Sources of 3300 global Internet projects were received.
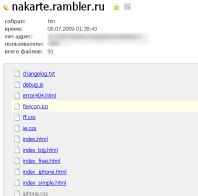 A couple of months ago, we ( 2 Comrades and Anton Isaykin ) discovered a vulnerability inherent mainly in large Internet projects (such as Rambler, Mail, Yandex, Opera, etc.). It was possible to get access to the file structures of the most famous sites (a total of 3320 sites) and in some cases their full source codes.
A couple of months ago, we ( 2 Comrades and Anton Isaykin ) discovered a vulnerability inherent mainly in large Internet projects (such as Rambler, Mail, Yandex, Opera, etc.). It was possible to get access to the file structures of the most famous sites (a total of 3320 sites) and in some cases their full source codes.It would seem that in the XXI century it is difficult to find such a vulnerability. It seems that everything has already been found, and what is not found is sitting somewhere very, very deep. It turned out that the root of today's evil is a completely everyday thing. Surely each of you ever dealt with the SVN version control system.
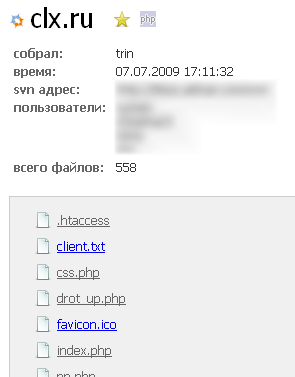
SVN is an advanced tool for organizing the joint development of dozens or even hundreds of developers. Due to the nature of the architecture, SVN stores its own metafiles in each project directory, neatly folded into a hidden .svn directory. In one of the files called entries is a list of all files and directories located in the same folder as .svn . Also there is information about the location of the repository, the size of the files, the date they were changed and the logins of the users working on the project. Already not bad, right? I will explain, it turns out, if a project is developed using SVN, then looking at draftcopy.ru/.svn/entries we will see the file structure of the project root with the authors, recent changes, a link to the main branch of the repository and so forth.
 But you can go further. In the same .svn folder is the text-base directory, which contains the latest versions of all files in the repository. The picture is also complemented by the fact that the files do not have a standard extension (for example .php), which allows them to be immediately sent to the interpreter, but an additional extension .svn-base , due to which the file is given to the person who requested it "as is", i.e. . bare source code!
But you can go further. In the same .svn folder is the text-base directory, which contains the latest versions of all files in the repository. The picture is also complemented by the fact that the files do not have a standard extension (for example .php), which allows them to be immediately sent to the interpreter, but an additional extension .svn-base , due to which the file is given to the person who requested it "as is", i.e. . bare source code!')
draftcopy.ru/.svn/text-base/index.php.svn-base
It is worth noting that the picture described is ideal and, although it was in most cases, a large percentage of the source codes could not be obtained for one reason or another.
Having realized for the first time that the discovered vulnerability has been inherent in most projects over the past nine years, it was decided to completely scan the Runet to see what the Internet projects are doing and to get interesting statistics. But before the story about how it was, you should tell gray admins how to defend against this ...
Vulnerability Protection
Vulnerability can be circumvented in several ways. The way to the forehead is to prohibit accessing the SVN metadirectories on port 80, i.e. by means of a web server.
Nginx solution
location ~ /.svn/ {
deny all;
}
nginx` , server . , . — .
Apache
<Directory ~ ".*\.svn">
Order allow,deny
Deny from all
Satisfy All
</Directory>
, httpd.conf apache .svn .
SVN
— . , , , . . svn export .twocomrades.ru
, . -, ru. , . , 3000 .
, , , 200 500 , js-. - 200 , .
, . 4 . . , ( com 700 ( 2 ru)).
- , , . , , , . .
, . (yandex.ru, rambler.ru, mail.ru, opera.com, rbc.ru, 003.ru, bolero.ru, habrahabr.ru, 19 ), , , 3000+ .
opera.com .
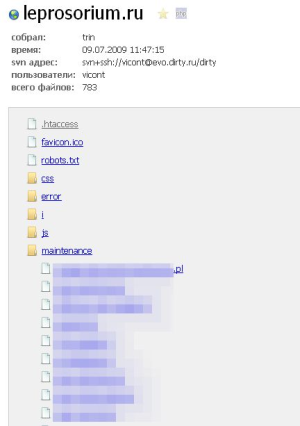
:
: 2253388: 3320
, . , . , . , .
, …
:
- SVN, ;
- CSS CSS $make 0_0;
- 0_0, « » ;
- «» ;
- MySQL, html ;
- CodeIgniter;
PostgreSQL wikimedia => PostgreSQL MySQL ;-);-(- ( ) perl.
- 10 «hack» «secure» ;
- , phpmyadmin «__xpma123uff__» , ;
- inc , .php, .
P.S. , .
P.S.S. :
- , , .
- . .
P.P.P.S. oowl.
P.P.P.P.S. , . , xmlapi, xsl . , , . , , .
, , - nginx :
- Q: ?
A: , , — - , .svn , .svn. -, , .svn. - Q: nginx URL ( server, )?
A: . , , .


Source: https://habr.com/ru/post/70330/
All Articles