Zero-day exploit "Aurora" (CVE-2010-0249), an attack on Google and everything is all
On January 12, Google announced an attack on its Gmail email service. According to the company, the attack was carried out from the territory of China, and its goal was to collect personal information from user accounts. As it became known later, Google is not the only company that at the time was faced with a similar problem.
The starting point of the attack, the purpose of which was to install malicious software, was sending spam letters, which called on the recipients to make the transition by a malicious link. After the transition, the attack was implemented by a previously unknown exploit CVE-2010-0249 for Microsoft Internet Exporer browsers of various versions (6, 7, 8).
Three days later, in one of the blogs , Microsoft published information that for IE8 users the risk of infection is much lower than for all others. This is due to the fact that, by default, on all platforms where this browser can be installed, data execution prevention (DEP) technology is activated, which prevents the correct execution of the code of this exploit.
')
Now the vulnerability will be closed only in the February monthly update of products from Microsoft (Patch Tuesday). The exploit code has already become available to the general public and published on a variety of information security resources. And the monthly waiting for a “patch” is a fairly long time.
The exploit code itself performs heap spray attacks to execute malicious shellcode . That is why with the included DEP technology, the exploit will not be able to execute the data on the heap, and in the worst case, you will experience a crash of the browser. If the shellcode is executed, a Trojan program will be loaded, which will install the other malicious modules into the system.
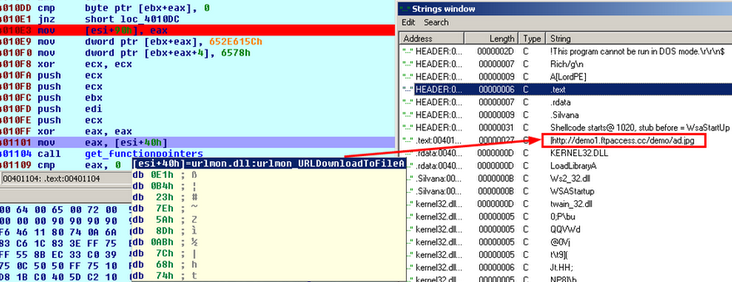
Below we publish a video that illustrates the work of the Aurora exploit (CVE-2010-0249), under different versions of the Internet Explorer browser:
Internet Exporer 6
Internet Exporer 7
Internet Exporer 8
The starting point of the attack, the purpose of which was to install malicious software, was sending spam letters, which called on the recipients to make the transition by a malicious link. After the transition, the attack was implemented by a previously unknown exploit CVE-2010-0249 for Microsoft Internet Exporer browsers of various versions (6, 7, 8).
Three days later, in one of the blogs , Microsoft published information that for IE8 users the risk of infection is much lower than for all others. This is due to the fact that, by default, on all platforms where this browser can be installed, data execution prevention (DEP) technology is activated, which prevents the correct execution of the code of this exploit.
')
Now the vulnerability will be closed only in the February monthly update of products from Microsoft (Patch Tuesday). The exploit code has already become available to the general public and published on a variety of information security resources. And the monthly waiting for a “patch” is a fairly long time.
The exploit code itself performs heap spray attacks to execute malicious shellcode . That is why with the included DEP technology, the exploit will not be able to execute the data on the heap, and in the worst case, you will experience a crash of the browser. If the shellcode is executed, a Trojan program will be loaded, which will install the other malicious modules into the system.

Below we publish a video that illustrates the work of the Aurora exploit (CVE-2010-0249), under different versions of the Internet Explorer browser:
Internet Exporer 6
Internet Exporer 7
Internet Exporer 8
Source: https://habr.com/ru/post/81142/
All Articles