How does the smart card
For a long time working with smart cards, I myself didn’t have a very clear idea about their insides. When I receive a document describing the structure and operation of a smart card, I share this information.
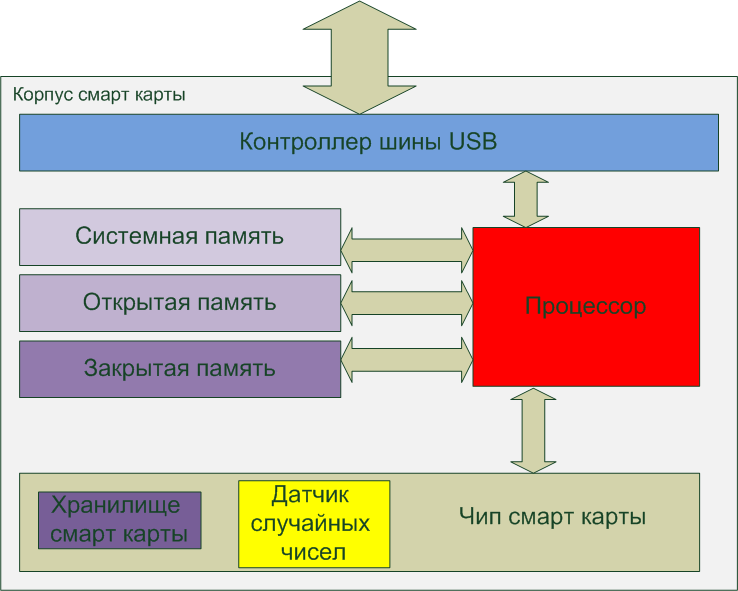
A smart card with a USB controller, or a USB dongle can be represented as a diagram (by and large a USB dongle differs from a smart card only by the presence / absence of a USB bus controller):
')
As can be seen from the figure, there are 3 memory sections in the smart card:
Accordingly, the processor works with these three memory areas, it is possible to read and write to all the above-described memory areas.
To work with the processor at a low level, APDU (Application Protocol Data Unit) commands are used. Using the APDU commands, it is even possible to access the smart card file system, although this is not recommended.
The most interesting component is the smart card chip, which provides:
The capabilities of smart card chips vary by manufacturer, but these differences are not significant. The differences are associated with algorithms for hardware implementation of encryption and hashing algorithms, various manufacturers implement different algorithms. But such algorithms as RSA (asymmetric encryption), DES (symmetric encryption) and SHA-1 (hashing), I think are implemented in almost all smart card chips.
Since the main purpose of a smart card is to work with digital certificates, this work can be represented as follows:
PS This topic was written based on materials from the company Aladdin. If someone has a technical description of the hardware component of keys from other manufacturers, share, please, I will be very grateful.
A smart card with a USB controller, or a USB dongle can be represented as a diagram (by and large a USB dongle differs from a smart card only by the presence / absence of a USB bus controller):

')
As can be seen from the figure, there are 3 memory sections in the smart card:
- System memory - contains the file system and operating system. It stores the data necessary to verify the correctness of the entered PIN codes and administrator passwords.
- Open memory - contains data that can be read without a PIN code. Smart card name, smart card id and others.
- Closed memory - contains data that can be accessed only by PIN-code.
Accordingly, the processor works with these three memory areas, it is possible to read and write to all the above-described memory areas.
To work with the processor at a low level, APDU (Application Protocol Data Unit) commands are used. Using the APDU commands, it is even possible to access the smart card file system, although this is not recommended.
The most interesting component is the smart card chip, which provides:
- Storing information in the internal storage of the smart card chip. Moreover, it should be noted that it is impossible to extract information from this repository. The smart card chip does not contain a command to retrieve data from storage. In this repository are the private keys of digital certificates (a somewhat illiterate phrase, but the essence is clear).
- Generate a key pair. The smart card chip contains a random number sensor (I don’t know why this is called a sensor in the domestic literature, I used to call it a random number generator from school). After generating the key pair, the private key enters the storage of the smart card chip and never goes beyond the smart card chip, the public key is transferred to the processor, which generates a certificate request and sends it outside the smart card limits (to the digital certificate authority).
- Hardware implementation of symmetric encryption algorithms. However, due to limited resources, symmetric encryption in a smart card chip is a very long process. In this regard, it is not recommended to perform symmetric encryption of large amounts of information by means of a smart card chip.
- Hardware implementation of hashing algorithms.
- Hardware implementation of asymmetric algorithms.
The capabilities of smart card chips vary by manufacturer, but these differences are not significant. The differences are associated with algorithms for hardware implementation of encryption and hashing algorithms, various manufacturers implement different algorithms. But such algorithms as RSA (asymmetric encryption), DES (symmetric encryption) and SHA-1 (hashing), I think are implemented in almost all smart card chips.
Since the main purpose of a smart card is to work with digital certificates, this work can be represented as follows:
- The processor receives a key pair generation command from the external environment.
- The processor translates this command into a smart card chip.
- In a smart card chip, a random number generator generates a key pair, the private key of which is placed in the smart card chip storage, and the public key is transferred to the processor.
- The processor generates a certificate request (in the format PKCS # 10), which contains the public key of the generated key pair.
- The processor sends the generated request to the external environment. This request goes to the certificate issuing center and, based on this request, issues a certificate that is returned to the smart card.
- Having received a certificate, the processor writes it to a closed area of memory.
PS This topic was written based on materials from the company Aladdin. If someone has a technical description of the hardware component of keys from other manufacturers, share, please, I will be very grateful.
Source: https://habr.com/ru/post/74092/
All Articles