How to use PAM-modules for local authentication in Linux using GOST-2012 keys on Rutoken

Simple passwords do not protect, and complex passwords cannot be remembered. Therefore, they are so often found on a sticker under the keyboard or on the monitor. In order for passwords to remain in the heads of “forgetful” users and the reliability of protection not to be lost, there is two-factor authentication (2FA).
Due to the combination of factors of ownership of the device and knowledge of its PIN code, the PIN code itself can be simpler and easier to remember. Deficiencies in the length or randomness of the PIN code are compensated for by the requirement of physical ownership and restrictions on the search for the PIN code.
')
In addition, in state institutions it happens that they want everything to work according to GOST. This option 2FA to enter Linux and will be discussed. I'll start from afar.
PAM modules
Pluggable Authentication Modules (PAMs) are modules with a standard API and implementations of various authentication mechanisms in applications.
All utilities and applications that can work with PAM pick them up and can use them to authenticate the user.
In practice, this works something like this: the login command turns to PAM, which performs all the necessary checks using the modules specified in the configuration file and returns the result back to the login command.
librtpam
The module developed by the Active company adds two-factor authentication of users by smart cards or USB tokens using asymmetric keys according to the latest standards of domestic cryptography.
Consider the principle of its work:
- the token stores the user's certificate and its private key;
- The certificate is saved in the user's home directory as trusted.
The authentication process is as follows:
- Rutoken searches for the user's personal certificate.
- The token PIN is requested.
- The random data is signed on a private key directly in the Rutoken chip.
- The received signature is verified using the public key from the user certificate.
- The module returns the result of the signature verification to the calling application.
You can authenticate using the keys GOST R 34.10-2012 (length 256 or 512 bits) or outdated GOST R 34.10-2001.
There is no need to worry about the security of keys - they are generated directly in Rutoken and never leave his memory during cryptographic operations.

Rutoken EDS 2.0 is certified by the FSB and FSTEC according to NDV 4, therefore it can be used in information systems that process confidential information.
Practical use
Almost any modern Linux is suitable, for example, we will use xUbuntu 18.10.
1) Install the necessary packages
sudo apt-get install libccid pcscd openscIf you want to add a desktop lock with a screensaver, additionally install the
libpam-pkcs11 package.2) Add a PAM module with support for GOST
Download the library from https://download.rutoken.ru/Rutoken/PAM/
Copy the contents of the PAM folder librtpam.so.1.0.0 to the system folder
/usr/lib/ or /usr/lib/x86_64-linux-gnu/ or /usr/lib643) Install the package with librtpkcs11ecp.so
Download and install the DEB or RPM package from the link: https://www.rutoken.ru/support/download/pkcs/
4) We verify that Rutoken EDS 2.0 works in the system
In the terminal, execute
$ pkcs11-tool --module /usr/lib/librtpkcs11ecp.so -TIf you see the
Rutoken ECP <no label> , then everything is fine.5) Read the certificate
Check that the device has a certificate
$ pkcs11-tool --module /usr/lib/librtpkcs11ecp.so -OIf after the line:
Using slot 0 with a present token (0x0)- If information about keys and certificates is displayed , then you need to read the certificate and save it to disk. To do this, run the following command, where instead of {id} you need to substitute the ID certificate that you saw in the output of the previous command:
$ pkcs11-tool --module /usr/lib/librtpkcs11ecp.so -r -y cert --id {id} --output-file cert.crt
If the cert.crt file is created, go to step 6). - there is nothing , then the device is empty. Contact your administrator or create the keys and certificate yourself by following the next step.
5.1) Create a test certificate
Attention! The described methods for creating keys and certificates are suitable for testing and are not intended for use in combat mode. To do this, you need to use keys and certificates issued by a trusted certification authority of your organization or an accredited certification authority.
The PAM module is designed to protect local computers and involves work in small organizations. Since there are few users, the Administrator can manually monitor the revocation of certificates and manually block accounts, as well as the validity period of certificates. The PAM module is not yet able to verify certificates by CRL and build trust chains.
Easy way (via browser)
To obtain a test certificate, use the Rootoken Registration Center web service . The process will take no more than 5 minutes.
Geek path (via console and possibly compiler)
Check OpenSC Version
$ opensc-tool --versionIf the version is less than 0.20, then upgrade or collect the pkcs11-tool branch with GOST 2012 support from our GitHub (at the time of this article release 0.20 has not yet been released) or from the master branch of the main OpenSC project no later than the 8cf1e6f commit
We generate a key pair with parameters:
--key-type: GOSTR3410-2012-512: (-2012 512 c ), GOSTR3410-2012-256:A (-2012 256 A)--id: object identifier (CKA_ID) as double-digit character numbers in hex from the ASCII table. Use only ASCII codes for printed characters, as id will need to pass OpenSSL as a string. For example, ASCII codes “3132” correspond to the string “12”. For convenience, you can use the online service for converting strings to ASCII codes .$ ./pkcs11-tool --module /usr/lib/librtpkcs11ecp.so --keypairgen --key-type GOSTR3410-2012-512:A -l --id 3132Next we will create a certificate. Two ways will be described below: the first through the CA (we will use test CAs), the second - self-signed. To do this, you must first install and configure OpenSSL version 1.1 or later to work with Rutoken through a special rtengine module using the Install and Configure OpenSSL manual.
For example: for '-
-id 3132 ' in OpenSSL you need to specify " pkcs11:id=12 ".You can use the services of a test CA, of which there are many, for example, here , here and here , for this we will create a certificate request
Another option is to succumb to laziness and create a self-signed
$ openssl req -utf8 -new -keyform engine -key "pkcs11:id=12" -engine rtengine -out req.csrDownload the certificate to the device
$ openssl req -utf8 -x509 -keyform engine -key "pkcs11:id=12" -engine rtengine -out cert.cer6) Register the certificate in the system
Make sure your certificate looks like a base64 file:

If your certificate looks like this:

then you need to convert the certificate from the DER format to the PEM format (base64)
$ openssl x509 -in cert.crt -out cert.pem -inform DER -outform PEMAgain we check that now everything is in order.
Add a certificate to the list of trusted certificates
$ mkdir ~/.eid
$ chmod 0755 ~/.eid
$ cat cert.pem >> ~/.eid/authorized_certificates
$ chmod 0644 ~/.eid/authorized_certificatesThe last line protects the list of trusted certificates from accidental or intentional changes by other users. This eliminates the situation when someone adds their certificate here and can log in on your behalf.
7) Configure authentication
The configuration of our PAM module is completely standard and done just like the settings of other modules. We create in the file
/usr/share/pam-configs/rutoken-gost-pam containing the full name of the module, whether it is enabled by default, module priority and authentication parameters.In the authentication parameters there are requirements for the success of the operation:
- required: such modules should return a positive response. If the result of the module call contains a negative answer, this will lead to an authentication error. The request will be reset, but the rest of the modules will be called.
- requisite (required): similar to required, but immediately leads to authentication failure and ignores the rest of the modules.
- sufficient: if in front of such a module none of the required or sufficient modules returned a negative result, the module will return a positive answer. The remaining modules will be ignored.
- optional (optional): if there are no required modules in the stack and none of the sufficient modules returned a positive result, then at least one of the optional modules should return a positive answer.
The full contents of the file
/usr/share/pam-configs/rutoken-gost-pam :Name: Rutoken PAM GOST
Default: yes
Priority: 800
Auth-Type: Primary
Auth: sufficient /usr/lib/librtpam.so.1.0.0 /usr/lib/librtpkcs11ecp.so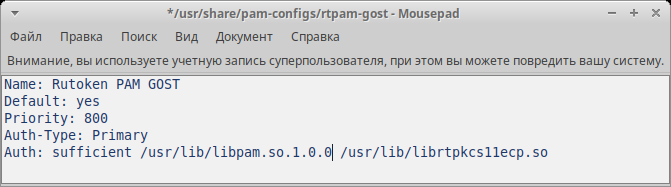
save the file, then execute
$ sudo pam-auth-updatein the window that appears, put an asterisk near Rutoken PAM GOST and click OK

8) Check the setting
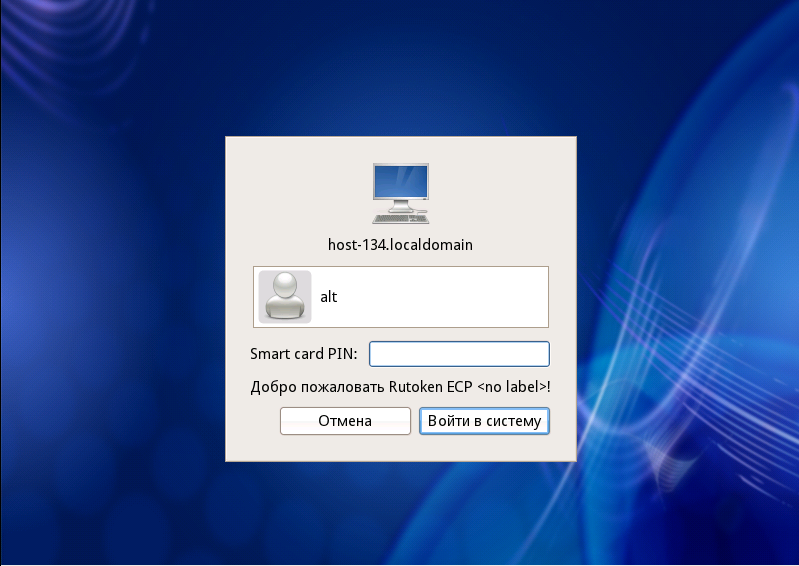
To understand that everything is configured, but not to lose the ability to log in, enter the command
$ sudo loginEnter your username. Everything is configured correctly if the system requires a device PIN.

9) Configure the computer lock when extracting the token
The
libpam-pkcs11 package includes the pkcs11_eventmgr, utility pkcs11_eventmgr, which allows you to perform various actions when PKCS # 11 events occur.To configure
pkcs11_eventmgr use the configuration file: /etc/pam_pkcs11/pkcs11_eventmgr.confFor various Linux distributions, the command that causes the account to be locked when removing smart cards or tokens will be different. See
event card_remove .An example configuration file is presented below:
pkcs11_eventmgr { # daemon = true; # debug = false; # polling_time = 1; # - # - 0 expire_time = 0; # pkcs11 pkcs11_module = usr/lib/librtpkcs11ecp.so; # # : event card_insert { # ( ) on_error = ignore ; action = "/bin/false"; } # event card_remove { on_error = ignore; # # GNOME action = "dbus-send --type=method_call --dest=org.gnome.ScreenSaver /org/gnome/ScreenSaver org.gnome.ScreenSaver.Lock"; # XFCE # action = "xflock4"; # Astra Linux (FLY) # action = "fly-wmfunc FLYWM_LOCK"; } # event expire_time { # ( ) on_error = ignore; action = "/bin/false"; } } After that, add the
pkcs11_eventmgr application to startup. To do this, edit the .bash_profile file:$ nano /home/<_>/.bash_profileAdd the line pkcs11_eventmgr to the end of the file and reboot.
The described steps to configure the operating system can be used as instructions in any modern Linux distribution, including domestic ones.
Conclusion
Linux PCs are becoming more and more popular in Russian government agencies, and setting up reliable two-factor authentication in this OS is not always easy. We will be happy with this guide to help solve the “password problem” and reliably protect access to your PC without spending a lot of time on it.
Source: https://habr.com/ru/post/461199/
All Articles