Background: quantum cryptography on the fingers

The history of quantum cryptography began not with communication technologies, but with an attempt to solve a completely different task - to create money that cannot be faked.
Stephen Wiesner of Columbia University in 1983 proposed creating state-class quantum banknotes that cannot be copied even if the person who wants to do this has typographical equipment and paper with which the original was made. The probability of making an exact copy of the original, protected by quantum technologies, tends to zero.
How did it all start?
The essence of the technology is that there are traps with photons on each banknote, each of which is polarized in a certain way along two different bases. One basis provided for "cross-shaped" polarization: that is, the photon could be polarized at an angle of 0 or 90 degrees from some vertical, and the second - diagonal, that is, with angles of 45 and 135 degrees.
')
To copy a banknote, the counterfeiter must measure the polarizations of the photons, but he does not know in which basis each of them is polarized (the Central Bank keeps this information secret, and only he knows which polarizations correspond to the number of the banknote). The offender can choose bases in a random way, and then he has some chances for success, however, very small. But they become insignificant if you create photon traps. That is, to increase the number of photons on each banknote (the probability of guessing decreases as an inverse power function of the number of photons). If each banknote is supplied with a dozen traps, the probability of a successful counterfeit drops to almost zero.
It was a great idea, but, unfortunately, technically unrealizable: convenient and accessible for mass use traps for photons, suitable for placement on money, have not been created yet.
What is quantum communication and when did the working system appear?
Wiesner also suggested that a similar mechanism could be used to create confidential communication channels. A year after the publication of his article, scientists Gilles Brassard and Charles Bennett developed the first protocol for quantum communication, which they named after the first letters of their surnames and the year the technology was created - BB84. This protocol is widely used in modern quantum communication networks.
Bennett and Brassard proposed to encode the data in single-photon quantum states, for example, in their polarization. As in the case of other quantum objects, the very fact of measurement necessarily affects the state of the object, therefore, if someone third tries to “overhear” the transfer of photons - that is, measure the states of photons that we exchange, we will definitely notice it because photon states. Therefore, in theory, seamlessly connecting to the channel of quantum data transmission is impossible in principle - the fundamental laws of quantum mechanics do not allow (in practice, this technology has some vulnerabilities, but more on that below).
The BB84 protocol works as follows. One of the interlocutors (traditionally called Alice) sends photons to the other (Bob), polarized in one of two non-orthogonal to each other bases: rectangular or diagonal. Bob obtains them and measures the polarization, choosing bases for measurement randomly, and records the measurement results and bases. Then he and Alice exchange information on the bases used (but not on the measurement results) over the open channel, and the data obtained on the basis of unmatched bases are discarded. Only the values measured in the matching bases remain (in the technology of quantum key distribution, this is called “key sifting”).
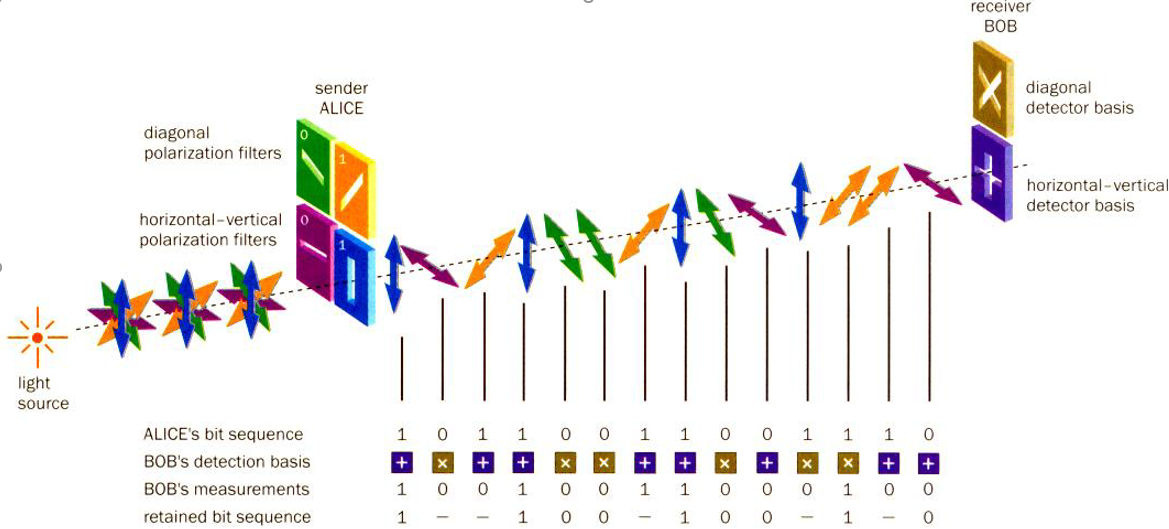
Wolfgang Tittel, Grégoire Ribordy and Nicolas Gisin, Quantum cryptography, Physics World, Volume 11, Number 3 https://iopscience.iop.org/article/10.1088/2058-7058/11/3/30
A possible “spy” who overhears data transmission over this line of communication (it is usually called Eve) can intercept a single photon, measure its polarization and try to send a copy of the photon to Bob.
But, in accordance with the theorem on the impossibility of cloning an arbitrary quantum state, this will lead to an increase in the number of errors in the distributed quantum key. As a result, both Alice and Bob will understand that their channel is being listened to by a stranger. To determine the level of errors in the key after the quantum distribution procedure, Alice and Bob over the open channel compare a small part of the key. It is believed that if the level of errors in the key is less than 11 percent, then the security of the communication line can be guaranteed.
Bennett and Brassard conducted the first experiment on the transmission of information through the quantum channel at the end of October 1989. They were not lucky - they didn’t take their idea seriously, so the scientists decided to create a prototype of the experimental device independently and with their own money. Friends helped to implement the installation. The first installation for absolutely secure quantum communications transmitted data over a distance of 32.5 centimeters. Brassard recalls that their system protected the data only from a person who would have been completely deaf: the power unit was very noisy, and the noise was different depending on the polarization of the photons the unit provided at the moment.
Despite all the shortcomings, the installation was working. Actually, from this moment began the history of quantum communications and quantum networks, which today stretch for thousands of kilometers and go into space.
Why is all this necessary?
Today, almost no data is transmitted without encryption. The most popular encryption methods that are used now are based on one assumption: the task of decrypting messages is so complex that the attacker's computing power is not enough to solve it. In other words, the cost (in money and time) of decryption will be disproportionately higher than the value of the information thus obtained. This applies to both symmetric encryption (AES, DES, Russian GOST 28147-89 ), and asymmetric (for example, RSA).
Is quantum communication safe?
At the moment, it is completely safe, but the situation may soon change due to the appearance of a quantum computer.
The fact is that in public-key encryption systems, so-called one-way functions are used, in which, by a known argument, it is easy to find the value of a function, but the inverse operation is extremely complicated. For example, multiplying even very large numbers is a simple task for a computer, while the opposite is multiplication (factorization), which requires many times more computational time than to solve the original problem, and the complexity of this problem grows rapidly as the number increases.
The use of the asymmetry of multiplication and factorization is based, for example, on the widespread RSA encryption algorithm, and many other encryption systems, which are called “asymmetric”. Their main advantage is that to use them you do not need to transfer encryption keys via a special secure channel (for example, a flash drive with a trusted courier), as is the case with symmetric algorithms, where the same secret key is used for encryption and decryption.
In asymmetric technologies, two keys are used - public and private, the first can be transmitted over networks, and it can be used only to encrypt the message, and for decryption, the private key is stored, which is stored by the user. The private and public keys are interconnected with an asymmetric function, and it is believed that it is almost impossible to recover a closed one from a public key with the help of modern technologies (this may take billions of years).
But it is now, in the future, the situation may change if quantum computers appear. Back in the mid-1990s, mathematician Peter Shore developed a quantum algorithm that got his name. The algorithm allows for factorization almost as fast as multiplication. Quantum devices on which Shor's algorithm can be launched already exist, but so far they have successfully factorized only the numbers 15 and 21. With the advent of more advanced quantum machines, all cryptosystems based on this asymmetry will become useless.
Some scientists call the quantum computer “information atomic bomb”, because of which we will have to remove most of the information and banking services we use today: about 50% of the Internet traffic of these services is encoded with public key algorithms. Moreover, the fact that a quantum computer is not created now does not mean that the data you are exchanging now is safe — perhaps it will be decrypted in the future. For example, the US intelligence agency NSA stores at least some exabytes of undeciphered data in its data center in Utah. As soon as new decryption methods appear, they can be decrypted.
But quantum physics also provides us with protection against computational capabilities and quantum and future classical computers and computational algorithms - quantum key distribution.
Is this just a theory or are there real cases?
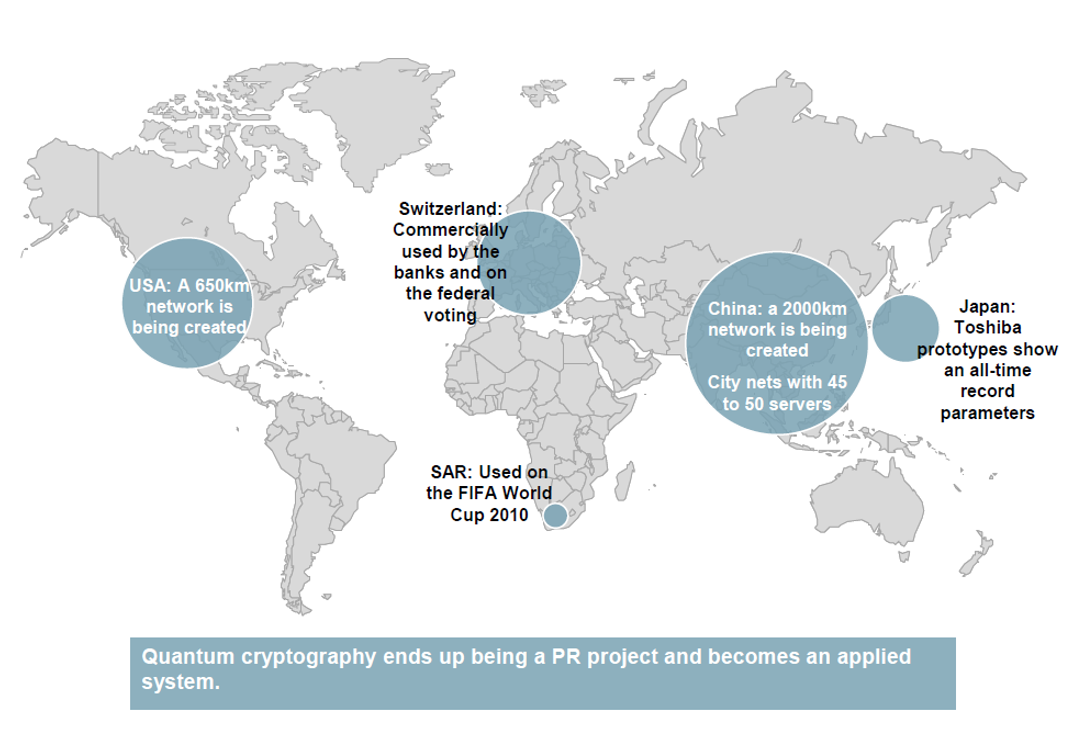
In short, not only theory for a long time. The quantum technology market is still small; the first company that set itself the goal of making money on quantum cryptography - ID Quantique - appeared ten years later after the first experiments of the Bennett group, in 2001. It was founded by immigrants from the University of Geneva, among whom was the eminent physicist Nicolas Gisin. But the first to put the technology on commercial rails was American Magiq Technologies Inc. In November 2003, she announced that she was ready to offer its potential customers a system of quantum key distribution, which can work 120 kilometers away.
A few months later, ID Quantique put its system on the market, very soon it became one of the market leaders. Using quantum technology, she organized data protection during the regional elections in Geneva in 2007, and in February 2018 set a record for the transmission distance of quantum data via fiber-optic cable - 421 kilometers.
The range and speed of data transmission still remain the main problem of quantum communication. The fact is that the transmitted data is encoded in states of single photons, at this stage the quantum communication lines are very vulnerable to interference and noise, therefore, in practice, backbone networks transmit the quantum key to distances up to 100 km. At greater distances, the key generation rate becomes too low.
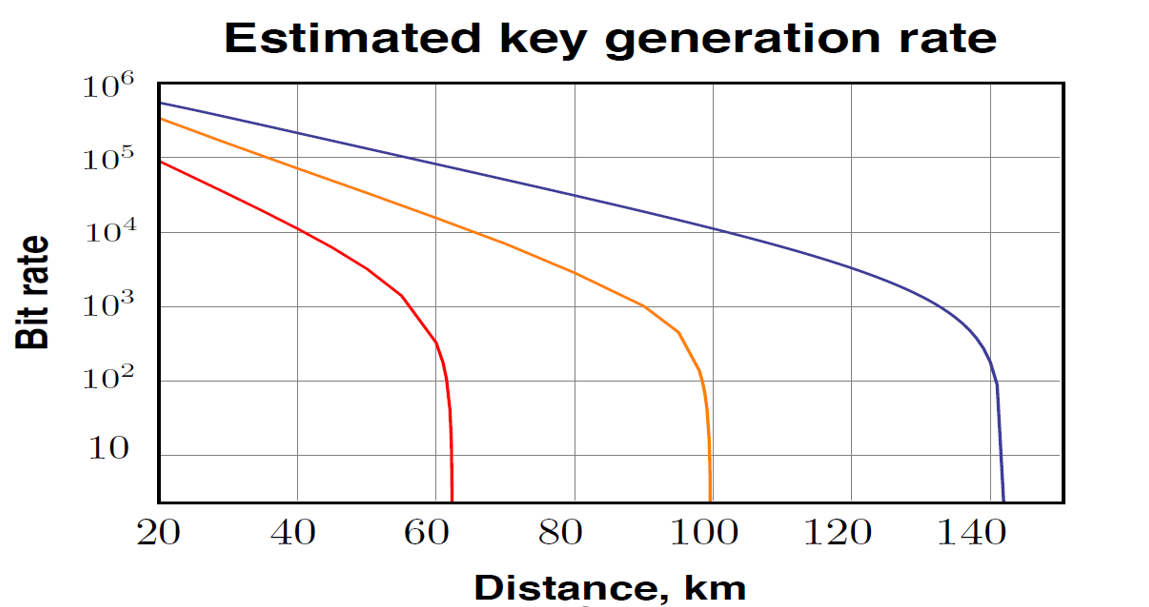
Phys. Rev. Lett. 121, 190502 (2018) Secure quantum key distribution over 421 km of optical fiber
In most cases, quantum communication is used within one locality. For large distances, quantum networks are built from a number of separate fragments connected by specially protected nodes.
Today, three companies dominate the global market for commercial quantum communication systems: Chinese Qasky and QuantumCTek, as well as Swiss ID Quantique. They supply almost the entire range of solutions and components: from sources and detectors of single photons, quantum random number generators to integrated devices:
- ID Quantique offers two types of systems: based on a bidirectional scheme (Plug and Play) and coherent one-pass (coherent one way - COW). These devices are designed to work in urban fiber-optic networks and allow you to transmit quantum keys at distances up to 70 kilometers.
- Qasky produces systems for government agencies; there is no market for its products.
- QuantumCTek in 2018 showed devices for urban networks: key generation systems, compatible switches, devices for secure telephony.
Quantum communications protection technologies are actively used by large banks and financial organizations, government agencies, and data processing centers. The world market for quantum cryptography in 2018 was estimated at $ 343 million , and in 2021 it is expected to double by half - to $ 506 million . In Russia, the first attempts to transfer quantum keys to laboratories took place in the early 2000s at the Institute of Physics of Semiconductors of the SB RAS. In 2014, a prototype of a working quantum communication system was presented at ITMO University in St. Petersburg - then it was about data transmission between two buildings of the university at a distance of 1 kilometer, that is, in fact, about a laboratory experiment.
In 2016, the Russian Quantum Center launched the first city quantum communication line, based on the use of “regular” optical fiber. She linked the two offices of Gazprombank, which were located at a distance of about 30 kilometers from each other.
Currently, experimental and commercial quantum networks have been created and are being created in Moscow, Kazan and St. Petersburg. The projects are mainly supported by large Russian banks and Rostelecom.
Are there any bigger projects?
There are several large quantum networks in the world. In the USA (Quantum Key Distribution, Quantum Xchange), in Europe (SECOQC and Swiss Quantum), in Japan, Toshiba is engaged in this project, but China is developing the most large-scale project.
The Chinese quantum network today is about 2 thousand kilometers in length and connects the capital and several of the largest financial and industrial centers.
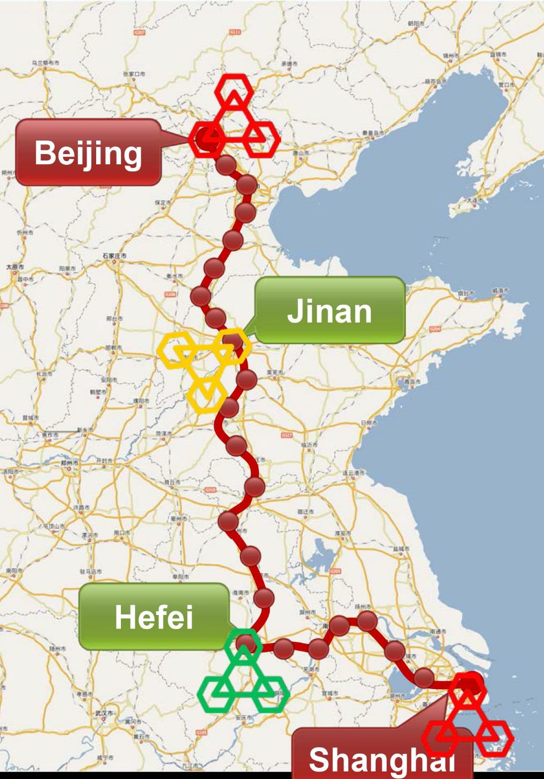
In addition, China is one of the pioneers in the field of space quantum communications. Satellite channels are one of the ways to solve the problem of distributing a quantum key to long and intercontinental distances.
In 2016, China launched a small Mo-Tzu satellite (aka QUESS - Quantum Experiments at Space Scale, "Quantum Space-Scale Experiments") developed by the Jian-Wei Pan group from the Shanghai University of Science and Technology. In 2017, data appeared on the results of the experiment with the satellite: the device provided the distribution of quantum keys at a distance of over 7,600 kilometers - between the observatories in Beijing and in Vienna. Chinese scientists plan to develop global quantum communication lines, where the satellite will act as a trusted node.
What with quantum technologies in Russia?
In addition to the Russian Quantum Center (RCC) and its subsidiary QRate, in the Russian Federation, groups of MSU employees work together with OJSC InfoTeKS and ITMO St. Petersburg (Kvanttelecom) to implement the quantum communication project.
Moscow State University and Infotex presented a pre-production sample of a quantum telephone - a voice communication system, where voice data is encrypted through quantum key distribution. According to the developers, the total investment in the project will be about 700 million rubles, and the cost of the basic set of equipment - a server and two phones - will be about 30 million rubles .
The RCC was the first in the world to develop a quantum protected blockchain - a tool for creating a distributed database in which it is almost impossible to fake records. Quantum cryptography methods allowed to protect the blockchain from the threats associated with the advent of a quantum computer. The scheme was tested on urban fiber networks.
In addition, RCC and QRate built a quantum network and demonstrated a multisite session of quantum-protected videoconferencing at the St. Petersburg International Economic Forum. The leaders of Sberbank, Gazprombank and PwC Russia auditing company took part in the quantum communication session.
QRate has also developed a serial setup for quantum cryptography, which can be integrated into the existing standard telecommunications infrastructure and adapted to work with cryptographic protocols. The devices use detectors and sources of single photons created in the RCC.

At the design and creation stage, there is a quantum network in Skolkovo, negotiations are underway on the development of an already existing quantum network with Sberbank and Gazprombank.
QRate also plans its own space project in the future: install a quantum signal transmitter on a small Kubsat satellite, and distribute quantum keys between two ground stations.
There are conferences on quantum technologies?
Yes, there are, including in Russia.
ICQT
The International Conference on Quantum Technologies, ICQT, is held every two years in Moscow. Scientists, top managers of technology companies and information security experts speak at the event. Here are a few big names from ICQT 2019: Eugene Polzik, Rainer Blatt, Peter Zoller, Tommaso Kalarco, Hartumt Neven, Mikhail Lukin, Christopher Monroe. This time the conference takes place from July 15 to 19 .
July 18 will be a free open day. You can listen to speakers from Google, Airbus Blue Sky, D-Wave and Quantum Flagship. Anyone can come, but you need to register on Timepad.
QEC2019 Quantum error correction
From July 29 to August 2, a conference on the correction of quantum errors will be held in London. It is called “Quantum error correction”. Quantum information has a large number of unusual properties, one of them is just the correction of quantum errors.
The conference is organized by a group of scientists from the Institute of Physics. Not all associations participate in the conference, but a group dealing with quantum technology issues - Quantum Optics, Quantum Information and Quantum Control group.
QCALL Early-Stage Researchers Conference 2019
From September 16 to September 19, a conference on quantum technologies will also be held in Italy. Young scientists who specialize in quantum technologies are invited to take part in it. The core of the conference is 15 researchers from Europe. The organizers hope to combine the efforts of a large number of scientists from around the world on solving the most important issues of modern quantum science.
Source: https://habr.com/ru/post/460165/
All Articles