StealthWatch: Deployment and Customization. Part 2

Hello colleagues! Having determined the minimum requirements for the deployment of StealthWatch in the last part , we can begin the deployment of the product.
1. Ways to deploy StealthWatch
There are several ways to “touch” StealthWatch:
')
- dcloud - a cloud lab service;
- Cloud Based: Stealthwatch Cloud Free Trial - here Netflow from your device will sprinkle into the cloud and the StealthWatch software will be analyzed there;
- On-premise POV ( GVE request ) - the way I went, they will drop 4 OVF files of virtual machines with built-in licenses for 90 days, which can be deployed on a dedicated server on the corporate network.
Despite the abundance of downloaded virtual machines, for a minimal working configuration, only 2 are enough: StealthWatch Management Console and FlowCollector. However, if there is no network device that can export Netflow to a FlowCollector, then you must also deploy FlowSensor, since the latter allows you to collect Netflow using SPAN / RSPAN technologies.
As I said earlier, your real network can act as a laboratory stand, since StealthWatch needs only a copy, or, more correctly, squeezing a copy of traffic. The figure below shows my network, where on the Security Gateway I will configure Netflow Exporter and, as a result, I will send Netflow to the collector.

To access future VMs, on your firewall, if any, the following ports should be enabled:
TCP 22 l TCP 25 l TCP 389 l TCP 443 l TCP 2393 l TCP 5222 l UDP 53 l UDP 123 l UDP 161 l UDP 162 l UDP 389 l UDP 514 l UDP 2055 l UDP 6343
Some of them are well-known services, some are reserved for Cisco services.
In my case, I just deployed StelathWatch on the same network as Check Point, and I did not have to configure any permission rules.
2. Installing FlowCollector using VMware vSphere as an example
2.1. Click Browse and select OVF file1. After checking the availability of resources, go to the View menu, Inventory → Networking (Ctrl + Shift + N).

2.2. In the Networking tab, select New Distributed port group in the virtual switch settings.

2.3. We set the name, let it be StealthWatchPortGroup, the rest of the settings can be made as in the screenshot and click Next.
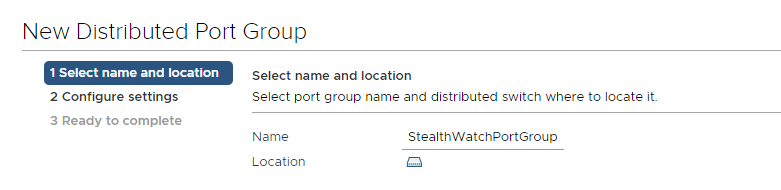

2.4. We complete the creation of the Port Group with the Finish button.
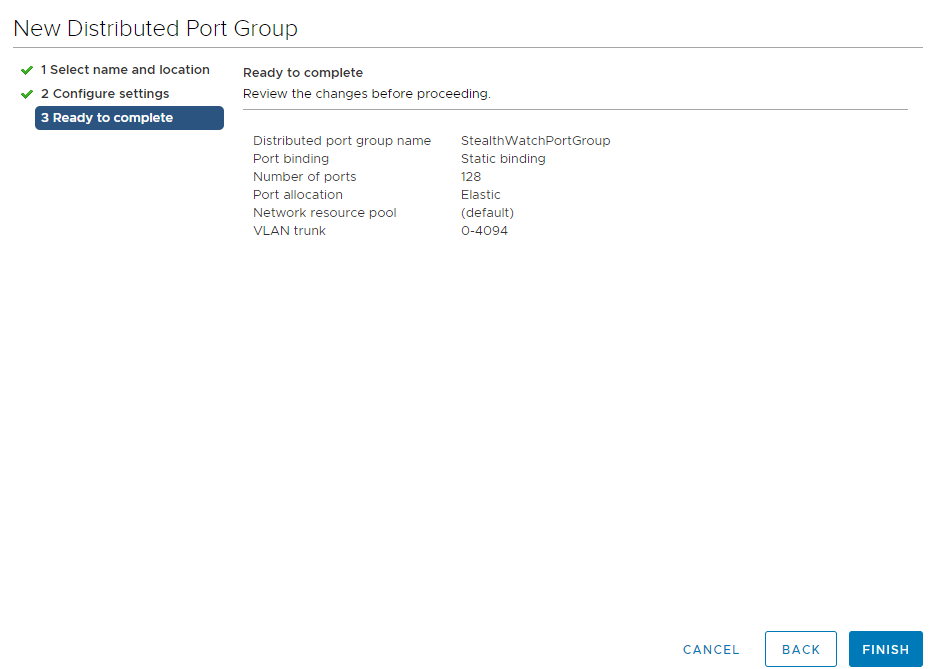
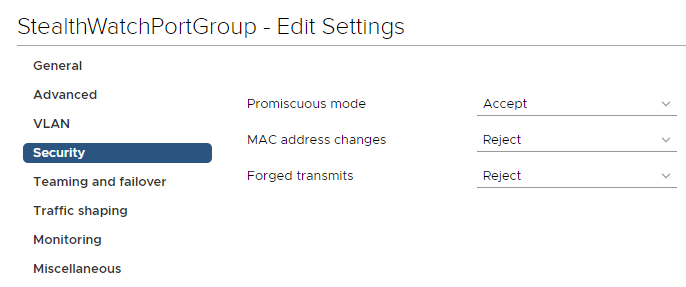
2.5. In the created Port Group, edit the settings by right-clicking on the port group, select Edit Settings. In the Security tab, be sure to turn on “inaudible mode”, Promiscuous Mode → Accept → OK.
2.6. As an example, we import the OVF FlowCollector, the download link of which was sent by a Cisco engineer after a GVE request. Right-clicking on the host on which you plan to deploy VM, select Deploy OVF Template. Regarding the allocated space, it will “start up” at 50 GB, but for combat conditions it is recommended to allocate 200 gigabytes.

2.7. Select the folder where the OVF file is located.
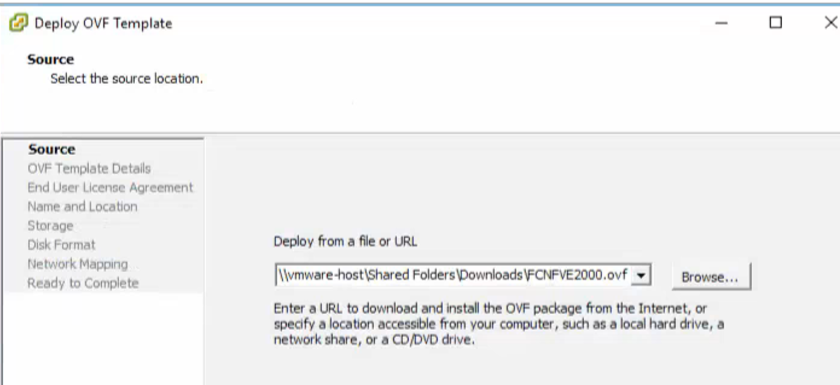
2.8. Click "Next."
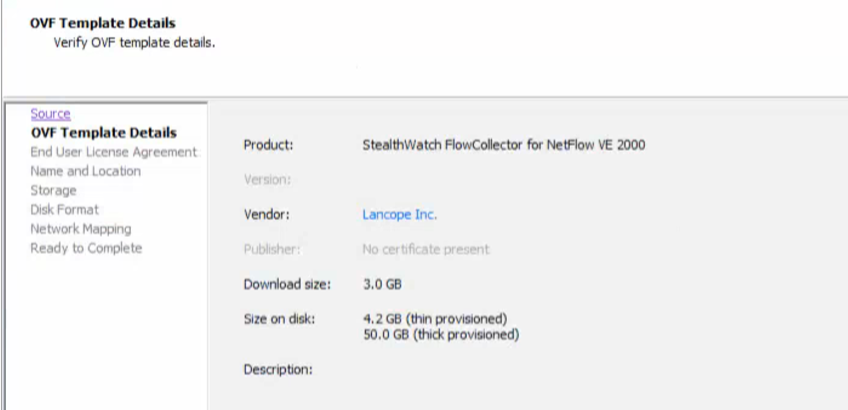
2.9. We indicate the name and server where we deploy it.

2.10. As a result, we get the following picture and click "Finish".
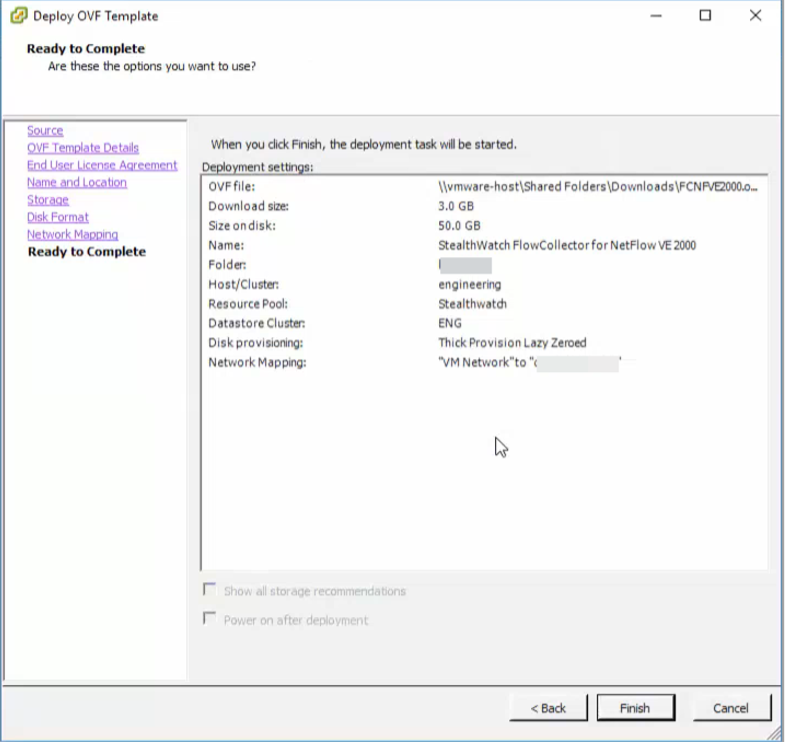
2.11. We follow the same steps to deploy the StealthWatch Management Console.

2.12. Now you need to specify the necessary networks in the interfaces so that FlowCollector sees both the SMC and the devices from which Netflow will be exported.
3. Initializing the StealthWatch Management Console
3.1. Going to the console of the installed SMCVE machine, you will see a place to enter your login and password, by default sysadmin / lan1cope .

3.2. We go to the Management point, set the IP address and other network parameters, then confirm their change. The device will reboot.



3.3. Go to the web interface (via https to the address that you specified SMC) and initialize the console, the default username / password is admin / lan411cope .
PS: it happens that Google Chrome does not open, Explorer will always help out.
3.4. Be sure to change passwords, set DNS, NTP servers, domain and more. The settings are intuitive.
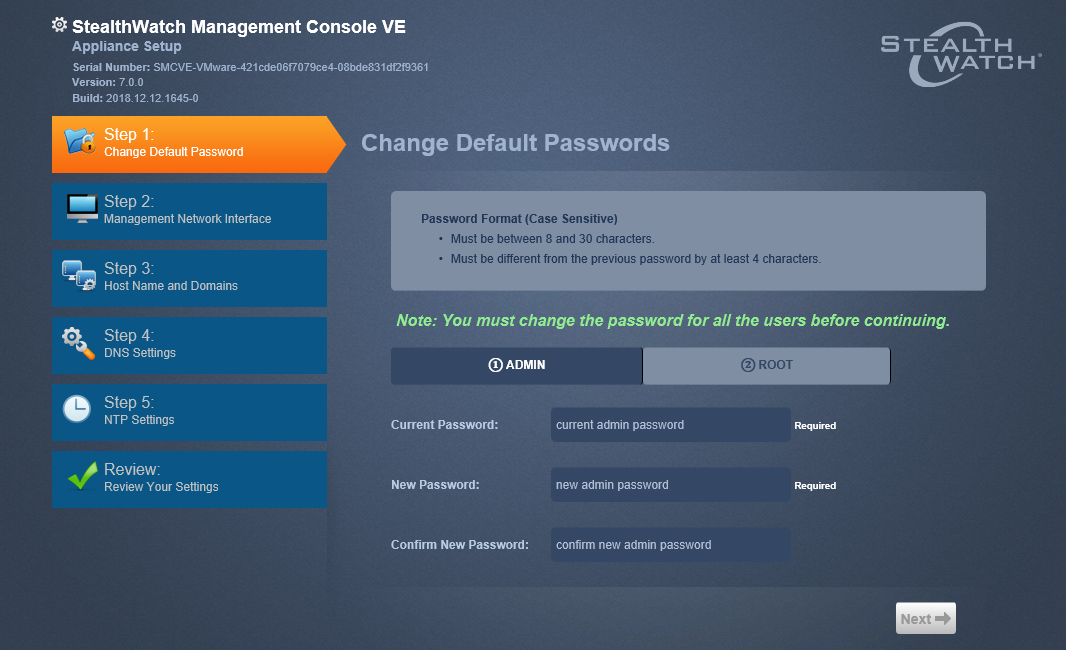
3.5. After clicking the “Apply” button, the device will reboot again. After 5-7 minutes, you can connect again to this address; StealthWatch will be managed through a web interface.
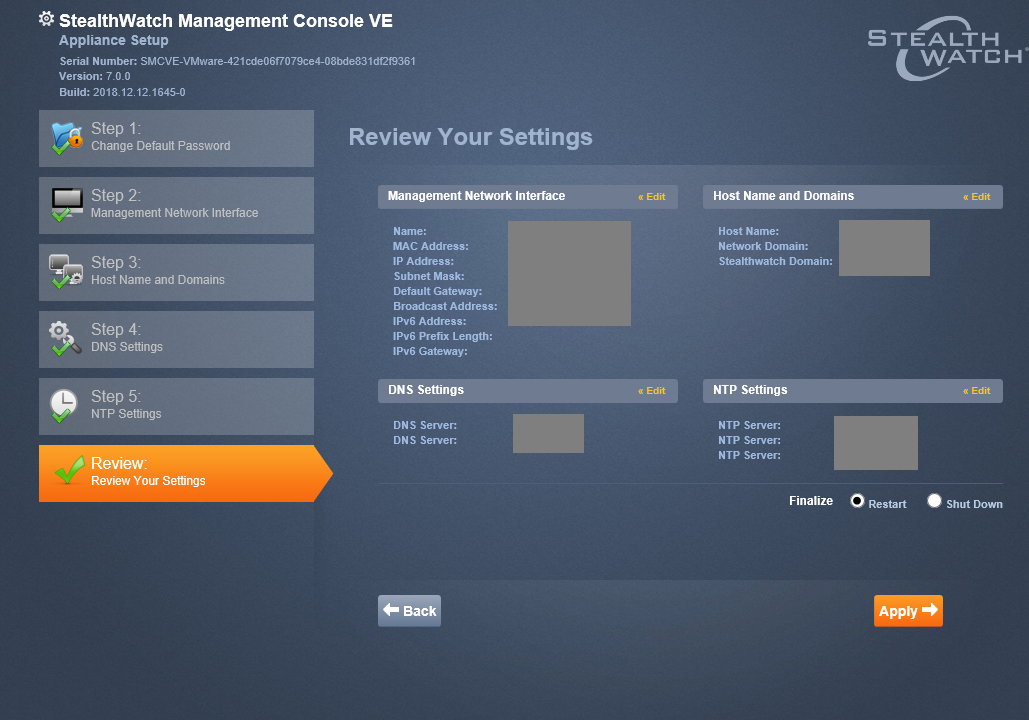
4. Setting FlowCollector
4.1. With the collector all the same. First, specify the IP address, mask, domain in the CLI, then FC is rebooted. After that, you can connect to the web interface at the specified address and perform the same basic setup. Due to the fact that the settings are similar, detailed screenshots are omitted. Login credentials are the same .

4.2. On the penultimate item, you must specify the IP address of the SMC, in this case the console will see the device, you will have to enter this credential to confirm this setting.

4.3. We select the domain for StealthWatch, it was set earlier, and port 2055 is normal Netflow, if you work with sFlow, port 6343 .
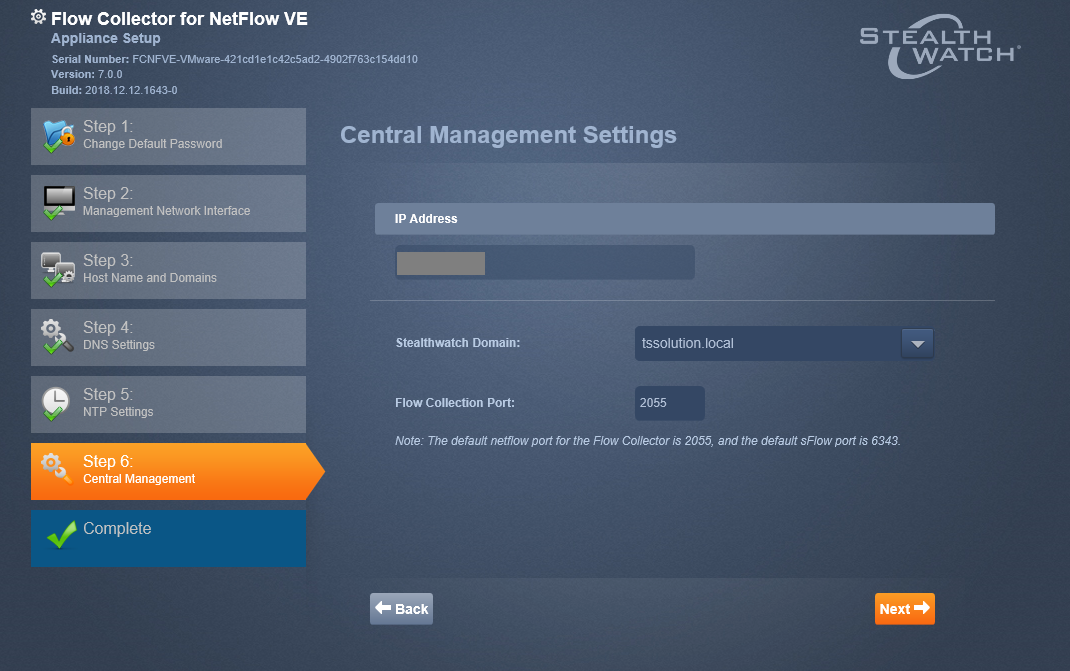
5. Netflow Exporter Configuration
5.1. To configure the Netflow exporter, I strongly recommend that you turn to this resource , here are the main guides for configuring the Netflow exporter for many devices: Cisco, Check Point, Fortinet.
5.2. In our case, I repeat, we export Netflow from the Check Point gateway. Netflow exporter is configured in a tab with a similar name in the web interface (Gaia Portal). To do this, click “Add”, specify the version of Netflow and the required port.

6. Analysis of the work of StealthWatch
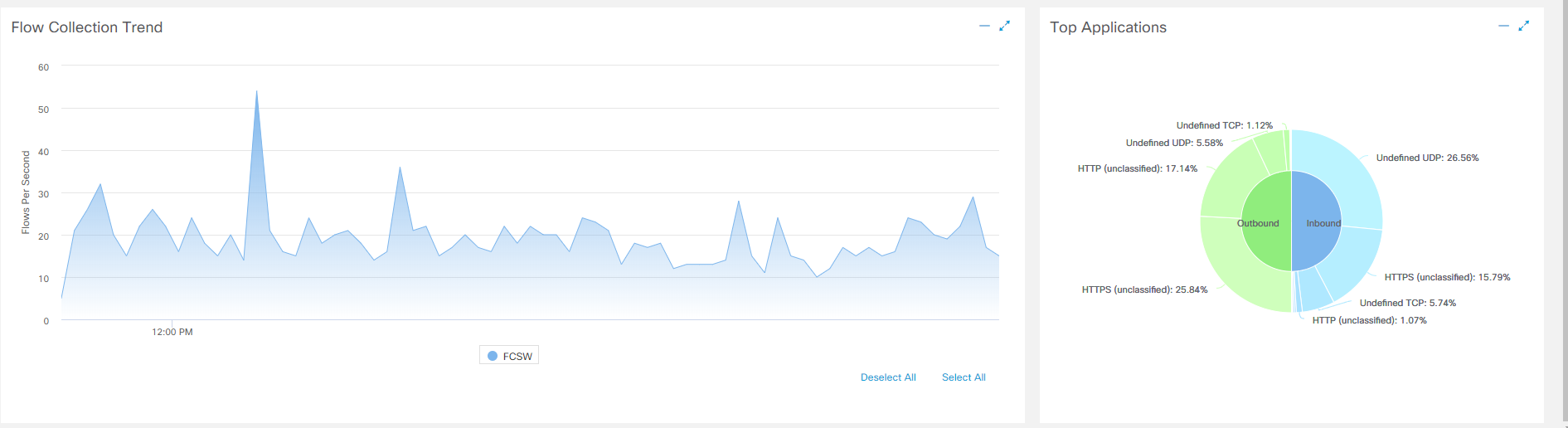
6.1. Going to the SMC web interface, on the very first page of Dashboards> Network Security you can see that the traffic has gone!
6.2. Some settings, for example, splitting hosts into groups, monitoring individual interfaces, their load, managing collectors, and more can only be found in the StealthWatch Java application. Of course, Cisco is slowly transferring all the functionality to the browser version and soon we will refuse such a desktop client.
To install the application, you must first install the JRE (I installed version 8, although it is said that it is supported up to 10) from the official Oracle site.
In the upper right corner of the web interface of the management console, to download, click the "Desktop Client" button.
You save and install the client forcibly, java will most likely swear at it, you may need to add the host to java exceptions.
As a result, a fairly understandable client opens in which it is easy to see the loading of exporters, interfaces, attacks and their flows.



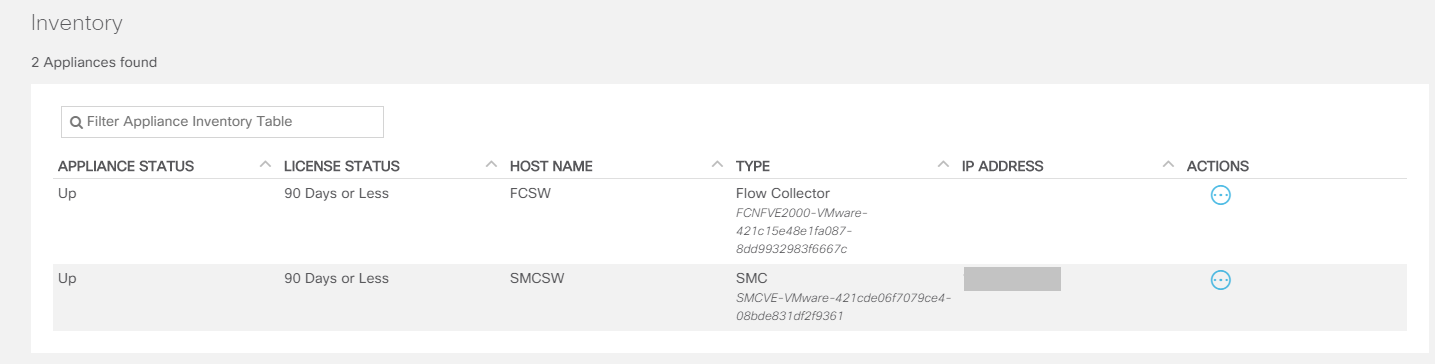
7. StealthWatch Central Management
7.1. The Central Management tab contains all the devices that are part of the deployed StealthWatch, such as: FlowCollector, FlowSensor, UDP-Director and Endpoint Concetrator. There you can manage network settings and device services, licenses and manually turn off the device.
You can go to it by clicking on the "gear" in the upper right corner and selecting Central Management.

7.2. By going to the Edit Appliance Configuration at FlowCollector, you will see the SSH, NTP, and other network settings directly related to the appendix. To proceed, select Actions → Edit Appliance Configuration from the required device.


7.3. License management can also be found under the Central Management> Manage Licences tab. Trial licenses in case of a GVE request are given for 90 days .

The product is ready to go! In the next part, we will look at how StealthWatch can detect attacks and generate reports.
Source: https://habr.com/ru/post/461831/
All Articles