Office 365 Cloud Services: Check Point CloudGuard SaaS Testing

Hello, Habr! My name is Boris, and I am responsible for the information security of client and internal services at Linxdatacenter. Today we’ll talk about how to protect corporate mail in Office 365 from data leakage and loss. The IT engineer’s nightmare is a crowd of colleagues with panicked screams about unopened documents and missing mail. And when all the data is synchronized in a public cloud, a single act of an unwary user separates a nightmare from reality. There are several ways to insure against this disaster, but not everyone is equally good. For several weeks, we persistently searched for a solution for the peace of mind of the IT department and tested it. Today I want to talk about the test results and the product that we have chosen for use in the product.
What are the risks?
The human factor plays a key role in protecting information. In more than 90% of cases, the main cause of incidents is a person and his actions, which lead to a violation of information security. The most dangerous and most often used by staff applications are email and file sharing applications. For our company, such services are Office 365 E-mail and OneDrive. Both applications are available outside the office, without the use of a VPN connection and two-factor authentication.
To begin with, let us dwell on the most common types of attacks that occur when using these applications, and their consequences.
')
Typical Attacks in Office 365 Email
| Typical Attacks | Possible consequences |
| Using malware |
|
| Phishing |
|
| Unauthorized access |
|
Typical Attacks in Office 365 OneDrive
| Using malware |
|
| Unauthorized access |
|
Now that you’ve also thought about the risks associated with using seemingly innocent email applications, we’ll move on to protecting them.
What solutions were considered?
To protect Office 365 cloud services, we reviewed the following solutions: Microsoft ATP and Check Point CloudGuard SaaS. Why exactly these products? The fact is that CloudGuard SaaS for the period of testing, and now, is the only SaaS-solution of its kind that interacts with Office 365 services at the API level. Microsoft ATP, in turn, is an embedded product. The remaining vendors have solutions that are built into the work of the mail service by redirecting traffic to a physical or virtual server that processes the message and returns it to the end user. To do this, you need to configure Office 365 connectors and change MX records in DNS, which can lead to downtime of email services. The work of the mail service is critical for us, so we did not consider such solutions.
Before active testing, reports and reviews on the listed products on various specialized resources were studied, a survey of colleagues was conducted.
Microsoft ATP
Microsoft Office 365 Advanced Threat Protection offers three paid subscription levels (E1, E3, and E5) for companies with 300 or more users. Each level includes scanning attachments and the sandbox (Safe Attachments), filtering the reputation of URLs (safe links), basic protection against spoofing, as well as antiphishing.
Sounds great ... However, MS Office 365 ATP has a number of significant vulnerabilities. First, the service allows hackers to search for MX records to determine if users are using Office 365. After that, attackers target an attack by using fake Office 365 login or file sharing via OneDrive. In addition, any hacker can activate a mailbox with Microsoft ATP protection, and then constantly check his attacks on the system using the trial and error method until he finds a strategy that works. Attackers for as little as $ 10 can open hundreds of accounts to test their methods and still make a solid profit if their attacks are successful in the long run. Not so long ago, researchers discovered a 0-day vulnerability called BaseStriker. Although, to be honest, publications on circumvention of Microsoft protection appear regularly.
Avanan reported that BaseStriker is used by hackers to conduct more effective phishing attacks. This method allows you to send a large number of web links through MSFT servers without scanning. This link may point the user to a phishing site or to a file that downloads malware. BaseStriker can infiltrate Office 365, essentially obfuscating ATP by splitting and hiding a malicious link using a URL tag. A malicious link is included in the email, but instead of being part of the original link, it is shared. This is shown in detail in the Avanan example.
Using your own program shell in the user’s environment (inside the browser), which, as it turned out, doesn’t react at all to malware and scripts, allows the execution of malicious code on a phishing site. In Prevent mode, emulation takes about 30 minutes or more. Colleagues who tested this solution also do not yet recommend using it in practice.
A vivid demonstration of ATP (Proof-of-concept) and its shortcomings is also available on the TrustedSec website ( link ).
Check Point Cloud Guard SaaS
Let's move on to the solution from Check Point. In our test, we used the CloudGuard SaaS solution.
CloudGuard SaaS connects to Office 365 through an administrator account and granting access rights to mail and files.
Scan Levels:
- Incoming and outgoing letters, attachments, links in letters.
- Files on file storage.
The solution consists of several modules operating at different levels:
- Attachments and files are scanned by the Anti-Virus module , using Check Point SandBlast technology.
- The Anti-Phishing module works on previously unknown and potentially dangerous senders. Check Point claims to use more than 300 parameters to determine phishing.
- The DLP module responds to documents, letters, and attachments that contain potentially important financial or organizational information. A quite useful function, especially against possible sabotage or employee mistakes, as well as for controlling information flows.
- The Shadow IT module allows you to identify the use of third-party services in addition to Office 365. Shadow IT refers to IT devices, software, and services that are present in the organization but not served by the IT department. They are not on the balance sheet of the IT department, their status and work are not controlled, moreover, the IT department may not know anything about them. These include Amazon AWS, GPC, amoCRM, and other services.
- Anomaly Detection allows you to identify anomalies when users log on to Office 365.
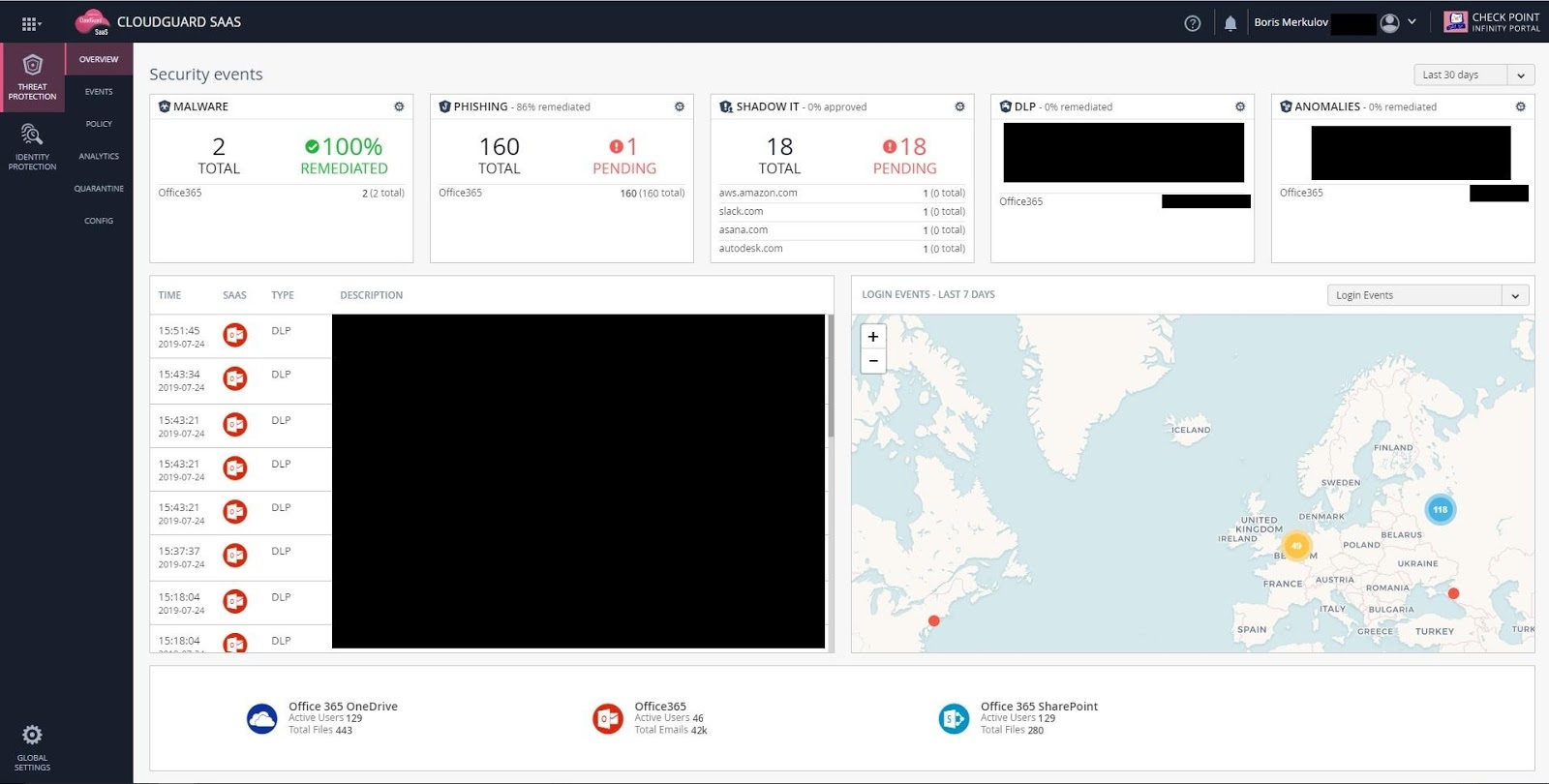 In the Cloud Guard SaaS dashboard, statistics for each module are displayed.
In the Cloud Guard SaaS dashboard, statistics for each module are displayed.All modules are trained and allow the administrator to indicate false positives.
For testing, CloudGuard SaaS was connected to Office 365 Email and Office 365 OneDrive in monitoring mode.
Let's move on to practice
Let's analyze the data of the service over the past couple of months from the date of implementation.

CloudGuard scans email attachments to prevent threats and runs them through the sandbox.
The screenshot above shows the following information:
- the number of external users (we mean addresses not with our domain);
- the number of protected internal users (those that are in the system);
- number of incoming emails with attachments;
- number of outgoing emails with attachments.
Office 365 Scan Report
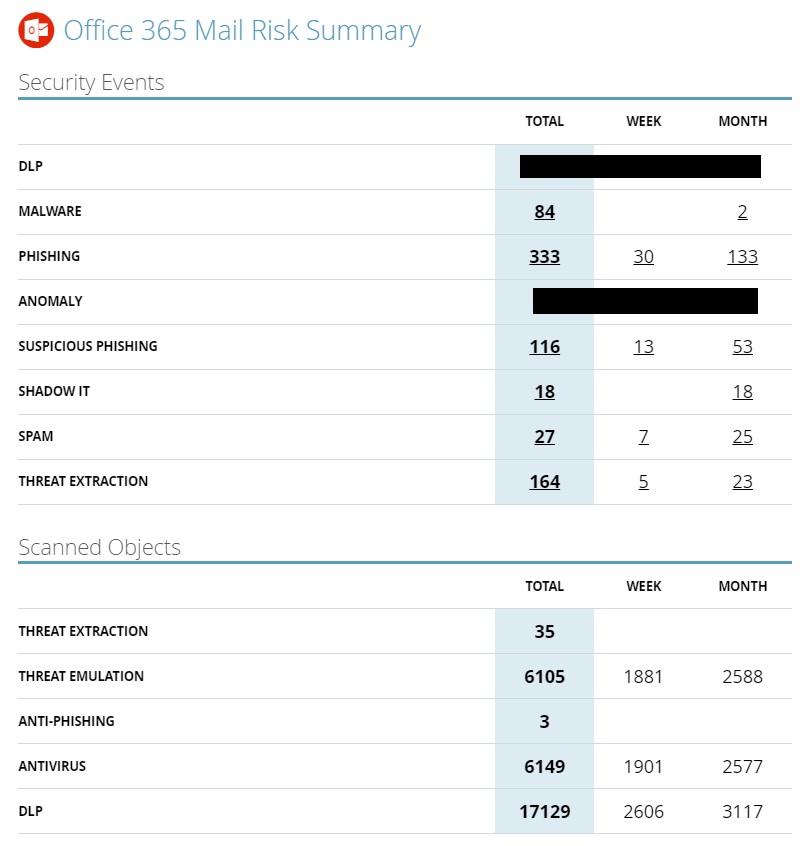
Summary of identified threats and scanned objects.
The screenshot above provides information about the prevented threats (Security Events) and scanned objects (Scanned objects):
- leakage of confidential information (Data Leak Prevention);
- malware entry attempts (malware);
- phishing
- abnormal activity - it is different;
- suspicion of phishing;
- shadow IT;
- SPAM
- threat extraction (converting files to a safe form).
OneDrive Scan Report
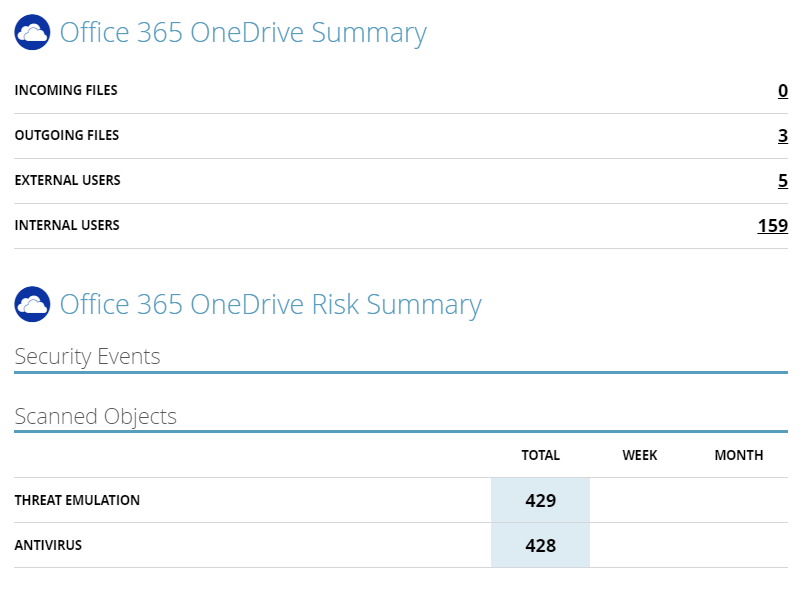
In fact, the report is a much larger amount of information. For example, in the DLP module, you can see what mask is triggered, find a letter that caused a potential information leak. Alas, I can’t share such a screen.
Examples of displaying malicious emails on the CloudGuard portal
- Email with detected malicious attachment:
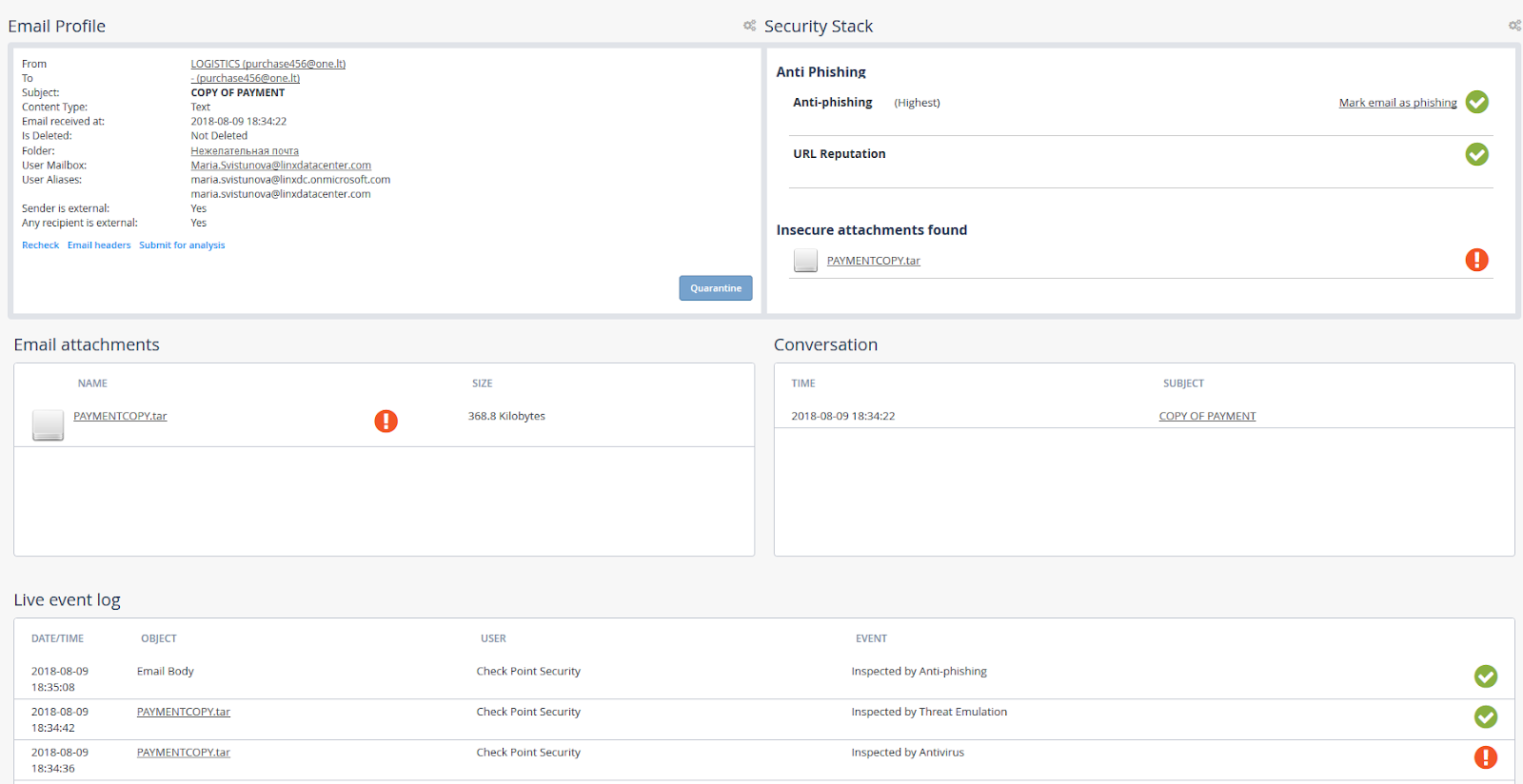
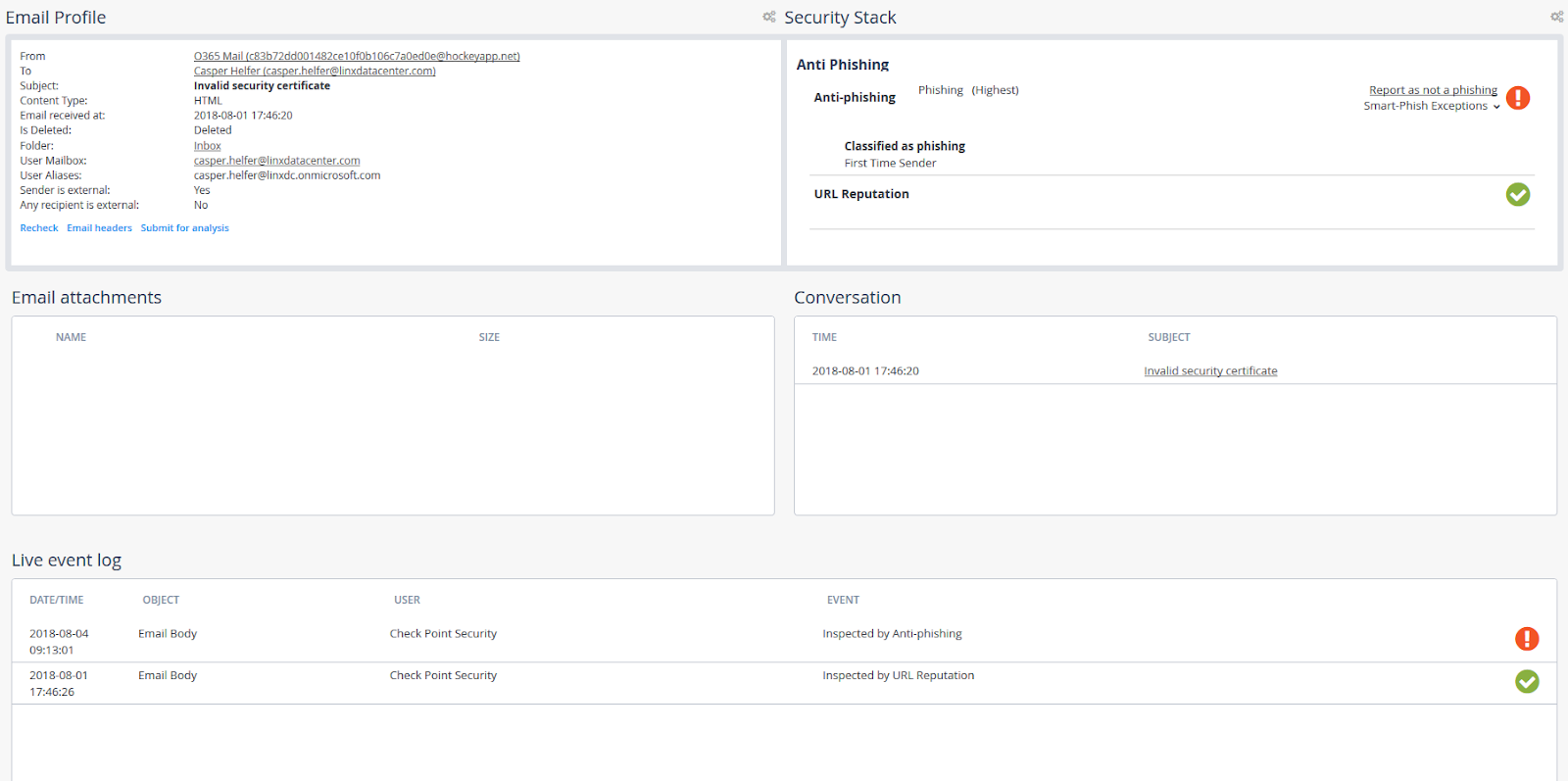
- Phishing email missed by Microsoft built-in filters:
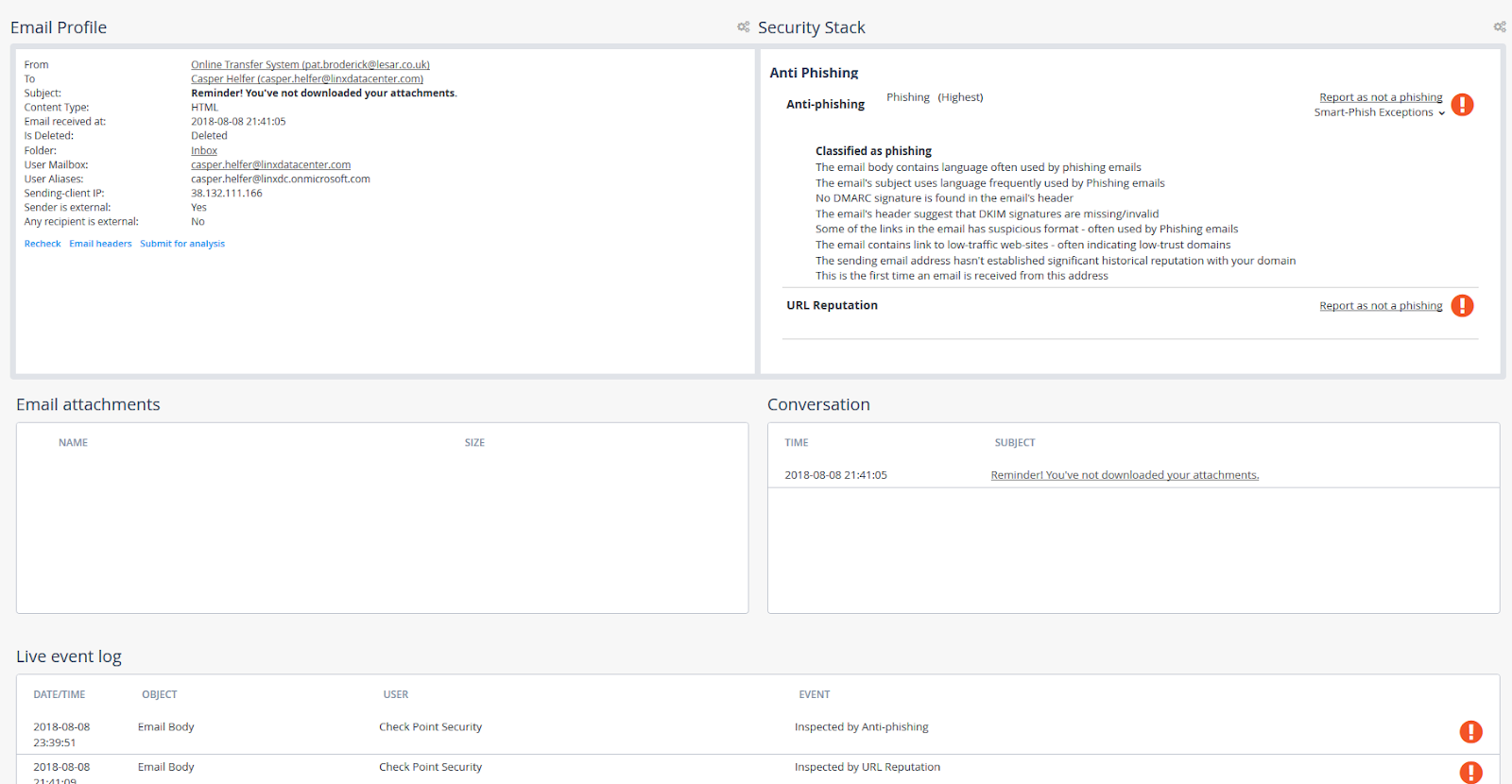
- The URL reputation (one of the parameters for evaluating phishing emails) is fine, but the link in the email is phishing:
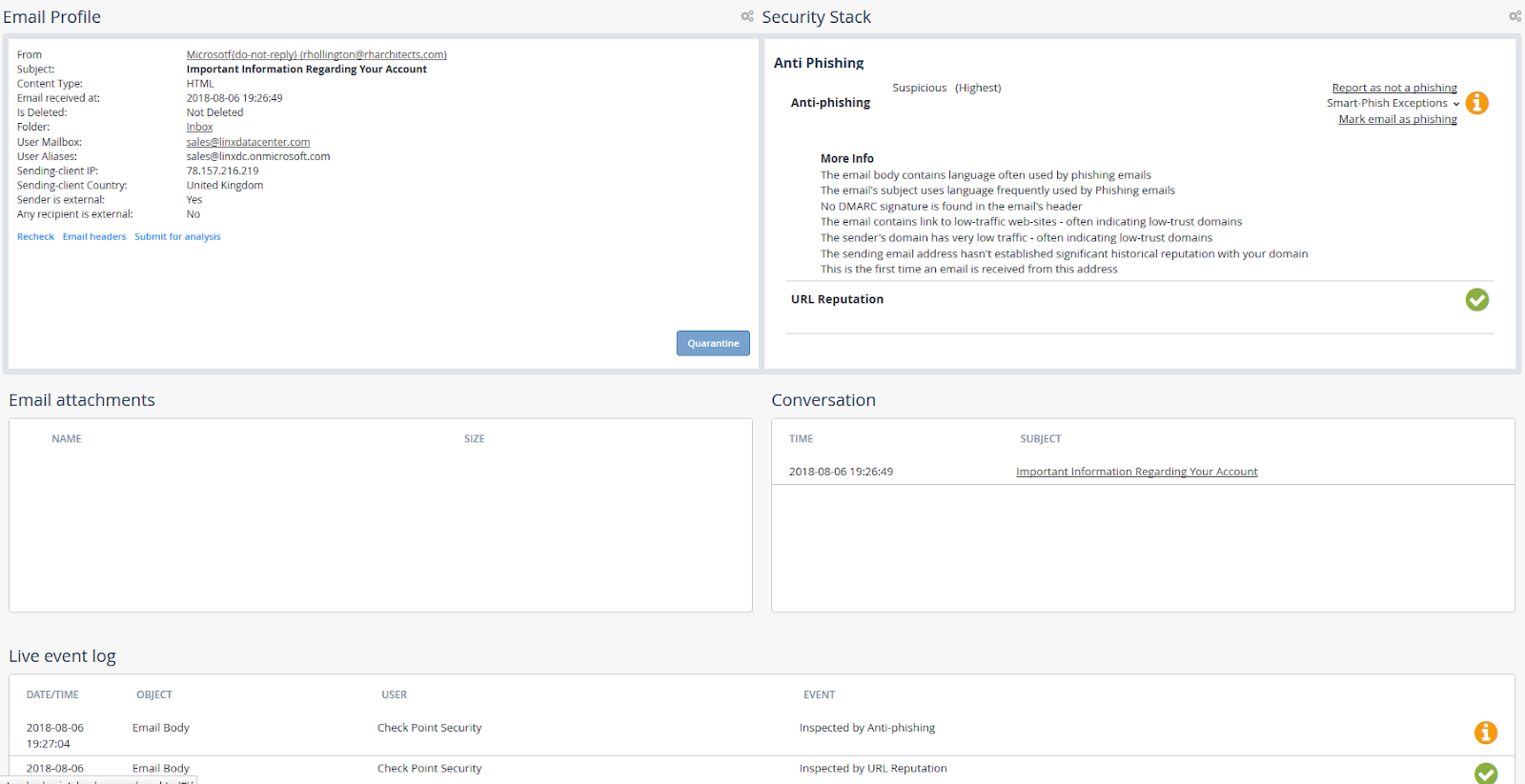
- An example of a message suspected of phishing, also not seen by Microsoft filters:
And ... conclusions
Now let's talk about the pros and cons of CloudGuard SaaS.
Pros:
- Nice and fairly simple interface.
Fast, very fast integration in Office 365: requires administrator account and 5-10 minutes.- Consultations and direct support of the vendor.
- The possibility of free testing for 30 days.
- The ability to use native Office 365 groups to create a list of protected addresses, flexible license management.
- Each user connected to Check Point CloudGuard SaaS can be protected by any module for a fixed price and on any available CloudGuard SaaS service (Office 365 mail, OneDrive, SharePoint, Google Drive, Dropbox, etc.).
- Detailed reports for each event;
- Not so long ago there was an antispam!
In addition, in future editions, the vendor promises the implementation of several important improvements:
- Identity Protection module for Azure AD, which will allow you to bind two-factor authentication to each of the available services;
- protection against SMS phishing.
Minuses:
- Check Point gets full access to our services. Relations are built on mutual trust.
- Not the fastest technical support response to emerging issues.
- Lack of whitelisting for external mailing addresses.
- The inability to upload reports from the analytics section is sorely lacking.
- The absence of the read-only role of the portal user (only admin is available).
In general, we are satisfied with the test results and opted for the product of Check Point. CloudGuard SaaS is currently connected to Office 365 Email and Office 365 OneDrive in Prevent mode.
I would like to note that Linxdatacenter engineers also considered Cisco Email Security and Fortimail as another option for protecting the mail server from phishing attacks and spam, but the implementation of CES requires changing the MX domain record, connecting the connectors in Exchange and can potentially lead to a small downtime. which, unfortunately, is critical. Perhaps in the near future we will return to testing the updated CES and Fortimail solutions.
Source: https://habr.com/ru/post/461861/
All Articles