XSS vulnerability on Futurico.ru
I found a semi-active XSS vulnerability on Futurico.ru.
It's simple: enter a message on the site (small phrase).
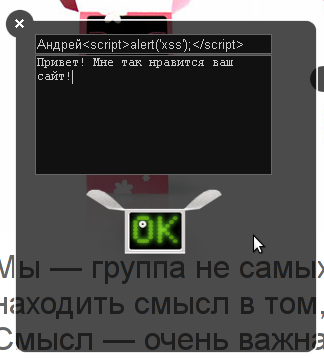
Then we find out the message id - we take out the POST parameters when loading:

And now just pass futurico.ru/map/getPointInfo.php?point= **** POST-parameter using the GET method and see our message:
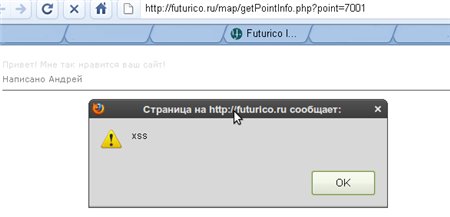
No filtering.
At the moment, the developers have partially disabled the "small phrases", but you can still write messages and contact them id.
More information can be found here.
It's simple: enter a message on the site (small phrase).

Then we find out the message id - we take out the POST parameters when loading:

And now just pass futurico.ru/map/getPointInfo.php?point= **** POST-parameter using the GET method and see our message:

No filtering.
At the moment, the developers have partially disabled the "small phrases", but you can still write messages and contact them id.
More information can be found here.
')
Source: https://habr.com/ru/post/65602/
All Articles