Neverending story
At the request of FkSD , because he does not have enough karma.
Tonight the Kido botnet started working. The event, expected by experts, from April 1 - happened.
Computers infected with Trojan-Downloader.Win32.Kido (aka Conficker.C), interacting with each other through P2P connections, gave the command to the infected machines to download new files.
The new version of Kido (Net-Worm.Win32.Kido.js) is significantly different from the previous versions and has two important differences - this is a worm again and it will work only until May 3, 2009. A more detailed analysis of its functionality is currently underway.
In addition to updating itself, Kido has uploaded new files to infected computers, and this is the most interesting part of this story.
One of the downloaded files is a fake antivirus - FraudTool.Win32.SpywareProtect2009.s
The very first version of Kido, in November last year, also downloaded fake antiviruses into the system. After almost half a year, this functionality is once again used by unknown cybercriminals.
SpywareProtect2009 is hosted on spy-protect-2009.com, spywrprotect-2009.com, spywareprotector-2009
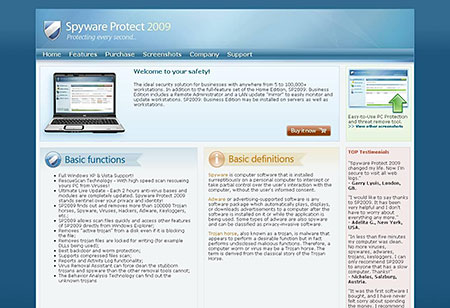
Being launched, it shows the following interface and, according to tradition, offers “delete found viruses”, demanding money for it - $ 49.95


At the moment, support for the spread of this fake antivirus is provided by sites located in Ukraine (131-3.elaninet.com, 78.26.179.107)
The second file that Kido installed on infected systems was Email-Worm.Win32.Iksmas.atz, also known as Waledac. This is a mail worm that has the functionality of data theft and spamming.
Iksmas (Waledac) appeared in January 2009 and even then many experts noticed some similarities in the part of the work algorithms between Kido and them. All the while, there was an epidemic of Kido — a parallel mass epidemic of Iksmas was going on in an email. However, until now there has been no evidence of the connection between these worms.
Tonight, this evidence has appeared - Kido and Iksmas are now present together on infected computers, and a giant botnet designed to send spam has appeared in the hands of evil-minded people.
In addition, according to still unverified information, the sites of some companies and organizations participating in the Conficker Working Group may be under attack.
')
Gostev Alexander, www.secureblog.info
Tonight the Kido botnet started working. The event, expected by experts, from April 1 - happened.
Computers infected with Trojan-Downloader.Win32.Kido (aka Conficker.C), interacting with each other through P2P connections, gave the command to the infected machines to download new files.
The new version of Kido (Net-Worm.Win32.Kido.js) is significantly different from the previous versions and has two important differences - this is a worm again and it will work only until May 3, 2009. A more detailed analysis of its functionality is currently underway.
In addition to updating itself, Kido has uploaded new files to infected computers, and this is the most interesting part of this story.
One of the downloaded files is a fake antivirus - FraudTool.Win32.SpywareProtect2009.s
The very first version of Kido, in November last year, also downloaded fake antiviruses into the system. After almost half a year, this functionality is once again used by unknown cybercriminals.
SpywareProtect2009 is hosted on spy-protect-2009.com, spywrprotect-2009.com, spywareprotector-2009

Being launched, it shows the following interface and, according to tradition, offers “delete found viruses”, demanding money for it - $ 49.95


At the moment, support for the spread of this fake antivirus is provided by sites located in Ukraine (131-3.elaninet.com, 78.26.179.107)
The second file that Kido installed on infected systems was Email-Worm.Win32.Iksmas.atz, also known as Waledac. This is a mail worm that has the functionality of data theft and spamming.
Iksmas (Waledac) appeared in January 2009 and even then many experts noticed some similarities in the part of the work algorithms between Kido and them. All the while, there was an epidemic of Kido — a parallel mass epidemic of Iksmas was going on in an email. However, until now there has been no evidence of the connection between these worms.
Tonight, this evidence has appeared - Kido and Iksmas are now present together on infected computers, and a giant botnet designed to send spam has appeared in the hands of evil-minded people.
In addition, according to still unverified information, the sites of some companies and organizations participating in the Conficker Working Group may be under attack.
')
Gostev Alexander, www.secureblog.info
Source: https://habr.com/ru/post/56879/
All Articles