are protected. Analysis of the logs showed that the sites were visited fairly innocuous, which of them started the iframe with the dropper, it was not possible to find out (not all the same, in fact).
')
Now, about the treatment itself. There are a lot of ways, but I will tell you how to do it over the network, without approaching the victim and without being bothered with how to deal with this window (this, by the way, helps against other viruses).
All further actions are done from another computer:
- We are looking for a harmful process tasklist / s computer_name . In our case, it turned out to be user32.exe (a very good feint with ears in my opinion, from the first time the eye does not cling to the name).
- We kill it through taskkill / s computer_name / pid process_id
- Run regedit and connect the network registry from this computer. We are looking for where the virus is. It turned out that he changed himself in as a shell:
HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon, Shell . Return to explorer.exe - It also turned out that the virus had set the “TaskManager launch ban” policy, so it just wasn't to be killed. A quick search in Google (it was faster than applying a policy) showed that you need to kill a branch:
HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ System, DisableTaskMgr (via the remote registry, the key can be found as HKEY_USERS \ SID_ of the current user , if logged in one, then this is just a “long” SID in contrast to the system short) - Reboot, run Cure-It and kill the remains of the virus from the temporary folders.
In general, everything is simple, and most importantly from your workplace. Naturally, the remote access should not be filed on the computer, the remote registry should not be disabled.
And finally, a little from another area: in case of computer virus infection, I recommend, if possible, to scan it from another machine, also over the network. Repeatedly, there were precedents when the virus powdered antivirus brains by portraying its absence, and naturally it didn’t work for another computer.
PS: Surely for administrators this method will be trivial and obvious, but on Habré there are not only Windows administrators, but also ordinary users who will probably find this method useful (I hope so :)).
UPD: In the comments they wrote many other ways, using special programs and ways to find the code. I can only insert my 5 kopecks, that if there is no special LiveCD, the installation disc from Vista and above is well suited for this purpose. At the beginning of the installation, press Shift + F10, the console opens, and from it you can run a lot of programs (for example, from a flash drive), in particular, Far and the registry editor work well.
Source: https://habr.com/ru/post/83945/
All Articles