We build a cluster system of protection against DDoS
This article was written by a friend of mine who is professionally engaged in the creation of high-load network solutions, including DDoS anti-attack systems.
At his request, publish it in Habré. If you like the article, he will be happy to invite to hl.squirrel@yahoo.com .
I will try to briefly describe the solution scheme for comprehensive protection against various types of high-intensity DDoS attacks. This solution was successfully tested and operates on the service stop-ddos.net
The scheme is based on the separation of the protection system (frontend) from the application server (backend).
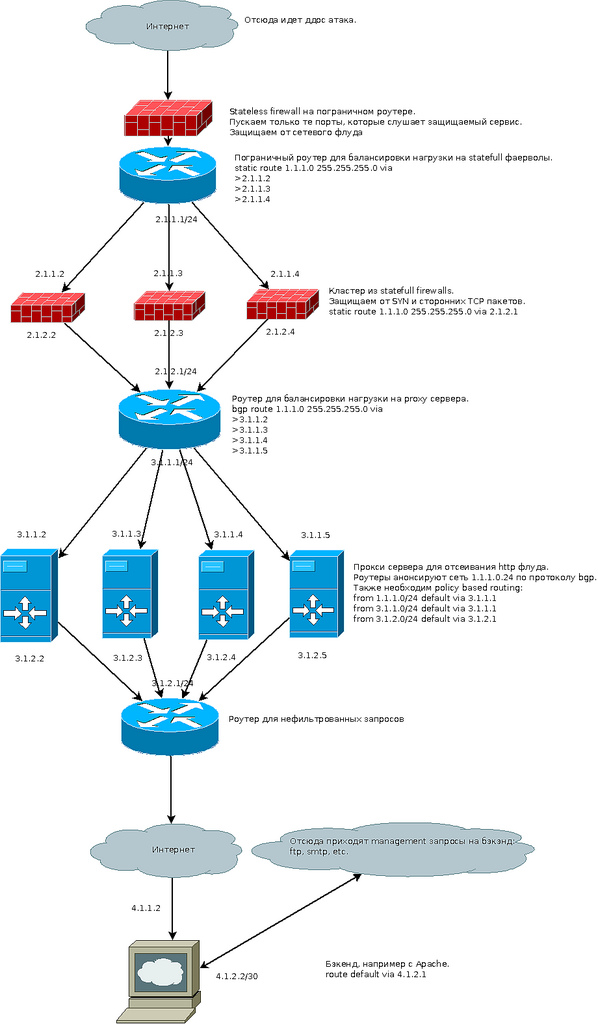
The picture of the described scheme is at the end of the article.
')
To date, the most effective means of dealing with the usual network flood is a wide channel. A channel of 10Gbps is enough to repel most attacks of this type.
In order not to load the equipment once again during such an attack, we eliminate the extra packets to our addresses. For example, the service we protect lives on port 80 TCP. In this case, packets with a destination port other than 80 can be safely filtered stateless. The CISCO 7600 level router is quite suitable for this.
However, do not forget about the backup channel, at least 1Gbps wide.
We protect against SYN flood using statefull firewalls (SFFW).
Ideally, a hardware firewall (for example, Juniper SRX 5800). Depending on the intended attack power, the required number of firewalls is selected. On the router, located at the entrance of our protection, a route is created by the network protected by us (on the diagram it is 2.1.1.0/24) with the next-hop address of each SFFW.
Each SFFW has a static network route 1.1.1.0 to the next router. It balances the load between the nodes of the last level of protection, which are servers with a UNIX system.
In this case, it is convenient to use the BGP dynamic routing protocol (when one node fails, the load is automatically distributed between the working nodes). Thus, each server announces the route to the network 1.1.1.0 with next-hop self to the router.
Packages that have reached this level of protection fall into reverse proxy. This should be a proxy server that can distinguish a bot from a real client. For example, nginx with a log analyzer, the number of simultaneous connections from an address in combination with any other methods invented or found by you. Examples of such solutions have already been published on Habré.
On proxy servers, we configure policy based routing as shown in the example. This will relieve requests for backend from secondary passing through a statefull firewall.
Now about backend. The address to which requests come from the frontend should be different from the address through which the server is managed. If the management address is lit (for example, a letter generated by the application), you can always throw the management address into the blackhole and this will not affect the operation of the application.
In reality, there is no point in using as many routers as shown in the diagram. Instead, it is more rational to use one device as routers with several routing tables (VRF, routing instances) or several logical routers.
Hardware stateful firewalls can also be excluded from this scheme, and instead of them on proxy servers use PF in the SYN Proxy mode (PF in this mode shows the best performance on native OpenBSD, in the case of Linux it is better to abandon PF, and simply run sysctl as needed ). However, the number of servers in this case will have to increase.
Incoming mail is most advantageous to send to the Google MX (let someone try to ping them :)), and then fetch the mail to the server. DNS is also best kept not at home - large foreign registrars provide a sufficiently fault-tolerant cluster as NS for purchased domains. Also, for a fee, you can place your domain on their NS servers.
PSPlease throw a bit of karma to post to the blog "Information Security".
Thank you, moved!
UPD. Answers to comments are given by the author of the article.
At his request, publish it in Habré. If you like the article, he will be happy to invite to hl.squirrel@yahoo.com .
I will try to briefly describe the solution scheme for comprehensive protection against various types of high-intensity DDoS attacks. This solution was successfully tested and operates on the service stop-ddos.net
The scheme is based on the separation of the protection system (frontend) from the application server (backend).
There are 3 main types of DDoS attacks:
- attack aimed at overflow of channel resources to the Internet;
- attack aimed at exceeding the maximum number of simultaneous server connections (SYN flood);
- attack aimed at the exhaustion of the processor capacity of the server (frequent requests for pages - HTTP flood).
The solution should provide protection against each type of attack.
The picture of the described scheme is at the end of the article.
')
Network flood
To date, the most effective means of dealing with the usual network flood is a wide channel. A channel of 10Gbps is enough to repel most attacks of this type.
In order not to load the equipment once again during such an attack, we eliminate the extra packets to our addresses. For example, the service we protect lives on port 80 TCP. In this case, packets with a destination port other than 80 can be safely filtered stateless. The CISCO 7600 level router is quite suitable for this.
However, do not forget about the backup channel, at least 1Gbps wide.
SYN flood
We protect against SYN flood using statefull firewalls (SFFW).
Ideally, a hardware firewall (for example, Juniper SRX 5800). Depending on the intended attack power, the required number of firewalls is selected. On the router, located at the entrance of our protection, a route is created by the network protected by us (on the diagram it is 2.1.1.0/24) with the next-hop address of each SFFW.
Each SFFW has a static network route 1.1.1.0 to the next router. It balances the load between the nodes of the last level of protection, which are servers with a UNIX system.
In this case, it is convenient to use the BGP dynamic routing protocol (when one node fails, the load is automatically distributed between the working nodes). Thus, each server announces the route to the network 1.1.1.0 with next-hop self to the router.
HTTP flood
Packages that have reached this level of protection fall into reverse proxy. This should be a proxy server that can distinguish a bot from a real client. For example, nginx with a log analyzer, the number of simultaneous connections from an address in combination with any other methods invented or found by you. Examples of such solutions have already been published on Habré.
On proxy servers, we configure policy based routing as shown in the example. This will relieve requests for backend from secondary passing through a statefull firewall.
Now about backend. The address to which requests come from the frontend should be different from the address through which the server is managed. If the management address is lit (for example, a letter generated by the application), you can always throw the management address into the blackhole and this will not affect the operation of the application.
In reality, there is no point in using as many routers as shown in the diagram. Instead, it is more rational to use one device as routers with several routing tables (VRF, routing instances) or several logical routers.
Hardware stateful firewalls can also be excluded from this scheme, and instead of them on proxy servers use PF in the SYN Proxy mode (PF in this mode shows the best performance on native OpenBSD, in the case of Linux it is better to abandon PF, and simply run sysctl as needed ). However, the number of servers in this case will have to increase.
post office
Incoming mail is most advantageous to send to the Google MX (let someone try to ping them :)), and then fetch the mail to the server. DNS is also best kept not at home - large foreign registrars provide a sufficiently fault-tolerant cluster as NS for purchased domains. Also, for a fee, you can place your domain on their NS servers.

PS
Thank you, moved!
UPD. Answers to comments are given by the author of the article.
Source: https://habr.com/ru/post/78145/
All Articles