"God Mode for the Internet": tracking users through extensions Chrome and Firefox
 Many have browser extensions installed. At a minimum, ad blocker. But when installing extensions, you should be careful: not all of them are useful, and some are used for surveillance at all.
Many have browser extensions installed. At a minimum, ad blocker. But when installing extensions, you should be careful: not all of them are useful, and some are used for surveillance at all.Even if a particular extension does not “steal” any information right now, there is no guarantee that it will not begin to do so in the future. This is a system problem.
Recently, experts uncovered the activities of the "analytical" company Nacho Analytics , which offers the service under the ambitious motto "God mode for the Internet", tracking the actions of millions of users through the Chrome and Firefox extensions in almost real time delay).
The researchers called DataSpii (pronounced data-spy) a catastrophic leak of personal data. They note that the analytic firm and its clients not only receive the history of visited pages, but extract various personal information from URLs and page headers.
')
Nacho Analytics customers can search the general traffic for various parameters, for example:
- GPS coordinates of users;
- tax returns, business documents, slides of corporate presentations on OneDrive and other hosting services;
- video from Nest security cameras;
- VINs of recently purchased cars, names and addresses of their owners;
- attachments to Facebook Messenger messages and Facebook photos, even sent privately;
- bank card details;
- travel routes;
- and much more.
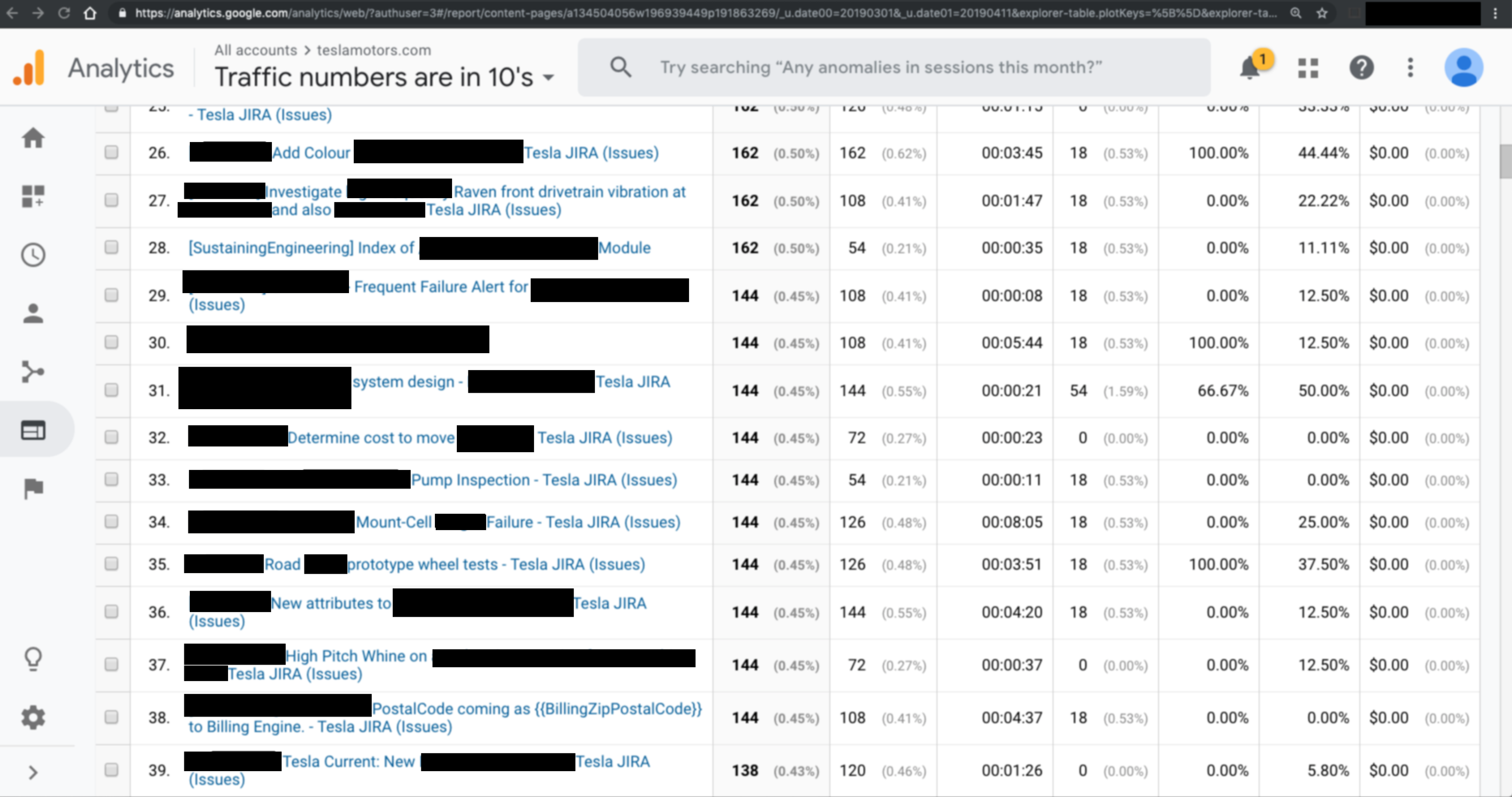
For $ 49 per month, the service allowed you to track the actions of employees or users of a particular company / site: for example, Apple, Facebook, Microsoft, Amazon, Tesla Motors or Symantec.

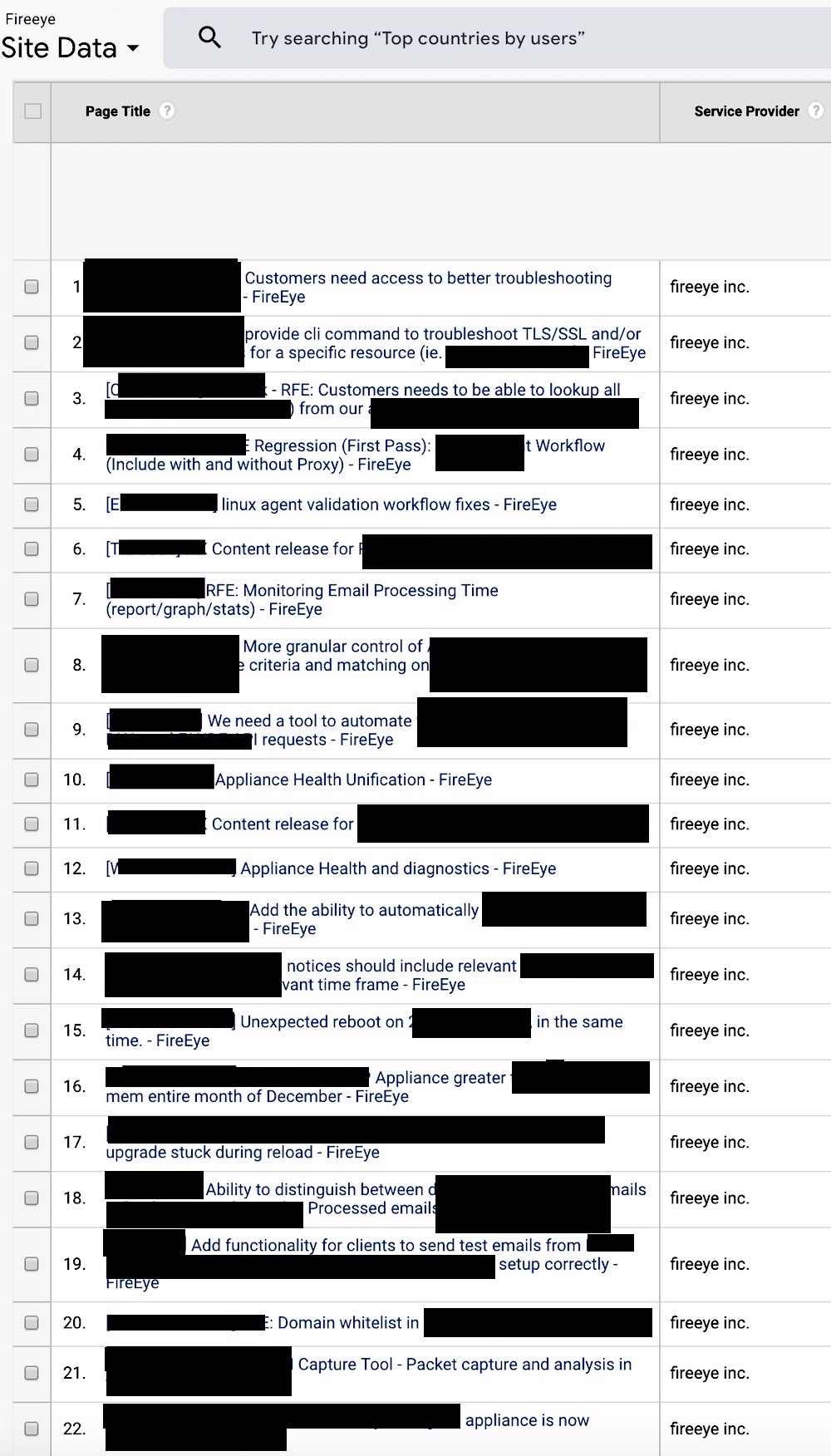
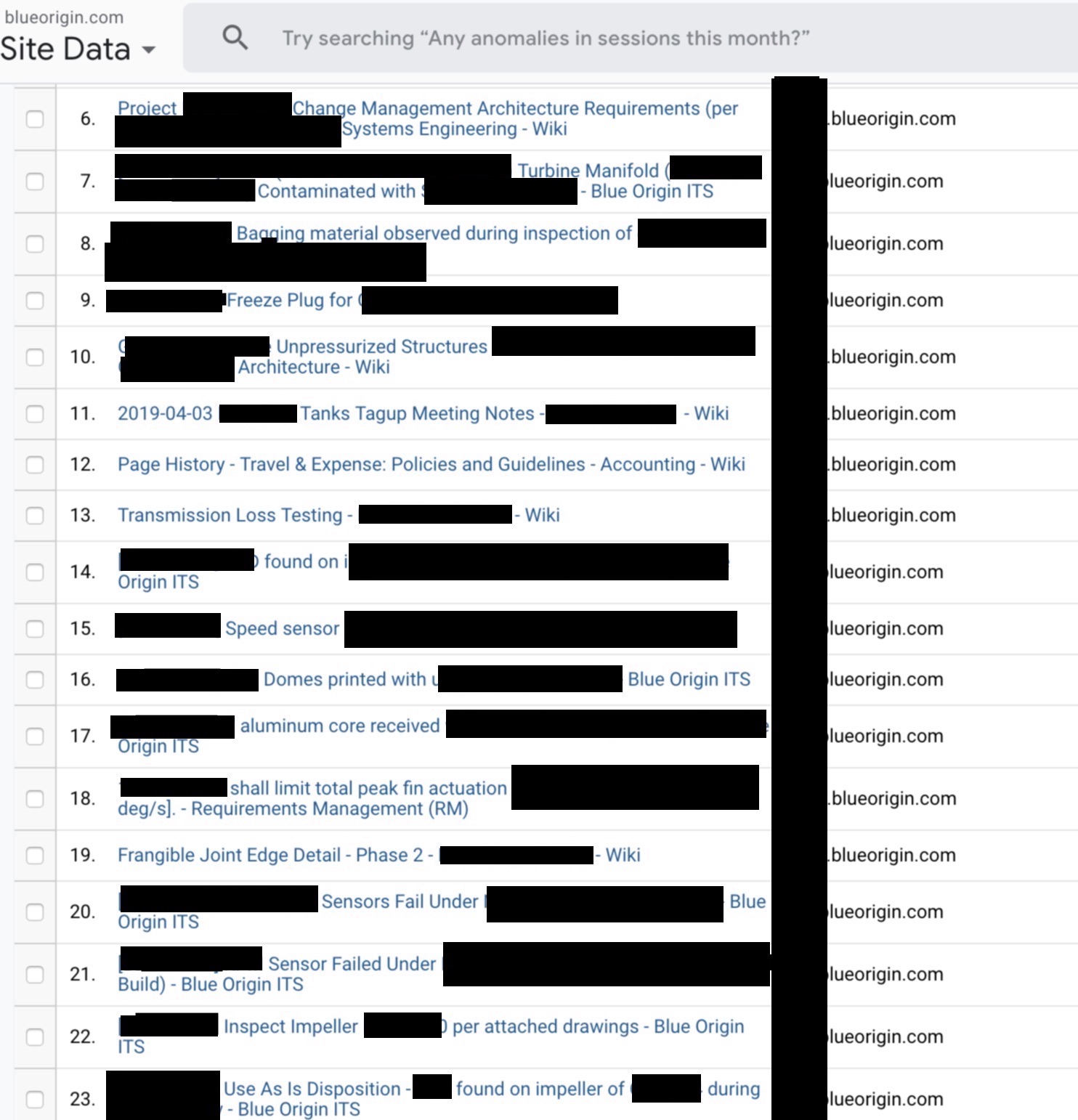
The DataSpii leak has affected more than 4 million users. Researchers have identified a number of extensions through which surveillance has been carried out. They are listed in the table below:
| Extension name | Number of users | Browser | Chrome extension ID (if any) |
| Hover zoom | More than 800,000 | Chrome | nonjdcjchghhkdoolnlbekcfllmednbl |
| SpeakIt! | More than 1.4 million | Chrome | pgeolalilifpodheeocdmbhehgnkkbak |
| Superzoom | 329,000+ | Chrome and Firefox | gnamdgilanlgeeljfnckhboobddoahbl |
| SaveFrom.net Helper | Up to 140,000 | Firefox | N / a |
| Fairshare unlock | More than 1 million | Chrome and Firefox | alecjlhgldihcjjcffgjalappiifdhae |
| PanelMeasurement | More than 500,000 | Chrome | kelbkhobcfhdcfhohdkjnaimmicmhcbo |
| Branded surveys | eight | Chrome | dpglnfbihebejclmfmdcbgjembbfjneo |
| Panel Community Surveys | one | Chrome | lpjhpdcflkecpciaehfbpafflkeomcnb |
The last four extensions clearly informed that they were collecting data from the browser, the rest did not.
The following table lists the companies targeted by the Nacho Analytics analytics service and what specific information was displayed. The relevant data was either provided directly, or there were links to them in the interface.
| Company | Nacho Analytics Data |
| 23andMe | Published reports 23andMe |
| Alienvault | JIRA data from alienvault.atlassian.net |
| Amazon web services | AWS S3 Authentication Request Strings |
| American airlines | Passenger information: name, confirmation number from the ticket |
| Amgen | Corporate Network Data |
| Apple | The last 4 digits of a credit card when ordering Apple products, type of card, place of receipt of the order, name of the customer, iCloud mailing address |
| AthenaHealth | Corporate Network Data |
| Atlassian | Almost real-time update of tasks for company employees with thousands of sub-domains atlassian.net |
| Blue origin | JIRA data from the domain blueorigin.com |
| Buzzfeed | JIRA data from domain buzzfeed.atlassian.net |
| Capitalone | Zoom Conferences URL from capitalone.zoom.us |
| Cardinalhealth | JIRA data from cardinalhealth.atlassian.net |
| Dell | Zoom Conferences URL from dell.zoom.us |
| Drchrono | Patient names, prescription drug names |
| Epic systems | Network data LAN of corporate network visitors |
| Facebook Messenger applications, including tax returns | |
| Fireye | JIRA data from fireeye.com domain from the corporate network |
| Intuit | Quickbook invoices |
| Kaiser permanente | Network data from a corporate LAN |
| Kareo | Patient Names |
| Merck | Network data from a corporate LAN |
| Microsoft OneDrive | Files from OneDrive hosting, including tax returns |
| NBCDigital | JIRA data from nbcdigital.atlassian.net |
| Nest | Video Recordings from Nest Security Cameras |
| Netapp | Zoom conferencing URL with netapp.zoom.us |
| Oracle | Zoom Conferences URL with oracle.zoom.us |
| Palo alto networks | Corporate Network Data |
| Pfizer | Corporate Network Data |
| JIRA data from reddit.atlassian.net | |
| Roche | Corporate Network Data |
| Shopify | AWS S3 parameter leakage victim |
| Skype | Skype Chat URLs |
| Southwest airlines | Information about passengers: it was possible to track passengers on board almost in real time, and there was enough confidential data in the service to cancel a flight or change a flight |
| Spacex | Corporate Network Data |
| Symantec | Corporate Network Data |
| Tesla | Corporate Network Data |
| Tmobile | JIRA data from tmobile.atlassian.net |
| Trend micro | JIRA data from visitors to the internal subdomain trendmicro.com |
| Uber | Coordinates of taxi pick-up and drop-off points, Zoom conference URLs from uber.zoom.us |
| UCLA | Zoom Conferences URL from ucla.zoom.us |
| Under armor | JIRA data from underarmour.atlassian.net |
| United airlines | Passenger last names and their flight confirmation numbers |
| Walmart | Zoom Conferences URL from walmart.zoom.us |
| Zendesk | Application for tickets in the support service, among which you can search for a specific client |
| Zoom video communications | Zoom Conference URL |
After the researchers reported a data leak in Google and Mozilla, the listed extensions were removed from the official catalogs, and Nacho Analytics suspended the “God Mode for the Internet” service. Maybe not forever.
Some extensions explicitly reported data collection from the browser and performed it only with the consent of users, but others did it secretly. Interestingly, individual extensions (Hover Zoom and SpeakIt) for additional masking did not start sending the collected data immediately, but only 24 days after installation.
Surprisingly, Nacho Analytics positions itself as a legal “analytic service”. She claims that data collection is carried out with the consent of users. But it is known that about 99% of people do not read the agreement on the use of the software during installation, so such a “consent” is just a convention. Moreover, theoretically, a company can buy an existing popular extension from its current owner - and modify it a bit in the new version to start collecting data. Most users are likely to agree to the new usage agreement without reading it.
As mentioned above, the ecosystem of browser extensions in their current form is a systemic security issue. Browser developers should consider how to solve it.

Source: https://habr.com/ru/post/460987/
All Articles