How are pentesters cooked? Entrance Testing for Digital Security Interns
The Summer of Hack 2019 at Digital Security is already in full swing, which means it's time to tell how we recruited people.

Under the cut, voluminous and interesting material about how we select young specialists for our internship “Summer of Hack 2019”, and specifically to the Department of Security Audit.
')
Consider what, in our opinion, a pentester should know in order to successfully do its job.
We will analyze a number of difficult tasks that we tortured the guys, including on behalf of one of them.
Perhaps the most interesting part of the selection for an internship in the security audit department was our profile. Every year we gather as a whole department and discuss what skills, in our opinion, are in demand for a modern specialist in the field of practical safety, recall the most interesting tasks that had to be solved this year, and write out areas of knowledge without which it is difficult to imagine a successful auditor. When all the jokes are joked and the stories are told, the bottom line remains a set of ideas.
This year, we were guided by the following requirements:
After questions were developed. Partially, we borrowed them from the questions we asked at the interviews, but more than half were specially prepared for this questionnaire. Our experts spent their personal time preparing traffic dumps, arguing how to better formulate the question, and which vulnerabilities were “too specific, why torment trainees”. For such zeal, we cannot help but take off our hat (white, of course).
The analysis of each question consists of two parts. The first part is the answer of one of our trainees - Danila Korgik_0 Leontyeva (he is the author of the publication), and the second is the comments of specialists who were piling over the questionnaire.
Hello, Habr!
First, a little lyrical digression.
More specifically, “How did I find out about Summ3r 0f h4ck”.
I heard about the announcement of the internship from a speech by Denis Rybin and Ilya Bulatov at the RuCTF2019 conference.
Literally after 4 days, a post was posted on habr about the opening of an internship set.
And in the evening of the same day I opened the task, in the security audit department, and immersed myself in work. Today I will share with the reader what difficulties I had to face and which solution option I could offer.
Examine the code. Describe what flaws you see and how you would fix them.

When researching a web application, you found that the application uses a JWT token as authorization.
What security concerns do you see, what kind of checks would you do?
JWT Token:
In the web application, the user password is changed using the following request (see Option 1). What potential security threats do you see? What checks would you carry out? Will the situation change in the case of the following behavior (see Option 2)? Explain your answer.
Imagine that you got into the internal network of the company and intercepted the traffic whose dump is attached below. Describe what attacks you would try to conduct and with what tools?
Dump: yadi.sk/d/qkLcfwSCzdxcwg
Here is the nginx web server configuration. Describe in detail what security problems you see in it?
Configuration: pastebin.com/nYp7uVbB
When can a Linux user read other user's home directories?
During the work in the internal network of the company, you were able to receive the following traffic. Analyze it, try to get useful data and files from the traffic, and also describe what further attacks you could conduct.
Traffic dump: yadi.sk/d/e3gNme4MBo6tFQ
You are on network A (10.0.10.0/24), you were able to access via SSH to the Linux host (10.0.20.5) on network B (10.0.20.0/24). However, you found that you do not have full access to network B. Think of and describe in detail the method by which you could scan network B without installing any additional scripts / utilities / programs on the Linux host.
You are exploring a mobile application for Android. You have found that the application sends requests over the secure HTTPS protocol.
1) Describe how you would try to bypass the protection and get unprotected HTTP traffic.
2) What will change if SSL-pinning is enabled in the application, how can I try to circumvent protection in this case?
Tell us about the most interesting attack technique or published vulnerability that you have learned about recently.
The only task in the “free format". The attack that I liked lately is dns-rebinding.
That’s all for me. Thanks for attention!
Closing remarks from Digital Security
Now let us slightly open the veil, how did the process of evaluating the guys go.
Each answer was independently evaluated by at least 3 specialists (one must somehow have fun in their free time from audits). The range of acceptable ratings was from 0 to 5 points with the ability to set at least 2.5, or even 3.1337 if you wish.
As a result, the estimates are averaged and summed up. Thus, the maximum could score 50 points. Our experts tried to be as loyal as possible and understand what the next candidate had in mind about “ hacking through the form code ” or something else like that)
We set the passing score after the application deadline is closed. This year he made 29 points, and the best result was 43.5. As a result, approximately 24% of all applicants went for an internship.
The statistics are as follows:
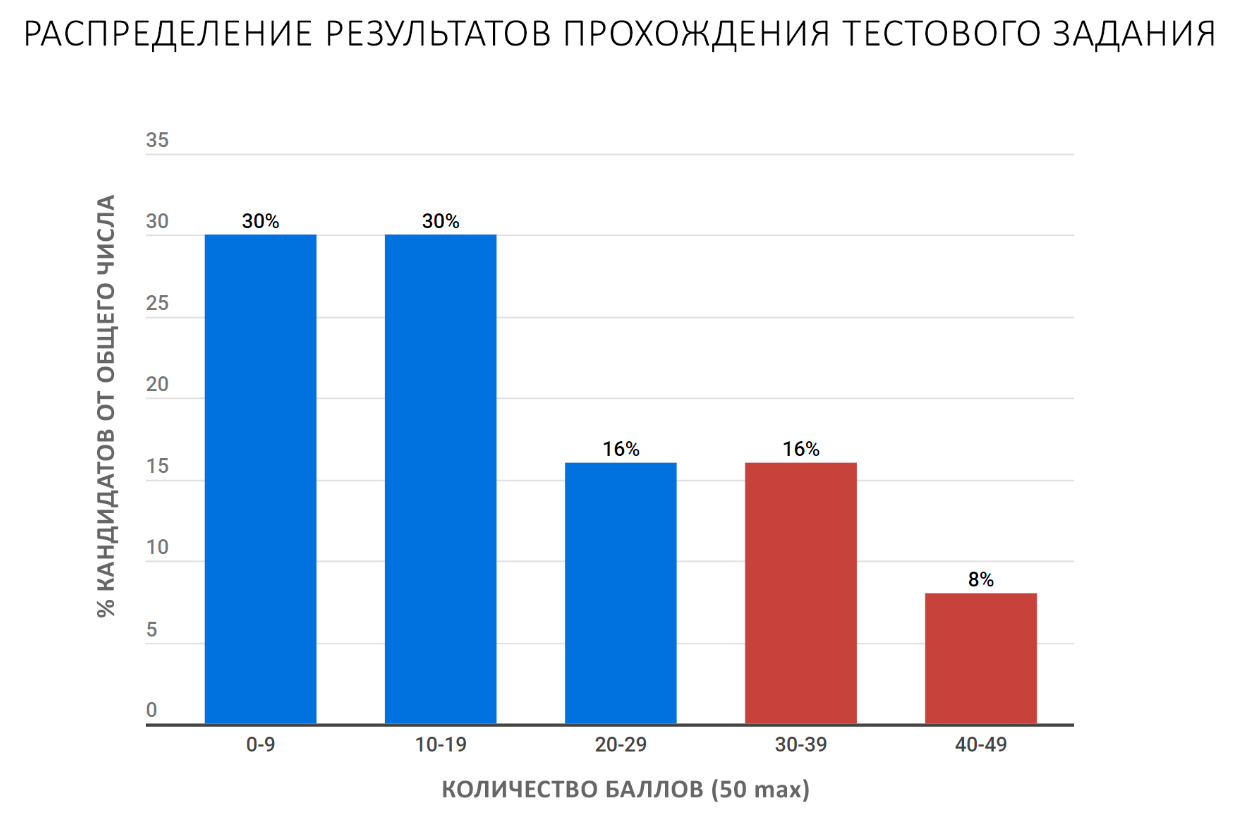
However, for these lucky ones it didn’t end so simply, because then they had a face-to-face interview, where we asked the guys what they liked in the questionnaire, what questions were the most difficult to answer and how long it took them to complete . Thus, we were convinced that no one helped the guys with the questionnaire, and they filled it out themselves. At the same time, we received useful feedback for the next years.
It may seem that such a system is unreasonably complex, but, unfortunately, we cannot afford to accept everyone and want to share our knowledge with the most motivated of the guys.
By the way, which is noteworthy, every year we see a surge in applications exactly at the end of the term:
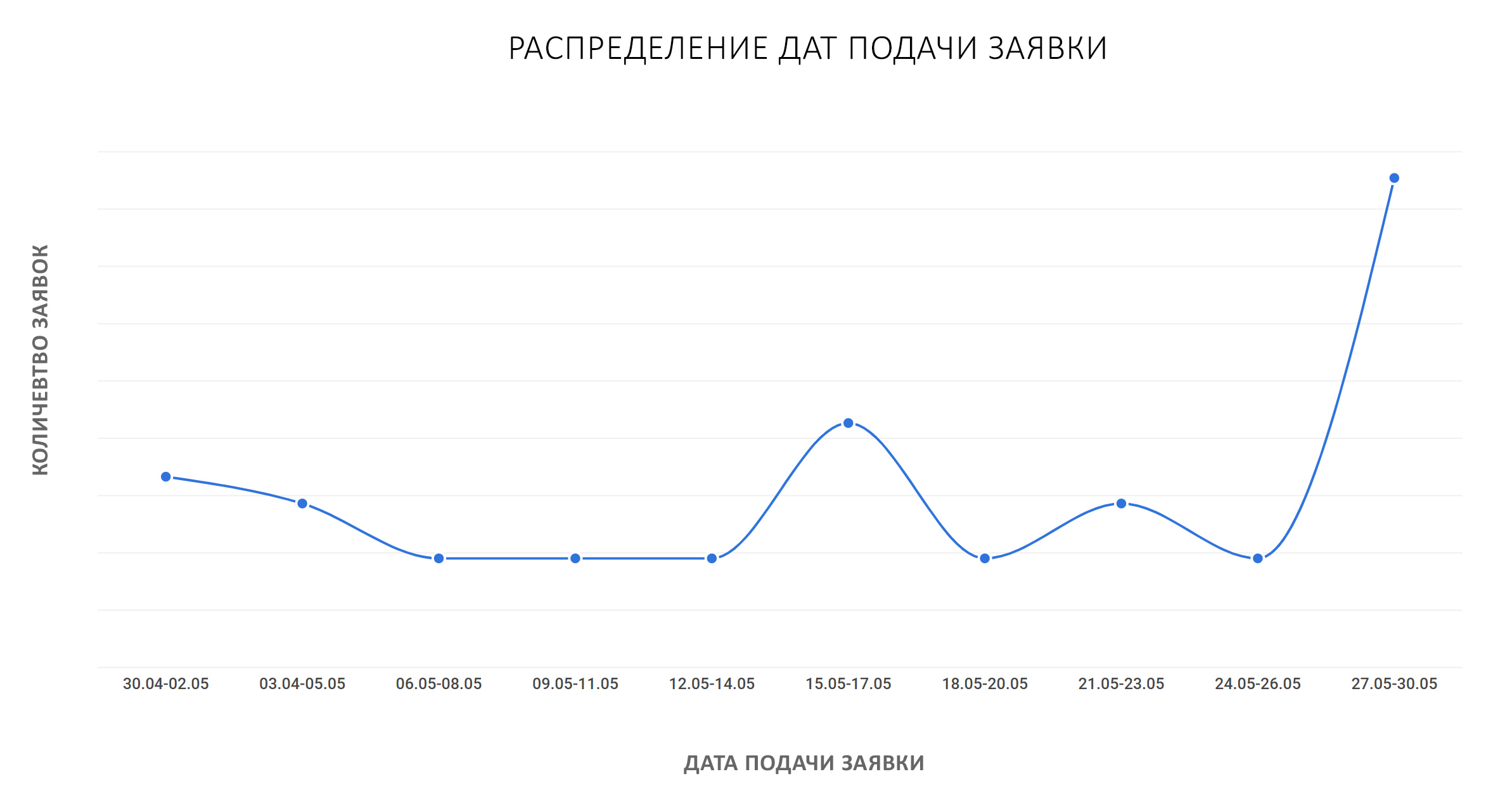
For our part, we provide a wide variety of lectures (almost every day!), Access to our small but proud internal laboratory with a bunch of interesting hacking tasks compiled by experienced specialists where you can hone your practical skills and train your “hacker instinct".
The main occupation of the internship is a joint study with an experienced curator of some interesting and significant aspect of security, whether it be vulnerabilities in new technology or a tool that allows you to solve existing difficulties in conducting security analysis. However, we will talk more about this in our materials dedicated to the end of Summer of Hack 2019.
As a conclusion, I want to say that for the second year we have been selecting using such a system and are increasingly convinced of its effectiveness. With the help of it, we really manage to select strong trainees and get information about the average level of knowledge among students and graduates.

Under the cut, voluminous and interesting material about how we select young specialists for our internship “Summer of Hack 2019”, and specifically to the Department of Security Audit.
')
Consider what, in our opinion, a pentester should know in order to successfully do its job.
We will analyze a number of difficult tasks that we tortured the guys, including on behalf of one of them.
Perhaps the most interesting part of the selection for an internship in the security audit department was our profile. Every year we gather as a whole department and discuss what skills, in our opinion, are in demand for a modern specialist in the field of practical safety, recall the most interesting tasks that had to be solved this year, and write out areas of knowledge without which it is difficult to imagine a successful auditor. When all the jokes are joked and the stories are told, the bottom line remains a set of ideas.
This year, we were guided by the following requirements:
- Basic knowledge of the device web-applications and attacks on them;
- Basic knowledge of browser-based protection and access control mechanisms (yes, the same SOP and CORS, where without them);
- Basic code reading skills and the ability to see logic behind it;
- Understanding the operation of computer networks and routing in them;
- Experience with Linux-like systems;
- The ability not to be afraid of unfamiliar technology. The ability to google and organize the information received;
- And a pinch of Android (though not necessary, but this is our little whim).
After questions were developed. Partially, we borrowed them from the questions we asked at the interviews, but more than half were specially prepared for this questionnaire. Our experts spent their personal time preparing traffic dumps, arguing how to better formulate the question, and which vulnerabilities were “too specific, why torment trainees”. For such zeal, we cannot help but take off our hat (white, of course).
The analysis of each question consists of two parts. The first part is the answer of one of our trainees - Danila Korgik_0 Leontyeva (he is the author of the publication), and the second is the comments of specialists who were piling over the questionnaire.
Hello, Habr!
First, a little lyrical digression.
More specifically, “How did I find out about Summ3r 0f h4ck”.
I heard about the announcement of the internship from a speech by Denis Rybin and Ilya Bulatov at the RuCTF2019 conference.
Literally after 4 days, a post was posted on habr about the opening of an internship set.
And in the evening of the same day I opened the task, in the security audit department, and immersed myself in work. Today I will share with the reader what difficulties I had to face and which solution option I could offer.
No. 1. Php source code
Examine the code. Describe what flaws you see and how you would fix them.

Job parsing
4th line - use the md5 hash.
Problem - md5 can be brutalized in a reasonable amount of time using hashcat.
How to fix?
Using more "resource-intensive" hashing algorithms.
In this case, you must completely refuse the user cookies and tie all the logic to phpsession.
5th line - PostgreSQL-injections.
How to fix?
Using prepared statement.
Implementation of prepared statement to verify login
11 line - a number of unsuccessful decisions.
How to fix?
By default, in php, the session lifetime is only 24 minutes, let's implement this.
Set the secure flag, httpOnly.
In this case, you should refuse the strange user cookie and tie all the logic to phpsession.
18 line - XSS (English Cross-Site Scripting - "intersite scripting").
How to fix? Convert all possible characters to the corresponding HTML entities.
We will explicitly indicate the encoding in order to avoid its substitution for UTF-7.
Line 20 - defects of the authentication system and session storage.
Problem - if you set the user id encoded in base64 in the cookie user, you can log in to his account!
How to fix? When authorizing the user, we record the session in the database and when installing the session, we check its presence in the database.
Problem - md5 can be brutalized in a reasonable amount of time using hashcat.
How to fix?
Using more "resource-intensive" hashing algorithms.
In this case, you must completely refuse the user cookies and tie all the logic to phpsession.
5th line - PostgreSQL-injections.
How to fix?
Using prepared statement.
Implementation of prepared statement to verify login
$query = "SELECT username FROM login WHERE username=?"; $stmt = $conn->prepare($query); $stmt->execute(array($username)); $username = $stmt->fetchColumn(); if($username == FALSE) { die(" !"); } 11 line - a number of unsuccessful decisions.
- Session life too long. A whole year is a lot. If the cookie is hijacked successfully, long access to the user account by the attacker is possible.
- Missing httpOnly flag. If set to TRUE, cookies will only be accessible through the HTTP protocol. That is, cookies in this case will not be available to scripting languages like JavaScript.
- No cookie hashing.
- Lack of setting the secure flag. The secure flag indicates that the cookie value should be transmitted from the client over a secure HTTPS connection. If set to TRUE, the cookie from the client will be sent to the server only if a secure connection is established.
How to fix?
By default, in php, the session lifetime is only 24 minutes, let's implement this.
Set the secure flag, httpOnly.
In this case, you should refuse the strange user cookie and tie all the logic to phpsession.
18 line - XSS (English Cross-Site Scripting - "intersite scripting").
How to fix? Convert all possible characters to the corresponding HTML entities.
$query = htmlentities($query, ENT_QUOTES, "UTF-8"); We will explicitly indicate the encoding in order to avoid its substitution for UTF-7.
header("Content-Type: text/html; charset=utf-8"); Line 20 - defects of the authentication system and session storage.
Problem - if you set the user id encoded in base64 in the cookie user, you can log in to his account!
How to fix? When authorizing the user, we record the session in the database and when installing the session, we check its presence in the database.
$query = "SELECT sessions FROM login WHERE sessions=?"; $stmt = $conn->prepare($query); $stmt->execute(array($_COOKIE["user"])); $session = $stmt->fetchColumn(); if($session == TRUE) { do_login($_COOKIE["user"]); } Expert Commentary D:
The first question with which the questionnaire met future interns concerned the main and widely known web vulnerabilities. The only difficulty here is the need to see them in the source code in PHP. However, no one set the task of “hiding bugs”.
Here is a list of vulnerabilities that can be detected in this listing in order of frequency of their detection:
Password hashing using the MD5 algorithm was noticed even by candidates far from the web. However, there were also interesting nuances, for example, many candidates used very incorrect terms, trying to describe the problems in their own words. “Algorithm vulnerabilities”, “one-way functions”, “the existence of collisions” and other strange turns went into battle, upon closer examination, they turned out to be nothing more than a set of big words that did not reveal the essence. Of course, here we went to a meeting and did not find fault with those people who are just preparing to embark on the path to learning the wisdom of information security. To get a “set-off”, mention of the threat would be enough, that in case of compromising the database, the md5 hashes can be sorted out by an attacker in an acceptable time and passwords (or equivalent strings) can be obtained in clear text. And, of course, many mentioned the lack of salt and brute force based on the use of rainbow tables. We also perceived such comments positively, especially if the respondent explained why this is a threat.
Potential SQL injection. It’s hard to add something; when forming a call to the database, user input of login and password are directly concatenated with the request. If it is unlikely that you can manipulate the password value at this stage (a hash is taken from it), then introducing an injection into username will not be difficult for a potential attacker.
Output of unnecessary debug information leading to an XSS attack. By carefully reading the listing, one could pay attention to the echo call, which displays the generated request to the database in HTML comments on the page. Of course, such a conclusion of additional information to the page is completely optional and, most likely, simply forgotten by the developer after conducting the tests. Such additional information is very beneficial for the attacker and allows a much better understanding of how the application works. However, unfortunately, this is only half the trouble. The fact is that an attacker can manipulate the contents of the query variable, and its contents are not filtered or escaped before being displayed to the user - there is a potential XSS attack. However, its exploitation can turn out to be that still a headache due to the poorly located strtoupper function. The vector injected by the attacker will be uppercase, and if this is not a problem for HTML tags, then Javascript is very offended by such an appeal. This can be easily verified using the browser console.
Well, at least, apparently, the attacker will have to resort to the so-called “scriptless attacks” or sophisticated techniques for bypassing filtering (in this case, JSFUCK would do), so the fact of a security risk does not cancel this.
An error in the logic of the session management mechanism was the most interesting part of the task. Its discovery required not only to read the source line by line, but also to understand the logic of the whole listing. One could feel something was wrong by noticing the setting of a cookie containing the base64-encoded user id in the remember-me block. Further analysis of the logic of this mechanism leads us to the thought: “It turns out that an attacker who knows or goes through id can log into any account without entering a login and password ?!”. Yes, indeed, an attacker can, on his side, independently generate a cookie user and assign it any id value encoded by base64. Sending a request with such a cookie without username and password would trigger the do_login function and log in to someone else's account.
The mention of these 4 vulnerabilities in the candidates' response directly influenced their scores.
However, much depended on the quality of the response. Mentioning ways to rectify the situation, comments on additional factors affecting the feasibility of a particular attack, the use of the right terms and the ability to structure your thoughts, comments on additional weaknesses or potential threats - all this warmed our hearts and led to an increase in the final rating.
No. 2. Jwt
When researching a web application, you found that the application uses a JWT token as authorization.
What security concerns do you see, what kind of checks would you do?
JWT Token:
eyJhbGciOiJOb25lIiwidHlwIjoiSldUIn0.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6InNla2EiL CJpYXQiOjE1MTYyMzkwMjIsInJvbGUiOiJub2JvZHkiLCJpc0FkbWluIjoiRmFsc2UiLCJwYX Nzd29yZCI6IjFkMDBjYUgifQ.F7Y1mCAmg5-QFok-rkpLdwe8prCyiKsCyJ-3Z5f7luI Job parsing
Dan JSON Web Tokens (JWT).
Its structure -> [base64url (HEADER)]. [Base64url (PAYLOAD)]. [Base64url (SIGNATURE)]
[base64url (HEADER)] = eyJhbGciOiJOb25lIiwidHlwIjoiSldUIn0
base64url decode -> {"alg": "None", "typ": "JWT"}
We can immediately note the fact that the signature algorithm (“alg”: “None”) of the signature is not used. Some JWT libraries do not support the “none” algorithm, that is, the signature algorithm. When the alg header is “none”, the server side will not perform signature verification.
That is, you can write any payload in base64url, and its signature will not be verified.
Which allows us to create a user with admin rights.
Also, the fact that the payload part does not use such headers as aud (defines the recipients for which the JWT token is intended) and exp (token lifetime) does not make things easier for us.
Estimated Payload
eyJhbGciOiJOb25lIiwidHlwIjoiSldUIn0.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6ImhhY2siLCJpYXQiOjE1MTYyMzkwMjIsInJvbGUiOiJub2JvZHkiLCJpc0FkbWluIjoiVHJ1ZSIsInBhc3N3b3JkIjoiaGFjayJ9
base64url decode payload -> {"sub": "1234567890", "name": "hack", "iat": 1516239022, "role": "nobody", "isAdmin": "True", "password": "hack »}
Its structure -> [base64url (HEADER)]. [Base64url (PAYLOAD)]. [Base64url (SIGNATURE)]
[base64url (HEADER)] = eyJhbGciOiJOb25lIiwidHlwIjoiSldUIn0
base64url decode -> {"alg": "None", "typ": "JWT"}
We can immediately note the fact that the signature algorithm (“alg”: “None”) of the signature is not used. Some JWT libraries do not support the “none” algorithm, that is, the signature algorithm. When the alg header is “none”, the server side will not perform signature verification.
That is, you can write any payload in base64url, and its signature will not be verified.
Which allows us to create a user with admin rights.
Also, the fact that the payload part does not use such headers as aud (defines the recipients for which the JWT token is intended) and exp (token lifetime) does not make things easier for us.
Estimated Payload
eyJhbGciOiJOb25lIiwidHlwIjoiSldUIn0.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6ImhhY2siLCJpYXQiOjE1MTYyMzkwMjIsInJvbGUiOiJub2JvZHkiLCJpc0FkbWluIjoiVHJ1ZSIsInBhc3N3b3JkIjoiaGFjayJ9
base64url decode payload -> {"sub": "1234567890", "name": "hack", "iat": 1516239022, "role": "nobody", "isAdmin": "True", "password": "hack »}
Expert Commentary D:
In the work of the auditor often have to deal with new technologies, and the ability to understand them is very important. Including this question in the questionnaire, we assumed that most of the candidates hardly heard about the technology of JWT tokens except for the name. Therefore, this question, first of all, was aimed at the ability to search and analyze information from public sources. As a result, a person who missed the issuance of Google at the request of “JWT” and “jwt vulnerability” could come to the following conclusions:
1. This token does not have a signature algorithm, so an attacker is able to modify any fields inside the token, which is not assumed by the concept of JWT tokens.
2. Fields inside the token contain the user's password in clear form; storing such information in the token is, at a minimum, a bad practice. In most cases, you can refuse such a decision and thereby increase your level of security.
3. Remembering the lack of a signature and our ability to modify the fields inside the token, it is logical to assume that changing the value of isAdmin can increase our privileges to administrator privileges.
4. Another interesting idea that few people mentioned in their answer concerns the very fact of the ability to transfer user input in the fields of a JWT token. In a normal situation, an attacker can’t influence the data in the token in any way, which means that developers can often neglect the introduction of additional checks in the code of the handlers. This begs the simple idea: but let's try to conduct classic attacks not through GET / POST parameters, but through token fields. This can give an unexpectedly good result. Such a creative approach with the correct justification of our actions was highly appreciated by us in assessing both this and other issues.
Many candidates in their answers arranged a brief retelling of how the JWT token is structured, and where it is used, it was interesting for us to read, and yet, first of all, we evaluated the aspects of the answer regarding security.
Number 3. CORS / CSRF / IDOR / ???
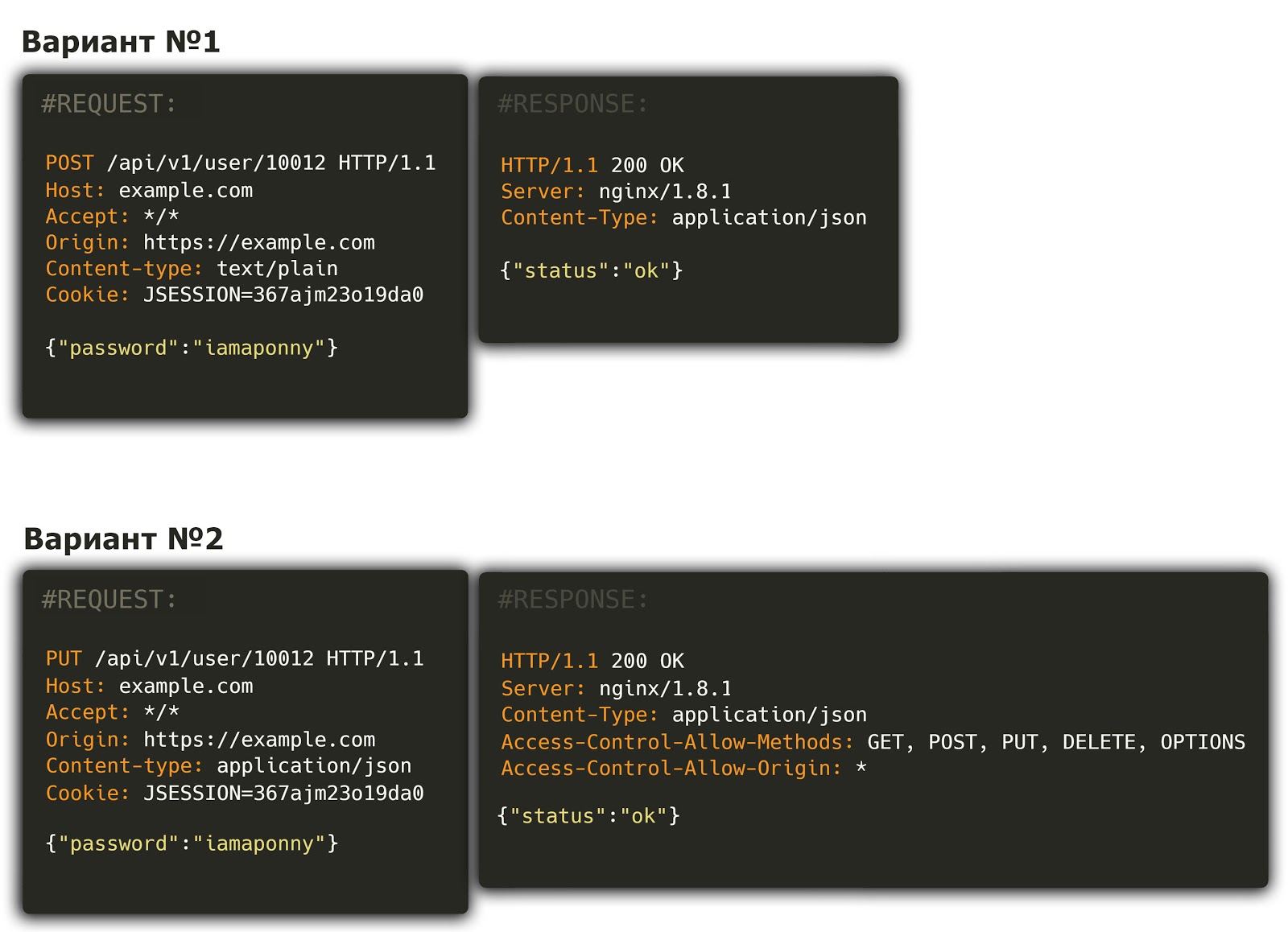
In the web application, the user password is changed using the following request (see Option 1). What potential security threats do you see? What checks would you carry out? Will the situation change in the case of the following behavior (see Option 2)? Explain your answer.

Job parsing
Option 1.
“What potential security threats do you see?”
1) Lack of access control.
If the user-a number to which the password change request is being made is not checked, then the password can be changed for any registered user in the system.
How to fix? - Matching JSESSION from the database and the requested id-shnik.
2) The ability to conduct CSRF attacks
We lure an authorized user to a host controlled by us and, after making a request, to example.com on behalf of the victim, to change the password.
How to fix? - Adding CSRF token.
Option 2
“What potential security threats do you see?”
A flaw in the CORS policy.
It is recommended that you whitelist the Access-Control-Allow-Origin header.
How to fix? -
1) Modifying the .htaccess file
2) PHP
“Will the situation change with the following behavior?”
Yes. Since the PUT request is used in the second case, which is important, since using the PUT request makes the CORS request “difficult”, which in turn completely deprives us of the opportunity to conduct a CSRF attack + the absence of such a header as Access-Control-Allow-Credentials: true deprives us the ability to send in place with other http headers and the user's cookie.
“What potential security threats do you see?”
1) Lack of access control.
If the user-a number to which the password change request is being made is not checked, then the password can be changed for any registered user in the system.
How to fix? - Matching JSESSION from the database and the requested id-shnik.
2) The ability to conduct CSRF attacks
We lure an authorized user to a host controlled by us and, after making a request, to example.com on behalf of the victim, to change the password.
How to fix? - Adding CSRF token.
Option 2
“What potential security threats do you see?”
A flaw in the CORS policy.
It is recommended that you whitelist the Access-Control-Allow-Origin header.
How to fix? -
1) Modifying the .htaccess file
<ifmodule mod_headers.c> Header always set Access-Control-Allow-Origin: "https://whitelist.domain.ru" Header always set Access-Control-Allow-Methods "PUT" </ifmodule> 2) PHP
<?php header('Access-Control-Allow-Origin: “https://whitelist.domain.ru”); header('Access-Control-Allow-Methods: PUT'); ?> “Will the situation change with the following behavior?”
Yes. Since the PUT request is used in the second case, which is important, since using the PUT request makes the CORS request “difficult”, which in turn completely deprives us of the opportunity to conduct a CSRF attack + the absence of such a header as Access-Control-Allow-Credentials: true deprives us the ability to send in place with other http headers and the user's cookie.
Expert I comment:
Let us consider, in order, what are the main problems that are visible on the given queries:
1) Indeed, since the user’s numerical identifier “10012” is observed in the request, the first step is to check whether it is possible to change the password for another user? Can it be enough to specify someone else's id ?
Vulnerabilities of the IDOR class are fairly easy to exploit and often have high criticality.
2) The request to change the password occurs by the POST method, the CSRF token is not observed, and the content type is “text / plain”. There is the possibility of faking such a request.
Consequently, in order to change the victim’s password, it is enough for the attacker to convince them to just visit the “malicious” link.
3) In the response headers, the server reveals the version of the software used . This can be called a vulnerability at a stretch, but it’s better to hide such banners - attackers can easily find the well-known 1-day exploits on them, plus the value of the software used greatly simplifies the planning of further attacks.
4) We would be very pleased to see the sentence “What will happen if we change the data format from JSON to XML ?”
The fact is that modern frameworks are smart, omnivorous and can process data in different formats. And when parsing XML, a dangerous XXE vulnerability is often allowed. With its help, the intruder can "go" to the internal network, can read configuration files from the server, and occasionally execute RCE.
5) I also wanted to see a remark like “Why is the knowledge of the old not checked when changing the password?”
As for “Option # 2”, there is a “trap” in it - CORS headers are used here, and the Content-Type of the request is already set to “application / json”.
The mistake that the vast majority of candidates made is the answer of the form "-That's the asterisk in Allow-Origin, which means you can send requests from any site!"
No you can not. Firstly, the Allow-Credentials: True header is missing, which means that the browser should execute the request “with cookies”, so that the request would be anonymous, without a session. And secondly, even if such a header were present, the browser would still forbid sending cookies - just because of the "asterisk". Their combination is forbidden, and the browser is ignored.
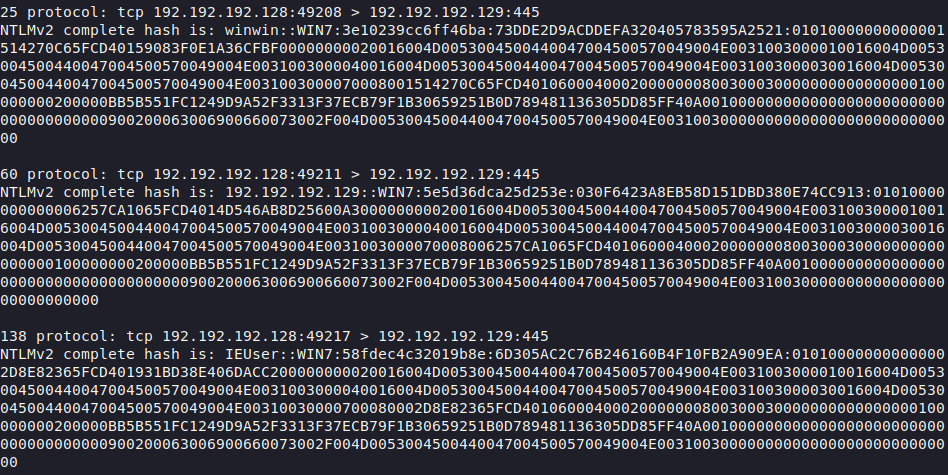
Number 4. Network dump
Imagine that you got into the internal network of the company and intercepted the traffic whose dump is attached below. Describe what attacks you would try to conduct and with what tools?
Dump: yadi.sk/d/qkLcfwSCzdxcwg
Job parsing
1) LLMNR Spoofing <
An attacker on the local subnet can listen to and respond to broadcast messages, claiming that the requested host name is his own IP address.
This causes the requesting client computer to connect to the attacker computer and, depending on the protocol, may try to authenticate.
The utilities used are Intercepter-NG, a project on githab VindicateTool.
2) Abuse of the HSRP protocol.
Problematic - when the “preempt” parameter is set to 1, the attacker has the opportunity to “squeeze out” other routers, due to the higher priority. After sending HSRP to the multicast, the controlled router becomes the main router (Active Router) in the network, and all traffic will pass through it. In fact, we came to the implementation of mitm attacks.
For this attack vector, we need to know the group and password.
From the traffic dump given to us, we recognize the group (it is - 3) and the password. The password in our case is default - cisco.
Utilities used are yersinia, scapy.
An attacker on the local subnet can listen to and respond to broadcast messages, claiming that the requested host name is his own IP address.
This causes the requesting client computer to connect to the attacker computer and, depending on the protocol, may try to authenticate.
The utilities used are Intercepter-NG, a project on githab VindicateTool.
2) Abuse of the HSRP protocol.
Problematic - when the “preempt” parameter is set to 1, the attacker has the opportunity to “squeeze out” other routers, due to the higher priority. After sending HSRP to the multicast, the controlled router becomes the main router (Active Router) in the network, and all traffic will pass through it. In fact, we came to the implementation of mitm attacks.
For this attack vector, we need to know the group and password.
From the traffic dump given to us, we recognize the group (it is - 3) and the password. The password in our case is default - cisco.
Utilities used are yersinia, scapy.
Expert X comment:
The objective of the question was to determine the trainee's familiarity with modern (and not so) techniques for conducting MitM attacks. Let's look at potential scenarios based on an existing traffic dump:
1) ARP spoofing
ARP-spoofing is the oldest and easiest way to implement MitM attacks. It consists in sending a gratuitous ARP request to host A.
The IP address of host B is the IP address, and our MAC address is the MAC address. Such a request allows you to modify the ARP table on host A, forcing it to send requests to our device when trying to access host B. Host B is usually the default gateway.
Recommended Tools: bettercap, arpspoof
2) LLMNR, NBNS spoofing
Link-Local Multicast Name Resolution and NetBIOS Name Service are the protocols used to resolve hostnames on the local network. Unlike the DNS protocol, there is no dedicated server that stores all the information; instead, the request is broadcast to all hosts on the network, if the hostname in the request matches the hostname of the device, it will send a response.
As was correctly noted in the answer, the attacker can respond to such requests by sending his IP address in the response, which will lead to the fact that in the future the victim will contact the attacker’s device, instead of the device whose hostname appeared in the request. In addition, an attacker can request NTLM authentication from the victim, which causes the victim device to send an NTLM hash, which can be further used for brute force.
Recommended Tools: Responder
3) WPAD spoofing
WPAD spoofing can be attributed to a special case of LLMNR and NBNS spoofing. Web Proxy Auto Discovery protocol is used to automatically configure an HTTP proxy server.
The device sends an LLMNR / NBNS request with the wpad hostname, receives the corresponding IP address and tries to access the wpad.dat file via HTTP, which stores information about the proxy settings.
As a result, the attacker can perform LLMNR / NBNS spoofing and provide the victim with his wpad.dat file, as a result, all HTTP and HTTPS traffic will go through the attacker.
Recommended Tools: Responder, mitm6
4) Router Advertisement
As you can see from the dump, there are devices with IPv6 enabled on the network. While on the network, you can try sending messages to the victim IPv6 Router Advertisement in order to change the default gateway or DNS server.
Router Advertisement (RA) messages are part of the Stateless Address Autoconfiguration (SLAAC) mechanism, which is required to automatically obtain IPv6 addresses on a network, without using a DHCPv6 server, or in conjunction with it. This is achieved by periodically sending multicast RA messages to the router, which contain the default gateway address, network prefix, DNS server address, domain prefix.
Recommended Tools: raw-packet
5) DHCP spoofing
Also, in a dump, DHCP Discover requests from the same device are repeated at some intervals. We can conclude that there is no DHCP server in this network and respond to the next Discover request by specifying the victim as a default gateway to the device.
Recommended Tools: Yersinia
6) HSRP spoofing
In addition, HSRP packets can be seen in the dump. Hot Standby Router Protocol can increase the availability of routers that act as the default gateway. IP-, -. Hello - , . HSRP, , , HSRP .
: Yersinia
7) STP-
Spanning Tree Protocol L2- . BPDU-, , . BPDU-, , , , , , , , STP, , .
: Yersinia
No. 5. Nginx config
Here is the nginx web server configuration. Describe in detail what security problems you see in it?
Configuration: pastebin.com/nYp7uVbB
Job parsing
nginx, :
1) 86 , http X-Managed secured, nginx /management/
2) API 70 105 .
1) 86 , http X-Managed secured, nginx /management/
2) API 70 105 .
Expert J comment:
, . nginx , web-, nginx web- /. nginx , , , .
, , , . , . , , .
gixy .
Gixy 4 :
1) Alias travesal:
80 :location /static { alias /prod_static/; }
- , . : //host/static../etc/passwd. - alias: , /static, /prod_static/, : /prod_static/../etc/passwd, /etc/passwd. alias traversal
2) Http Splitting (CRLF injection)
nginx , , . HTTP-.
: github.com/yandex/gixy/blob/master/docs/ru/plugins/httpsplitting.md
3) -
75 «rigin» . , - , , production.host.evil.com .
: github.com/yandex/gixy/blob/master/docs/ru/plugins/origins.md
4) add_header
nginx : add_header, , , , . CSP .
: github.com/yandex/gixy/blob/master/docs/ru/plugins/addheaderredefinition.md
, gixy, . :
1) 17 default_type text/html. : , , nginx Content-Type, default_type. , Content-Type: text/html. HTML- , , , XSS- .
2) POST-
29-30 , . , “” POST-. . But! SSRF , , , , .
3) php-fpm
48 , FastCGI- unix , 9000. , , . , PHP-.
4) “” CSP
production.host Content-Security-Policy, Javascript, .
5) “” CORS
76-77 CORS, , cookie .
6) , 86 . secured /managed.
7) , , , -. , , , /user/{userid} IDOR.
, , , .
No. 6. Linux Permissions
When can a Linux user read other user's home directories?
Job parsing
~ () Debian
C ( , /etc/passwd).
, ftp , ~.
Example:
* root@server:~# ls ~ftp
* welcome.msg
:
* root@server:~# cat ~ftp/welcome.msg
* Welcome, archive user %U@%R!
, : :
* root@amorale:~# echo ~ftp
* /srv/ftp
C ( , /etc/passwd).
, ftp , ~.
Example:
* root@server:~# ls ~ftp
* welcome.msg
:
* root@server:~# cat ~ftp/welcome.msg
* Welcome, archive user %U@%R!
, : :
* root@amorale:~# echo ~ftp
* /srv/ftp
Expert K Comment:
, :
- ACL
- capabilities
, , :
“ , root” .
,Linux/Unix.
, “ ” — .
, ,funky_test.txt-rwxrw-rx 1 alice interns 12 4 13:00 funky_test.txt
, Linux/Unix :
- - — “rwx” alice
- — “rw” interns
- — “rx” others
read, write, execute.
, — , :
- , read
- , read
- read
,read. , execute .
, .
, , . :
1. , ls.
2. —POSIX Access Control Lists.c .
Example 1
,aliceinterns.funny_test.txt:$ whoami alice $ id uid=1001(alice) gid=1001(alice) groups=1001(alice),1002(interns) $ ls -la ----rwx--- 1 alice interns 12 4 13:00 funky_test.txt $ cat funky_test.txt cat: funky_test.txt: Permission denied $Example 2
—funky_test.txt604.bob,interns:$ whoami bob $ id uid=1002(bob) gid=1003(bob) groups=1003(bob),1002(interns) $ ls -la funky_test.txt -rw----r-- 1 alice interns 12 4 13:00 funky_test.txt $ cat funky_test.txt cat: funky_test.txt: Permission deniedRemarks
alice, . ,permission_denied:$ id uid=1001(alice) gid=1001(alice) groups=1001(alice),1002(interns) $ ls -la ----rwx--- 1 alice interns 12 4 13:00 funky_test.txt $ chmod 777 funky_test.txt $ ls -la funky_test.txt -rwxrwxrwx 1 alice interns 12 4 13:00 funky_test.txt $ cat funky_test.txt secret_pass
bob .Why is that
, « », :
- ID
effective UID—- GID
effective GID—- others.
, — , “” , , , :
- , ,
others- , ,
others
.POSIX Access Control Lists
— /. , ACL, , “+”
POSIX ACLs, — , . ACL, .Example
How it works.alicefunky_test.txt,-rwxrw-rx 1 alice interns 12 4 13:00 funky_test.txt
ACL.getfacl, , ACL, ,ls.$ getfacl funky_test.txt # file: funky_test.txt # owner: alice # group: interns user::rwx group::rw- other::rx
, ACL . , bob :setfacl -mu:bob:rwx funky_test.txt
“+”ls -l funky_test.txt -rwxrwxr-x+ 1 alice interns 12 4 13:00 funky_test.txt
:getfacl funky_test.txt # file: funky_test.txt # owner: alice # group: interns user::rwx user:bob:rwx group::rw- mask::rwx other::rx
ACL . :
- .
effective UIDeffective GID— . , ACL, . , , , , , .- ACL
mask, ACLowner, group, others
, , , — .
, ACL, , :
- ACL, ;
- , ACL, .
Number 7. Network dump II
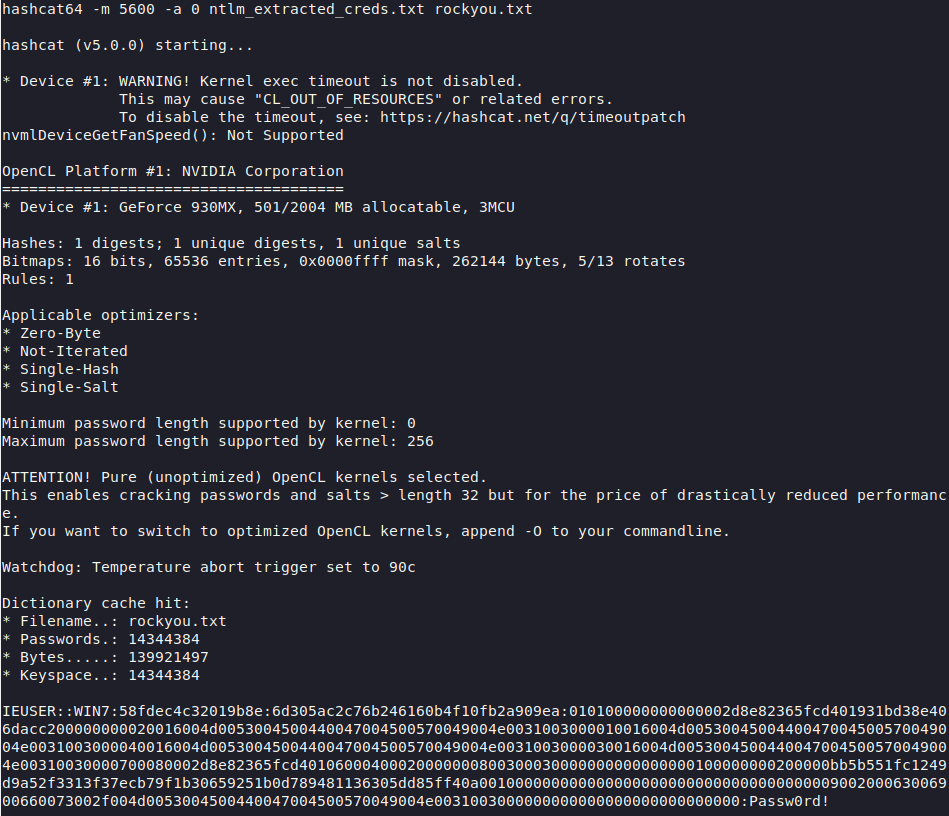
During the work in the internal network of the company, you were able to receive the following traffic. Analyze it, try to get useful data and files from the traffic, and also describe what further attacks you could conduct.
Traffic dump: yadi.sk/d/e3gNme4MBo6tFQ
Job parsing
— .
, .
, .

, SMB-, , , . SMB object list (File -> Export objects -> SMB… ).
— .
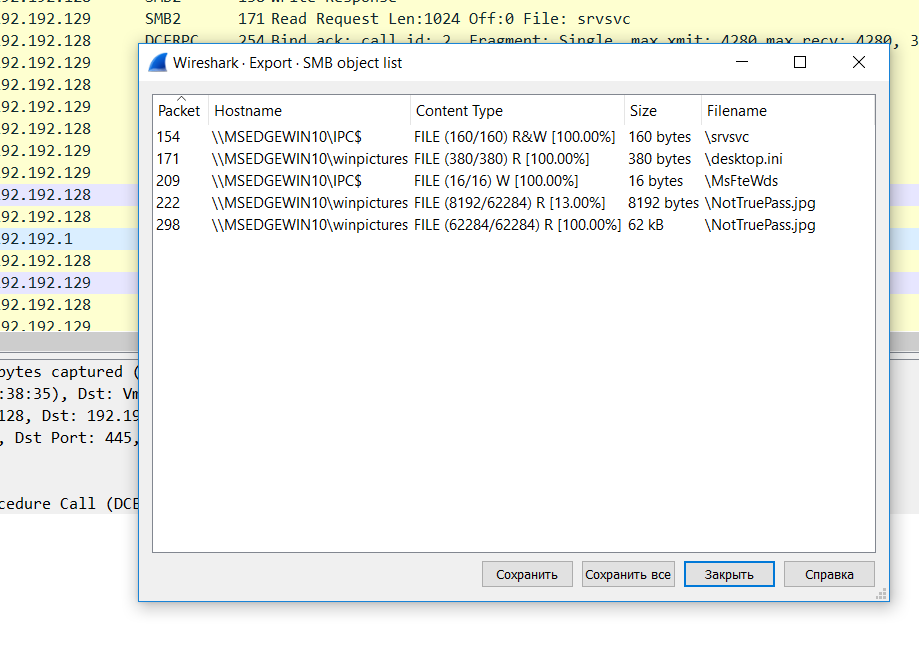
( SMB object list)

(NotTruePass.jpg)
.
“” TCP-… . . :(
, . .
( desktop.ini)
“” . , NTLM, , , NTLM “Pass-the-hash”. «-».
“” :
. MSEDGEWIN10.
— :
1) SMB Relay.
.
, MITM-
(. ).
— , , .
. , .
, , , .
2) NTLM Relay.
, NTLM-.
, NTLM-.
.
, , , .
, .
, .

, SMB-, , , . SMB object list (File -> Export objects -> SMB… ).
— .

( SMB object list)

(NotTruePass.jpg)
.
“” TCP-… . . :(
, . .

( desktop.ini)
“” . , NTLM, , , NTLM “Pass-the-hash”. «-».
“” :
1)User - 1 Account: IEUser Domain: WIN7 Host: WIN7 hex dump session key - 49 0c 38 3e f8 eb 63 88 79 0f 62 84 09 84 d2 dc 2) User - 2 Account: winwin Domain: WIN7 Host: WIN7 hex dump session key - 8d f6 1b 35 79 a3 78 d3 2e 81 09 f1 95 4f 71 0a 3) User - 3 Account: 192.192.192.29 Domain: WIN7 Host: WIN7 hex dump session key - c3 19 e0 21 1b e2 63 c6 03 9e e7 38 1b 56 f0 d1 . MSEDGEWIN10.
— :
1) SMB Relay.
.
, MITM-
(. ).
— , , .
. , .
, , , .
2) NTLM Relay.
, NTLM-.
, NTLM-.
.
, , , .
Expert K Comment:
, , :
- ( )
- — /
- ,
, :
Wireshark,Protocol Hierarchy StatisticsConversations.Protocol Hierarchy Statistics— .
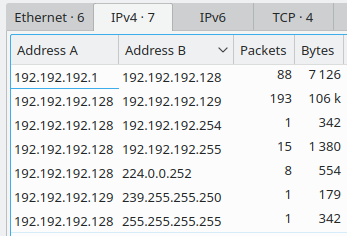
Conversations — , .
:
- (60%) — TCP, , , SMB. Protocol hierarchy SMB 40%, TCP, , 20% SMB.
- 192.192.192.128 192.192.192.129. SMB .
.
— SMB.
, — wireshark —ExportObject.tcp stream. , ,tcp stream, . , .
, , , , . , .
.
SMB .
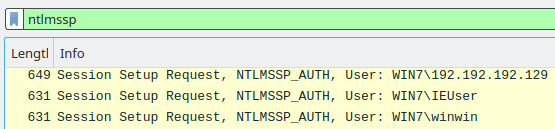
NTLM- “ntlmssp”.info, 3 :
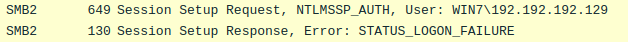
, .
Net-NTLMv2-, :
- challenge
- response
Net-NTLMv2hashcat.
,WIN7\winwinWIN7\192.192.192.129— , .WIN7\IEUser— , , , , , SMB.Net-NTLM, , Wireshark. , PCredz (https://github.com/lgandx/PCredz)IEUser( ) hashcat.
, .
6, ,SMB/NTLM,DNS.
, ,NTLMNTLMv1 (Net-NTLMv1),NTLMv2 (Net-NTLMv2)( ).
-NTLMNTLM,NTLMNTLMv1NTLMv2. , . But this is not so.
,NTLMv1/NTLMv2— challenge-response . , .
NT LM — “ ” — .
:
- PassTheHash — , , . But. ,
NT. PassTheHash NTLMv2 — . , “” , , .- NTLM Relay — , , NTLM. , .
- Spoofing, Windows: LLMNR, NetBios
- : MS17-010, / , .
Summary
:
- ( )
- ,
- eternalBlue
- NTLM relay
- NTLM relay — SMB
- , (ARP-spoofing, DNS )
Number 8. SSH Pivoting Tricks

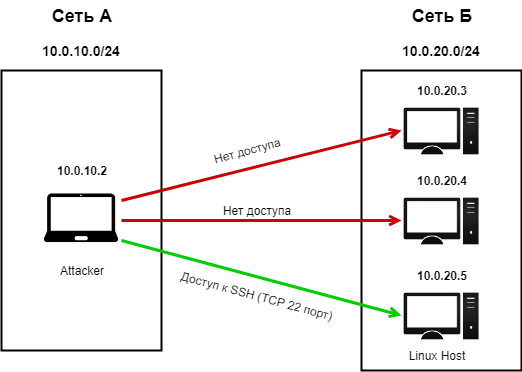
You are on network A (10.0.10.0/24), you were able to access via SSH to the Linux host (10.0.20.5) on network B (10.0.20.0/24). However, you found that you do not have full access to network B. Think of and describe in detail the method by which you could scan network B without installing any additional scripts / utilities / programs on the Linux host.
Job parsing
, , :
nmap
?
Option:
1) ping.
-> ping -b 10.0.20.255
ping , , .
, .
.
, CentOS 7.
.
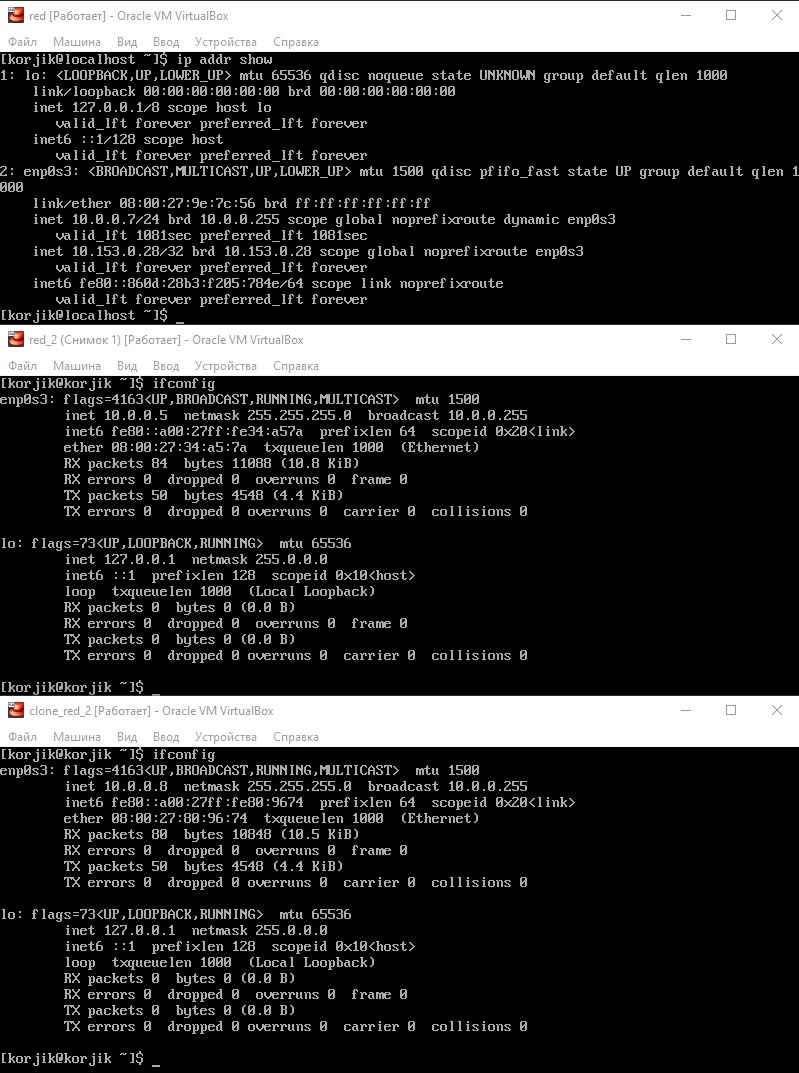
( )
, . :(
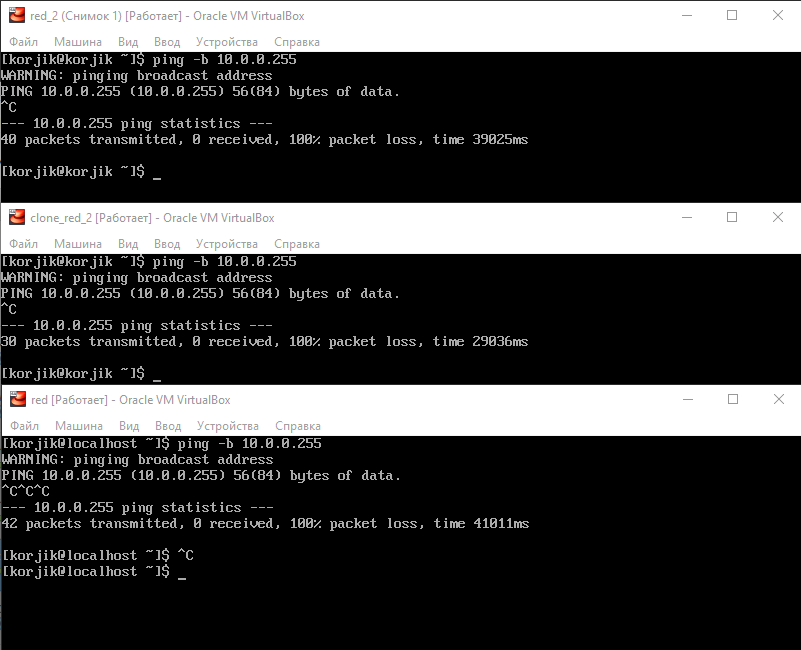
2) ARP- .
->
Debian — arp-scan --interface=/* */ 10.0.0.0/16
Linux arp, ( Debian) - , arp-scan.
arp-scan, , , .
nmap
?
Option:
1) ping.
-> ping -b 10.0.20.255
ping , , .
, .
.
, CentOS 7.
.

( )
, . :(

2) ARP- .
->
Debian — arp-scan --interface=/* */ 10.0.0.0/16
Linux arp, ( Debian) - , arp-scan.
arp-scan, , , .
KryaKrya expert comment:
, , , Pivoting. , , , , , .
, ping , ARP- (arp -a), (route). , netcat (nc -h), , (nc -vnz 10.0.20.3 0-1000). , , , , , , - bash, python .
— SSH-, SOCKS- SSH, .
ssh -D 1337 user@10.0.20.5 -f -N
. nmap SOCKS- proxychains .
proxychains nmap 10.0.20.0/24
nmap 10.0.20.0/24 --proxy socks4://10.0.20.5:1337
nmap - SOCKS-. SYN- ( nmap ) SOCKS-, SOCKS- TCP- , SYN- , SYN, SYN ACK. CONNECT- (-sT), nmap SOCKS-.
nmap -sT 10.0.20.0/24 --proxy socks4://10.0.20.5:1337
, - , , . , Linux-, nmap -sT , , , , , , .
No. 9. Android SSL pinning bypass
You are exploring a mobile application for Android. You have found that the application sends requests over the secure HTTPS protocol.
1) Describe how you would try to bypass the protection and get unprotected HTTP traffic.
2) What will change if SSL-pinning is enabled in the application, how can I try to circumvent protection in this case?
Job parsing
«, HTTP-.»
.
proxy host wifi.
Android , , .
— ( ) — ( , ).
, MITM, Android 6.0, , .
6.0, .
« , SSL-pinning, ?»
, SSL-pinning.
SSL-pinning — , , «» .
HTTPS-, , «». , .
, MITM-, .
, , , .
— Frida.
Frida — Dinamic Instrumentation Toolkit, , .
, Frida Javascript.
Frida , , , «True» «False», .
Frida:
1. , . -.
2. Frida. Root.
.
APK- . , , .
. apk META-INF .
“” APK-.
APK smali Java, , .
, , .
.
proxy host wifi.
Android , , .
— ( ) — ( , ).
, MITM, Android 6.0, , .
6.0, .
« , SSL-pinning, ?»
, SSL-pinning.
SSL-pinning — , , «» .
HTTPS-, , «». , .
, MITM-, .
, , , .
— Frida.
Frida — Dinamic Instrumentation Toolkit, , .
, Frida Javascript.
Frida , , , «True» «False», .
Frida:
1. , . -.
2. Frida. Root.
.
APK- . , , .
. apk META-INF .
“” APK-.
APK smali Java, , .
, , .
Expert Commentary I:
, MITM HTTPS .
, Proxy WiFi. ProxyDroid, iptables .
, Root , , ?
SSL-Pinning, , , “Frida+Objection”. , :)
No. 10. What is your favorite attack?
Tell us about the most interesting attack technique or published vulnerability that you have learned about recently.
The only task in the “free format". The attack that I liked lately is dns-rebinding.
That’s all for me. Thanks for attention!
Closing remarks from Digital Security
Now let us slightly open the veil, how did the process of evaluating the guys go.
Each answer was independently evaluated by at least 3 specialists (one must somehow have fun in their free time from audits). The range of acceptable ratings was from 0 to 5 points with the ability to set at least 2.5, or even 3.1337 if you wish.
As a result, the estimates are averaged and summed up. Thus, the maximum could score 50 points. Our experts tried to be as loyal as possible and understand what the next candidate had in mind about “ hacking through the form code ” or something else like that)
We set the passing score after the application deadline is closed. This year he made 29 points, and the best result was 43.5. As a result, approximately 24% of all applicants went for an internship.
The statistics are as follows:

However, for these lucky ones it didn’t end so simply, because then they had a face-to-face interview, where we asked the guys what they liked in the questionnaire, what questions were the most difficult to answer and how long it took them to complete . Thus, we were convinced that no one helped the guys with the questionnaire, and they filled it out themselves. At the same time, we received useful feedback for the next years.
It may seem that such a system is unreasonably complex, but, unfortunately, we cannot afford to accept everyone and want to share our knowledge with the most motivated of the guys.
By the way, which is noteworthy, every year we see a surge in applications exactly at the end of the term:

For our part, we provide a wide variety of lectures (almost every day!), Access to our small but proud internal laboratory with a bunch of interesting hacking tasks compiled by experienced specialists where you can hone your practical skills and train your “hacker instinct".
The main occupation of the internship is a joint study with an experienced curator of some interesting and significant aspect of security, whether it be vulnerabilities in new technology or a tool that allows you to solve existing difficulties in conducting security analysis. However, we will talk more about this in our materials dedicated to the end of Summer of Hack 2019.
As a conclusion, I want to say that for the second year we have been selecting using such a system and are increasingly convinced of its effectiveness. With the help of it, we really manage to select strong trainees and get information about the average level of knowledge among students and graduates.
Source: https://habr.com/ru/post/461077/
All Articles