RuCTFE 2009
Abstract
 On November 7, 2009, for the first time, international student information protection competitions were held in Russia. In this article we will understand what CTF is, how RuCTFE differs from RuCTF, what RuCTFE 2009 is , what the HackerDom team is and what to do if you also want to take part in such competitions.
On November 7, 2009, for the first time, international student information protection competitions were held in Russia. In this article we will understand what CTF is, how RuCTFE differs from RuCTF, what RuCTFE 2009 is , what the HackerDom team is and what to do if you also want to take part in such competitions.What is CTF?
CTF is also a team game in which participants can demonstrate their computer security skills and abilities. Teams are evaluated in three categories at once: protection, attack, publication of reports on found vulnerabilities. In some competitions, sometimes a task category is added (aka task).
As a rule, all teams are given the same image for a virtual machine with services installed in it. All services are developed specifically for each competition, so until the beginning of the game they can not be found in the public domain. The task of the team is to ensure stable and secure operation of its server throughout the entire game time. To do this, it is audited, which includes finding and fixing vulnerabilities, as well as its administration. In addition to protecting your server, you need to attack the servers of other teams, taking advantage of the vulnerabilities found. Confirmation of the success of an attack is getting private information (flags) from another server, which is periodically placed by the checking system of the jury. A simple example of a service could be a forum. The flag in it is a private message sent from one forum user to another.
An integral part of the CTF is the lack of uniform rules of competition. Organizers contribute something new to each game. It is almost never known in advance what the operating system will be on the game, what the services will be and in what programming languages they will be written. Teams must be ready for anything, that is, be able to quickly navigate the new situation.
')
CTF in Russia
This has already been written . I will add statistics on the number of teams from Russia who participated in various international student competitions.
| Schedule ( K.O. ) | # | Competition | Year |
|---|---|---|---|
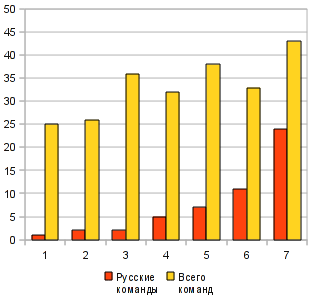 | one | iCTF 2006 | 2006 |
| 2 | CIPHER 3 | 2007 | |
| 3 | iCTF 2007 | ||
| four | CIPHER 4 | 2008 | |
| five | iCTF 2008 | ||
| 6 | CIPHER 5 | 2009 | |
| 7 | RuCTFE 2009 |
At the moment there are not so many competitions held in Russia. This All-Russian
RuCTF ( Hacker , USU )
and regional
UralCTF ( Hacker House , Ural State University ),
UFOCTF (UFOlogists, TIT SFU ).
I hope that this list will soon be added to at least SiBears ( TSU ) and CIT ( St. Petersburg State University ITMO ).
RuCTFE 2009
Unlike RuCTF, which take place internally and only for Russian student teams, RuCTFE 2009 was international and online.
43 teams took part (iCTF 2009 - 38, CIPHER 5 - 33) from 11 countries of the world: Russia, Germany, USA, Austria, Italy, France, Argentina, Norway, Croatia, India and Vietnam. Probably at the moment these were the largest student CTF competitions.
The rules and layout of the competition network were quite common for the CTF.
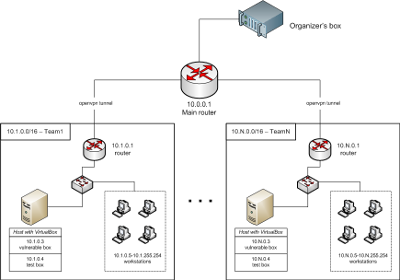
Competitions were held for 10 hours. The main surprise for the teams was the operating system chosen for the game. Most often you can find various Linux distributions, BSD. This time, when booting the virtual machine, the teams first saw debian and calmed down a bit, but then X was started, which is rather unusual, and the android 1.6 emulator was started in them. All services were written for him.
Services
There were five of them. You can read all the details in the documentation for them, but this is a spoiler for those who want to first try to test their strength and independently find vulnerabilities in the image (GPG key: djlrfgbdjbdbyjplhfdcndeqvfvfdjnbz) that the teams received. I will give a brief information on services from the developers themselves.
Cryptopizza
Service for receiving orders for the phone pizza delivery worker. Written in Java for the Google Android v1.6 platform. It implements an invented crypto protocol using symmetric AES and asymmetric RSA encryption for secure delivery of orders to the phone via open communication channels. Orders on the device are stored in SQLite DBMS.
F
ftp server with anti-virus functionality. Written in python using Android Scripting Environment. ftp is implemented using a lr parser built from a COP grammar that describes the language of commands sent by clients. Reactions to commands are implemented in functions that are called during convolutions of corresponding products. The antivirus component allowed us to perform signature-based analysis of downloaded files and check them with the help of “emulation”, and allowed updating signature databases.
Jabber
Service that implements the idea of Jabber-bot on the phone. This simple bot provides features similar to the newsletter. Written in Perl under the Google Android v1.6 platform using Android Scripting Environment.
Simple
A simple service that implements the functionality of installation / verification / listing of installed flags. Uses a simple cryptoprotection protocol based on two cryptographic algorithms based on fixed-key Feistel networks to encrypt requests and responses. Run for Linux EABI with tcp socket support and POSIX threads.
Stalker
Multiplayer online game service. Implemented as a dedicated server and clients to connect. As the flags are used valuable objects of the game - artifacts sold to the merchant. Technically, the server and client are implemented as Perl-scripts for Linux. In addition, for the phone in Java language under the Google Android v1.6 platform, a map is implemented that displays the player's status: visible objects, the location of the merchant, other players, anomalies, monsters and artifacts. There are no significant vulnerabilities in the service, and the teams need to understand the principle of the client’s work and write a convenient interface for managing their character, possibly automated by some artificial intelligence.
Taski
In addition to services, teams were asked to evaluate their strengths in analyzing the black box, searching in Gopher, algorithms and Haskell, steganography, knowledge of the classics of world fiction and ... Russian dances .

Results RuCTFE 2009
The game did not work right away. Most of the teams experienced problems both in general with setting up the android emulator and with its unstable work, which often turned out to be the result of malicious actions by other teams. Nevertheless, since the middle of the game, a grave struggle has unfolded in the top 15 lines of the scorbord.
As a result, the top5 scorbord looked like this:
- squareroots ( University of Mannheim , Germany)
- 0ldEur0pe ( RWTH Aachen , Germany)
- SiBears ( TSU , Russia)
- Siths ( Ural State University , Russia)
- h4ck! nb3rg ( Upper Austria University of Applied Sciences , Austria)
Hacker House, who are they?
This is a team, and more recently, a club from Ural State University. Since they began Russia's participation in the international CTF.
They conducted the first in Russia:
- regional UralCTF in 2006 (with the initiative support of a team from SUSU and ChelSU)
- All-Russian RuCTF in 2008
- International RuCTFE in 2009
The HackerDom team repeatedly became the prize-winner of international competitions, and in 2008 became the winner of CIPHER 4.
From HackerDom, the preparation and implementation of RuCTFE 2009 was carried out by a development team of 10 people with active technical support from the provider UralVES and the Clustertech group of companies.
Want to participate in the CTF?
If you are interested in student CTF - put together a team and register on the nearest UCSB iCTF , and then on the RuCTF 2010 quals!
And if you want to measure your strength with professional teams, then good luck with DEF CON ;)
Source: https://habr.com/ru/post/75362/
All Articles