Conficker.C. Discovery goal
A brief description of the new virus behavior was published here a few days earlier.
At the end of Wednesday, TrendMicro noticed a new modification of the Conficker.c worm, named WORM_DOWNAD.E. The previous version of the worm uses p2p functionality to download an update that shows many windows with notifications about non-existing threats, as well as annoying pop-up windows, until you agree to pay $ 49.95. Thus, the developers of the virus, finally, opened their goal: profit.
Trend Micro threat research specialist Paul Ferguson (Paul Ferguson) has published a list of changes made by the update, containing some interesting facts.
First, Conficker will end its work on May 3, 2009. During installation, the virus uses a random file name and service name. After installation, the virus removes its previous version. It spreads through MS08-067 vulnerability (which was fixed by Microsoft, so that the updated systems will not be infected) for systems with external ip addresses. If there is no internet connection, it tries to update via the local network. It opens port 5554 and starts broadcasting as an HTTP server, sending SSDP requests.
')
It also connects with myspace.com, msn.com, ebay.com, cnn.com and aol.com.
And after launch, it deletes all entries about itself, including files, history, and registry keys.
Ferguson also noted a connection to the Waledac (another well-known virus) domain (goodnewsdigital.com), and an attempt to download the encrypted print.exe file.
In the latest activity of virus-infected machines, one can observe the downloading of new Waledac binaries and the installation of a false antivirus.
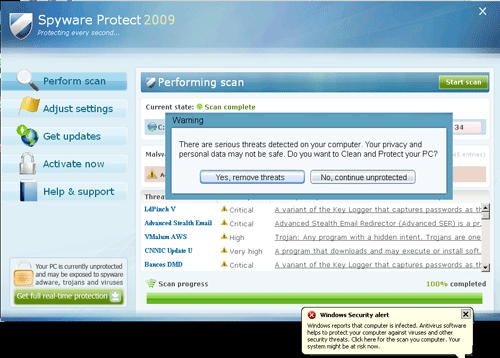
At the end of Wednesday, TrendMicro noticed a new modification of the Conficker.c worm, named WORM_DOWNAD.E. The previous version of the worm uses p2p functionality to download an update that shows many windows with notifications about non-existing threats, as well as annoying pop-up windows, until you agree to pay $ 49.95. Thus, the developers of the virus, finally, opened their goal: profit.
Trend Micro threat research specialist Paul Ferguson (Paul Ferguson) has published a list of changes made by the update, containing some interesting facts.
First, Conficker will end its work on May 3, 2009. During installation, the virus uses a random file name and service name. After installation, the virus removes its previous version. It spreads through MS08-067 vulnerability (which was fixed by Microsoft, so that the updated systems will not be infected) for systems with external ip addresses. If there is no internet connection, it tries to update via the local network. It opens port 5554 and starts broadcasting as an HTTP server, sending SSDP requests.
')
It also connects with myspace.com, msn.com, ebay.com, cnn.com and aol.com.
And after launch, it deletes all entries about itself, including files, history, and registry keys.
Ferguson also noted a connection to the Waledac (another well-known virus) domain (goodnewsdigital.com), and an attempt to download the encrypted print.exe file.
In the latest activity of virus-infected machines, one can observe the downloading of new Waledac binaries and the installation of a false antivirus.

Source: https://habr.com/ru/post/57043/
All Articles