JSON hijacking
.jpg) The article discusses the method of intercepting data sent via JSON using the " __defineSetter__ " method. This vulnerability affects JSON sites from which: contains confidential data (otherwise not sports), is a valid JS object, is sent via a GET request. Requirements for the victim: the browser supports JavaScript, it is enabled, the __defineSetter__ method is supported.
The article discusses the method of intercepting data sent via JSON using the " __defineSetter__ " method. This vulnerability affects JSON sites from which: contains confidential data (otherwise not sports), is a valid JS object, is sent via a GET request. Requirements for the victim: the browser supports JavaScript, it is enabled, the __defineSetter__ method is supported.Thus, if you do not pass sensitive data to JSON, or give it only to a POST request, your site is not specifically affected by this vulnerability. The author of the article even made a few diagrams in Visio. To demonstrate the process, let's get started.
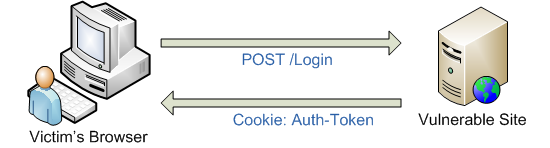
In the first illustration, we see the victim log in to the vulnerable site and receive a “cookie”, which is carefully stored by the browser, which is clear to everyone.
')
After that, sooner or later, the bad guy sends a message to the victim (in the illustration - email) with a link to the video of the piano hamster.
But in actual fact, the link leads to the bad guy website. Accordingly, what happens: the victim's browser loads the page from the bad guy's website.
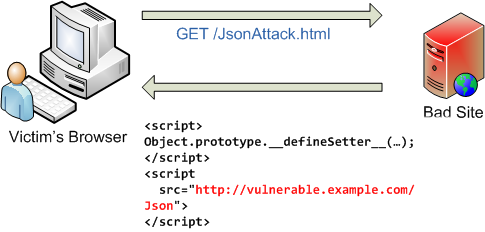
On the requested page is a little javascript with overriding the __defineSetter__ method and a link to external javascript. When the browser stumbles upon external javascript, it sends a GET request, with identification data to the vulnerable site, receiving JSON with confidential data in response.
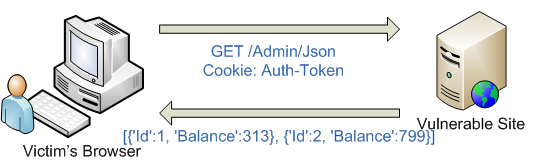
Now the bad guy has access to confidential data.
Source: https://habr.com/ru/post/63176/
All Articles