UPD: Cisco and 2 providers
The problem is as old as today and we will solve it :)
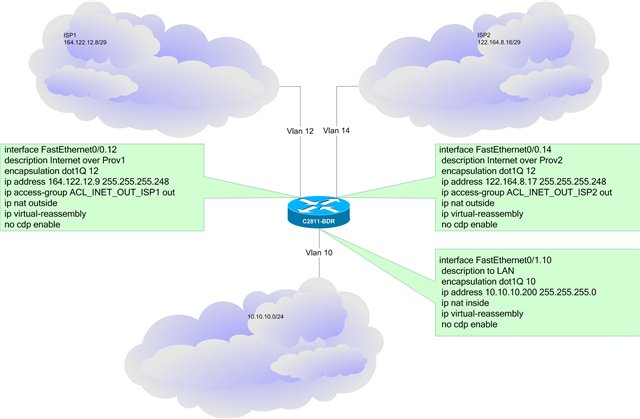
Given: 2 providers (ISP1 and ISP2), internal network and between them a router.
Task: configure one main (ISP1) and one backup channel (ISP2), if the first one drops, it switches to the second one, when the first channel is raised, it switches back.
UPD: Updated, added ip sla, so far without explanation.
Let us proceed from the fact that the switches are also from Cisco :) and for the beginning we will configure 3 Vlans:
Vlan 10 - internal network
Vlan 12 - ISP1
Vlan 14 - ISP2
Port number 1 belongs to Vlan 12 -ISP1, port 2 belongs to Vlan 14 (ISP2), the third trunk port is for the router, the other ports belong to Vlan 10, our internal network.
We’ve dealt with switching, we are now going to our root router, Cisco 2811 with Jos c2800nm-adventerprisek9_ivs-mz.124-24.T1.bin is taken as an example (although it will work on a different root router with another IOS)
')
Configure the interfaces:
Set up pools for NAT:
Access lists (ACL):
ACL'i for interfaces, so that no one breaks :)
ACL'i for those who are online:
Route-map:
And now the most interesting is tracking:
object 104
track 104 ip sla 104
delay down 2 up 5
object 204
track 204 ip sla 204
delay down 2 up 5
and routes:
and now actually what we check the availability of our gateways:
ip sla 104
icmp-echo 164.122.12.9 source-interface FastEthernet0 / 0.12
request-data-size 1
timeout 700
threshold 600
frequency 30
ip sla schedule 104 life forever start-time now
ip sla 204
icmp-echo 122.164.8.17 source-interface FastEthernet0 / 0.14
request-data-size 1
timeout 700
threshold 600
frequency 30
ip sla schedule 204 life forever start-time now
Given: 2 providers (ISP1 and ISP2), internal network and between them a router.
Task: configure one main (ISP1) and one backup channel (ISP2), if the first one drops, it switches to the second one, when the first channel is raised, it switches back.

UPD: Updated, added ip sla, so far without explanation.
Let us proceed from the fact that the switches are also from Cisco :) and for the beginning we will configure 3 Vlans:
Vlan 10 - internal network
Vlan 12 - ISP1
Vlan 14 - ISP2
C2970#vlan data
C2970(vlan)#vlan 10 name OurNet
VLAN 10 added:
Name: OurNet
C2970(vlan)#vlan 12 name ISP1
VLAN 12 added:
Name: ISP1
C2970(vlan)#vlan 14 name ISP2
VLAN 13 added:
Name: ISP2
C2970-Servers(vlan)#exit
APPLY completed.
Exiting....
C2970#Port number 1 belongs to Vlan 12 -ISP1, port 2 belongs to Vlan 14 (ISP2), the third trunk port is for the router, the other ports belong to Vlan 10, our internal network.
interface FastEthernet0/1
description -=I=- ISP1 -=I=-
switchport access vlan 12
switchport mode access
no cdp enable
interface FastEthernet0/2
description -=I=- ISP2 -=I=-
switchport access vlan 14
switchport mode access
no cdp enable
interface FastEthernet0/3
description -=I=- RTR -=I=-
switchport mode trunk
no mdix auto
interface FastEthernet0/4
switchport access vlan 10
switchport mode access
no cdp enable
...
interface FastEthernet0/24
switchport access vlan 10
switchport mode access
no cdp enableWe’ve dealt with switching, we are now going to our root router, Cisco 2811 with Jos c2800nm-adventerprisek9_ivs-mz.124-24.T1.bin is taken as an example (although it will work on a different root router with another IOS)
')
Configure the interfaces:
interface FastEthernet0/0
no ip address
duplex auto
speed auto
no cdp enable
!
interface FastEthernet0/0.12
description -=I=- Internet over ISP1 -=I=-
encapsulation dot1Q 12
ip address 164.122.12.9 255.255.255.248
ip access-group ACL_INET_OUT_ISP1 out
ip nat outside
ip virtual-reassembly
no cdp enable
!
interface FastEthernet0/0.14
description -=I=- Internet over ISP2 -=I=-
encapsulation dot1Q 14
ip address 122.164.8.17 255.255.255.248
ip access-group ACL_INET_OUT_ISP2 out
ip nat outside
ip virtual-reassembly
no cdp enable
!
interface FastEthernet0/1
no ip address
duplex auto
speed auto
!
interface FastEthernet0/1.10
description to -=I=- LAN -=I=-
encapsulation dot1Q 10
ip address 10.10.10.200 255.255.255.0
ip nat inside
ip virtual-reassembly
no cdp enableSet up pools for NAT:
ip nat pool ISP1-PUBLIC-IP 164.122.12.9 164.122.12.9 netmask 255.255.255.248
ip nat pool ISP2-PUBLIC-IP 122.164.8.17 122.164.8.17 netmask 255.255.255.248Access lists (ACL):
ACL'i for interfaces, so that no one breaks :)
ip access-list extended ACL_INET_OUT_ISP1
deny ip any 10.0.0.0 0.255.255.255 log-input
deny ip any 172.16.0.0 0.15.255.255 log-input
deny ip any 192.168.0.0 0.0.255.255 log-input
permit ip host 164.122.12.9 any
deny ip any any log-input
ip access-list extended ACL_INET_OUT_ISP2
deny ip any 10.0.0.0 0.255.255.255 log-input
deny ip any 172.16.0.0 0.15.255.255 log-input
deny ip any 192.168.0.0 0.0.255.255 log-input
permit ip host 122.164.8.17 any
deny ip any any log-inputACL'i for those who are online:
ip access-list extended ACL_NAT-INET_OUT_ISP1
remark /--------------------------------------
remark Black Hole RFC 1918
remark --------------------------------------/
deny ip any 10.0.0.0 0.255.255.255 log-input
deny ip any 172.16.0.0 0.15.255.255 log-input
deny ip any 192.168.0.0 0.0.255.255 log-input
remark /--------------------------------------
remark SMTP For Exchange
remark --------------------------------------/
permit tcp host 10.10.10.254 any eq smtp
deny tcp any any eq smtp log-input
remark /--------------------------------------
remark WSUS
remark --------------------------------------/
permit ip host 10.10.10.251 any
remark /--------------------------------------
remark Full Aceess for Odmins
remark --------------------------------------/
permit ip host 10.10.10.10 any
remark /--------------------------------------
remark Access for Exchange
remark --------------------------------------/
permit ip host 10.10.10.254 any
remark /--------------------------------------
remark Deny SMTP for TI (gate)
remark --------------------------------------/
deny tcp host 10.10.10.249 eq smtp any log-input
remark /--------------------------------------
remark Access to Internet for TI (gate)
remark --------------------------------------/
permit ip host 10.10.10.249 any
remark /--------------------------------------
remark Self
remark --------------------------------------/
permit ip host 164.122.12.9 any
remark /--------------------------------------
remark Deny All
remark --------------------------------------/
deny ip any any log-input
ip access-list extended ACL_NAT-INET_OUT_ISP2
remark /--------------------------------------
remark Black Hole RFC 1918
remark --------------------------------------/
deny ip any 10.0.0.0 0.255.255.255 log-input
deny ip any 172.16.0.0 0.15.255.255 log-input
deny ip any 192.168.0.0 0.0.255.255 log-input
remark /--------------------------------------
remark SMTP For Exchange
remark --------------------------------------/
permit tcp host 10.10.10.254 any eq smtp
deny tcp any any eq smtp log-input
remark /--------------------------------------
remark WSUS
remark --------------------------------------/
permit ip host 10.10.10.251 any
remark /--------------------------------------
remark Full Aceess for Odmins
remark --------------------------------------/
permit ip host 10.10.10.10 any
remark /--------------------------------------
remark Access for Exchange
remark --------------------------------------/
permit ip host 10.10.10.254 any
remark /--------------------------------------
remark Deny SMTP for TI (gate)
remark --------------------------------------/
deny tcp host 10.10.10.249 eq smtp any log-input
remark /--------------------------------------
remark Access to Internet for TI (gate)
remark --------------------------------------/
permit ip host 10.10.10.249 any
remark /--------------------------------------
remark Self
remark --------------------------------------/
permit ip host 122.164.8.17 any
remark /--------------------------------------
remark Deny All
remark --------------------------------------/
deny ip any any log-inputRoute-map:
route-map NAT-TO-ISP1 permit 10
description -= Routing/NAT to ISP1, outgoing traffic =-
match ip address ACL_NAT-INET_OUT_ISP1
match interface FastEthernet0/0.12
!
route-map NAT-TO-ISP2 permit 10
description -= Routing/NAT to ISP2, outgoing traffic =-
match ip address ACL_NAT-INET_OUT_ISP2
match interface FastEthernet0/0.14And now the most interesting is tracking:
track 100 list boolean and
object 101
object 102
object 103object 104
delay down 2 up 3
!
track 101 interface FastEthernet0/0.12 line-protocol
delay down 2 up 5
!
track 102 interface FastEthernet0/1 line-protocol
delay down 2 up 5
!
track 103 ip route 164.122.12.9 255.255.255.248 reachability
delay down 2 up 5
!track 104 ip sla 104
delay down 2 up 5
!
track 200 list boolean and
object 201
object 202
object 203object 204
delay down 2 up 3
!
track 201 interface FastEthernet0/0.14 line-protocol
delay down 2 up 5
!
track 202 interface FastEthernet0/1 line-protocol
delay down 2 up 5
!
track 203 ip route 122.164.8.17 255.255.255.248 reachability
delay down 2 up 5
!track 204 ip sla 204
delay down 2 up 5
and routes:
ip route 0.0.0.0 0.0.0.0 164.122.12.9 10 tag 100 name -=[ISP1]=- track 100
ip route 0.0.0.0 0.0.0.0 122.164.8.17 20 tag 200 name -=[ISP2]=- track 200and now actually what we check the availability of our gateways:
ip sla 104
icmp-echo 164.122.12.9 source-interface FastEthernet0 / 0.12
request-data-size 1
timeout 700
threshold 600
frequency 30
ip sla schedule 104 life forever start-time now
ip sla 204
icmp-echo 122.164.8.17 source-interface FastEthernet0 / 0.14
request-data-size 1
timeout 700
threshold 600
frequency 30
ip sla schedule 204 life forever start-time now
Source: https://habr.com/ru/post/70801/
All Articles