17 ways to penetrate the company’s internal network
Safety The word meaning the security of a person or organization from something / someone. In the era of cybersecurity, we are increasingly thinking not so much about how to protect ourselves physically, but about how to protect ourselves from external threats ( cyber threats ).
Today we’ll talk about how you can penetrate a modern corporate network, which is protected on the perimeter by various, even very good, means of network security, and most importantly, we’ll talk about how to deal with this.

')
Let's look at a modern network that uses the latest technology in the field of security.

You have a perimeter protected, there are various Firewalls, Next-Generation Firewalls and many other perimeter security tools.
What are the options for penetrating your corporate network and in which cases your Next-Generation Firewall will not help you in any way?
Think for a moment. Try to answer this question, but I would like to give a few examples that can demonstrate that no matter how powerful, cool, widely advertised, that fall in the best squares, circles, Gartner, Forest curves and so on, the products you did not use, anyway There is the possibility of attackers attacking your corporate or departmental network, and therefore you need to look a little wider than the perimeter defense.
So, one of the examples that Cisco has come across is the use of DNS to steal information .

Typically, cybercriminals use the DNS protocol to either load some new modules or use DNS as an interaction between already installed modules inside a corporate / departmental network on infected computers with some “command servers”. In this case, the DNS protocol was used to leak information in the domain name. According to statistics, most domains, third-level domain names contain no more than 25-30 characters, however, we see that on the right graph, our domain lengths are 200-230 characters.
A person is not able to come up with this kind of domain. He is not able to remember him either. In its pure form, it is a kind of “anomaly” that can tell us that either domains are used for some marketing purposes, but usually these long ones are not even used for marketing purposes, or it is the actions of attackers. And in this case, 1 of the DNS servers serving this malicious domain was used to ensure that the domain names containing sufficiently long text strings ( 231 characters) were decrypted and stolen credit card numbers were revealed in them. As we understand, given that DNS is the de facto standard for the modern Internet, corporate or departmental networks, we cannot block DNS and even inspecting the DNS on the Firewall does not always help us, because in this case the attackers used a non-standard approach to circumvent perimeter protection.
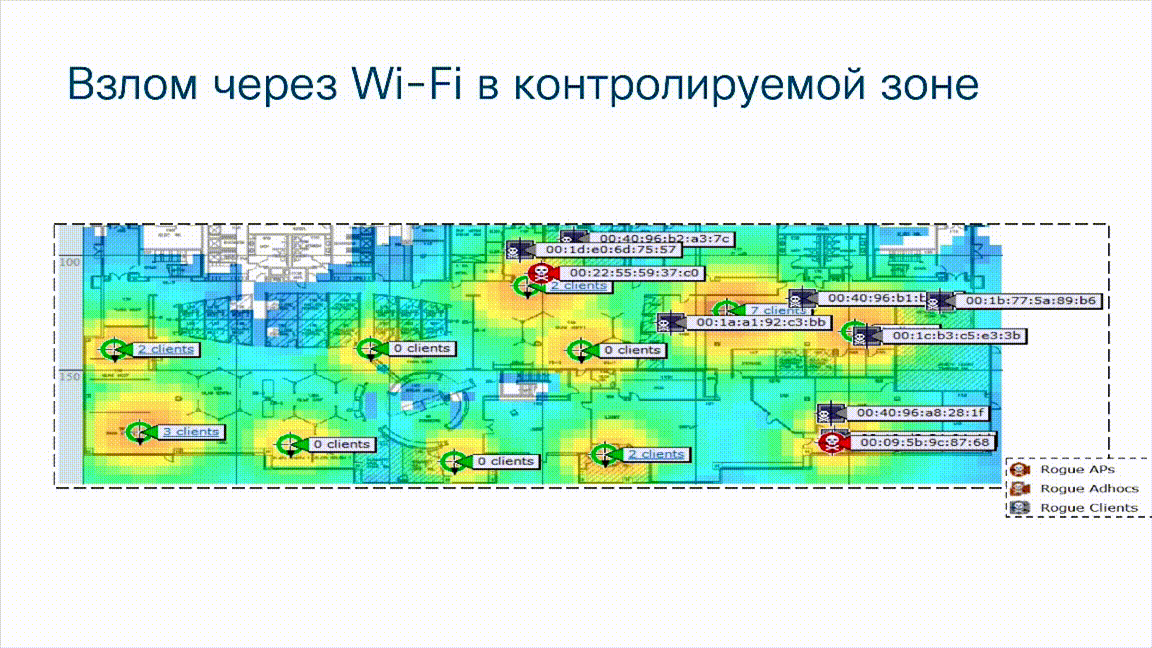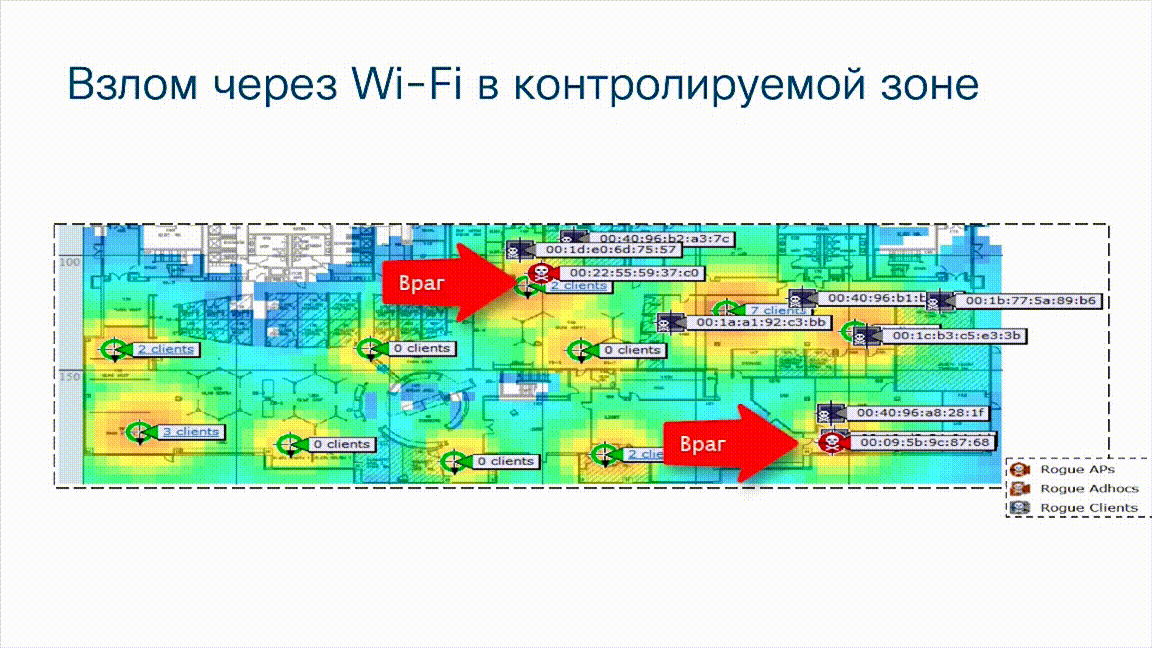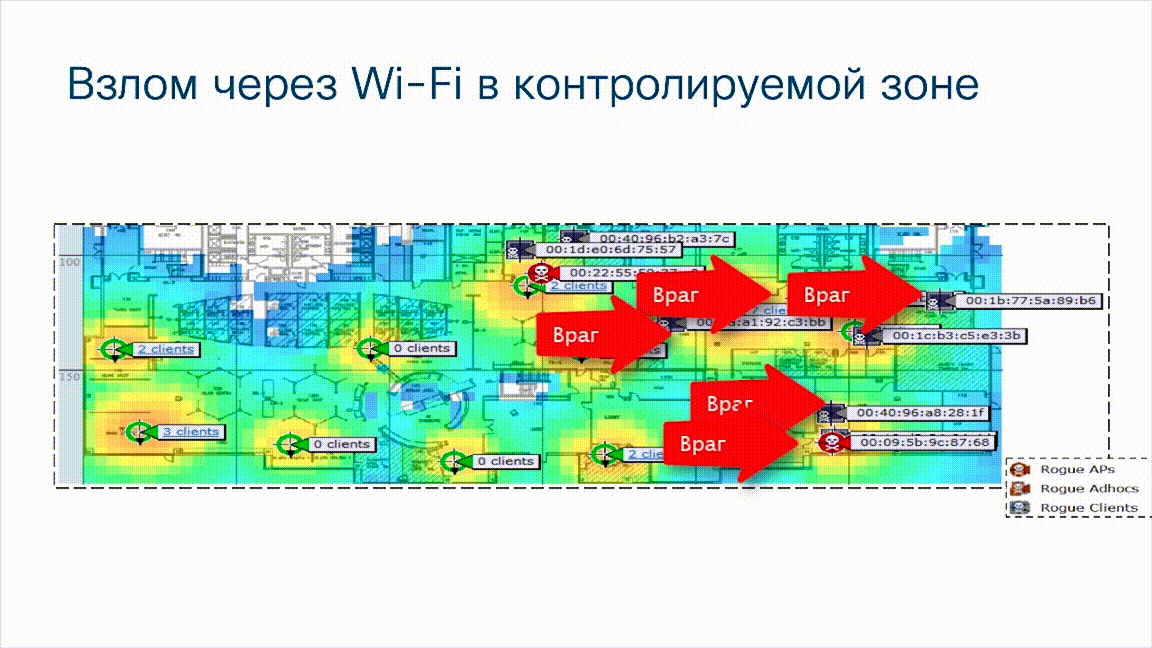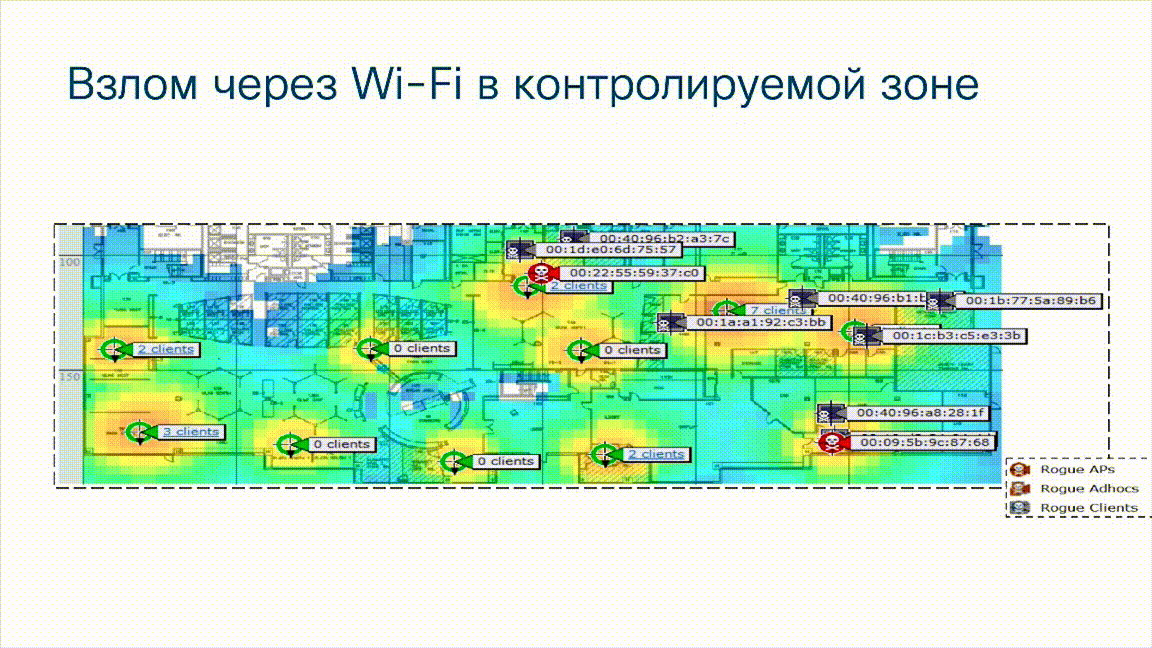
Another example
This is an illustration from a Cisco wireless network monitoring system. You see the location of legally installed access points ( green circles ) on the map of the building, but note that here we see that there are unauthorized wireless access points ( red circles ), as well as wireless, unauthorized foreign clients who are trying to connect to a corporate wireless network ( gray rectangles ). It is clear that this method of connection also bypasses the perimeter, also does not go through corporate Firewalls, and if access points were not protected, attackers could penetrate the corporate network bypassing the perimeter, bypassing the NG Firewalls standing on this same perimeter. In addition, if an attacker can create a fake access point, then the client who connected to the access point may not even know about it, while the attacker can intercept data that is transmitted from the client. It can be a smartphone, it can be a tablet, laptop or even a stationary computer that connected to an unauthorized, alien, fake access point and in this case, unfortunately, the Firewalls did not help us either.
Another example
Following this incident, Cisco substantially changed the security architecture of network equipment. Hardware and software components were added that allow you to track bookmarks in the equipment, as well as prevent the appearance of these bookmarks, but at the beginning of the 2000s there were such examples.
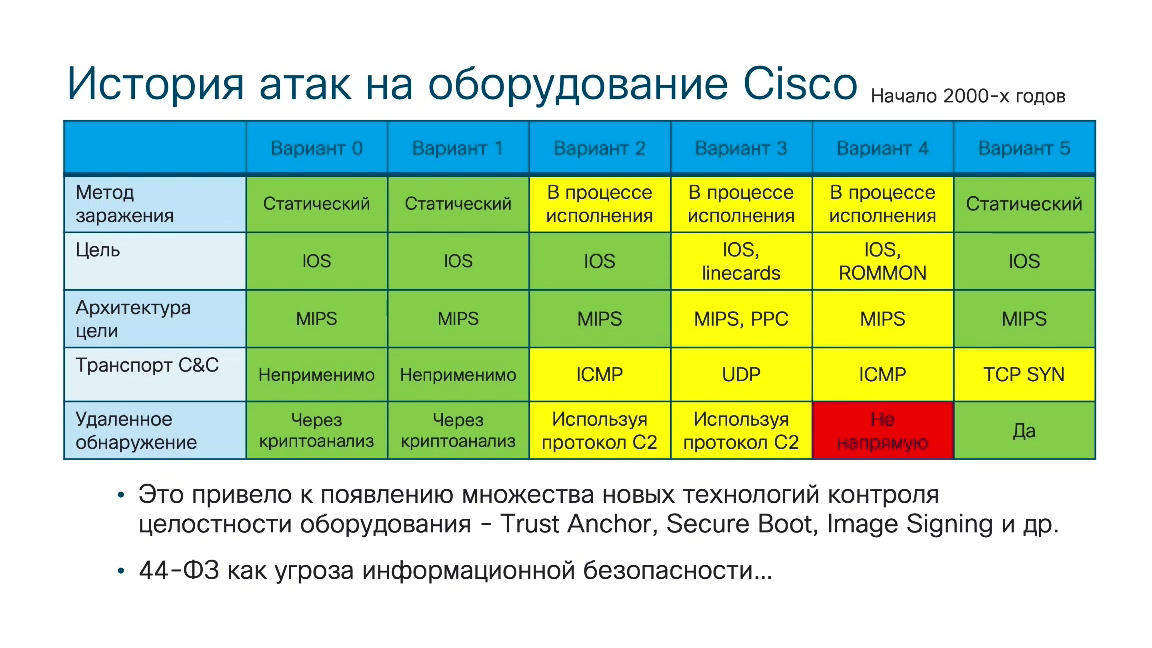
There were several of them that we managed to fix, and in this case we are faced with a situation where, as part of a certain delivery, the customer receives equipment with a pre-installed malicious code. Since he initially trusts his supplier, he does not think about the need to check network equipment. Verification can be done through software that the customer can download from the official website. This is necessary in order to make sure that the equipment does not have any bookmarks and it does not steal information that is transmitted through a network device. Also, there were several cases when administrators without a contract for technical support for the equipment they purchased, were forced to download new firmware from third-party sites. This also led to the fact that these firmware contained malicious code that “mirrored” all traffic and sent it to the attacker. That is, in this case, we also understand that classic perimeter security tools cannot do anything about this, because the bookmarks are on the equipment facing the firewalls.
You can recall a more recent example when Cisco (its division of Cisco Talos) discovered a threat called VPN-Filter, when attackers infected various network devices of various manufacturers (D-Link, Asus, etc.) and installed the corresponding malicious code on them, which also steal traffic and redirect it to attackers. That is, underestimating this problem leads to the fact that the lower level of the network infrastructure remains completely unprotected and no firewalls, of course, help here, since network devices are located before the firewalls and they can transmit all traffic, especially if It is not encrypted, by intruders.

One more example
2 years ago (in 2017), attackers found a vulnerability on the web portal of one of the largest credit bureaus Equifax. This vulnerability allowed to access the Web portal and execute some commands on it. After identifying the vulnerability, the attackers launched an exploit and gained access to the system with administrative rights. No data was stolen at that time. That is, the attackers only tested the very possibility of working on the Web portal with administrative rights. But then after about 2 months, a vulnerability that for some reason was not resolved was exploited.

Attackers entered the internal systems of the credit bureau and disguised their activities from network security. First, due to the trusting relationship between the Web portal and internal servers, including database servers, the security system did not control the connection data in any way and allowed the attacker to enter the corporate network. In addition, the attackers used an encrypted connection and it remained uncontrolled in terms of network security. For several months, the attacker managed to steal information, as a result of which more than 140 million citizens of the United States, Great Britain and several other countries were affected whose data was stolen as a result of this attack, despite the availability of perimeter protection, which, unfortunately, in this case does not did not help.

Another example
Another example occurred in the last year of 2018 when, in the two-week period between August 21 and September 5, a hacker group called Magic Art hacked British Airways’s servers and stole 380,000 customers' data, including personal data and credit card information. According to British Airways, about half a million customers suffered in two weeks .

The most interesting thing is that the attackers did not even try to penetrate the corporate network! They hacked into the airline’s website, replaced the script that collected customer data and forwarded this data to a malicious resource that was controlled by attackers. Also, according to one version of this incident, it is considered that the attackers did not hack into the main site of British Airways, but its cached copy (CDN, used by communication providers to cache popular resources). Thus, perimeter defense did not help to defend against this attack.
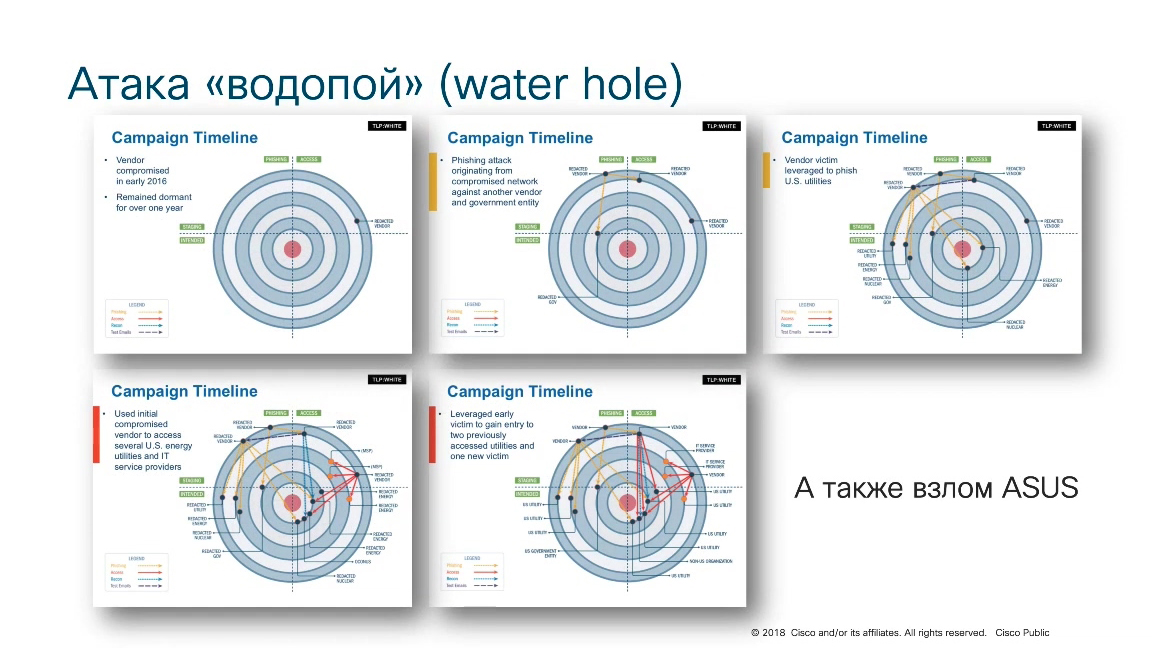
Another attack , called the “water hole”, which was recorded some time ago by US law enforcement. Attacks against a number of energy companies in the United States of America were recorded, and a very unconventional scheme was identified as part of the investigation, which, however, has since become quite popular.
Why is it called a watering place?
If we recall the life of animals (especially animals of Africa), then during a drought, many animals come to rare watering places that did not dry out during a drought and nature makes it so that the animals do not attack each other during a watering, but the fact is that just on the way to the watering place, predators very often wait for animals and eat them in order to feed themselves and their herds, prides and so on (depending on which predator we are talking about). So the attackers took advantage of exactly the same strategy.
Instead of breaking the victim companies, on which they focus their efforts, there can be many such companies (units, tens or even hundreds). Sometimes it’s enough to hack just one software manufacturer, from the site of which then everyone starts to download software updates (new firmware, patches, updates or new software versions). If the manufacturer was hacked, then along with these updates that are downloaded from his website, it is possible to place malicious code on the network of the victim company, which then makes it easier for hackers to develop a bridgehead inside the victim’s already compromised network. That is, in such a roundabout way, but the hackers achieved their goal. This kind of attack was recorded in 2016 in the United States of America. After that, there were several similar scenarios. Just recently (at the end of 2018), an attack was recorded on Asus, which distributed malicious updates from its website. The same thing was done by Avast, which distributed an infected program for defragmenting and optimizing the operation of a Windows system called CCleaner. This malicious campaign was detected and uncovered by Cisco Talos in 2017.
These are all examples when it is far from always necessary to crack the victim’s company itself. You can hack into the organizations serving it and due to some trusting relationships between the victim company and the hacked company, all communications between it are subject to less control and this is actively used by attackers.

Finally, the last and one of the most recent examples.
On June 18, 2019, NASA's aerospace agency recorded and announced that hackers had already entered the internal network of one of its units (one of its laboratories) in April 2018. That is, they for a long time went unnoticed and were able to steal more than 500 MB of data on the mission to Mars. The most interesting thing that happened was due to the introduction of the Raspberry Pi hardware portable computer, which was installed on the NASA network and which stole information and transmitted it outside.
These examples all demonstrate very well that even the presence of very powerful, well-designed, well-designed perimeter defense systems does not guarantee that intruders will not penetrate.

This is due to the fact that they have 17 channels of penetration into our organization , some of which we have already watched.
There are some channels that are beyond the scope of the review (for example, a regular VPN connection, or a site-to-site VPN with remote sites, or Remote Access VPN with remote users), but if there is a secure connection over it, in addition to completely legal traffic , can penetrate and malicious in the internal network of the company. USB flash drives thrown in the parking lot in front of the organization’s entrance are also a favorite tool that cybercriminals use to bypass perimeter means of corporate information security or departmental information security, because such a USB stick is inserted into the computer and bypasses all perimeter protection means. One can only hope that something more modern than the antivirus obsolete by ideology is installed on the computer, which does not see any targeted attacks aimed at organizing.
Another example Cisco encountered two years ago.
The CEO of a large Russian energy company “infected” on his home laptop with malicious code WannaCry. This happened on Friday night, just as WannaCry began to spread around the world. On Saturday morning, the director brought an infected laptop to work. Well, where else to bring it? There are no IT specialists at home, but they are at work.
While these specialists, urgently called by the CEO, were driving to work, the malicious code managed to spread through the corporate network, because the CEO connected this laptop to the corporate network. He connected automatically, after which even the corporate network isolated from the outside world suffered from WannaCry.
It is clear that Cisco can have many more such examples when a high-ranking or authorized employee, manager, middle or senior manager brings a home device to work, which for some reason can be infected. It may even be not only an employee. It may be an auditor. This may be a contractor who brings this kind of device as part of certain routine maintenance on the protected site. For example, in 2003, it was because of the contractor who connected his laptop to the internal network at the Davis – Besse nuclear power plant in the United States of America that the nuclear power plant was infected by the Conficker worm, which led to the shutdown of the reactor and a blackout on the entire east coast of the USA .
Another example when they work with perimeter protection methods is developers who work on DevOps, who usually have their own “rules of the game”, who like to work not on computers issued by the company, but on their laptops with their own software, which you can always put some means of protection and this is a kind of "entry point" into the corporate network, or the introduction of bookmarks in the software developed in the organization.
Finally, we must not forget about the clouds.
If your organization uses clouds extensively, no corporate perimeter protection will help. It is necessary to expand the security system outside the perimeter and monitor the internal infrastructure.
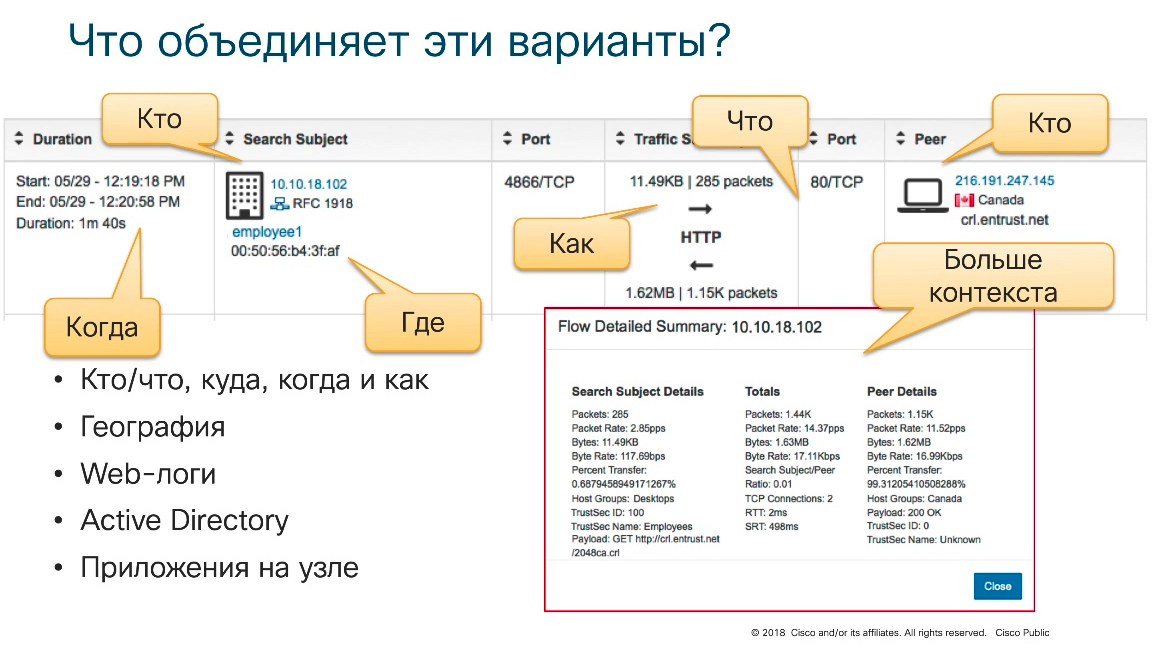
The NetFlow protocol, which was originally developed for Troubleshooting, to analyze network traffic statistics, will help in this, but due to its capabilities, especially due to the advanced features that exist in the ninth version of the NetFlow protocol, or in its standardized version of IPFIX, it is possible to answer questions who are interested from the point of view of information security (who ?, what ?, when?, how?, in what volume? carried out certain interactions). Then, having imposed the appropriate decision-making algorithms on it, it becomes possible to draw conclusions about the presence of a particular threat, one or another anomaly, which may be interesting in the context of information security.
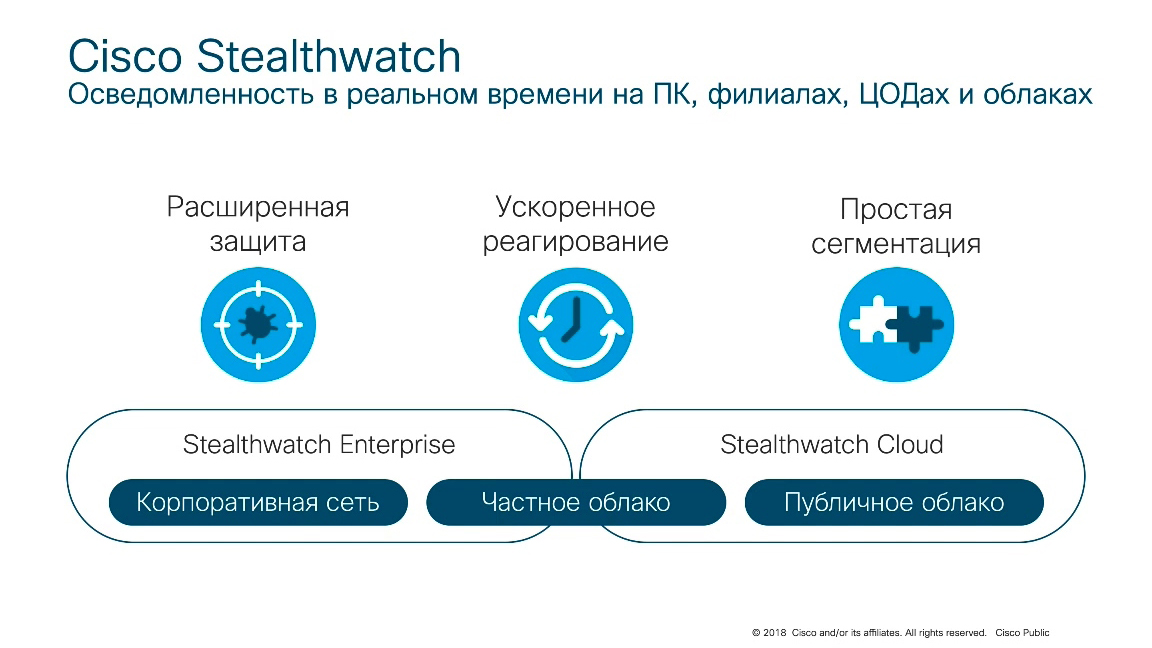
One example of a solution that uses this particular design for informational purposes is the Cisco Stealthwatch solution .
This is a solution that analyzes Flow protocols (not only NetFlow). It can be sFlow, Jflow, IPFIX, NetStream - it doesn’t matter. That is, this solution will work not only on the Cisco infrastructure, but also on the infrastructure of other vendors (including even Russian manufacturers that support the protocol with Flow), or when it is possible to transfer traffic via PAN, or Airspan to Cisco Stealthwatch and By analyzing the existing infrastructure, it is possible to identify certain anomalies, certain threats in the corporate or departmental network.
One of the key differences between this approach and perimeter protection is that the administrator does not need to install separate sensors, separate taps in the control points of the network at control points. Cisco is turning the existing network infrastructure into this kind of distributed monitoring system.
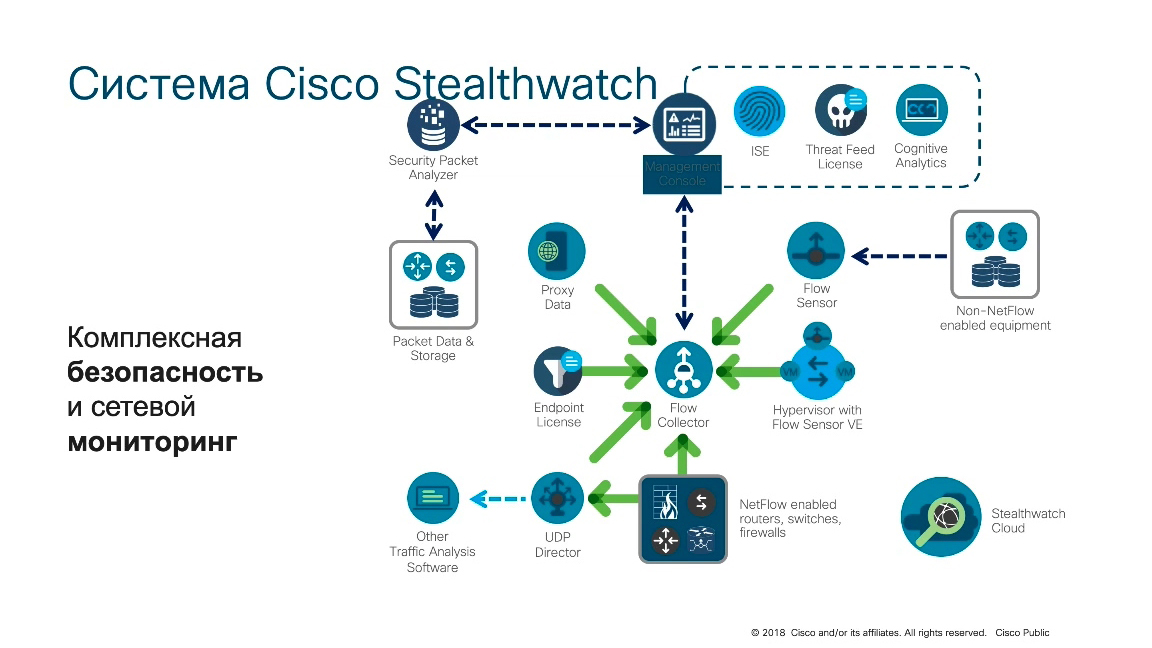
In its minimum solution, the Cisco stealthwatch consists of two components - Flow Collector, which collects data from devices supporting Flow protocols and a management console that is responsible for management, visualization, report generation, and so on. In those cases, if for some reason the device either does not support Flow, or support for enabling Flow leads to a significant processor load, you can use the so-called “Flow sensors”. This is a hardware or virtual solution that passes network traffic through itself, transmits it to NetFlow and transfers it to the Flow Collector. Thus, it is possible to connect some equipment to the Flow Sensor than connect the span port that initially does not support the Flow protocol and provide full and greater visibility of the internal network, not just its perimeter.
In addition to Flow sensors, there is also such a component as UDP Direcrot, which allows you to efficiently process data from remote sites. When there is a weak Internet channel between the remote site and headquarters, but NetFlow data must be transmitted, UDP Direcrot optimizes the transmission of such traffic.
In addition, Cisco has developed a special protocol nvzFlow, which allows you to integrate the network component with the host, and through the Network Visibility module, the module that is built into AnyConnect (this is a software security client that installs on Windows, Linux, Mac OS, iOS, Android, and so on ) Thanks to this, it became possible to translate the behavior of the node, the behavior of user applications into a protocol similar to NetFlow and to automatically correlate events that occur on nodes with events that occur at the network level, thereby improving the state of information security monitoring in a corporate or departmental network.
Another element that can send data to the Flow Collector is a proxy server, and thus you can correlate the network layer data that is obtained after analyzing NetFlow or other Flow protocols and the application layer that we receive from various proxy servers, thereby making it possible record the work of encryptors, interaction with command servers, network operation by the Tor network, and so on.
In order to collect evidence of unlawful activity, in order to store it, conduct an investigation, or transfer it to law enforcement, Cisco Stealthwatch solutions integrate with the Cisco Security Packet Analyzer component, which just stores all the information necessary for further investigation and interaction with law enforcement agencies.
The most interesting thing is that this solution works not only inside the corporate / departmental network, not only inside the data center, not only inside the industrial site (for example, in the automated process control system), but it can also work on various cloud platforms, thereby a single solution allows you to see different areas corporate or departmental network. To see anomalies in them, to see a threat and to signal accordingly and, if necessary, block these threats, relying not only on what passes through the corporate perimeter. If you notice some kind of flash drive, unprotected Wi-Fi, dropped Raspberry Pi into the corporate network and so on, the perimeter will not see this. This will see a Stealthwatch that properly monitors everything that passes through the network infrastructure.As if it were disguised as an attacker, it will always go through the switches and routers that we have located on the corporate or departmental network. He can’t bypass them in principle, and in this case Stealthwatch works, which sees all network traffic and, due to the imposition of a large number of different algorithms, can detect various anomalies or threats.
It looks as follows.
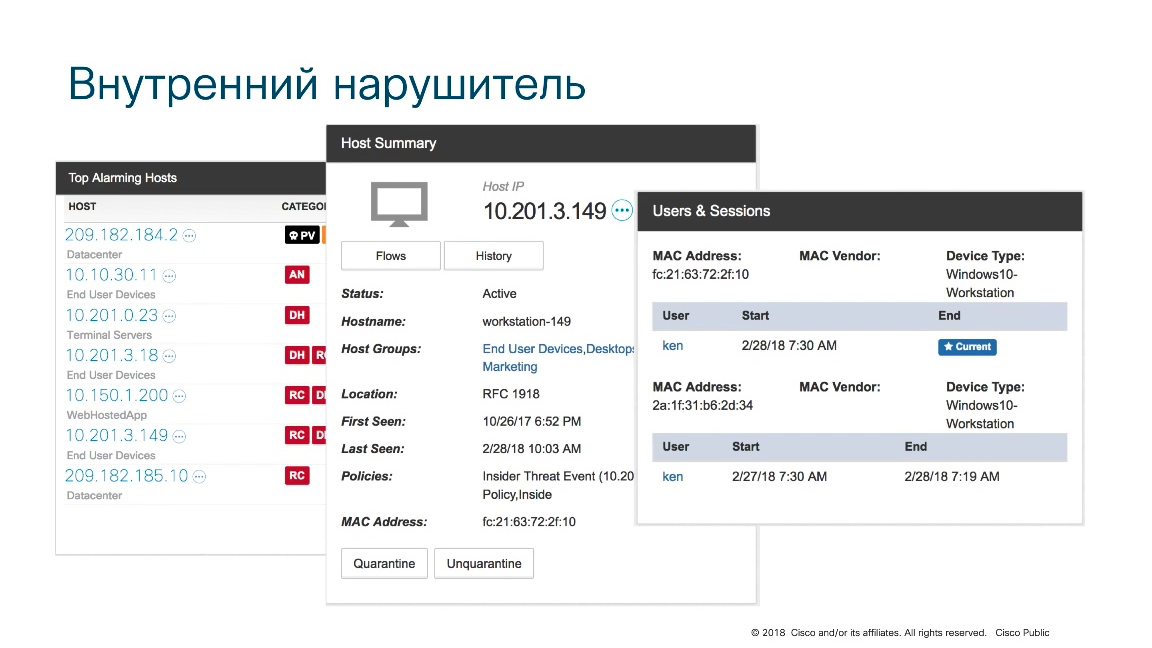
The picture shows the top nodes that are fixed for a certain time interval. One of these nodes has the address 10.201.3.149. This is a workstation. It is in the user device group. It can be seen when and what activity occurred on this node. You can see which policies are applied to this node. It can be seen what kind of user is working on this node, for example due to integration with the Active directory. Thus, we know a specific user, a specific employee of the organization, who works at a particular moment on this host and this allows for more rapid investigation of incidents.
But this is far from all that can be seen.

Suppose we see events with a very high level of suspicion, the so-called "Concern Index" and want to get more detailed information about what is hidden behind this event. We want to get all associated connections associated with this threat of information leakage.

Having done this, it was discovered that the intruder uses the SSH protocol to capture data from the internal corporate network. Please note that while only about one gigabyte of data was sent from the attacker's site, more than 160 GB of data was received. It is possible that we are talking about an attacker who is trying to capture data that he manages to "reach out" and download it to his computer. For what?
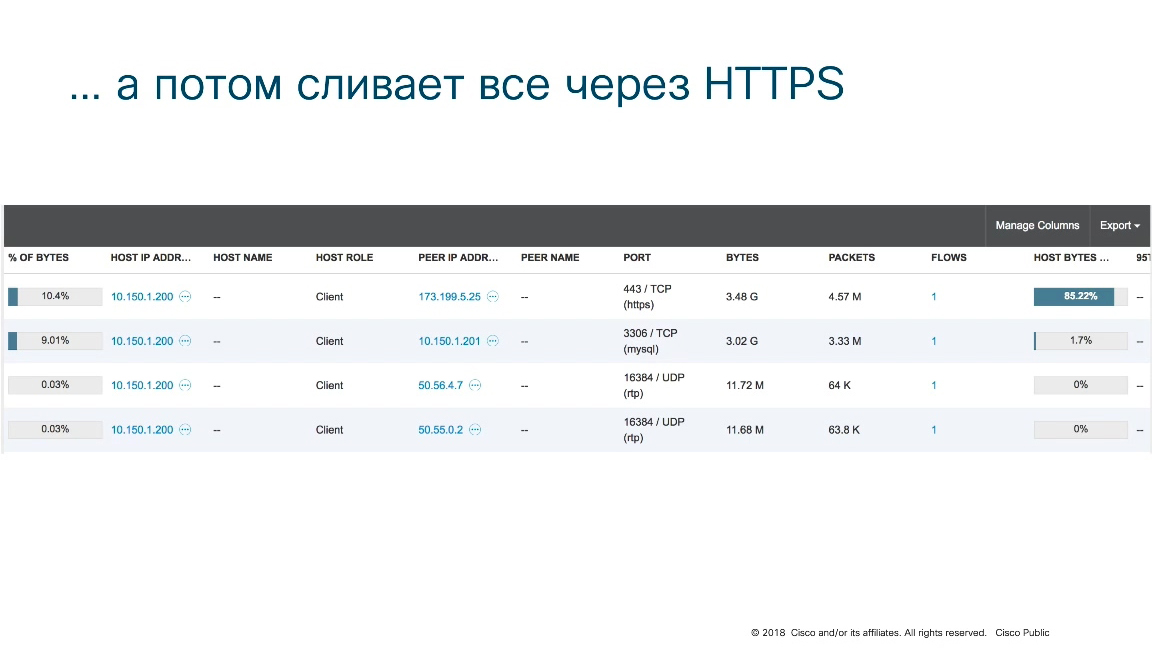
Here Stealthwatch also helps.
In this case, it can be seen that the hacker "merges" the data through an HTTPS connection somewhere to an external host. That is, perhaps this is really an attacker who, as if recalling the story of Snowden, at the beginning copied to himself all the data that he could reach, and then he tries to transfer it outside the company. In the case of Snowden, he did this on external media, taking him outside the checkpoint. In the case of this case, the attacker is trying to "merge" the data via HTTPS out to some command server, to the cloud, or somewhere else.

Another example of how Cisco Stealthwatch can help. For example, the spread of worms or malicious code within the corporate network.
Usually, in order to fix this, you need to have agent / agents on the host. There may be an antivirus. It could be a class decision and an EDR (endpoint detection and response). It may be something else that, by analyzing the activity on the node, detects the actions of malicious code. But what should we do if we cannot install agents on the nodes (for example, these agents too “eat up” processor power, or increase the load on it, or “eat up” RAM)? The computer slows down and therefore does not want to put any protective agents on it (for example, in the data center). Or this is a segment on which you can’t put any protective agents at all. It can be an industrial segment (ACS TP), it can be a segment with operating systems for which protective agents have not been developed. There can be many reasons.In other words, in the absence of host protections, engineers remain blind. They have the only data source for detecting malicious activity - this is network traffic and Stealthwatch again helps here, which in this case recorded the actions of malicious code. Node scanning events are visible, and in the details of this event, you can see that this activity is inherent in the spread of worms over the network.
This can be visualized.

Vizit in this form.
Visualization is taking place and we can understand where the starting point was, who further came under the distribution and quickly localize the problem, preventing it from developing on our network, preventing the attacker from expanding the "bridgehead" in our corporate or departmental network. And what to do in situations where attackers begin to actively use encryption, as for example the case with Equifax?

Unfortunately, according to Cisco statistics, cybercriminals over the past year have 3 times increased the number of malicious programs that they use for their activities, or rather, to hide it - encryption. It is known from theory that the “correct” encryption algorithm cannot be hacked. In order to understand what is hidden inside the encrypted traffic, you must either decrypt it knowing the key, or try to decrypt it with various tricks, or by hacking it in the forehead, or using some vulnerabilities in cryptographic protocols.
In fact, it turned out that in practice there are other methods of analyzing encrypted traffic without decrypting it. This method is simply called "machine learning." It turned out that if a very large amount of various traffic used by cybercriminals was applied to the input of a special classifier and trained to classify this kind of malicious action, even inside encrypted traffic that we cannot decrypt or decrypt, the system can detect with a very high degree of probability malicious code inside encrypted traffic.
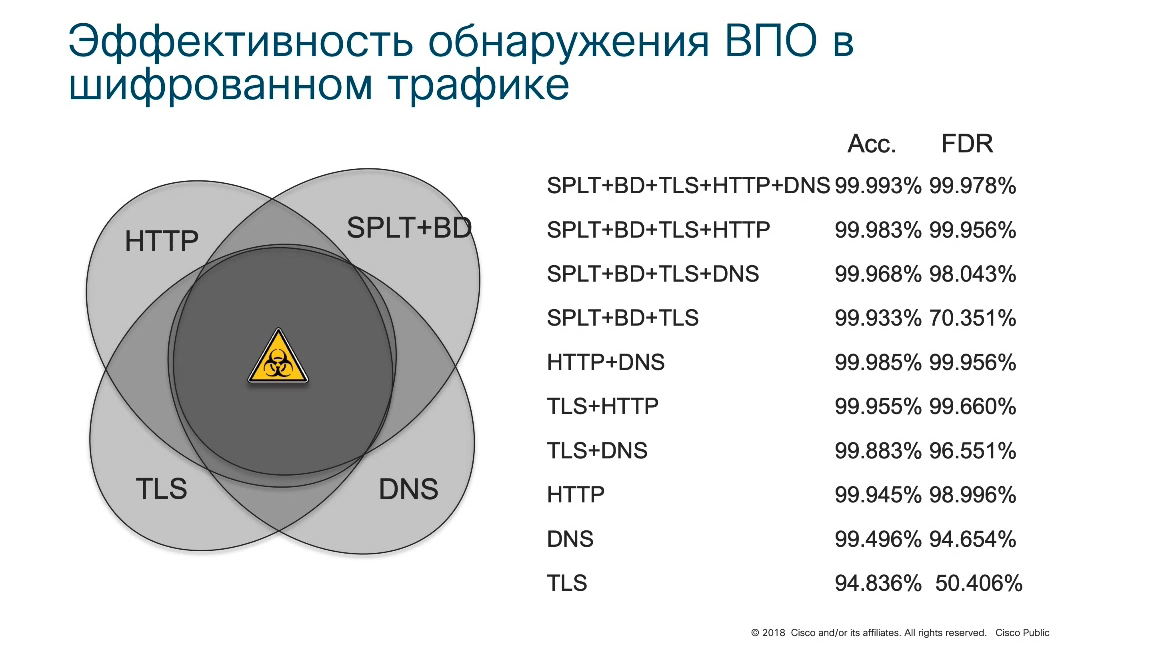
Please note the detection accuracy is 99.99%. False positives are hundredths of a percent. That is, based on the analysis of telemetry that Cisco receives from network equipment, even without any cryptographic transformations, it can be said that malicious activity is hidden inside this or that encrypted traffic and this allows more efficient monitoring of the internal infrastructure.
Today, many companies, many service applications are moving to the TLS 1.3 protocol.which cannot be decrypted initially. That is, it is specially designed so that it is impossible to make even the legal Man In The Middle. This is done to ensure the privacy of user data. This user privacy, unfortunately, does not play into the hands, but against corporate security services, which earlier (before TLS 1.3) could still decrypt traffic on the perimeter using various SCAffolders, but now, unfortunately, do it already impossible. But the technology that is embedded in Cisco Stealthwatch called Encrypted Traffic Analytics allows you to understand what is inside without decrypting traffic . Of course, no one will understand what is written there. It's impossible.Cryptography works here. But you can understand the type of this traffic and if it is malicious, then make the appropriate decisions.

Here's what the Encrypted Traffic Analytics technology looks like.
It can be seen that information is being leaked (“Exfiltration” inscription - data leak) from a particular node, which a user by the name of Roland Torsiello is working on and the “Encrypted” mark is visible. This means traffic is encrypted. That is, despite the presence of encryption, it is still possible to record the fact of information leakage, that is, damage to the corporate resource.
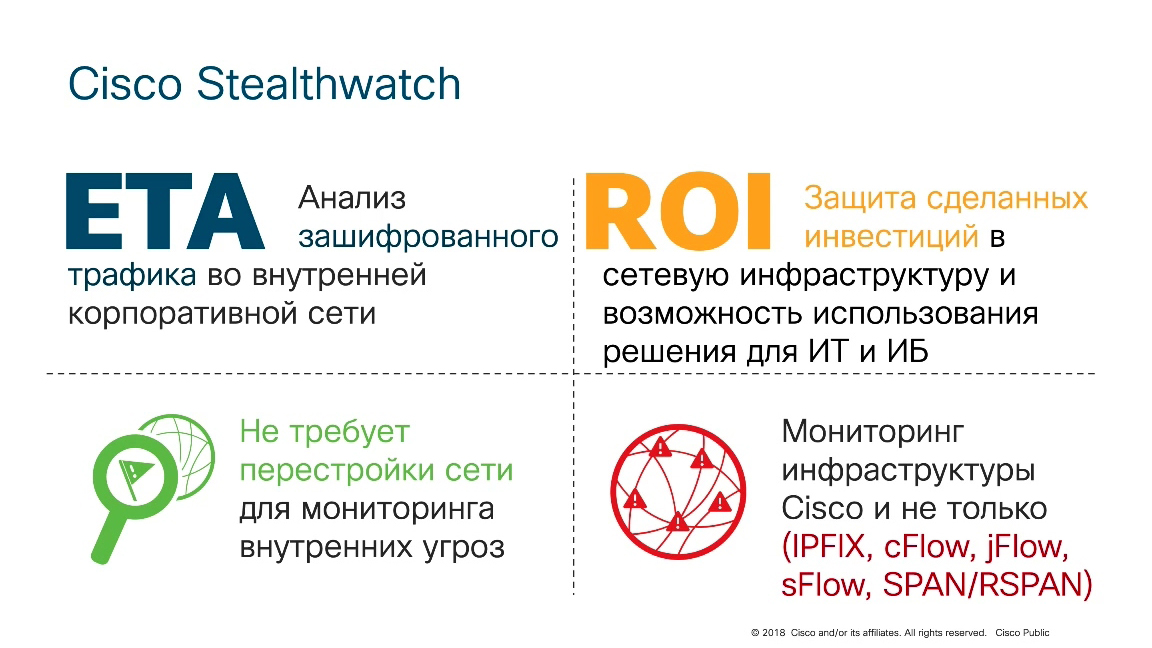
I want to note that the Cisco Stealthwatch solution has a number of very important features. Important benefits.
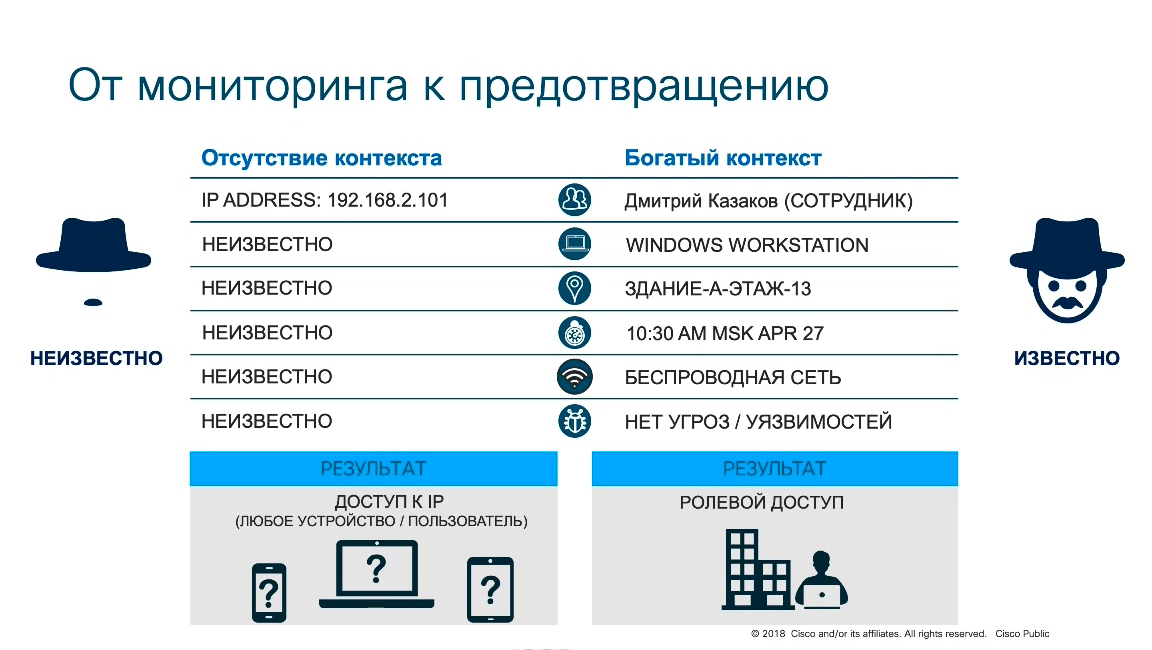
After some malicious activity was recorded, the question arises: “How to block it?”.

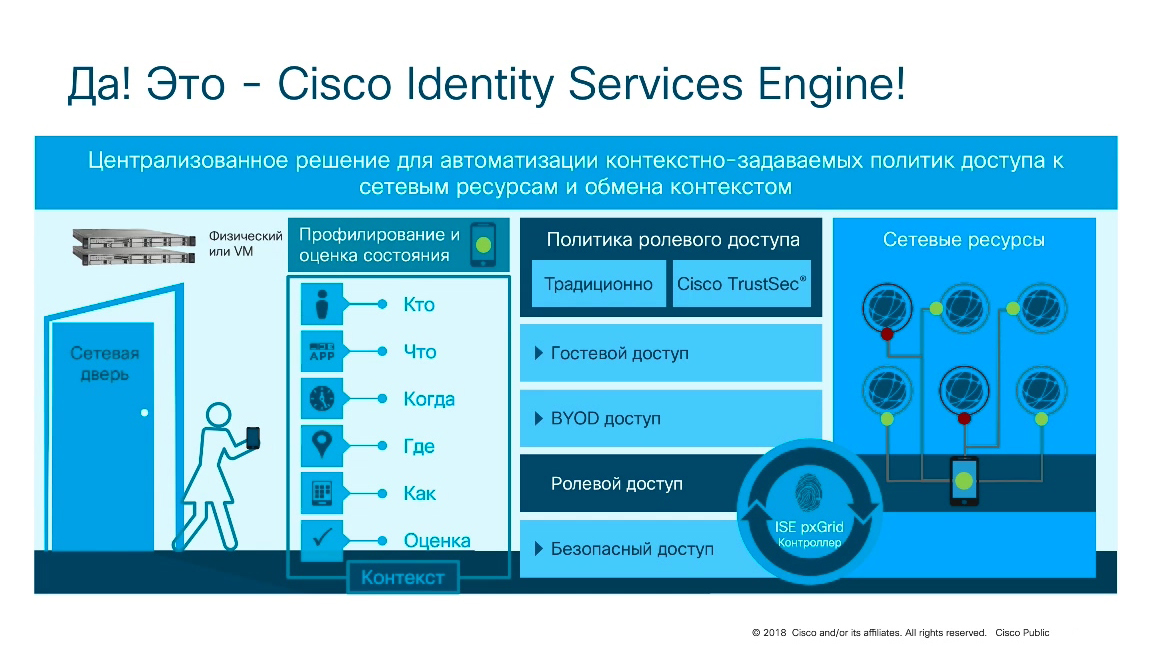
In this case, the Cisco ISE (Identity Services Engine) solution is very suitable , which turns a network infrastructure that has already turned into a distributed attack detection system, and Cisco ISE turns it into a distributed firewall. This is when each switch, each router, each access point is used as a decision point - “start up or not start up?”, “Start up the user?”, “Start up the device?”, “Start up the application?” To the requested resource. Cisco ISE turns the existing infrastructure (and not only the origin of Cisco, this can be done on other vendors) into a distributed firewall. If NG Firewalls (for example, Cisco FirePower) and NGIPS (for example, Cisco Firepower IPS) are usually used on the perimeter, then you can use the Cisco Stealthwatch and Cisco ISE bundles in the internal network.

Together, they allow you to monitor and control access to the internal infrastructure, significantly reducing the attack area and, most importantly, that they can be integrated with perimeter defense tools and they have a single end-to-end security policy. In the event that the Cisco solution is not on the perimeter, anyway, due to Cisco ISE, you can create a single end-to-end security policy, thereby increasing the security of corporate / departmental resources from the actions of attackers who have learned how to bypass the perimeter protection system in different ways.
Video presentation:
Audio presentation:
For all the information provided, many thanks to Cisco and
Today we’ll talk about how you can penetrate a modern corporate network, which is protected on the perimeter by various, even very good, means of network security, and most importantly, we’ll talk about how to deal with this.

')
Let's look at a modern network that uses the latest technology in the field of security.

You have a perimeter protected, there are various Firewalls, Next-Generation Firewalls and many other perimeter security tools.
What are the options for penetrating your corporate network and in which cases your Next-Generation Firewall will not help you in any way?
Think for a moment. Try to answer this question, but I would like to give a few examples that can demonstrate that no matter how powerful, cool, widely advertised, that fall in the best squares, circles, Gartner, Forest curves and so on, the products you did not use, anyway There is the possibility of attackers attacking your corporate or departmental network, and therefore you need to look a little wider than the perimeter defense.
So, one of the examples that Cisco has come across is the use of DNS to steal information .

Typically, cybercriminals use the DNS protocol to either load some new modules or use DNS as an interaction between already installed modules inside a corporate / departmental network on infected computers with some “command servers”. In this case, the DNS protocol was used to leak information in the domain name. According to statistics, most domains, third-level domain names contain no more than 25-30 characters, however, we see that on the right graph, our domain lengths are 200-230 characters.
A person is not able to come up with this kind of domain. He is not able to remember him either. In its pure form, it is a kind of “anomaly” that can tell us that either domains are used for some marketing purposes, but usually these long ones are not even used for marketing purposes, or it is the actions of attackers. And in this case, 1 of the DNS servers serving this malicious domain was used to ensure that the domain names containing sufficiently long text strings ( 231 characters) were decrypted and stolen credit card numbers were revealed in them. As we understand, given that DNS is the de facto standard for the modern Internet, corporate or departmental networks, we cannot block DNS and even inspecting the DNS on the Firewall does not always help us, because in this case the attackers used a non-standard approach to circumvent perimeter protection.

Another example
This is an illustration from a Cisco wireless network monitoring system. You see the location of legally installed access points ( green circles ) on the map of the building, but note that here we see that there are unauthorized wireless access points ( red circles ), as well as wireless, unauthorized foreign clients who are trying to connect to a corporate wireless network ( gray rectangles ). It is clear that this method of connection also bypasses the perimeter, also does not go through corporate Firewalls, and if access points were not protected, attackers could penetrate the corporate network bypassing the perimeter, bypassing the NG Firewalls standing on this same perimeter. In addition, if an attacker can create a fake access point, then the client who connected to the access point may not even know about it, while the attacker can intercept data that is transmitted from the client. It can be a smartphone, it can be a tablet, laptop or even a stationary computer that connected to an unauthorized, alien, fake access point and in this case, unfortunately, the Firewalls did not help us either.
Another example
Following this incident, Cisco substantially changed the security architecture of network equipment. Hardware and software components were added that allow you to track bookmarks in the equipment, as well as prevent the appearance of these bookmarks, but at the beginning of the 2000s there were such examples.

There were several of them that we managed to fix, and in this case we are faced with a situation where, as part of a certain delivery, the customer receives equipment with a pre-installed malicious code. Since he initially trusts his supplier, he does not think about the need to check network equipment. Verification can be done through software that the customer can download from the official website. This is necessary in order to make sure that the equipment does not have any bookmarks and it does not steal information that is transmitted through a network device. Also, there were several cases when administrators without a contract for technical support for the equipment they purchased, were forced to download new firmware from third-party sites. This also led to the fact that these firmware contained malicious code that “mirrored” all traffic and sent it to the attacker. That is, in this case, we also understand that classic perimeter security tools cannot do anything about this, because the bookmarks are on the equipment facing the firewalls.
You can recall a more recent example when Cisco (its division of Cisco Talos) discovered a threat called VPN-Filter, when attackers infected various network devices of various manufacturers (D-Link, Asus, etc.) and installed the corresponding malicious code on them, which also steal traffic and redirect it to attackers. That is, underestimating this problem leads to the fact that the lower level of the network infrastructure remains completely unprotected and no firewalls, of course, help here, since network devices are located before the firewalls and they can transmit all traffic, especially if It is not encrypted, by intruders.

One more example
2 years ago (in 2017), attackers found a vulnerability on the web portal of one of the largest credit bureaus Equifax. This vulnerability allowed to access the Web portal and execute some commands on it. After identifying the vulnerability, the attackers launched an exploit and gained access to the system with administrative rights. No data was stolen at that time. That is, the attackers only tested the very possibility of working on the Web portal with administrative rights. But then after about 2 months, a vulnerability that for some reason was not resolved was exploited.

Attackers entered the internal systems of the credit bureau and disguised their activities from network security. First, due to the trusting relationship between the Web portal and internal servers, including database servers, the security system did not control the connection data in any way and allowed the attacker to enter the corporate network. In addition, the attackers used an encrypted connection and it remained uncontrolled in terms of network security. For several months, the attacker managed to steal information, as a result of which more than 140 million citizens of the United States, Great Britain and several other countries were affected whose data was stolen as a result of this attack, despite the availability of perimeter protection, which, unfortunately, in this case does not did not help.

Another example
Another example occurred in the last year of 2018 when, in the two-week period between August 21 and September 5, a hacker group called Magic Art hacked British Airways’s servers and stole 380,000 customers' data, including personal data and credit card information. According to British Airways, about half a million customers suffered in two weeks .

The most interesting thing is that the attackers did not even try to penetrate the corporate network! They hacked into the airline’s website, replaced the script that collected customer data and forwarded this data to a malicious resource that was controlled by attackers. Also, according to one version of this incident, it is considered that the attackers did not hack into the main site of British Airways, but its cached copy (CDN, used by communication providers to cache popular resources). Thus, perimeter defense did not help to defend against this attack.

Another attack , called the “water hole”, which was recorded some time ago by US law enforcement. Attacks against a number of energy companies in the United States of America were recorded, and a very unconventional scheme was identified as part of the investigation, which, however, has since become quite popular.
Why is it called a watering place?
If we recall the life of animals (especially animals of Africa), then during a drought, many animals come to rare watering places that did not dry out during a drought and nature makes it so that the animals do not attack each other during a watering, but the fact is that just on the way to the watering place, predators very often wait for animals and eat them in order to feed themselves and their herds, prides and so on (depending on which predator we are talking about). So the attackers took advantage of exactly the same strategy.
Instead of breaking the victim companies, on which they focus their efforts, there can be many such companies (units, tens or even hundreds). Sometimes it’s enough to hack just one software manufacturer, from the site of which then everyone starts to download software updates (new firmware, patches, updates or new software versions). If the manufacturer was hacked, then along with these updates that are downloaded from his website, it is possible to place malicious code on the network of the victim company, which then makes it easier for hackers to develop a bridgehead inside the victim’s already compromised network. That is, in such a roundabout way, but the hackers achieved their goal. This kind of attack was recorded in 2016 in the United States of America. After that, there were several similar scenarios. Just recently (at the end of 2018), an attack was recorded on Asus, which distributed malicious updates from its website. The same thing was done by Avast, which distributed an infected program for defragmenting and optimizing the operation of a Windows system called CCleaner. This malicious campaign was detected and uncovered by Cisco Talos in 2017.
These are all examples when it is far from always necessary to crack the victim’s company itself. You can hack into the organizations serving it and due to some trusting relationships between the victim company and the hacked company, all communications between it are subject to less control and this is actively used by attackers.

Finally, the last and one of the most recent examples.
On June 18, 2019, NASA's aerospace agency recorded and announced that hackers had already entered the internal network of one of its units (one of its laboratories) in April 2018. That is, they for a long time went unnoticed and were able to steal more than 500 MB of data on the mission to Mars. The most interesting thing that happened was due to the introduction of the Raspberry Pi hardware portable computer, which was installed on the NASA network and which stole information and transmitted it outside.
These examples all demonstrate very well that even the presence of very powerful, well-designed, well-designed perimeter defense systems does not guarantee that intruders will not penetrate.

This is due to the fact that they have 17 channels of penetration into our organization , some of which we have already watched.
There are some channels that are beyond the scope of the review (for example, a regular VPN connection, or a site-to-site VPN with remote sites, or Remote Access VPN with remote users), but if there is a secure connection over it, in addition to completely legal traffic , can penetrate and malicious in the internal network of the company. USB flash drives thrown in the parking lot in front of the organization’s entrance are also a favorite tool that cybercriminals use to bypass perimeter means of corporate information security or departmental information security, because such a USB stick is inserted into the computer and bypasses all perimeter protection means. One can only hope that something more modern than the antivirus obsolete by ideology is installed on the computer, which does not see any targeted attacks aimed at organizing.
Another example Cisco encountered two years ago.
The CEO of a large Russian energy company “infected” on his home laptop with malicious code WannaCry. This happened on Friday night, just as WannaCry began to spread around the world. On Saturday morning, the director brought an infected laptop to work. Well, where else to bring it? There are no IT specialists at home, but they are at work.
While these specialists, urgently called by the CEO, were driving to work, the malicious code managed to spread through the corporate network, because the CEO connected this laptop to the corporate network. He connected automatically, after which even the corporate network isolated from the outside world suffered from WannaCry.
It is clear that Cisco can have many more such examples when a high-ranking or authorized employee, manager, middle or senior manager brings a home device to work, which for some reason can be infected. It may even be not only an employee. It may be an auditor. This may be a contractor who brings this kind of device as part of certain routine maintenance on the protected site. For example, in 2003, it was because of the contractor who connected his laptop to the internal network at the Davis – Besse nuclear power plant in the United States of America that the nuclear power plant was infected by the Conficker worm, which led to the shutdown of the reactor and a blackout on the entire east coast of the USA .
Another example when they work with perimeter protection methods is developers who work on DevOps, who usually have their own “rules of the game”, who like to work not on computers issued by the company, but on their laptops with their own software, which you can always put some means of protection and this is a kind of "entry point" into the corporate network, or the introduction of bookmarks in the software developed in the organization.
Finally, we must not forget about the clouds.
If your organization uses clouds extensively, no corporate perimeter protection will help. It is necessary to expand the security system outside the perimeter and monitor the internal infrastructure.

The NetFlow protocol, which was originally developed for Troubleshooting, to analyze network traffic statistics, will help in this, but due to its capabilities, especially due to the advanced features that exist in the ninth version of the NetFlow protocol, or in its standardized version of IPFIX, it is possible to answer questions who are interested from the point of view of information security (who ?, what ?, when?, how?, in what volume? carried out certain interactions). Then, having imposed the appropriate decision-making algorithms on it, it becomes possible to draw conclusions about the presence of a particular threat, one or another anomaly, which may be interesting in the context of information security.

One example of a solution that uses this particular design for informational purposes is the Cisco Stealthwatch solution .
This is a solution that analyzes Flow protocols (not only NetFlow). It can be sFlow, Jflow, IPFIX, NetStream - it doesn’t matter. That is, this solution will work not only on the Cisco infrastructure, but also on the infrastructure of other vendors (including even Russian manufacturers that support the protocol with Flow), or when it is possible to transfer traffic via PAN, or Airspan to Cisco Stealthwatch and By analyzing the existing infrastructure, it is possible to identify certain anomalies, certain threats in the corporate or departmental network.
One of the key differences between this approach and perimeter protection is that the administrator does not need to install separate sensors, separate taps in the control points of the network at control points. Cisco is turning the existing network infrastructure into this kind of distributed monitoring system.

In its minimum solution, the Cisco stealthwatch consists of two components - Flow Collector, which collects data from devices supporting Flow protocols and a management console that is responsible for management, visualization, report generation, and so on. In those cases, if for some reason the device either does not support Flow, or support for enabling Flow leads to a significant processor load, you can use the so-called “Flow sensors”. This is a hardware or virtual solution that passes network traffic through itself, transmits it to NetFlow and transfers it to the Flow Collector. Thus, it is possible to connect some equipment to the Flow Sensor than connect the span port that initially does not support the Flow protocol and provide full and greater visibility of the internal network, not just its perimeter.
In addition to Flow sensors, there is also such a component as UDP Direcrot, which allows you to efficiently process data from remote sites. When there is a weak Internet channel between the remote site and headquarters, but NetFlow data must be transmitted, UDP Direcrot optimizes the transmission of such traffic.
In addition, Cisco has developed a special protocol nvzFlow, which allows you to integrate the network component with the host, and through the Network Visibility module, the module that is built into AnyConnect (this is a software security client that installs on Windows, Linux, Mac OS, iOS, Android, and so on ) Thanks to this, it became possible to translate the behavior of the node, the behavior of user applications into a protocol similar to NetFlow and to automatically correlate events that occur on nodes with events that occur at the network level, thereby improving the state of information security monitoring in a corporate or departmental network.
Another element that can send data to the Flow Collector is a proxy server, and thus you can correlate the network layer data that is obtained after analyzing NetFlow or other Flow protocols and the application layer that we receive from various proxy servers, thereby making it possible record the work of encryptors, interaction with command servers, network operation by the Tor network, and so on.
In order to collect evidence of unlawful activity, in order to store it, conduct an investigation, or transfer it to law enforcement, Cisco Stealthwatch solutions integrate with the Cisco Security Packet Analyzer component, which just stores all the information necessary for further investigation and interaction with law enforcement agencies.
The most interesting thing is that this solution works not only inside the corporate / departmental network, not only inside the data center, not only inside the industrial site (for example, in the automated process control system), but it can also work on various cloud platforms, thereby a single solution allows you to see different areas corporate or departmental network. To see anomalies in them, to see a threat and to signal accordingly and, if necessary, block these threats, relying not only on what passes through the corporate perimeter. If you notice some kind of flash drive, unprotected Wi-Fi, dropped Raspberry Pi into the corporate network and so on, the perimeter will not see this. This will see a Stealthwatch that properly monitors everything that passes through the network infrastructure.As if it were disguised as an attacker, it will always go through the switches and routers that we have located on the corporate or departmental network. He can’t bypass them in principle, and in this case Stealthwatch works, which sees all network traffic and, due to the imposition of a large number of different algorithms, can detect various anomalies or threats.
It looks as follows.

The picture shows the top nodes that are fixed for a certain time interval. One of these nodes has the address 10.201.3.149. This is a workstation. It is in the user device group. It can be seen when and what activity occurred on this node. You can see which policies are applied to this node. It can be seen what kind of user is working on this node, for example due to integration with the Active directory. Thus, we know a specific user, a specific employee of the organization, who works at a particular moment on this host and this allows for more rapid investigation of incidents.
But this is far from all that can be seen.

Suppose we see events with a very high level of suspicion, the so-called "Concern Index" and want to get more detailed information about what is hidden behind this event. We want to get all associated connections associated with this threat of information leakage.

Having done this, it was discovered that the intruder uses the SSH protocol to capture data from the internal corporate network. Please note that while only about one gigabyte of data was sent from the attacker's site, more than 160 GB of data was received. It is possible that we are talking about an attacker who is trying to capture data that he manages to "reach out" and download it to his computer. For what?

Here Stealthwatch also helps.
In this case, it can be seen that the hacker "merges" the data through an HTTPS connection somewhere to an external host. That is, perhaps this is really an attacker who, as if recalling the story of Snowden, at the beginning copied to himself all the data that he could reach, and then he tries to transfer it outside the company. In the case of Snowden, he did this on external media, taking him outside the checkpoint. In the case of this case, the attacker is trying to "merge" the data via HTTPS out to some command server, to the cloud, or somewhere else.

Another example of how Cisco Stealthwatch can help. For example, the spread of worms or malicious code within the corporate network.
Usually, in order to fix this, you need to have agent / agents on the host. There may be an antivirus. It could be a class decision and an EDR (endpoint detection and response). It may be something else that, by analyzing the activity on the node, detects the actions of malicious code. But what should we do if we cannot install agents on the nodes (for example, these agents too “eat up” processor power, or increase the load on it, or “eat up” RAM)? The computer slows down and therefore does not want to put any protective agents on it (for example, in the data center). Or this is a segment on which you can’t put any protective agents at all. It can be an industrial segment (ACS TP), it can be a segment with operating systems for which protective agents have not been developed. There can be many reasons.In other words, in the absence of host protections, engineers remain blind. They have the only data source for detecting malicious activity - this is network traffic and Stealthwatch again helps here, which in this case recorded the actions of malicious code. Node scanning events are visible, and in the details of this event, you can see that this activity is inherent in the spread of worms over the network.
This can be visualized.

Vizit in this form.
Visualization is taking place and we can understand where the starting point was, who further came under the distribution and quickly localize the problem, preventing it from developing on our network, preventing the attacker from expanding the "bridgehead" in our corporate or departmental network. And what to do in situations where attackers begin to actively use encryption, as for example the case with Equifax?

Unfortunately, according to Cisco statistics, cybercriminals over the past year have 3 times increased the number of malicious programs that they use for their activities, or rather, to hide it - encryption. It is known from theory that the “correct” encryption algorithm cannot be hacked. In order to understand what is hidden inside the encrypted traffic, you must either decrypt it knowing the key, or try to decrypt it with various tricks, or by hacking it in the forehead, or using some vulnerabilities in cryptographic protocols.
In fact, it turned out that in practice there are other methods of analyzing encrypted traffic without decrypting it. This method is simply called "machine learning." It turned out that if a very large amount of various traffic used by cybercriminals was applied to the input of a special classifier and trained to classify this kind of malicious action, even inside encrypted traffic that we cannot decrypt or decrypt, the system can detect with a very high degree of probability malicious code inside encrypted traffic.

Please note the detection accuracy is 99.99%. False positives are hundredths of a percent. That is, based on the analysis of telemetry that Cisco receives from network equipment, even without any cryptographic transformations, it can be said that malicious activity is hidden inside this or that encrypted traffic and this allows more efficient monitoring of the internal infrastructure.
Today, many companies, many service applications are moving to the TLS 1.3 protocol.which cannot be decrypted initially. That is, it is specially designed so that it is impossible to make even the legal Man In The Middle. This is done to ensure the privacy of user data. This user privacy, unfortunately, does not play into the hands, but against corporate security services, which earlier (before TLS 1.3) could still decrypt traffic on the perimeter using various SCAffolders, but now, unfortunately, do it already impossible. But the technology that is embedded in Cisco Stealthwatch called Encrypted Traffic Analytics allows you to understand what is inside without decrypting traffic . Of course, no one will understand what is written there. It's impossible.Cryptography works here. But you can understand the type of this traffic and if it is malicious, then make the appropriate decisions.

Here's what the Encrypted Traffic Analytics technology looks like.
It can be seen that information is being leaked (“Exfiltration” inscription - data leak) from a particular node, which a user by the name of Roland Torsiello is working on and the “Encrypted” mark is visible. This means traffic is encrypted. That is, despite the presence of encryption, it is still possible to record the fact of information leakage, that is, damage to the corporate resource.

I want to note that the Cisco Stealthwatch solution has a number of very important features. Important benefits.
- -, , .
- -, . Cisco , , Cisco .
- . , , . Flow .
- And the most interesting. , Cisco Stealthwatch Cisco, , Cisco , . , Cisco Vendor Agnostic ( ). «» . Cisco, Huawei, Juniper, 3com, Hewlett, , , Zelax, . , Flow, SPAN/RSPAN .

After some malicious activity was recorded, the question arises: “How to block it?”.


In this case, the Cisco ISE (Identity Services Engine) solution is very suitable , which turns a network infrastructure that has already turned into a distributed attack detection system, and Cisco ISE turns it into a distributed firewall. This is when each switch, each router, each access point is used as a decision point - “start up or not start up?”, “Start up the user?”, “Start up the device?”, “Start up the application?” To the requested resource. Cisco ISE turns the existing infrastructure (and not only the origin of Cisco, this can be done on other vendors) into a distributed firewall. If NG Firewalls (for example, Cisco FirePower) and NGIPS (for example, Cisco Firepower IPS) are usually used on the perimeter, then you can use the Cisco Stealthwatch and Cisco ISE bundles in the internal network.

Together, they allow you to monitor and control access to the internal infrastructure, significantly reducing the attack area and, most importantly, that they can be integrated with perimeter defense tools and they have a single end-to-end security policy. In the event that the Cisco solution is not on the perimeter, anyway, due to Cisco ISE, you can create a single end-to-end security policy, thereby increasing the security of corporate / departmental resources from the actions of attackers who have learned how to bypass the perimeter protection system in different ways.
Video presentation:
Audio presentation:
For all the information provided, many thanks to Cisco and
Source: https://habr.com/ru/post/461631/
All Articles