Digital Shadows - competently helps reduce digital risks

Perhaps you know what OSINT is and have used the Shodan search engine, or are already using the Threat Intelligence Platform to prioritize IOC from different feeds. But sometimes it is necessary to constantly look at your company from the outside and get help in eliminating identified incidents. Digital Shadows allows you to track digital assets of the company and its analysts suggest concrete actions.
In fact, Digital Shadows harmoniously complements the existing SOC or completely closes the external perimeter tracking functionality. The construction of the ecosystem has been going on since 2011 and a lot of interesting things have been implemented under the hood. DS _ monitors the Internet, soc. network and darknet and reveals from the entire flow of information only important.
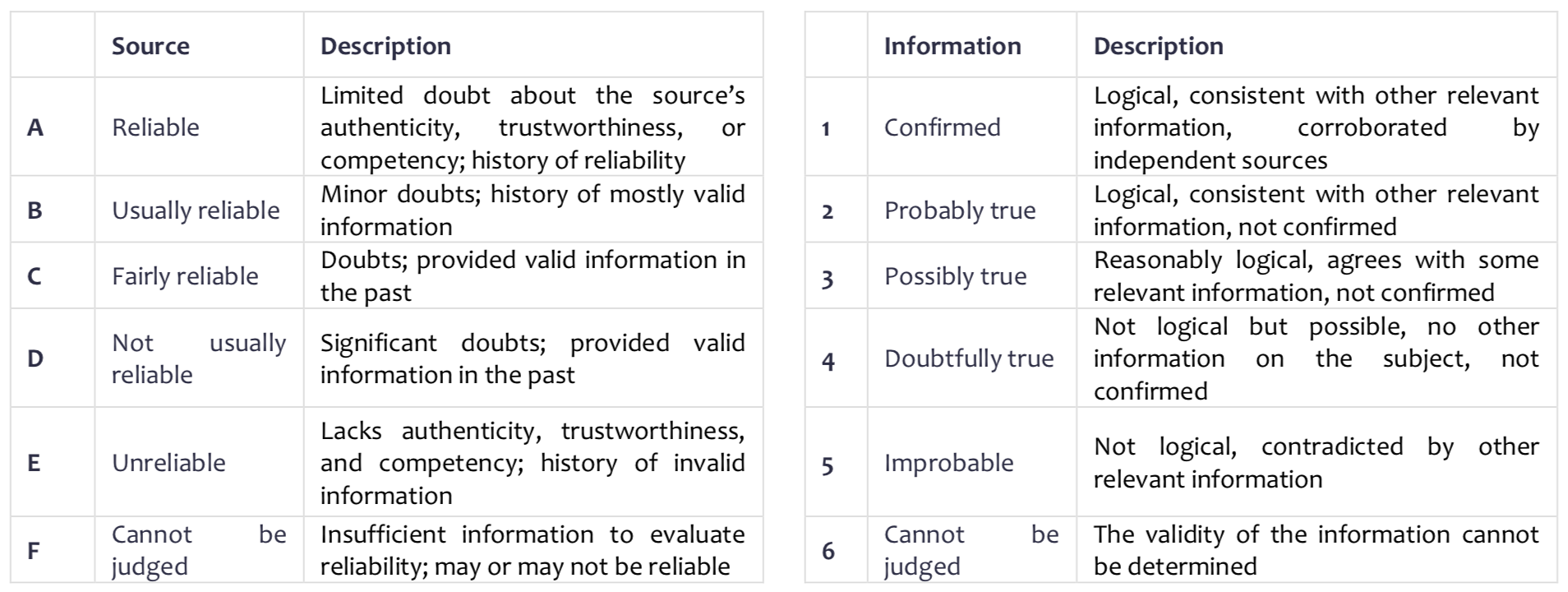
In its weekly IntSum newsletter , the company provides a sign that you can use in your daily life to evaluate the source and the information received. You can also see the tablet at the end of the article.
Digital Shadows is able to detect and redeem phishing domains, fake social media accounts; find compromised employee credentials and leaked data, reveal information about upcoming cyber attacks on the company, constantly monitor the organization’s public perimeter and even regularly analyze mobile applications in the sandbox.
')
Identifying digital risks
Each company in the course of its activities is cluttered with chains of relations with customers and partners, and the data that it seeks to protect becomes more and more vulnerable, their number only grows.
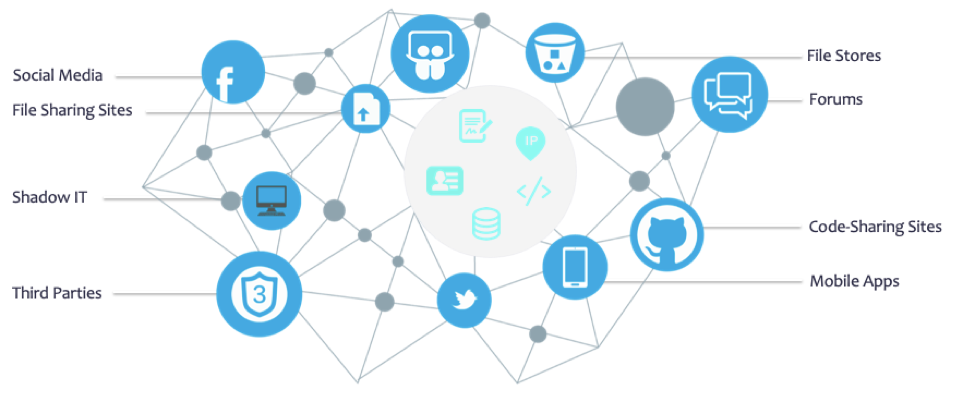
To begin managing these risks, a company must begin to look beyond its perimeter, monitor it, and receive operational information about changes.
Data Loss Detection (sensitive documents, available staff, technical information, intellectual property).
Imagine if your intellectual property was disclosed on the Internet or your internal confidential code accidentally got into the GitHub repository. Attackers can use this data to launch more targeted cyber attacks.
Online Brand Security (phishing domains and profiles in social networks, imitating the mobile software company).
Since it is now difficult to find a company without a social network or similar platform for interacting with potential customers, attackers try to impersonate the company’s brand. Cybercriminals do this by registering fake domains, social network accounts and mobile applications. If phishing / fraud succeeds, it can affect customer revenue, loyalty and trust.
Attack Surface Reduction (vulnerable services on the perimeter with the Internet, open ports, problem certificates).
As the IT infrastructure grows, the attack surface continues to grow, the number of information objects. Sooner or later, internal systems may be randomly published in the outside world, for example, a database.
DS _ will inform about problems before the attacker can take advantage of them, highlight the most priority ones, analysts will recommend further actions and you can immediately take a takedown.
DS interface _
You can use the solution’s web interface directly or use the API.
As you can see, the analytical summary is presented in the form of a funnel, ranging from the number of references and ending with real incidents obtained from various sources.
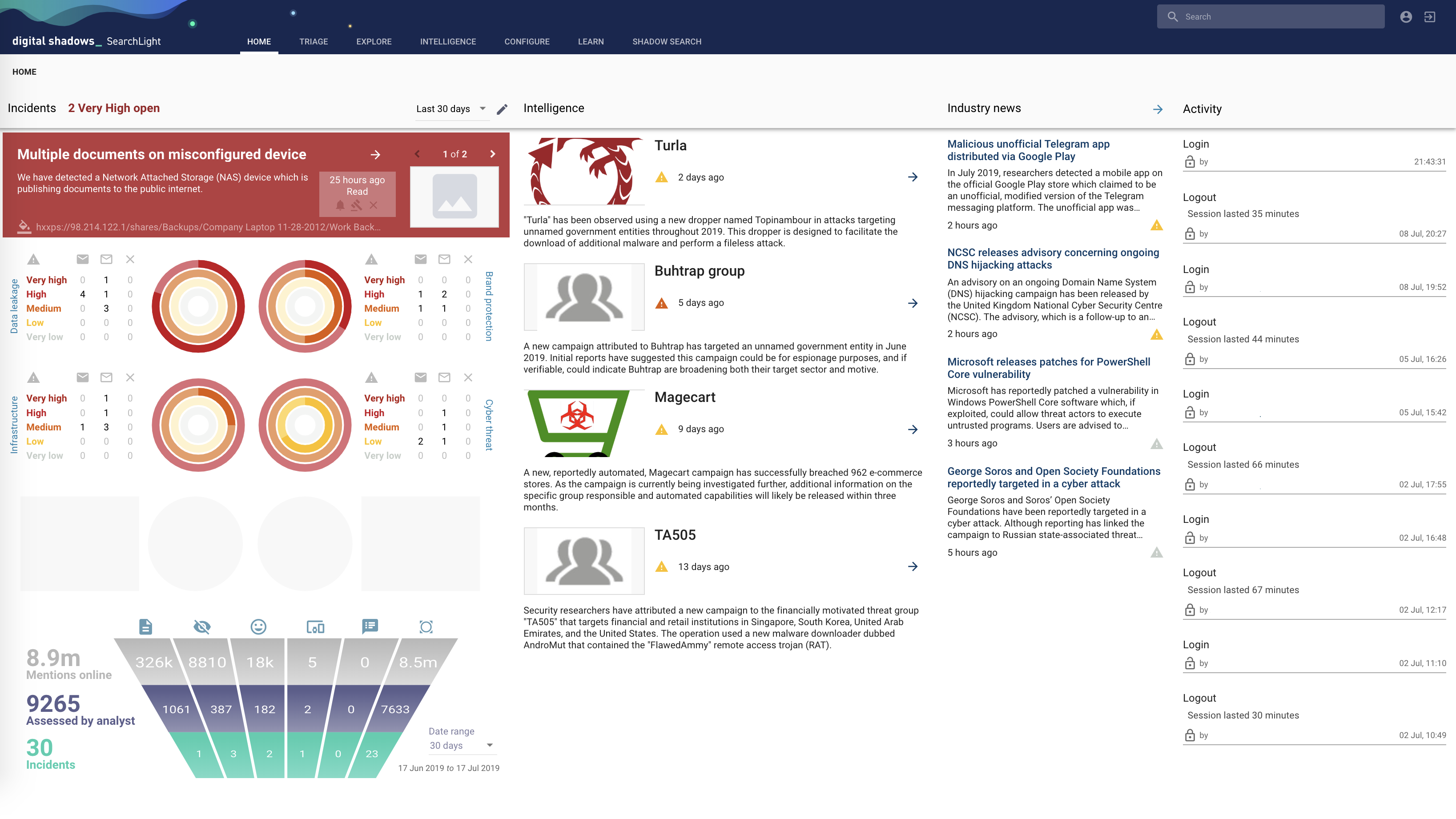
Many use the solution as a Wikipedia with information about active attackers, their campaigns and events in the field of information security.
Digital Shadows are easy to integrate into any external system. Both notifications and REST APIs are supported for integration into your system. You can call IBM QRadar, ArcSight, Demisto, Anomali and others .
How to manage digital risk - 4 basic steps
Step 1: Identify Business Critical Assets
This first step, of course, is to understand what the organization cares about most and what it wants to protect.
Can be divided into key categories:
- People (customers, employees, partners, suppliers);
- Organizations (related and service companies, common infrastructure);
- Systems and operational critical applications (websites, portals, customer data databases, payment processing systems, employee access systems or ERP applications).
When compiling this list, it is recommended to follow a simple idea - assets should be around critical business processes or economically important functions of a company.
Usually add hundreds of resources, including:
- company names;
- brands / trademarks;
- IP address ranges
- domains;
- links to social networks;
- suppliers;
- mobile applications;
- patent numbers;
- labeling documents;
- DLP identifiers;
- email signatures.
Adaptation of the service for yourself guarantees only relevant alerts. This is an iterative cycle, and system users will add assets as they become available, such as new project names, upcoming mergers and acquisitions, or updated web domains.
Step 2: Understanding Potential Threats
In order to best estimate the risks, it is necessary to understand the potential threats and digital risks of the company.
- Technicians, tactics and procedures of malefactors (TTP)
The MITER ATT & CK framework and others help to find a common language between defense and attack. Gathering information and understanding behavior across a wide range of intruders provides a very useful context for protection. This allows you to understand the next step in the observed attack, or to build a general concept of protection based on the Kill Chain . - Capabilities of intruders
The attacker will use the weakest link or shortest path. Various attack vectors and their combinations - mail, web, passive information gathering, etc.
Step 3: Monitor unwanted digital asset appearances
To identify assets, you need to regularly monitor a large number of sources, such as:
- Git repositories;
- Poorly configured cloud storage;
- Paste sites;
- Soc. media;
- Crime forums;
- Dark web.
To start with something, you can use free utilities and techniques, ranked by degree of difficulty in the ' A Practical Guide to Reducing Digital Risk ' guide.
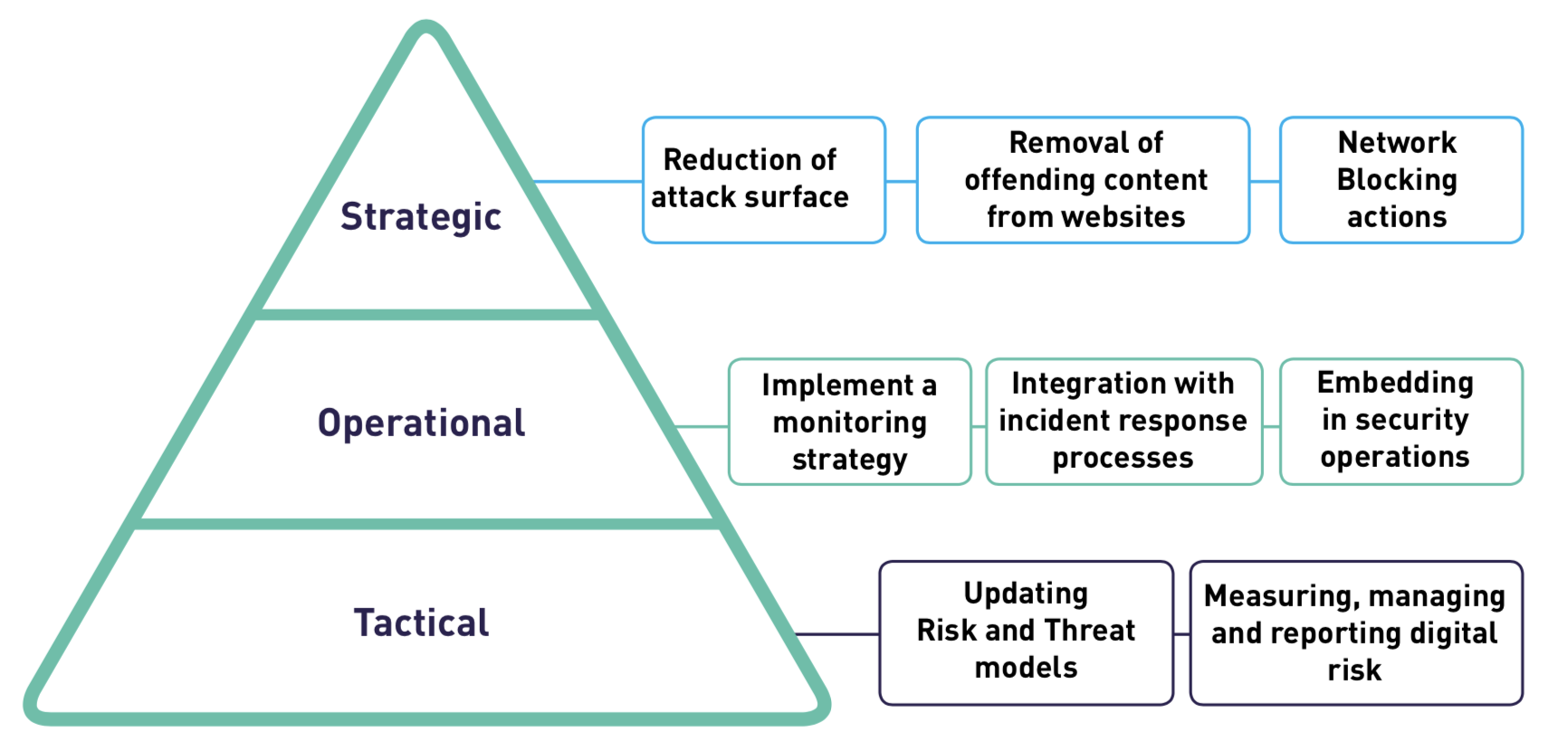
Step 4: Take Protection Measures
After receiving the notification, you must take specific actions. Tactical, Operational and Strategic.
In Digital Shadows, each alert includes recommended actions. If this is a phishing domain or a page on the social network, then you can track the status of repayment performance in the “Takedowns” section.
Access to the demo portal for 7 days
At once I will make a reservation that this is not full-fledged testing, but only temporary access to the demo portal for getting acquainted with its interface and searching through some information. Full testing will contain relevant data for a particular company and involves the work of the analyst.
Demo portal will contain:
- examples of alerts for phishing domains, open credentials, and infrastructure weaknesses;
- Search darknet pages, criminal forums, feeds and much more;
- 200 profiles of cyber threats, tools and campaigns.
You can access this link .
Weekly newsletters and podcasts
In the weekly IntSum newsletter, you can receive a brief summary of current information and recent events over the past week. You can also listen to the ShadowTalk podcast.
To assess the source of Digital Shadows using qualitative statements of the two matrices, assessing the reliability of the sources and the accuracy of the information obtained from them.
This article is based on the ' A Practical Guide to Reducing Digital Risk '.
If you are interested in the decision, you can contact us - the company Factor Group , the distributor of Digital Shadows _ . It is enough to write in free form on digitalshadows@fgts.ru .
Authors: popov-as and dima_go .
Source: https://habr.com/ru/post/460465/
All Articles