Forrester Study - Identity and Access Management
I have a firm belief that all kinds of surveys and studies, albeit limited by geographic or business framework, are still useful for understanding, in the first approximation, the alignment of forces in the markets and tracking where and in which or other suppliers are moving. Among other things, this little thing sometimes helps to cool the ardor of overly ambitious sales managers and move on to more adequate discussions of costs and conditions :)
In November, a report on an important topic of access control, user rights and other things caught my eye. Forrester in its research uses a well-thought-out methodology, so it was interesting to read that the leaders in IAM today are Oracle, CA and IBM, and Miscrosoft has so far failed to catch up to at least the middle peasants.
')
Forrester ranked suppliers on 79 criteria, which were grouped into three broad categories:
Available package offers. To rank the strength of a solution, Forrester evaluated the following products by 60 criteria: creating user accounts and managing them, providing access to resources, managing roles, re-confirming access rights (recertification), managing web access, web services security, federated integration, forced enforcement of authority restrictions, enterprise single sign-on (E-SSO), reporting, etc.
In addition, since IAM products often need to be integrated with data leak prevention (DLP) software, security incident management, and reporting, Forrester has included interaction capabilities built into each IAM system in the questionnaires. Finally, the company evaluated the feedback from the clients of the studied companies and those questions from IT customers as a whole, which regularly come to analysts.
Strategy. In order to assess how far the supplier is able to support a full-featured range of products in a very dynamic and relatively new market, Forrester evaluated the following components of the strategy on 11 criteria: identity management concept, IAM solutions width, pricing policy and cost scenarios, partnership with system integrators; ecosystem supporting IAM solutions of a particular supplier.
Market share. To reliably determine the level of supplier presence in the market, Forrester assessed the installed base, income and profitability growth for both IAM solutions and the company as a whole by eight criteria.
9 largest suppliers were chosen for the study: CA, Courion, Hitachi ID Systems, IBM, Microsoft, Novell, Oracle, SAP and Sun Microsystems.
The study revealed the following positions of IAM suppliers (see fig.)
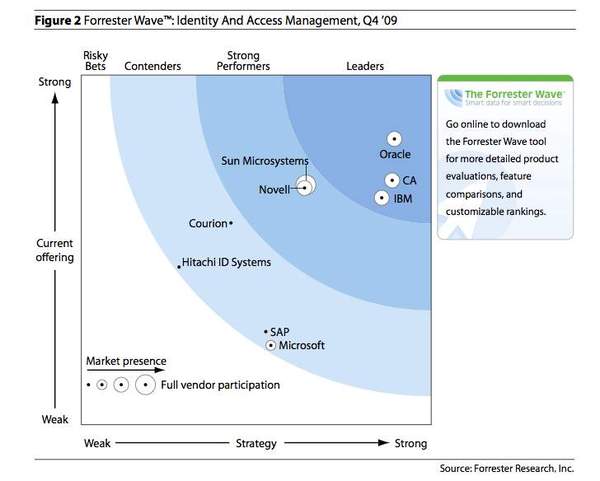
Forrester concludes that Oracle, CA and IBM are leading the packaged IAM solutions market. These companies offer integrated packages with user-friendly and user-friendly interfaces, advanced identity analysis, proven web access control tools, a certain level of integration with DLP and centralized audit and incident management systems. These suppliers have the widest installed base, which in turn helps shape the strategy of innovative solutions in the long term.
Novell, Sun Microsystems and Courion offer fairly competitive IAM packages, but they lack the full portfolio of solutions in this area. In particular, the providers of this group have not sufficiently developed the functions of centralized policy management, enforcing restrictions on permissions, integration with DLP, and privileged account management.
Microsoft, Hitachi ID Systems and SAP have not yet reached the level of suppliers of IAM package solutions and offer only selected products from this area. In particular, these companies cannot offer a solution that supports both account management and access. In addition, they all lack either full-featured web access control, or E-SSO, or enforcing restrictions on permissions.
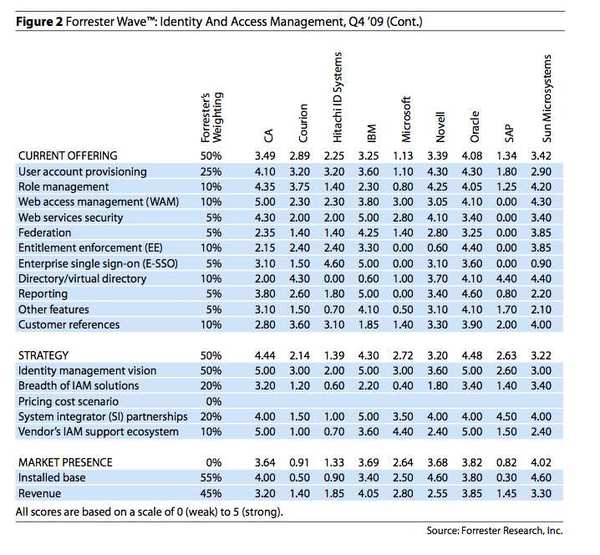
Detailed estimates for the functional are shown in Fig. 2:
Based on the study, Forrester has compiled brief profiles of suppliers (here I list only the leaders of the rating)
Oracle leads the ranking and its IAM-product package stands out from the rest because of its breadth. The company is still experiencing difficulties with the integration of products within this package after numerous acquisitions, this is especially noticeable in terms of defining roles and access re-certification. However, Oracle is the only vendor that has 1) a product to enforce restrictions on permissions (Oracle Entitlements Server, built on the basis of BEA AquaLogic Enterprise Security); 2) a proprietary product for adaptively configurable access (Oracle Adaptive Access Manager), integrated with role management and data retrieval tools; 3) an application-focused IAM strategy. Further Oracle achievements in the field of IAM will depend on the speed and success of integrating Sun Microsystems solutions.
Ca. Because of the high cost of licenses, CA SiteMinder has recently been replaced by a number of other vendor products, and CA Role & Compliance Manager (RCM) is not yet fully integrated with CA Identity Manager. However, with the acquisition of RCM, the company received the role management functionality developed on the Eurekify platform. In addition, it has fine-tuned tools for delimiting powers (IDFocus) and preventing data leakage (Orchestria).
These acquisitions will strengthen CA’s position in delegating administrative authority not only to company employees, but also to business partners. Moreover, the functions of developing and comparing roles, modeling and heuristic linking of accounts in RCM are among the best in their class. CA also offers a very fast implementation, and its fixed-cost projects provide quick returns for customers.
Ibm. Prior to Tivoli Identity Manager 5.0, the downsides of IBM solutions were a long integration cycle and lack of flexibility in relating TIM functionality to business processes. However, version 5.0 already represents a big leap forward, and the release of TIM 5.1 released in June 2009, among other things, completely fills the gaps in role management. Installation, user-friendliness and policy management functions in new versions of the product are significantly improved compared with TIM 4.6.4. DataPower integration with Tivoli Access Manager (TAM) provides IBM with leadership in web services security, and Federation Access Management has the broadest protocol support in its class. In addition, TIM 5.1 also integrates operational role management, segregation of duties, access re-certification and group management.
Despite the fact that IBM has relatively recently taken up the development of enforcement tools, its Tivoli Security Policy Manager product allows you to present roles in the context of powers, and this is a fundamentally new approach in this area. The breadth and detailed design of the IBM security portfolio offers the corporation leadership where IAM, DLP, and application security are required.
From myself I can say that it was interesting to compare the estimates of Oracle - a sort of near-median distribution, everything is and everything is quite average, not a single five, and IBM - as usual, distinguished by security, for example, but with a very uneven scatter of ratings. CA I know much less, but a friend-VP from the States says that the company has no particularly vigorous interests in Russia, they will continue to pile up five to ten megacross customers, of little interest. The main struggle, therefore, will be between Oracle and IBM in the near future, MS Forefront will not mature soon, if at all, it will be in time for distribution.
The Forrester report is paid, but the full text (in English) can be found here.
In November, a report on an important topic of access control, user rights and other things caught my eye. Forrester in its research uses a well-thought-out methodology, so it was interesting to read that the leaders in IAM today are Oracle, CA and IBM, and Miscrosoft has so far failed to catch up to at least the middle peasants.
')
Forrester ranked suppliers on 79 criteria, which were grouped into three broad categories:
Available package offers. To rank the strength of a solution, Forrester evaluated the following products by 60 criteria: creating user accounts and managing them, providing access to resources, managing roles, re-confirming access rights (recertification), managing web access, web services security, federated integration, forced enforcement of authority restrictions, enterprise single sign-on (E-SSO), reporting, etc.
In addition, since IAM products often need to be integrated with data leak prevention (DLP) software, security incident management, and reporting, Forrester has included interaction capabilities built into each IAM system in the questionnaires. Finally, the company evaluated the feedback from the clients of the studied companies and those questions from IT customers as a whole, which regularly come to analysts.
Strategy. In order to assess how far the supplier is able to support a full-featured range of products in a very dynamic and relatively new market, Forrester evaluated the following components of the strategy on 11 criteria: identity management concept, IAM solutions width, pricing policy and cost scenarios, partnership with system integrators; ecosystem supporting IAM solutions of a particular supplier.
Market share. To reliably determine the level of supplier presence in the market, Forrester assessed the installed base, income and profitability growth for both IAM solutions and the company as a whole by eight criteria.
9 largest suppliers were chosen for the study: CA, Courion, Hitachi ID Systems, IBM, Microsoft, Novell, Oracle, SAP and Sun Microsystems.
The study revealed the following positions of IAM suppliers (see fig.)

Forrester concludes that Oracle, CA and IBM are leading the packaged IAM solutions market. These companies offer integrated packages with user-friendly and user-friendly interfaces, advanced identity analysis, proven web access control tools, a certain level of integration with DLP and centralized audit and incident management systems. These suppliers have the widest installed base, which in turn helps shape the strategy of innovative solutions in the long term.
Novell, Sun Microsystems and Courion offer fairly competitive IAM packages, but they lack the full portfolio of solutions in this area. In particular, the providers of this group have not sufficiently developed the functions of centralized policy management, enforcing restrictions on permissions, integration with DLP, and privileged account management.
Microsoft, Hitachi ID Systems and SAP have not yet reached the level of suppliers of IAM package solutions and offer only selected products from this area. In particular, these companies cannot offer a solution that supports both account management and access. In addition, they all lack either full-featured web access control, or E-SSO, or enforcing restrictions on permissions.
Detailed estimates for the functional are shown in Fig. 2:

Based on the study, Forrester has compiled brief profiles of suppliers (here I list only the leaders of the rating)
Oracle leads the ranking and its IAM-product package stands out from the rest because of its breadth. The company is still experiencing difficulties with the integration of products within this package after numerous acquisitions, this is especially noticeable in terms of defining roles and access re-certification. However, Oracle is the only vendor that has 1) a product to enforce restrictions on permissions (Oracle Entitlements Server, built on the basis of BEA AquaLogic Enterprise Security); 2) a proprietary product for adaptively configurable access (Oracle Adaptive Access Manager), integrated with role management and data retrieval tools; 3) an application-focused IAM strategy. Further Oracle achievements in the field of IAM will depend on the speed and success of integrating Sun Microsystems solutions.
Ca. Because of the high cost of licenses, CA SiteMinder has recently been replaced by a number of other vendor products, and CA Role & Compliance Manager (RCM) is not yet fully integrated with CA Identity Manager. However, with the acquisition of RCM, the company received the role management functionality developed on the Eurekify platform. In addition, it has fine-tuned tools for delimiting powers (IDFocus) and preventing data leakage (Orchestria).
These acquisitions will strengthen CA’s position in delegating administrative authority not only to company employees, but also to business partners. Moreover, the functions of developing and comparing roles, modeling and heuristic linking of accounts in RCM are among the best in their class. CA also offers a very fast implementation, and its fixed-cost projects provide quick returns for customers.
Ibm. Prior to Tivoli Identity Manager 5.0, the downsides of IBM solutions were a long integration cycle and lack of flexibility in relating TIM functionality to business processes. However, version 5.0 already represents a big leap forward, and the release of TIM 5.1 released in June 2009, among other things, completely fills the gaps in role management. Installation, user-friendliness and policy management functions in new versions of the product are significantly improved compared with TIM 4.6.4. DataPower integration with Tivoli Access Manager (TAM) provides IBM with leadership in web services security, and Federation Access Management has the broadest protocol support in its class. In addition, TIM 5.1 also integrates operational role management, segregation of duties, access re-certification and group management.
Despite the fact that IBM has relatively recently taken up the development of enforcement tools, its Tivoli Security Policy Manager product allows you to present roles in the context of powers, and this is a fundamentally new approach in this area. The breadth and detailed design of the IBM security portfolio offers the corporation leadership where IAM, DLP, and application security are required.
From myself I can say that it was interesting to compare the estimates of Oracle - a sort of near-median distribution, everything is and everything is quite average, not a single five, and IBM - as usual, distinguished by security, for example, but with a very uneven scatter of ratings. CA I know much less, but a friend-VP from the States says that the company has no particularly vigorous interests in Russia, they will continue to pile up five to ten megacross customers, of little interest. The main struggle, therefore, will be between Oracle and IBM in the near future, MS Forefront will not mature soon, if at all, it will be in time for distribution.
The Forrester report is paid, but the full text (in English) can be found here.
Source: https://habr.com/ru/post/76763/
All Articles