Infected sites - the scourge of Runet
It is worth noting immediately that this is the scourge of not only the Runet, but the entire Network. But over the past couple of months I have been witnessing just a wild increase in the number of such sites in RuNet.
Over the past couple of months, more than a dozen people have come to me who have this kind of problem on their websites. It helped everyone, everyone is happy, but for people it ate money, time, nerves and positions in search engines.
What are “site viruses”? As a rule, this is a banal frame, which either spins the screenings of some porn pages, or, more often, tries to load a copy of the Trojan for your operating system through the holes in the browsers.
')
Basically, these are viruses of the Downloader.JS. * Family.
Trojans, on the other hand, can perform a wide variety of functions, from stealing various e-wallets and money on them, to stealing passwords to ftp and ssh from hosting sites to infect new sites.
Passwords, no matter how well they are encrypted, can be pulled out from almost any program, for example from Far Commander or Mozilla Firefox, it’s easier to get them out. And the list of such programs is quite extensive, in fact - all popular browsers and ftp-clients.
Retrieved passwords from ftp Trojan sends to the server, the uterus, which in a certain way handles them, and puts in a queue for infection. It sounds a little crazy, but in fact it is ridiculously easy to implement. The only difficulty that I see right now is to ensure the high speed of the malicious script.
These same scripts, logging in to FTP, are traversed in all directories recursively, injecting their code into certain files. As a rule, they can be called two masks: index. * And * .js. Typically, these scripts embed code in different ways, for example, a regular frame, or a call to a remote JS that draws the same frame. There are a lot of ways.
(clickable)
Often malicious code is disguised as popular services, for example, under Google Analytics or counter from LiveInternet.
If we, as competent users, can deal with the direct threat of a computer infection, the threat to the sites themselves will be more difficult.
First, from the moment of infection, your website, or even websites, is a peddler of infection, and if your audience is a girl schoolgirl, then there is a great chance that there will be quite a lot of infected machines.
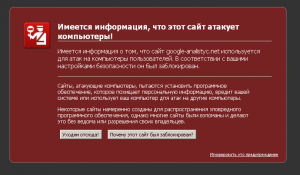
Secondly, all modern browsers block infected sites based on statistics from specialized Google search robots. It looks like the picture above. Naturally, your E-store, business card site or just a blog will be sharply negative. The client or reader is not so long to lose.
Thirdly, if the infected site hangs long enough without removing the malicious code, it begins to roll down from the positions in the search engines. Accurately rolls in Yandex and Google. For the rest, I'm not sure. Plus, in the issue of Google in front of the infected site is a mark, they say the site is dangerous, beware.
It also often happens because of the site owner’s fault, as many overlap the index file with htaccess with a page with a concise “Technical work”. But in this case, it is better to temporarily lose ground than to allow the site to further infect people while you correct the effects of the infection.
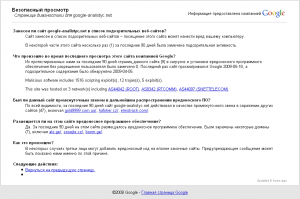
By the way, this is what Google says on the google-analistyc.net page:
(clickable)
As a result, you can get rid of the infection, in fact, in two ways. For example, if your sites include malicious code that leads to google-analistyc.net, then this code will help you:
Accordingly, if you find that there are two or three types of malicious code, you can quickly clean it out in such an uncomplicated way.
The second way is with your hands. Sometimes I had to edit files with my hands, because all the malicious code was completely different, and I could not write a regular expression for it.
After you delete all the malicious code, carefully watch what is loaded on the page, for example using firebug for firefox. Perhaps you missed something.
Well, about changing the password on ftp and checking your machine with an antivirus, I will say nothing at all - I think you yourself have guessed that it needs to be changed first.
In order to get rid of the red yoke on the site (see the first picture), you will need to crank a couple of simple events and wait about a week. Although the Russian support of Google beats the heel in the chest and insists that less than a month, well, nothing will come of it. It turns out, and only go.
It's simple, you need to go to the panel of Webmasters Google (and if it is not, then register and validate the site), and send a request for consideration. Considers of course robots, because you need to clean it well. If, when considered, which you yourself asked for, your site will again be recognized as dangerous, the time of its “whitening” increases dramatically.
It turned out a lot, and a little messy.
Ps. For WP, there are several plug-in solutions that will notify you if changes are detected in the files:
- belavir ;
- Paranoid 911 ;
Over the past couple of months, more than a dozen people have come to me who have this kind of problem on their websites. It helped everyone, everyone is happy, but for people it ate money, time, nerves and positions in search engines.
What are “site viruses”? As a rule, this is a banal frame, which either spins the screenings of some porn pages, or, more often, tries to load a copy of the Trojan for your operating system through the holes in the browsers.
')
Basically, these are viruses of the Downloader.JS. * Family.
Trojans, on the other hand, can perform a wide variety of functions, from stealing various e-wallets and money on them, to stealing passwords to ftp and ssh from hosting sites to infect new sites.
Passwords, no matter how well they are encrypted, can be pulled out from almost any program, for example from Far Commander or Mozilla Firefox, it’s easier to get them out. And the list of such programs is quite extensive, in fact - all popular browsers and ftp-clients.
Retrieved passwords from ftp Trojan sends to the server, the uterus, which in a certain way handles them, and puts in a queue for infection. It sounds a little crazy, but in fact it is ridiculously easy to implement. The only difficulty that I see right now is to ensure the high speed of the malicious script.
These same scripts, logging in to FTP, are traversed in all directories recursively, injecting their code into certain files. As a rule, they can be called two masks: index. * And * .js. Typically, these scripts embed code in different ways, for example, a regular frame, or a call to a remote JS that draws the same frame. There are a lot of ways.

(clickable)
Often malicious code is disguised as popular services, for example, under Google Analytics or counter from LiveInternet.
If we, as competent users, can deal with the direct threat of a computer infection, the threat to the sites themselves will be more difficult.
First, from the moment of infection, your website, or even websites, is a peddler of infection, and if your audience is a girl schoolgirl, then there is a great chance that there will be quite a lot of infected machines.
Secondly, all modern browsers block infected sites based on statistics from specialized Google search robots. It looks like the picture above. Naturally, your E-store, business card site or just a blog will be sharply negative. The client or reader is not so long to lose.
Thirdly, if the infected site hangs long enough without removing the malicious code, it begins to roll down from the positions in the search engines. Accurately rolls in Yandex and Google. For the rest, I'm not sure. Plus, in the issue of Google in front of the infected site is a mark, they say the site is dangerous, beware.
It also often happens because of the site owner’s fault, as many overlap the index file with htaccess with a page with a concise “Technical work”. But in this case, it is better to temporarily lose ground than to allow the site to further infect people while you correct the effects of the infection.
By the way, this is what Google says on the google-analistyc.net page:

(clickable)
As a result, you can get rid of the infection, in fact, in two ways. For example, if your sites include malicious code that leads to google-analistyc.net, then this code will help you:
grep -R google-analistyc.net. | awk '{print $ 1}' | cut -d ":" -f 1 | xargs -n1 sed -i "'s | <\! - ~ -> <iframe src = \” http: \ / \ google-analistyc.net \ /in.cgi? 12 \ "width = \" 0 \ " height = \ "0 \" style = \ "display: none \"> <\ / iframe> <\! - ~ -> || g '
Accordingly, if you find that there are two or three types of malicious code, you can quickly clean it out in such an uncomplicated way.
The second way is with your hands. Sometimes I had to edit files with my hands, because all the malicious code was completely different, and I could not write a regular expression for it.
After you delete all the malicious code, carefully watch what is loaded on the page, for example using firebug for firefox. Perhaps you missed something.
Well, about changing the password on ftp and checking your machine with an antivirus, I will say nothing at all - I think you yourself have guessed that it needs to be changed first.
In order to get rid of the red yoke on the site (see the first picture), you will need to crank a couple of simple events and wait about a week. Although the Russian support of Google beats the heel in the chest and insists that less than a month, well, nothing will come of it. It turns out, and only go.
It's simple, you need to go to the panel of Webmasters Google (and if it is not, then register and validate the site), and send a request for consideration. Considers of course robots, because you need to clean it well. If, when considered, which you yourself asked for, your site will again be recognized as dangerous, the time of its “whitening” increases dramatically.
It turned out a lot, and a little messy.
Ps. For WP, there are several plug-in solutions that will notify you if changes are detected in the files:
- belavir ;
- Paranoid 911 ;
Source: https://habr.com/ru/post/59969/
All Articles