Downadup worm modification - W32.Downadup.C.

Remember the Downadup worm (Konficker, Kido) ? Do you think this is already the case of days gone by and you can forget about it?
You're wrong.
At the beginning of March, the authors of this worm released a new modification: W32.Downadup.C . In this modification, the authors have removed the spread code of the worm, completely removed. But he became much smarter to protect against detection and received new protected opportunities for the spread of new viruses in an infected botnet.
')
Surprisingly, the authors were not afraid and continue to prepare for the monetization of the botnet. Everyone thought that they would be scared by the 250 thousand dollars offered by Microsoft for capturing the authors, and they would hide. But no - they continue to work.
So, who is interested to learn more about the new modification of the worm - read my translation of yesterday's article from the blog Symantec W32.Downadup.C Bolsters P2P :
Somewhere between March 4 and March 6, 2009, the authors of the Downadup worm published a new major update to the part of the Downadup network. Symantec engineers caught this update in one of their Honeypot (computers without protection directly open on the Internet. Used by anti-virus companies to catch new or known viruses and their testing) and quickly made protection against a new threat. In general, the whole history of this threat is extremely interesting.
Initially, the main task of the worm was distribution, and it successfully spread to a fairly reliable and large botnet, supplemented by a complex code-signing mechanism to protect the update mechanism, as well as a reliable P2P (peer to peer) protocol.
Below is a table in which you can see general data on the evolution of this threat:

Hardly need to translate this table in full, so I will write only a couple of words:
you see that in version C, the virus no longer spreads. But he received an improved mechanism for delivering updates via HTTP and P2P, as well as increased protection against detection and treatment. The virus even looks for and kills some programs that keep your computer safe.
One interesting aspect of W32.Downadup.C is the removal of the propagation mode. This coincided with public reports of a decrease in activity in TCP port 445 also from March 5th, 2009. A decrease in activity on TCP port 445 is highly expected, since W32.Downadup.A and W32.Downadup.B both had aggressive propagation algorithms, but W32.Downadup.C they are not. Symantekovsky DeepSight Threat Management System observed this decrease in activity (as you can see in Figure 1 below).
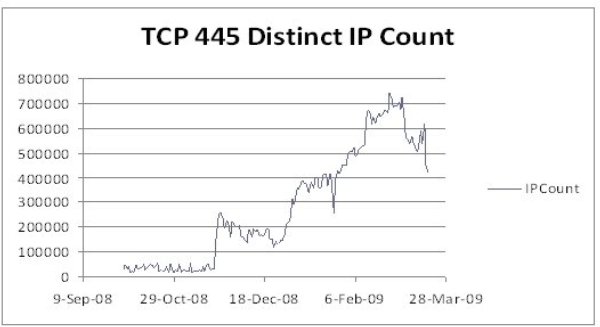
Chart 1. The decrease in the activity of TCP requests on port 445, possibly due to an update of the Downadup network with W32.Downadup.C.
The next important aspect of W32.Downadup.C is the addition to a reliable update mechanism via P2P. P2P functionality allows authors to send cryptographically signed updates to other computers infected with Downadup. This functionality contains a UDP P2P search engine that sends UDP traffic to the list of generated IP and ports. Chart 2 illustrates all UDP activity for ports greater than 1024, which was discovered through the Symantec DeepSight Threat Management System between February 18 and March 3, 2009.
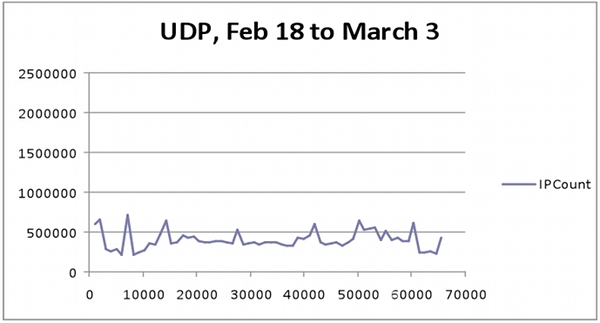
Graph 2. UDP activity for ports greater than 1024 between February 18 and March 3, 2009.
A sharp increase in this traffic was discovered on March 4th. This coincided with the W32.Downadup.C update, which was sent to computers infected with W32.Downadup.B. The strong increase in UDP activity indicates that a large number of systems infected with W32.Downadup.B have begun to perform UDP P2P searches on random IP addresses. This behavior is typical of the initial P2P setup of W32.Downadup.C.
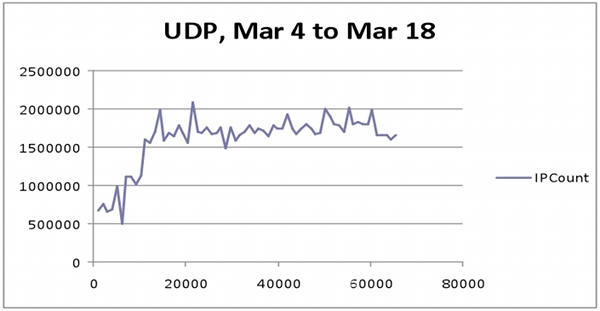
Graph 3. UDP activity for ports above 1024 between March 4 and March 18, 2009.
Pay attention to the number of IP (that is, the minimum number of infected computers) - more than 2 million (approx. Translator)
The main purpose of P2P functionality is to allow authors to send signed updates to computers infected with W32.Downadup.C. Essentially, this threat has evolved from an Internet worm (perhaps it was a test phase) into a full-featured backdoor / bot. The P2P network makes the downadup network a very difficult task because there is no centralized command center that can be closed.
In addition to P2P updates, the HTTP helper update method has also been improved. This method now generates a list of 50,000 domains every day and randomly selects 500 of them, which are checked daily for searching and downloading cryptographically signed updates.
Be that as it may, but so far there is no information or hint as to how this network will be used in the future.
Source: https://habr.com/ru/post/55123/
All Articles