Access Control Systems
As any theater begins with a hanger, so any information security system begins with ensuring the physical security of the information system itself, regardless of its type, size or cost.
In physical security, the term “access control” refers to the practice of restricting access to property, to buildings or premises, access to which is allowed only to authorized people. Physical access control can be achieved through the use of a person (guard, bouncer or employee at the reception), through mechanical methods such as locks and keys on the door, or through technological means such as access systems based on access cards or biometric identification.
It is obvious that in order to ensure the security of the home information system, it is necessary at least to lock the doors with a key before leaving. Otherwise, you will have only two entertainments: the recovery of lost data and the hope that the information that is valuable for you was encrypted ...
')

In most companies that use information systems for work, at the entrance, if not to the workroom, then the building is a specially trained person with the words “security” or “security service” on a badge or on the back :), which usually requires you to show a pass those who work in this building and write to the journal everyone who does not work in this building / room, but for some business matters must go inside. According to legend, he does this so that in case of loss of property, he can quickly find someone who could do it from outsiders. As a rule, modern office premises are equipped with video surveillance cameras, so in case of illegal actions of visitors they can be easily identified. Ideally, a specially trained guard should sit next to each door in the room, check passes and record who entered and left at what time (or better 2 in case one of the guards wants to move for a minute).
In addition to the guard, the doors to the premises should be locked (at least from the same guards :)).

If with locks everything is more or less clear (each house has an entrance door locked, or even several), then with security guards who accurately record every door opening in the log usually do not even have time to cause problems, since it is too unprofitable to contain such a break through people not entertaining in the immediate workflow of the company, which brings the main profit.
In order to reduce the costs of security personnel and increase the level of physical security, access control systems (in buildings and rooms) are used. Immediately, I’ll make a reservation that the presence of a guard in the person’s face is still necessary, so we will no longer touch on this issue, since it goes beyond the scope of the topic.
The access control system determines who is allowed to enter or exit, where they are allowed to exit or exit, where they are allowed to exit or exit, and when they are allowed to enter or exit. In this case, they mean those who have a pass (that is, the right of access), those who do not have a pass, where, where and when to enter / leave should not be concerned.
Electronic access control uses the power of computers to solve problems associated with the limitations imposed by mechanical locks and keys (and to the extent described by security guards). The electronic system determines whether it is possible to gain access to the protected area, based on the granted permission (pass). If access is obtained, the door opens for a certain time period and this action will be recorded in the system. If access is denied, the door will remain closed and the access attempt will also be recorded. The system will also monitor the door and give an alarm if the door is opened with the use of brute force, or if the door remains open for too long a time (suddenly someone deliberately left the door open so that an outsider could get inside).

Access control points can be doors, turnstiles, gates, barriers, parking spaces, elevators or other physical barriers where access can be controlled by electronics. Typically, the access control point is a door, and access is controlled by a magnetic lock and card reader.
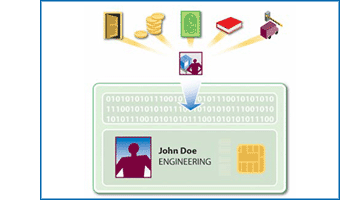
The main user interface with the access control system is a smartcard reader. Reader depends on smartcard technology. Readers of magnetic stripes, bar codes, or Weigand cards are usually called contact readers and are most often used in stores and ATMs. Some contact readers require that the card be held at a certain distance so that the data can be read well. Readers for proximity or contactless smartcards are actually radio transmitters. The reader's broadcast field activates the card, which then begins broadcasting with the reader. Smart cards with gold-plated contacts visible on the front of the card are known as contact smart cards and require the same gold-plated contacts on the reader to physically touch the contacts of the card in order to transfer data. Biometric readers are unique in their technological use, but they always require the user to present their body parts, be it touching the reader to present fingerprints or hand geometry, or having to look into the camera to recognize the face, scan the iris and retina, or pronounce some phrases into the microphone for voice recognition.
Simply put, the one who has the right to access the premises (pass) presents a pass to the system (brings it to the proximity reader) and either the door opens or does not open, but in any case such an event is automatically recorded in the system.
Of course, starting up a stormy activity to install an access control system to a room of 15 square meters, in which 3 people are sitting, does not make much sense.
But for a large enough company that has several buildings in different cities, it is worth thinking about the introduction of a full-fledged access control system in order to increase the general level of security, including information.
Suppose the company “whose name is not very important for us” has several regional branches. Moreover, the regions are quite decently separated from each other. With some regions, only satellite communication channel with appropriate bandwidth and other delights associated with the time delay of signal propagation can be used for communication, as shown in the figure.

Each branch has several large buildings in large cities. The communication lines between the buildings are of sufficient quality, therefore they are not displayed in the following figure.

The figure also shows the number of smartcard readers. The fact is that the access control system controllers are installed based on the number of proximity readers (i.e., in fact, the controller's power and price depends on the number of card readers). For a building in the minimum configuration of providing physical protection by means of access control systems, it is necessary to put readers on the main and emergency entrances, warehouse, server room, director's office, information security office (one for each side of the door, that is, 2 readers for the door). Total for the building you need to install 12 readers on average, because there will be variations with those premises that it is desirable to limit inside the building itself (it can be a clean room, a laboratory, a room for secret negotiations, an electrical substation, a garage, etc.). In addition, it is necessary to take into account the fact that each building has security and fire alarm systems (according to the requirements of the relevant authorities) and a video surveillance system, which must be properly linked to the access control system for ease of management.
For such a large system I want to formulate the requirements. Any details like “the system must support proximity readers and smart cards and log events of entry and exit from the room” will not be described here in view of their obviousness.
Let us dwell on the main points, and benifits, which I would like to get as a result of using such a system:
• Access control
• Time tracking
• Improving the quality of protection
• Control of autonomous objects, on which there is no resident security and maintenance personnel (PBX and power centers)
• Reducing the likelihood of material damage through theft.
• Documentation and the possibility of a retrospective of all events on the entrance / exit to the premises
• Integration with current IT infrastructure
• Integration with already installed security, fire alarm and video surveillance systems.
• Exclusion of unauthorized access to workplaces (AWP).
• Differentiated control for different groups of employees.
• Possibility of unlimited scaling of the access control system to the interregional level
Say what should be avoided at the initial stage of choosing a platform for access control:
• Use of non-industrial databases (in this case there will be a problem with specialists capable of working with this database, as well as the problem of transferring data to / from the database / base, not to mention the timely installation of updates and the removal of critical vulnerabilities of such systems, and more recently also the requirements of the law "on personal data")
• Lack of integration with Active Directory, in which there are already records about all employees of the company (you will have to duplicate information in the ACS database, and you will have difficulty guaranteeing the consistency of data within different IT systems)
• Lack of scalability to all branches of the company (if the system initially does not support the possibility of such scaling, then if this problem occurs, its solution will be impossible without a complete change of key equipment ACS)
• Lack of a single point of control of the system (the absence of one responsible for the system, and it will also be impossible to say what happens with access to objects if the system is not centrally controlled)
Additional requirements related to system scaling:
• The system should have an open architecture for easy integration of other components into it.
• Ensure easy system scaling to the interregional level
• Provide support for remote autonomous objects over thin TCP / IP channels (56 kbps)
• Use industrial DBMS (Oracle or MS SQL)
• Have integration with Active Directory
• Ensuring that cards can be used not only for access to the premises, but also for two-step user authorization.
More or less, all of the above requirements are satisfied by the OnGuard system.
Enterprice from Lenel Systems, shown in the figure below.
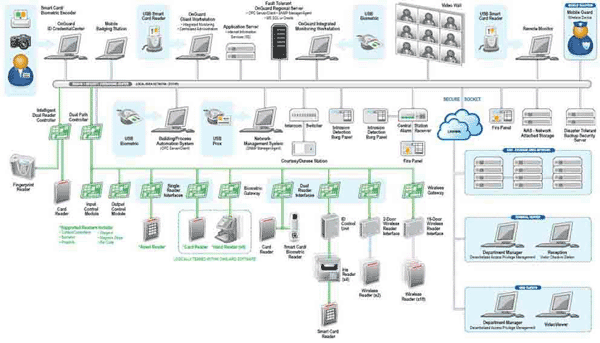
A better picture and useful information can be found in the brochure on this system .
What is remarkable in this system (do not count for advertising, just in time had to view about fifty different access control systems of both domestic and foreign developments):
Functional features and capabilities:
• Open architecture
• Use of ready standard software products
• Centralized management of the integrated security system
• Preserving the independence of local systems
• Centralized database (any relational to the customer's choice)
• Using a single ID card
• Scalability to the level of large interregional systems
• Interface for working with databases of HR systems
• Synchronize data across multiple databases across a LAN / WAN
• Simultaneous monitoring of events and alarms in multiple regions from a single workstation
• Segmented database architecture
Systems for which there are built-in interfaces:
• Passing system
• Digital CCTV systems
• Security alarm
• Visitor Management
• Protection of information
• Property Management
• Email
• Human Resource Management
• Time tracking
Elements of an integrated security system whose support is not limited quantitatively:
• Regional servers
• Access cards
• Time zones
• Monitoring stations
• Access Levels
• Relay outputs
+ Integration with Active Directory and other IT systems through proprietary software called OpenIT.
The last point is the most important, because Most of these systems do not have integration with Active Directory, but in vain, because this is a big plus for large companies. Many systems integrate video surveillance and alarm systems well, OnGuard can also be combined with security and fire alarm systems and a video surveillance system.
Let's compare the system from Lenel Systems with the most popular access control system of domestic production Perco by several criteria. We will compare the most advanced versions of both manufacturers:

What can be said from the results of the comparison. Perco developers need to work on the system. For those who want to use the Perco access control system in order to close more than one door or a turnstile for a real company with more than 300 employees, it will be possible to experience some of the advantages of proprietary systems and the quality of technical support for domestic software. manufacturers.
On this dwell on the negative reviews.

Now let's look at the advantages that the system uses to use an industrial database management system (Oracle or MS SQL) and integration with Active Directory. First, such a system can be easily integrated with existing personnel records systems. Secondly, you can use a slightly modified access card to organize two-factor user authentication at the workstation, thus forcing the user to block the workstation before leaving the room even for a few minutes. Thirdly, since the system will interact with Active Directory, the same cards can be used, for example, to pay for meals in the cafeteria and not to scoop money in your pockets. You can use the usual and bank cards for such a case, but it is much more interesting to mate with the accounting program and eat at the expense of salary (especially since the company can thus reduce tax deductions).
In general, if you decide to install an access control system, then remember that a simple supervisor who can accurately record the time of arrival and departure of a person can provide an account of working time. And to create an easy-to-use and administering system that provides automatic access control for each employee according to an individual scheme associated with alarm systems in video surveillance, which can be further expanded to several buildings without changing equipment, it is better to find something with an open architecture, industrial databases and integration with Active Directory. And the most important thing is not to give the personnel department too much authority to work with this system, otherwise they will turn it into a tool to blackmail employees for being late and absent in the workplace.
A couple of words about the essence, instead of introducing.
In physical security, the term “access control” refers to the practice of restricting access to property, to buildings or premises, access to which is allowed only to authorized people. Physical access control can be achieved through the use of a person (guard, bouncer or employee at the reception), through mechanical methods such as locks and keys on the door, or through technological means such as access systems based on access cards or biometric identification.
It is obvious that in order to ensure the security of the home information system, it is necessary at least to lock the doors with a key before leaving. Otherwise, you will have only two entertainments: the recovery of lost data and the hope that the information that is valuable for you was encrypted ...
')

In most companies that use information systems for work, at the entrance, if not to the workroom, then the building is a specially trained person with the words “security” or “security service” on a badge or on the back :), which usually requires you to show a pass those who work in this building and write to the journal everyone who does not work in this building / room, but for some business matters must go inside. According to legend, he does this so that in case of loss of property, he can quickly find someone who could do it from outsiders. As a rule, modern office premises are equipped with video surveillance cameras, so in case of illegal actions of visitors they can be easily identified. Ideally, a specially trained guard should sit next to each door in the room, check passes and record who entered and left at what time (or better 2 in case one of the guards wants to move for a minute).
In addition to the guard, the doors to the premises should be locked (at least from the same guards :)).

If with locks everything is more or less clear (each house has an entrance door locked, or even several), then with security guards who accurately record every door opening in the log usually do not even have time to cause problems, since it is too unprofitable to contain such a break through people not entertaining in the immediate workflow of the company, which brings the main profit.
In order to reduce the costs of security personnel and increase the level of physical security, access control systems (in buildings and rooms) are used. Immediately, I’ll make a reservation that the presence of a guard in the person’s face is still necessary, so we will no longer touch on this issue, since it goes beyond the scope of the topic.
The access control system determines who is allowed to enter or exit, where they are allowed to exit or exit, where they are allowed to exit or exit, and when they are allowed to enter or exit. In this case, they mean those who have a pass (that is, the right of access), those who do not have a pass, where, where and when to enter / leave should not be concerned.
Electronic access control uses the power of computers to solve problems associated with the limitations imposed by mechanical locks and keys (and to the extent described by security guards). The electronic system determines whether it is possible to gain access to the protected area, based on the granted permission (pass). If access is obtained, the door opens for a certain time period and this action will be recorded in the system. If access is denied, the door will remain closed and the access attempt will also be recorded. The system will also monitor the door and give an alarm if the door is opened with the use of brute force, or if the door remains open for too long a time (suddenly someone deliberately left the door open so that an outsider could get inside).

Access control points can be doors, turnstiles, gates, barriers, parking spaces, elevators or other physical barriers where access can be controlled by electronics. Typically, the access control point is a door, and access is controlled by a magnetic lock and card reader.

The main user interface with the access control system is a smartcard reader. Reader depends on smartcard technology. Readers of magnetic stripes, bar codes, or Weigand cards are usually called contact readers and are most often used in stores and ATMs. Some contact readers require that the card be held at a certain distance so that the data can be read well. Readers for proximity or contactless smartcards are actually radio transmitters. The reader's broadcast field activates the card, which then begins broadcasting with the reader. Smart cards with gold-plated contacts visible on the front of the card are known as contact smart cards and require the same gold-plated contacts on the reader to physically touch the contacts of the card in order to transfer data. Biometric readers are unique in their technological use, but they always require the user to present their body parts, be it touching the reader to present fingerprints or hand geometry, or having to look into the camera to recognize the face, scan the iris and retina, or pronounce some phrases into the microphone for voice recognition.
Simply put, the one who has the right to access the premises (pass) presents a pass to the system (brings it to the proximity reader) and either the door opens or does not open, but in any case such an event is automatically recorded in the system.
Nontrivial implementation case.
Of course, starting up a stormy activity to install an access control system to a room of 15 square meters, in which 3 people are sitting, does not make much sense.
But for a large enough company that has several buildings in different cities, it is worth thinking about the introduction of a full-fledged access control system in order to increase the general level of security, including information.
Suppose the company “whose name is not very important for us” has several regional branches. Moreover, the regions are quite decently separated from each other. With some regions, only satellite communication channel with appropriate bandwidth and other delights associated with the time delay of signal propagation can be used for communication, as shown in the figure.

Each branch has several large buildings in large cities. The communication lines between the buildings are of sufficient quality, therefore they are not displayed in the following figure.

The figure also shows the number of smartcard readers. The fact is that the access control system controllers are installed based on the number of proximity readers (i.e., in fact, the controller's power and price depends on the number of card readers). For a building in the minimum configuration of providing physical protection by means of access control systems, it is necessary to put readers on the main and emergency entrances, warehouse, server room, director's office, information security office (one for each side of the door, that is, 2 readers for the door). Total for the building you need to install 12 readers on average, because there will be variations with those premises that it is desirable to limit inside the building itself (it can be a clean room, a laboratory, a room for secret negotiations, an electrical substation, a garage, etc.). In addition, it is necessary to take into account the fact that each building has security and fire alarm systems (according to the requirements of the relevant authorities) and a video surveillance system, which must be properly linked to the access control system for ease of management.
For such a large system I want to formulate the requirements. Any details like “the system must support proximity readers and smart cards and log events of entry and exit from the room” will not be described here in view of their obviousness.
Let us dwell on the main points, and benifits, which I would like to get as a result of using such a system:
• Access control
• Time tracking
• Improving the quality of protection
• Control of autonomous objects, on which there is no resident security and maintenance personnel (PBX and power centers)
• Reducing the likelihood of material damage through theft.
• Documentation and the possibility of a retrospective of all events on the entrance / exit to the premises
• Integration with current IT infrastructure
• Integration with already installed security, fire alarm and video surveillance systems.
• Exclusion of unauthorized access to workplaces (AWP).
• Differentiated control for different groups of employees.
• Possibility of unlimited scaling of the access control system to the interregional level
Say what should be avoided at the initial stage of choosing a platform for access control:
• Use of non-industrial databases (in this case there will be a problem with specialists capable of working with this database, as well as the problem of transferring data to / from the database / base, not to mention the timely installation of updates and the removal of critical vulnerabilities of such systems, and more recently also the requirements of the law "on personal data")
• Lack of integration with Active Directory, in which there are already records about all employees of the company (you will have to duplicate information in the ACS database, and you will have difficulty guaranteeing the consistency of data within different IT systems)
• Lack of scalability to all branches of the company (if the system initially does not support the possibility of such scaling, then if this problem occurs, its solution will be impossible without a complete change of key equipment ACS)
• Lack of a single point of control of the system (the absence of one responsible for the system, and it will also be impossible to say what happens with access to objects if the system is not centrally controlled)
Additional requirements related to system scaling:
• The system should have an open architecture for easy integration of other components into it.
• Ensure easy system scaling to the interregional level
• Provide support for remote autonomous objects over thin TCP / IP channels (56 kbps)
• Use industrial DBMS (Oracle or MS SQL)
• Have integration with Active Directory
• Ensuring that cards can be used not only for access to the premises, but also for two-step user authorization.
More or less, all of the above requirements are satisfied by the OnGuard system.
Enterprice from Lenel Systems, shown in the figure below.

A better picture and useful information can be found in the brochure on this system .
What is remarkable in this system (do not count for advertising, just in time had to view about fifty different access control systems of both domestic and foreign developments):
Functional features and capabilities:
• Open architecture
• Use of ready standard software products
• Centralized management of the integrated security system
• Preserving the independence of local systems
• Centralized database (any relational to the customer's choice)
• Using a single ID card
• Scalability to the level of large interregional systems
• Interface for working with databases of HR systems
• Synchronize data across multiple databases across a LAN / WAN
• Simultaneous monitoring of events and alarms in multiple regions from a single workstation
• Segmented database architecture
Systems for which there are built-in interfaces:
• Passing system
• Digital CCTV systems
• Security alarm
• Visitor Management
• Protection of information
• Property Management
• Human Resource Management
• Time tracking
Elements of an integrated security system whose support is not limited quantitatively:
• Regional servers
• Access cards
• Time zones
• Monitoring stations
• Access Levels
• Relay outputs
+ Integration with Active Directory and other IT systems through proprietary software called OpenIT.
The last point is the most important, because Most of these systems do not have integration with Active Directory, but in vain, because this is a big plus for large companies. Many systems integrate video surveillance and alarm systems well, OnGuard can also be combined with security and fire alarm systems and a video surveillance system.
Let's try to compare the two systems.
Let's compare the system from Lenel Systems with the most popular access control system of domestic production Perco by several criteria. We will compare the most advanced versions of both manufacturers:

What can be said from the results of the comparison. Perco developers need to work on the system. For those who want to use the Perco access control system in order to close more than one door or a turnstile for a real company with more than 300 employees, it will be possible to experience some of the advantages of proprietary systems and the quality of technical support for domestic software. manufacturers.
On this dwell on the negative reviews.

Now let's look at the advantages that the system uses to use an industrial database management system (Oracle or MS SQL) and integration with Active Directory. First, such a system can be easily integrated with existing personnel records systems. Secondly, you can use a slightly modified access card to organize two-factor user authentication at the workstation, thus forcing the user to block the workstation before leaving the room even for a few minutes. Thirdly, since the system will interact with Active Directory, the same cards can be used, for example, to pay for meals in the cafeteria and not to scoop money in your pockets. You can use the usual and bank cards for such a case, but it is much more interesting to mate with the accounting program and eat at the expense of salary (especially since the company can thus reduce tax deductions).
Inference.
In general, if you decide to install an access control system, then remember that a simple supervisor who can accurately record the time of arrival and departure of a person can provide an account of working time. And to create an easy-to-use and administering system that provides automatic access control for each employee according to an individual scheme associated with alarm systems in video surveillance, which can be further expanded to several buildings without changing equipment, it is better to find something with an open architecture, industrial databases and integration with Active Directory. And the most important thing is not to give the personnel department too much authority to work with this system, otherwise they will turn it into a tool to blackmail employees for being late and absent in the workplace.
Source: https://habr.com/ru/post/65549/
All Articles