"God, Sex, Love and Secret" or statistics on the use of passwords in social networks
Users do not like to strain and many developers have come to terms with this. Remember the last 10 sites on which you registered, how many of them checked your password for complexity? But no matter what security measures the system makers come up with, they may be meaningless if the user himself facilitates the work of the attacker.
This article shows the result of the analysis of ~ 100,000 passwords. I hope this analysis will be interesting and useful to many people.
No, we do not store passwords in open form, statistics obtained during the experiment on one of the social networks, by anonymous data collection and alas, I can not lay out the resulting dictionary and call this network.
All passwords are checked by the criteria for the availability of numbers, special characters, register, as well as stability using cracklib methods.
')
The shortest password is 1 character, the longest is 63 characters.

Over 15 characters are completely irrelevant.
According to the results of the cracklib run - 35.5% of passwords were easily cracked

Specialist. symbols - 3%
Only numbers - 33%
Only letters - 24.7%
Letter numbers - 39.3%

91.5% - in lower case
3% - in the upper case
5.5% - different case
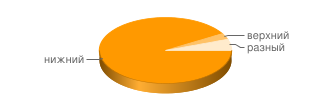
Suppose that an attacker has a base of 5 most common passwords and uses it to select all the accounts of your service. The top 5 passwords are 2.9% probability of successful selection in 5 attempts, and this is 290 people with a total number of users in 10,000 (such a small startups). Needless to say, these people will immediately lose both icq and mail ...
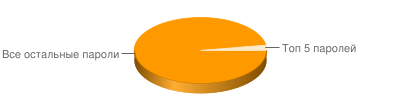
If we take into account all common passwords (occurring more than 5 times), of which there are only 381, then they allow access to ~ 9.2% of accounts. Just think, almost 10 of your users can be hacked by a tiny dictionary of less than 400 passwords.

The most delicious, alas, sonorous options as in the entire well-known film is not here, everything is trivial, and most people will not be surprised.
Users are idiots
Without password checking for complexity anywhere. The minimum set of rules determining the length of a password, the presence of letters and numbers in it at the same time, as well as a different register should be embedded in any registration form (or even better, generate a password for the user themselves). The form should have a threshold of attempts after which the user ceases to start up without entering a captcha (a very, very difficult captcha). My advice is to limit this number to three attempts. A good idea would be to add the counter of unsuccessful attempts to the user profile, in order to further introduce the delay between login attempts for each account separately. It’s really worth remembering that the user can start ddosit so that he cannot log in, but the unavailable state is much better than the leakage state of personal data.
I really hope that this information will help you to make your services better and safer.
This article shows the result of the analysis of ~ 100,000 passwords. I hope this analysis will be interesting and useful to many people.
Small retreat
No, we do not store passwords in open form, statistics obtained during the experiment on one of the social networks, by anonymous data collection and alas, I can not lay out the resulting dictionary and call this network.
What was done
All passwords are checked by the criteria for the availability of numbers, special characters, register, as well as stability using cracklib methods.
')
Data
Length distribution
The shortest password is 1 character, the longest is 63 characters.

Over 15 characters are completely irrelevant.
Difficult and simple passwords
According to the results of the cracklib run - 35.5% of passwords were easily cracked

The presence of specials. characters, numbers and letters
Specialist. symbols - 3%
Only numbers - 33%
Only letters - 24.7%
Letter numbers - 39.3%

Register
91.5% - in lower case
3% - in the upper case
5.5% - different case

Most Popular Passwords
What does this mean in reality?
Suppose that an attacker has a base of 5 most common passwords and uses it to select all the accounts of your service. The top 5 passwords are 2.9% probability of successful selection in 5 attempts, and this is 290 people with a total number of users in 10,000 (such a small startups). Needless to say, these people will immediately lose both icq and mail ...

If we take into account all common passwords (occurring more than 5 times), of which there are only 381, then they allow access to ~ 9.2% of accounts. Just think, almost 10 of your users can be hacked by a tiny dictionary of less than 400 passwords.

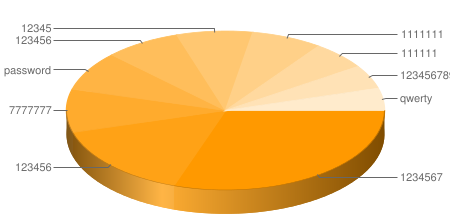
Top 10 Passwords
The most delicious, alas, sonorous options as in the entire well-known film is not here, everything is trivial, and most people will not be surprised.
- 1145 1234567
- 871 123456
- 332 7777777
- 303 password
- 292 12345
- 278 1111111
- 261 123456789
- 221 qwerty
- 216 111111
- 179 1234

findings
Without password checking for complexity anywhere. The minimum set of rules determining the length of a password, the presence of letters and numbers in it at the same time, as well as a different register should be embedded in any registration form (or even better, generate a password for the user themselves). The form should have a threshold of attempts after which the user ceases to start up without entering a captcha (a very, very difficult captcha). My advice is to limit this number to three attempts. A good idea would be to add the counter of unsuccessful attempts to the user profile, in order to further introduce the delay between login attempts for each account separately. It’s really worth remembering that the user can start ddosit so that he cannot log in, but the unavailable state is much better than the leakage state of personal data.
I really hope that this information will help you to make your services better and safer.
Source: https://habr.com/ru/post/46797/
All Articles