Security Week 29: Zoom vulnerability, security and drama
 Last week researcher Jonathan Leitsach published a very emotional post about vulnerabilities in a client for web conferencing Zoom for the macOS operating system. In this case, it is not entirely clear whether the vulnerability was an unintentional bug or a pre-planned feature. Let's try to figure it out, but if it’s short, it’s like this: if you have a Zoom client installed, an attacker can connect you to his teleconference without asking, moreover, he can activate the webcam without asking for additional permissions.
Last week researcher Jonathan Leitsach published a very emotional post about vulnerabilities in a client for web conferencing Zoom for the macOS operating system. In this case, it is not entirely clear whether the vulnerability was an unintentional bug or a pre-planned feature. Let's try to figure it out, but if it’s short, it’s like this: if you have a Zoom client installed, an attacker can connect you to his teleconference without asking, moreover, he can activate the webcam without asking for additional permissions.The moment when instead of searching for the patched version, someone decides to simply remove the client from the system. But in this case it will not help: a web server is installed along with the client, which works even after uninstallation - it can even “return” the client software to the site. Thus, even those who once used Zoom services, but then ceased, were in danger. Apple came to their aid, without much fanfare, removing the web server with an update for the OS. This story is a real infosec drama, in which users can only watch how a variety of software appears and disappears on their computers.
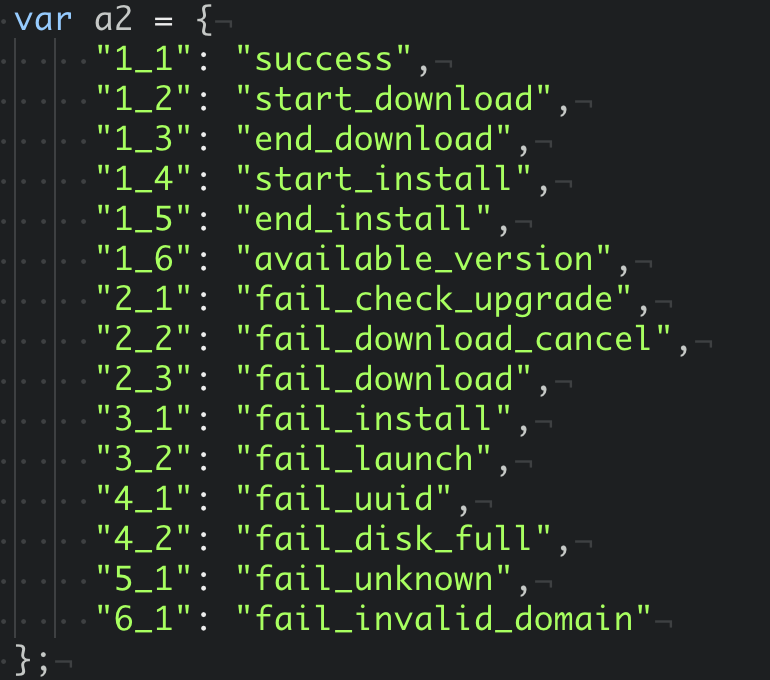
The study of the Zoom client’s methods began with a study of the local web server: the website of the service tries to access it when opening a link to connect to the newsgroup. A relatively elegant method of querying the status of a local server is used — by transferring an image of a specific format.
')
This is done to bypass the limitations of the browser, following the rules of Cross-Origin Resource Sharing . The Zoom web server can also send a connection request to the conference. This query looks like this:
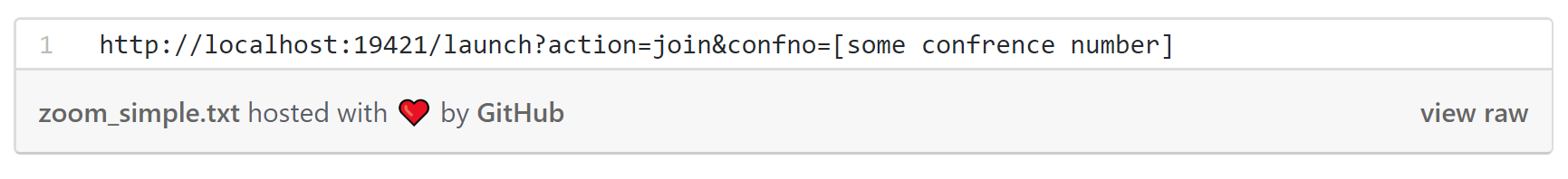
You can create a conference, place a similar request on a web page, send a link to the victim, and the client installed on the computer will automatically connect the user. Further it is worth looking at the parameters of the web conference itself:
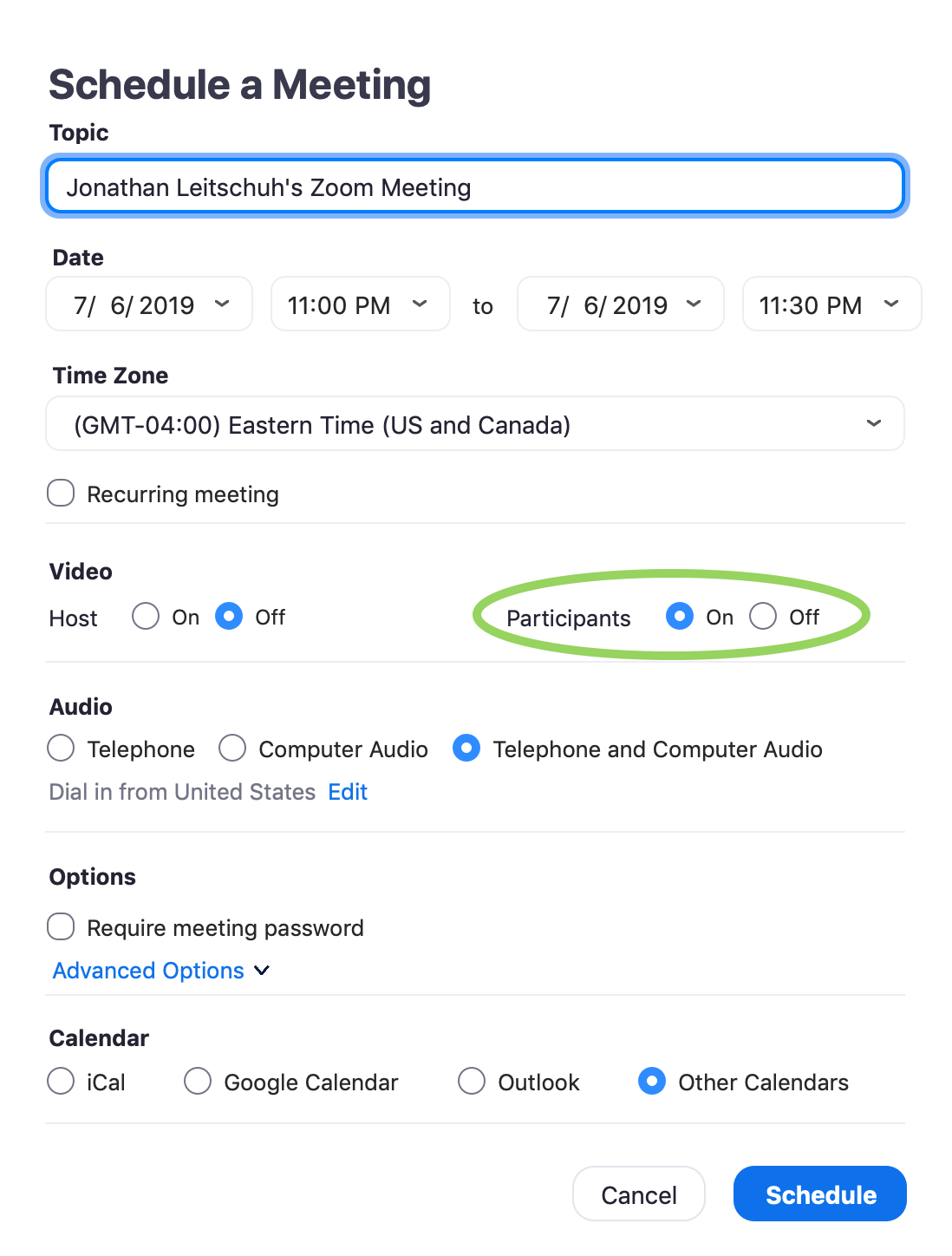
You have the option of forcing the user's webcam on. That is, you can lure an unsuspecting person to a conference call and immediately receive an image from the camera (but the victim must turn on the sound from the microphone manually). In the Zoom client, the automatic power on of the camera can be blocked, but with the default settings, the camera turns on immediately. By the way, if you send requests to connect to the conference continuously, the Zoom application will constantly switch focus to itself, not allowing the user to somehow undo this action. This is the classic Denial Of Service attack.
Finally, the researcher confirmed the possibility of forcibly upgrading or reinstalling the Zoom client if the computer is running a web server. At first, the vendor’s response was far from ideal. Zoom developers have proposed several patches in the logic of the web server in order to exclude the possibility of users connecting without demand. All of them easily managed or somewhat complicated the life of a potential intruder. The final solution was to add another parameter to the local server. As the researcher found out, it also did not solve the problem. The only thing that exactly repaired is the vulnerability that allows DoS-attacks. And on the proposal of Jonathan to remove the inclusion of a webcam at the request of the conference organizer, the answer was given that it was a feature “it’s more convenient for customers.”
The first time a researcher tried to contact the Zoom developers on March 8th. On July 8, the generally accepted three-month deadline for fixing vulnerabilities expired, and Jonathan published his post on what he considered an unsolved problem. Only after the publication of the article Zoom went to more radical measures: on July 9 a patch was released , which completely removes the web server from computers running macOS.
Dear editors regularly communicate via videoconferencing and can say from personal experience: everyone does it. Not in the sense that everyone installs a local web server with the client and then forget to remove it. All or almost all conference services require more privileges in the system than a browser page can provide them. Therefore, local applications, browser extensions, and other tools are used to make the microphone and camera work in the process of communication, and you can share files and images of your desktop. Frankly, the "vulnerability" (or rather, a deliberate error in logic) Zoom - this is not the worst thing that happened with such services.
In 2017, the problem was discovered in the browser extension of another conferencing service - Cisco Webex. In this case, the vulnerability allowed to execute arbitrary code in the system. In 2016, Trend Micro's password manager was also found in the local web server, which also opened up the ability to execute arbitrary code. At the end of last year, we wrote about a hole in the utility for Logitech keyboards and mice: even there a local web server was used, calls to which were possible from anywhere.
Conclusion: this is a fairly common practice, although from a security point of view, it is clearly not the best - there are too many potential holes with such a web server. Especially if it is created by default for interaction with external resources (for example, a site that initiates a web conference). Especially if it can not be removed. The ability to quickly restore the client Zoom after deletion was obviously done either for the convenience of users, or for the convenience of the developer. However, after the publication of the study, this brought additional problems. Okay, active Zoom users received an update, and the problem was resolved. And what to do with those who once used the Zoom client, then stopped, but the local web server still works for them? As it turned out, Apple quietly released an update that removes the web server, even in this case.
We must pay tribute to the developer of the Zoom service: after, so to speak, a negative public reaction, they solved the problem and now regularly share updates with users. This is clearly not a success story: here the developer tried to politely ignore the real proposals of the researcher, and the researcher called it a "zyrodeem" that they are not quite. But in the end everything ended well.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
Source: https://habr.com/ru/post/460135/
All Articles