Using jailbreak to extract data: risks and consequences
In my new blog on Habré, I want to share unique information on how exactly we extract data from smartphones. On our own site, we posted a number of articles on this topic, telling, it would seem, everything possible about how to extract data from Apple smartphones and tablets. Logical analysis, cloud extraction and low-level physical extraction analysis have both strengths and weaknesses; I will try to talk about them in the following publications.
I guess I will never tire of talking about the benefits of physical analysis. Here is access to all the contents of the file system, and decryption of all entries from the Keychain (and these are passwords, including, by the way, passwords for cryptocurrency wallets and "secret" chats). Here, extracting data from all applications (and not just those whose developers allowed backup) and access to downloaded e-mail messages, chat rooms and correspondence in a wide variety of applications, including well-protected ones (by hand, we use Telegram and Signal users).
How to get to the most interesting? Of course, we need low-level data access, which is impossible without gaining superuser rights. How to get superuser rights? If you are not a police or special services employee from the USA, Israel or the EU, then there is only one option: installing a jailbreak. Today I will talk about the risks and consequences of physical analysis of devices associated with the use of jailbreak to extract data.
Probably everyone knows what a jailbreak is for iOS and how it differs from root for Android (hint: for almost everyone). Jailbreak is the collective name of the application class for the iOS operating system, which allows escalating privileges to obtain superuser rights on the device. Escalation of privileges is carried out using errors in the iOS security system. Given the fact that Apple developers quickly fix bugs with the release of iOS updates, the release of new and new jailbreak tools is a continuous process.
')
Jailbreaks are used both by independent researchers to analyze iOS security systems, and by enthusiastic users who get the opportunity to modify the appearance and behavior of the system, as well as install applications from third-party sources in addition to the official Apple App Store. For us, these opportunities are superfluous; all we need is access to the device via SSH, and, of course, full access to the file system.
Thus, in our laboratory (as well as in the laboratories of forensic experts), jailbreaks are used to gain unlimited access to the file system, extract data from iPhone and iPad and decrypt Keychains (user passwords stored in Safari, system and third-party applications) .
Using the jailbreak has the following benefits:
File System Image:
Bunch of keys:
Using a jailbreak brings not only benefits, but also carries a number of risks.
Installing and using a jailbreak involves some risks. The risk of installing a jailbreak is often misunderstood. Most often, they are afraid of “scorching” the device - a situation as a result of which a hacked iPhone or iPad stops loading. The idea of such a danger of jailbreaking has been going on since iOS 8 and 9, for which jailbreaks patched the kernel and tried (sometimes - successfully, but more often - not very) to disable Kernel Patch Protection, KPP protection. The triggering of KPP led to a spontaneous reboot of the device or its bricking.
Modern jailbreaks (starting with jailbreaks for iOS 10) have practically no such risk: jailbreaks do not modify the system core and do not affect the boot process (and, of course, do not touch KPP). Moreover, even devices with jailbreak installed boot in normal mode; To obtain superuser rights, the jailbreak will need to be run again, after loading.
To an absolute minimum, this risk is reduced in jailbreaks of the Rootless category. These jailbreaks not only do not modify the system, but do not even remount the system partition. Accordingly, such jailbreaks are not able to influence the boot process of the system in any way.
What are the risks of installing a jailbreak? We list.
1. The device’s Internet connection. During the installation of the jailbreak, you will have to obtain a digital signature for the IPA package, which contains the jailbreak. Unsigned IPAs cannot be transferred to the device, much less can not be launched on it. Digital signature issued by Apple servers; they must be contacted for its receipt. The process is automated: it uses a ready-made and very easy to use open source Cydia Impactor application. However, if you allow the device access to the Internet, you risk: an attacker can remotely send a command to the device to block it or destroy data.
Solution: You can work around this problem by using the Apple Developer Program certificate. See the Walkthrough for details.
2. Jailbreak just does not install. Yes, the second most serious risk is that the jailbreak simply won’t get on the iPhone. Jailbreaks do not use one, but a whole chain of vulnerabilities; finding and using such a chain correctly is hard work. Alas, the error at any stage leads to the fact that the jailbreak will not be established, and you will find yourself in the best case with a device without a jailbreak, and in the worst case with a device with a remounted system partition, but without a jailbreak (about what is bad - below )
Solution: generally speaking, there are many jailbreaks. For iOS 12, for example, we counted at least 4 workable jailbreaks (in fact, there are more). One jailbreak didn’t work? Just try another; about them again in the Walkthrough .
We figured out the risks, the jailbreak is installed. How could this threaten?
Before talking about the risks of jailbreak, we will understand their types. There are only two of them: ordinary (classic) jailbreaks, and rootless jailbreak.
The classic jailbreak provides the user with, so to speak, “full stuffing”: the digital signature verification is disabled (you can install and run any applications), a third-party application store is installed (most often this is Cydia, but alternative options also began to appear). For this, quite a lot of files are written to the system partition, and the system partition itself is remounted in r / w mode.
What does this mean in practice? Junk in the system partition, which sometimes cannot be completely removed during the process of jailbreak removal (especially if the user managed to try installing different jailbreaks). Potential (and often real) device instability. Finally, the inability to correctly install OTA updates. Only full firmware recovery through iTunes helps, and sometimes the instability of the device persists, and you have to reset to factory settings. Not too nice.
All these things do not happen if you use the new rootless type of jailbreak, the only representative of which is RootlessJB. This jailbreak did not win the popularity of its classic counterparts for an obvious reason: it does not install (and does not support work) third-party stores (Cyida and the like). An ordinary user-enthusiast at this moment, the interest disappears, and he sets up a classic jailbreak.
Meanwhile, for our purposes, RootlessJB is of particular value. The fact is that we should return the iPhone under study in approximately the form in which it was received for analysis. That is, at least the device should not work less stable than before the analysis, and there should be no problems installing OTA updates. These are exactly what RootlessJB gives us. Judge for yourself: this jailbreak does not modify the system partition without writing a single extra file to it. Moreover, he cannot do this: the principle of operation of this jailbreak does not imply remounting the system partition in r / w mode.
Further more. Since the RootlessJB jailbreak does not need to be supported by a third-party application store, there is no need to disable digital signature verification (you can run individual binaries, but the paths to them must be manually entered into the permission control file). No need to disable digital signature verification - no need to write anything to the system partition. The system partition does not need to be opened for recording - you can skip the operation of the corresponding vulnerability, which simplifies the installation process and makes it more reliable. In other words, for us, RootlessJB is literally a gift.
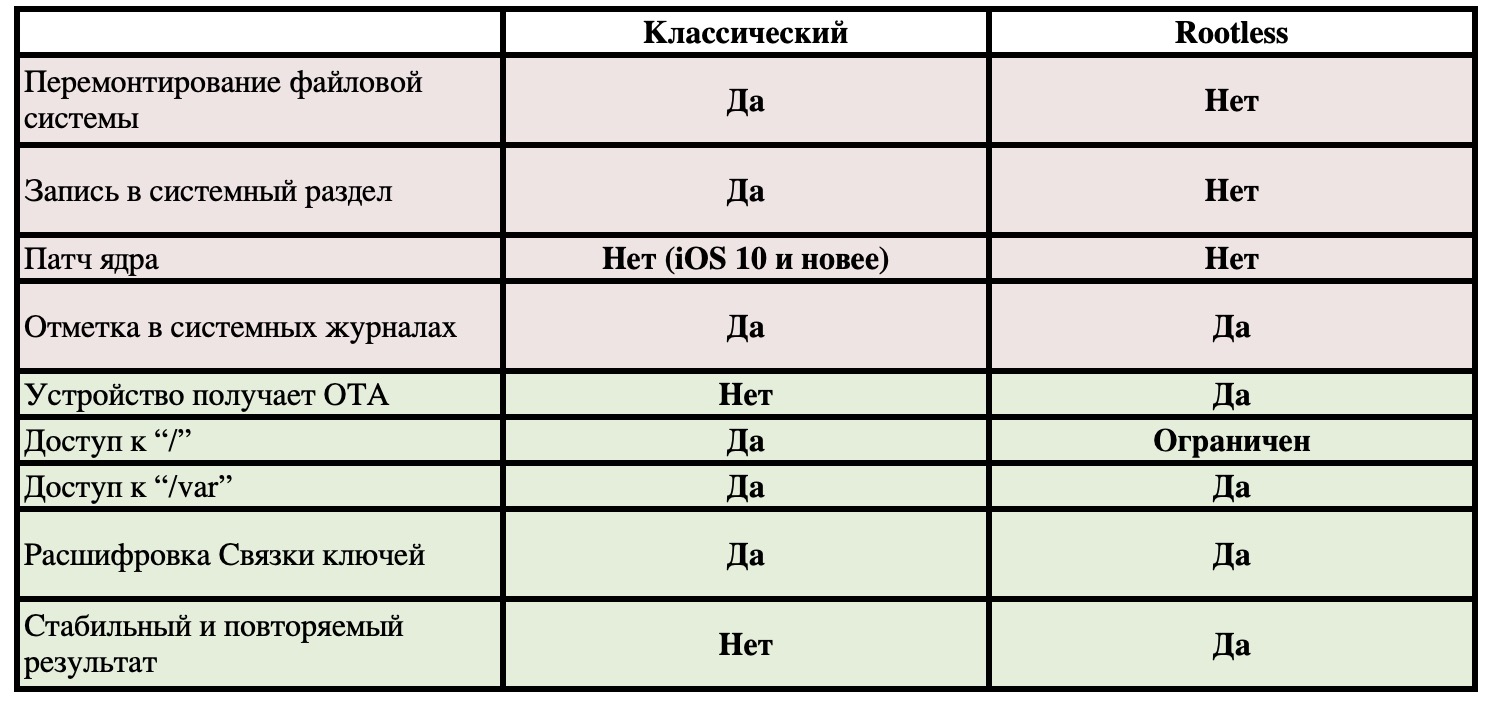
We finish the article with a table in which we compare the consequences of using different types of jailbreaks.
This article is the first one planned. I plan to talk about how exactly in the laboratories of the police and special services both in our country and abroad get access to information in Apple devices. Stay with us, it will be interesting!
I guess I will never tire of talking about the benefits of physical analysis. Here is access to all the contents of the file system, and decryption of all entries from the Keychain (and these are passwords, including, by the way, passwords for cryptocurrency wallets and "secret" chats). Here, extracting data from all applications (and not just those whose developers allowed backup) and access to downloaded e-mail messages, chat rooms and correspondence in a wide variety of applications, including well-protected ones (by hand, we use Telegram and Signal users).
How to get to the most interesting? Of course, we need low-level data access, which is impossible without gaining superuser rights. How to get superuser rights? If you are not a police or special services employee from the USA, Israel or the EU, then there is only one option: installing a jailbreak. Today I will talk about the risks and consequences of physical analysis of devices associated with the use of jailbreak to extract data.
What is jailbreak for?
Probably everyone knows what a jailbreak is for iOS and how it differs from root for Android (hint: for almost everyone). Jailbreak is the collective name of the application class for the iOS operating system, which allows escalating privileges to obtain superuser rights on the device. Escalation of privileges is carried out using errors in the iOS security system. Given the fact that Apple developers quickly fix bugs with the release of iOS updates, the release of new and new jailbreak tools is a continuous process.
')
Jailbreaks are used both by independent researchers to analyze iOS security systems, and by enthusiastic users who get the opportunity to modify the appearance and behavior of the system, as well as install applications from third-party sources in addition to the official Apple App Store. For us, these opportunities are superfluous; all we need is access to the device via SSH, and, of course, full access to the file system.
Thus, in our laboratory (as well as in the laboratories of forensic experts), jailbreaks are used to gain unlimited access to the file system, extract data from iPhone and iPad and decrypt Keychains (user passwords stored in Safari, system and third-party applications) .
Using the jailbreak has the following benefits:
File System Image:
- Working application databases, WAL files, access to recently deleted records
- Data for all applications, including those for which backups are prohibited
- Access your chat history in apps like Signal and Telegram
- Downloaded Email and Exchange
- System Logs
Bunch of keys:
- In addition to user passwords, which can also be extracted from the backup with a password, the records protected by the this_device_only attribute are also decrypted
- Including iTunes backup password retrieval
Using a jailbreak brings not only benefits, but also carries a number of risks.
Jailbreak Risks
Installing and using a jailbreak involves some risks. The risk of installing a jailbreak is often misunderstood. Most often, they are afraid of “scorching” the device - a situation as a result of which a hacked iPhone or iPad stops loading. The idea of such a danger of jailbreaking has been going on since iOS 8 and 9, for which jailbreaks patched the kernel and tried (sometimes - successfully, but more often - not very) to disable Kernel Patch Protection, KPP protection. The triggering of KPP led to a spontaneous reboot of the device or its bricking.
Modern jailbreaks (starting with jailbreaks for iOS 10) have practically no such risk: jailbreaks do not modify the system core and do not affect the boot process (and, of course, do not touch KPP). Moreover, even devices with jailbreak installed boot in normal mode; To obtain superuser rights, the jailbreak will need to be run again, after loading.
To an absolute minimum, this risk is reduced in jailbreaks of the Rootless category. These jailbreaks not only do not modify the system, but do not even remount the system partition. Accordingly, such jailbreaks are not able to influence the boot process of the system in any way.
What are the risks of installing a jailbreak? We list.
1. The device’s Internet connection. During the installation of the jailbreak, you will have to obtain a digital signature for the IPA package, which contains the jailbreak. Unsigned IPAs cannot be transferred to the device, much less can not be launched on it. Digital signature issued by Apple servers; they must be contacted for its receipt. The process is automated: it uses a ready-made and very easy to use open source Cydia Impactor application. However, if you allow the device access to the Internet, you risk: an attacker can remotely send a command to the device to block it or destroy data.
Solution: You can work around this problem by using the Apple Developer Program certificate. See the Walkthrough for details.
2. Jailbreak just does not install. Yes, the second most serious risk is that the jailbreak simply won’t get on the iPhone. Jailbreaks do not use one, but a whole chain of vulnerabilities; finding and using such a chain correctly is hard work. Alas, the error at any stage leads to the fact that the jailbreak will not be established, and you will find yourself in the best case with a device without a jailbreak, and in the worst case with a device with a remounted system partition, but without a jailbreak (about what is bad - below )
Solution: generally speaking, there are many jailbreaks. For iOS 12, for example, we counted at least 4 workable jailbreaks (in fact, there are more). One jailbreak didn’t work? Just try another; about them again in the Walkthrough .
Effects
We figured out the risks, the jailbreak is installed. How could this threaten?
Before talking about the risks of jailbreak, we will understand their types. There are only two of them: ordinary (classic) jailbreaks, and rootless jailbreak.
The classic jailbreak provides the user with, so to speak, “full stuffing”: the digital signature verification is disabled (you can install and run any applications), a third-party application store is installed (most often this is Cydia, but alternative options also began to appear). For this, quite a lot of files are written to the system partition, and the system partition itself is remounted in r / w mode.
What does this mean in practice? Junk in the system partition, which sometimes cannot be completely removed during the process of jailbreak removal (especially if the user managed to try installing different jailbreaks). Potential (and often real) device instability. Finally, the inability to correctly install OTA updates. Only full firmware recovery through iTunes helps, and sometimes the instability of the device persists, and you have to reset to factory settings. Not too nice.
All these things do not happen if you use the new rootless type of jailbreak, the only representative of which is RootlessJB. This jailbreak did not win the popularity of its classic counterparts for an obvious reason: it does not install (and does not support work) third-party stores (Cyida and the like). An ordinary user-enthusiast at this moment, the interest disappears, and he sets up a classic jailbreak.
Meanwhile, for our purposes, RootlessJB is of particular value. The fact is that we should return the iPhone under study in approximately the form in which it was received for analysis. That is, at least the device should not work less stable than before the analysis, and there should be no problems installing OTA updates. These are exactly what RootlessJB gives us. Judge for yourself: this jailbreak does not modify the system partition without writing a single extra file to it. Moreover, he cannot do this: the principle of operation of this jailbreak does not imply remounting the system partition in r / w mode.
Further more. Since the RootlessJB jailbreak does not need to be supported by a third-party application store, there is no need to disable digital signature verification (you can run individual binaries, but the paths to them must be manually entered into the permission control file). No need to disable digital signature verification - no need to write anything to the system partition. The system partition does not need to be opened for recording - you can skip the operation of the corresponding vulnerability, which simplifies the installation process and makes it more reliable. In other words, for us, RootlessJB is literally a gift.
We finish the article with a table in which we compare the consequences of using different types of jailbreaks.

Conclusion
This article is the first one planned. I plan to talk about how exactly in the laboratories of the police and special services both in our country and abroad get access to information in Apple devices. Stay with us, it will be interesting!
Source: https://habr.com/ru/post/461729/
All Articles