The Matrix has you: overview of projects using MITER ATT & CK

For a long time, the MITER ATT & CK (Adversarial Tactics, Techniques and Common Knowledge) matrix has been discussed at various sites, including a whole series of articles here at Habré itself. We can say that the community has adopted this model; moreover, many have begun to use it. Today we have compiled for you a small overview of various projects that are aimed at:
- Improving the perception and convenience of working with the matrix;
- Comparing Analytics with ATT & CK;
- Checks for various attacks described in the matrix.
We will agree on the shore: the monitored utilities have not been thoroughly tested, it is better to contact the original source for details.
')
Content
Introduction
The first model ATT & CK was created in September 2013 and was focused mainly on Windows. Since then, ATT & CK has evolved significantly due to the contribution of the cybersecurity community. In addition to it, an additional knowledge base PRE-ATT & CK, which describes preparation for the attack, and ATT & CK for mobile devices was created.
As of July 2019, Enterprise ATT & CK includes 314 attack methods for Windows, Linux and Mac. The matrix structure consists of 11 tactics: from initial access to taking control through C & C and exfiltration of data. Each phase of the attack life cycle consists of a variety of techniques that have been successfully used by various groups of cybercriminals to compromise an organization’s network. When testing security, RedTeam essentially does the same thing, so not using a similar knowledge base would be a big omission.
In this article we will not dwell on the ATT & CK matrix itself, all the details can be found on the developers website . The benefits and applicability of this knowledge base are indicated by its frequent use by large and not-so vendors: almost all threat detection and hunting solutions already have a correlation of events with this matrix.
Matrix navigation, data view
ATT & CK Navigator
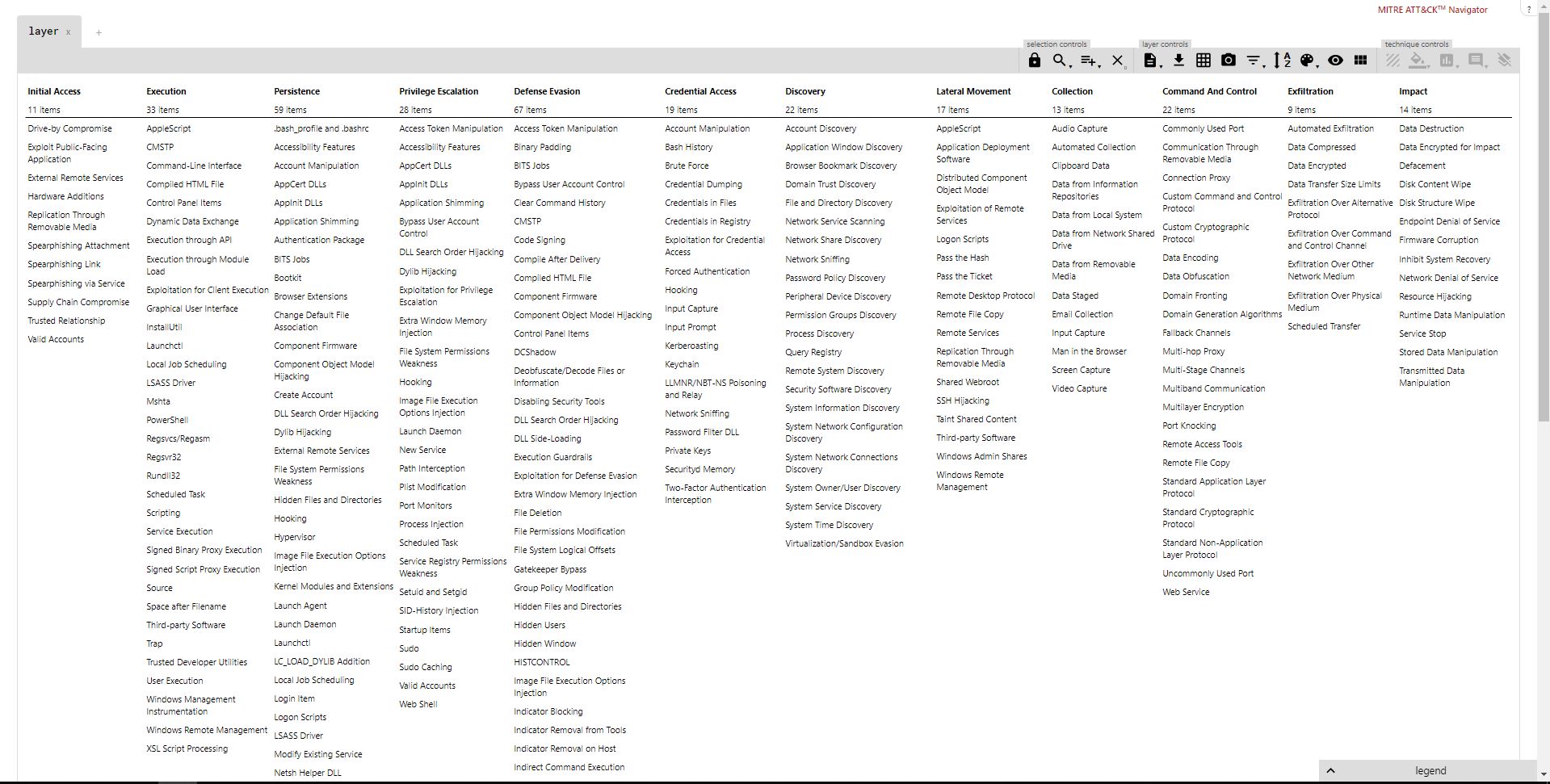
→ Project Page
An open source web application that provides basic navigation and annotations for all platform matrices. Despite its simplicity, the application greatly simplifies working with the matrix, allows you to create layers on top of the main matrix. A specific layer can demonstrate techniques of a particular group, or vice versa, visualize a protective coating. Navigator helps you plan your RedTeam or BlueTeam. In fact, the application simply allows you to manipulate the cells in the matrix: color coding, adding a comment, assigning a numeric value, etc.
Viewer playbook
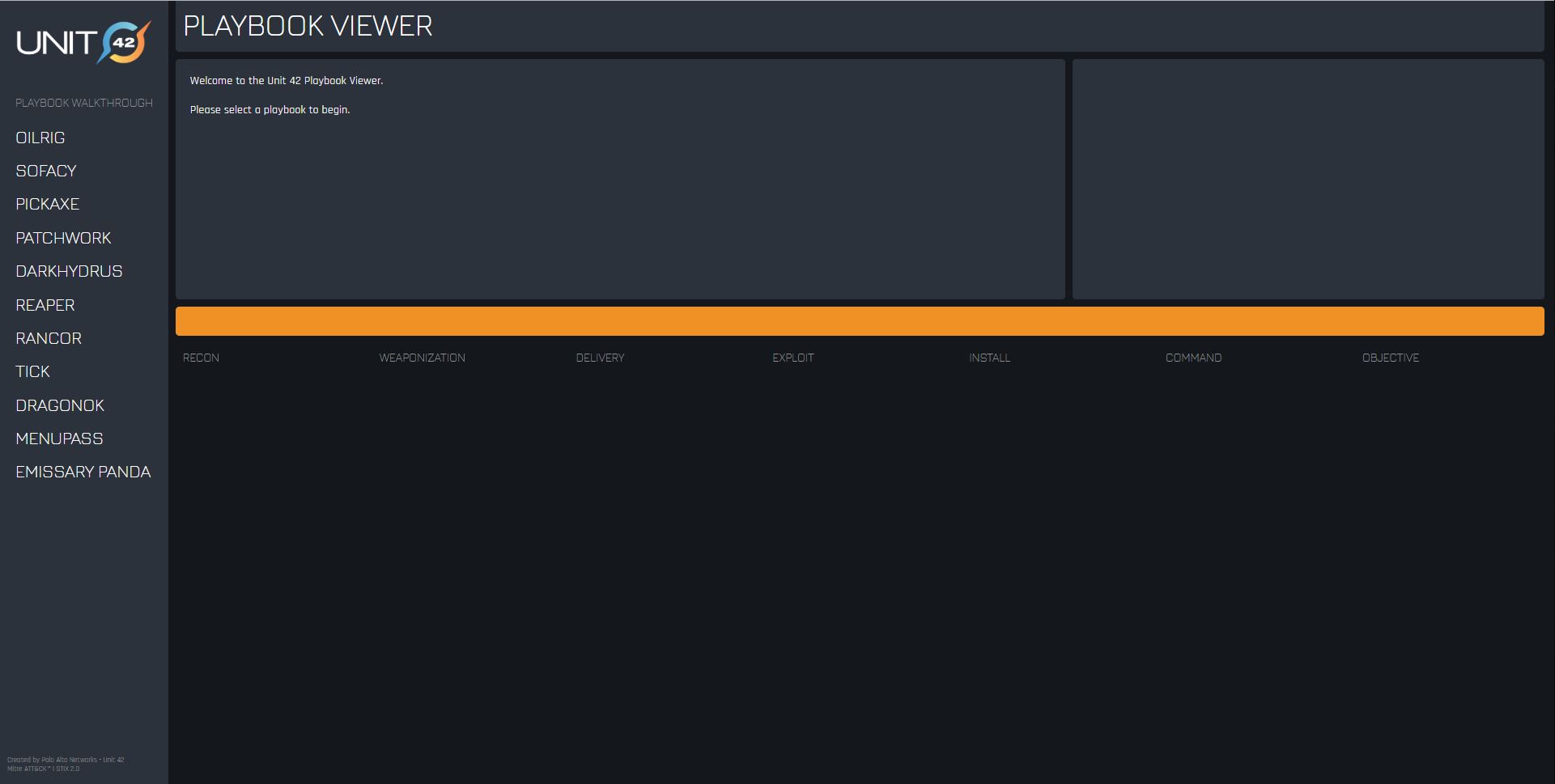
→ Project Page
→ Project page on github
Viewer Playbook is a system for analyzing the content of STIX2, which contains the methods of the enemy. The goal of the Playbook is to streamline the tools, methods and procedures that the adversary uses in a structured format that can be shared with others. The MITER ATT & CK infrastructure provides names, descriptions and links to examples of how opponents use tactics during an operation, as well as methods used by the adversary to achieve them.
For blueteam
Cyber Analytics Repository (CAR) and CAR Exploration Tool (CARET), Unfetter
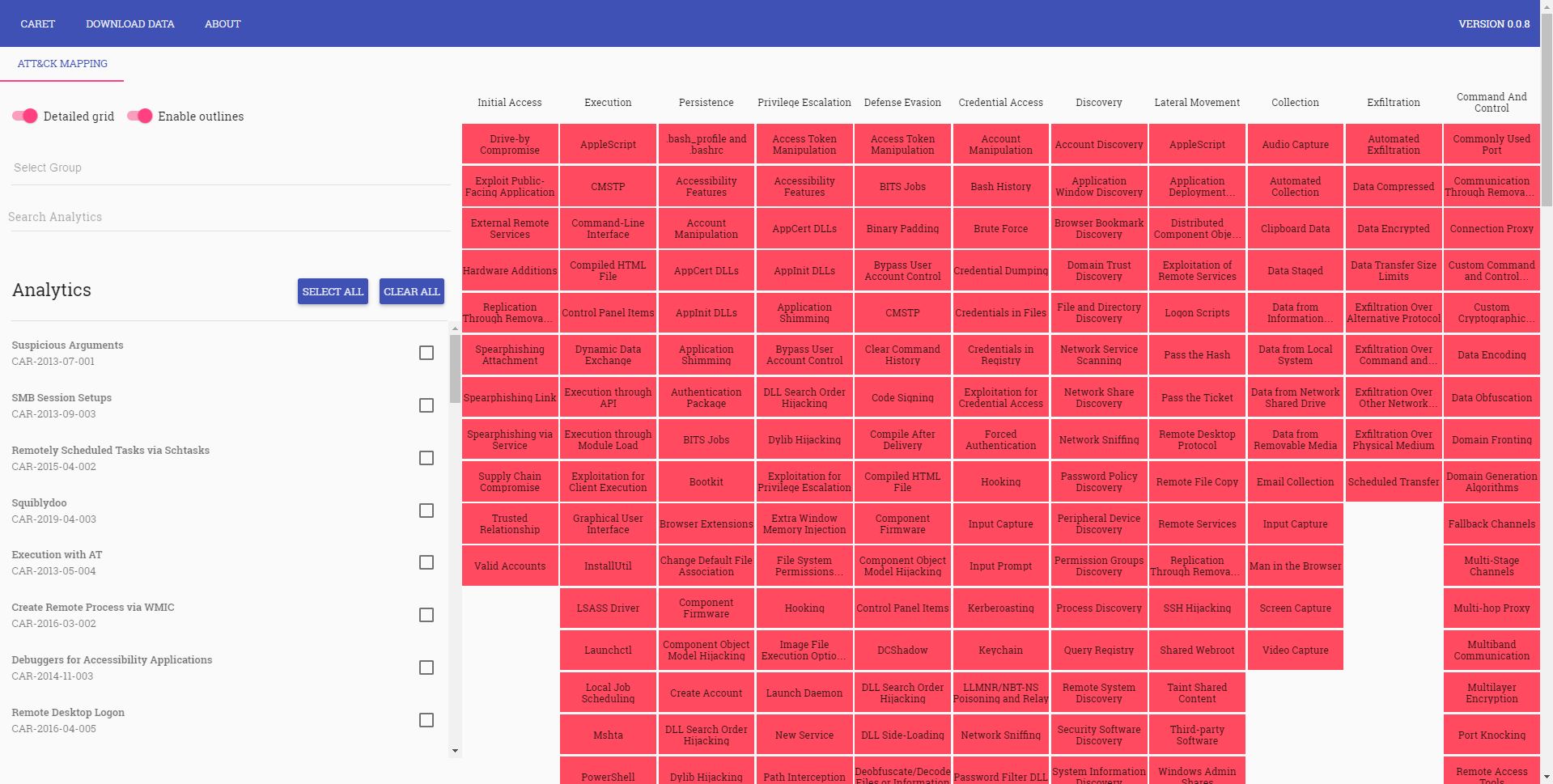
→ Project page Unfetter
→ Unfetter project page on github
→ CAR Project Page
→ CARET project page
The organization MITER decided not to dwell on the ATT & CK matrix alone and develop the idea further: this is how the registry of methods for detecting the behavior of violators based on the ATT & CK Cyber Analytics Repository was created. For convenience, they added a GUI to it - this is the CAR Exploration Tool (CARET). But even this was not enough, therefore, the project Unfetter was created together with the US National Security Agency. This project extends CARET to help cybersecurity professionals identify and analyze security gaps. Unfetter has 2 projects:
- Unfetter Discover allows network security analysts and network engineers to create and share sophisticated Cyber Threat Intelligence (CTI) data among their peers using ATT & CK data from MITER in STIX format.
- Unfetter Analytic allows you to compare analytics with the ATT & CK methods you need to detect.
CASCADE
→ Project Page
This is a MITRE research project that aims to automate much of the work of BlueTeam to determine the extent and severity of suspicious network behavior using host data. The CASCADE server prototype can handle user authentication, perform data analytics stored in Splunk or ElasticSearch, generate alerts. Alerts trigger a recursive investigation process when several subsequent requests collect related events, which include parent and child processes (process trees), network connections, and file activity. The server automatically generates a graph of these events, showing the relationship between them, and marks the graph with information from the ATT & CK matrix.
Atomic Threat Coverage

→ Project Page
It is a tool that allows you to automatically generate analytics designed to combat threats based on ATT & CK. With it, you can create and maintain your own analytical repository, import analytics from other projects (such as Sigma, Atomic Red Team, as well as private branches of these projects with your own analytics) and export to readable wiki pages on two platforms:
- Atlassian Confluence Pages
- Own auto-generated wiki pages
Essentially allows you to make your internal information portal for detecting and responding to attacks.
ATT & CK Python Client
→ Project Page
Python script to access the contents of the ATT & CK matrix in STIX format via a publicly available TAXII server. This project uses the cti-python-stix2 and cti-taxii-client Python libraries and classes developed by MITER. The main goal of the project is to provide an easy way to access and interact with new ATT & CK data.
For RedTeam
CALDERA
→ Project Page
CALDERA is an automated system for emulating the actions of intruders, built on the MITER ATT & CK platform. Its main purpose is to test endpoint security solutions and assess the state of network security. According to the terms of Gartner, this system can be attributed to the breach and attack simulation (BAS) products. CALDERA uses the ATT & CK model to identify and replicate enemy behavior, as if there was a real invasion. This will avoid the routine work and will give more time and resources to solve complex problems.
The recent update of the system has changed its structure: if earlier it consisted of a server, an agent and an executable file for emulating an adversary, now the plugin architecture is used. They connect new features and behavior to the base system. Now CALDERA comes with several predefined patterns of enemy behavior using the Stockpile plugin, but adding your own is easy enough.
Atomic Red Team

→ Project Page
→ Project page on github
→ Red Canary blog page
It is perhaps the most popular project related to the ATT & CK matrix. Red Canary has created a library of simple tests associated with the MITER ATT & CK Framework. These are small, easily portable tests for detecting attacks, each test is designed to be compared with a specific tactic. Tests are defined in a structured format with the expectation of their use by automation environments, which gives defenders an effective way to immediately begin testing their defense against a wide range of attacks.
ATT & CK-Tools
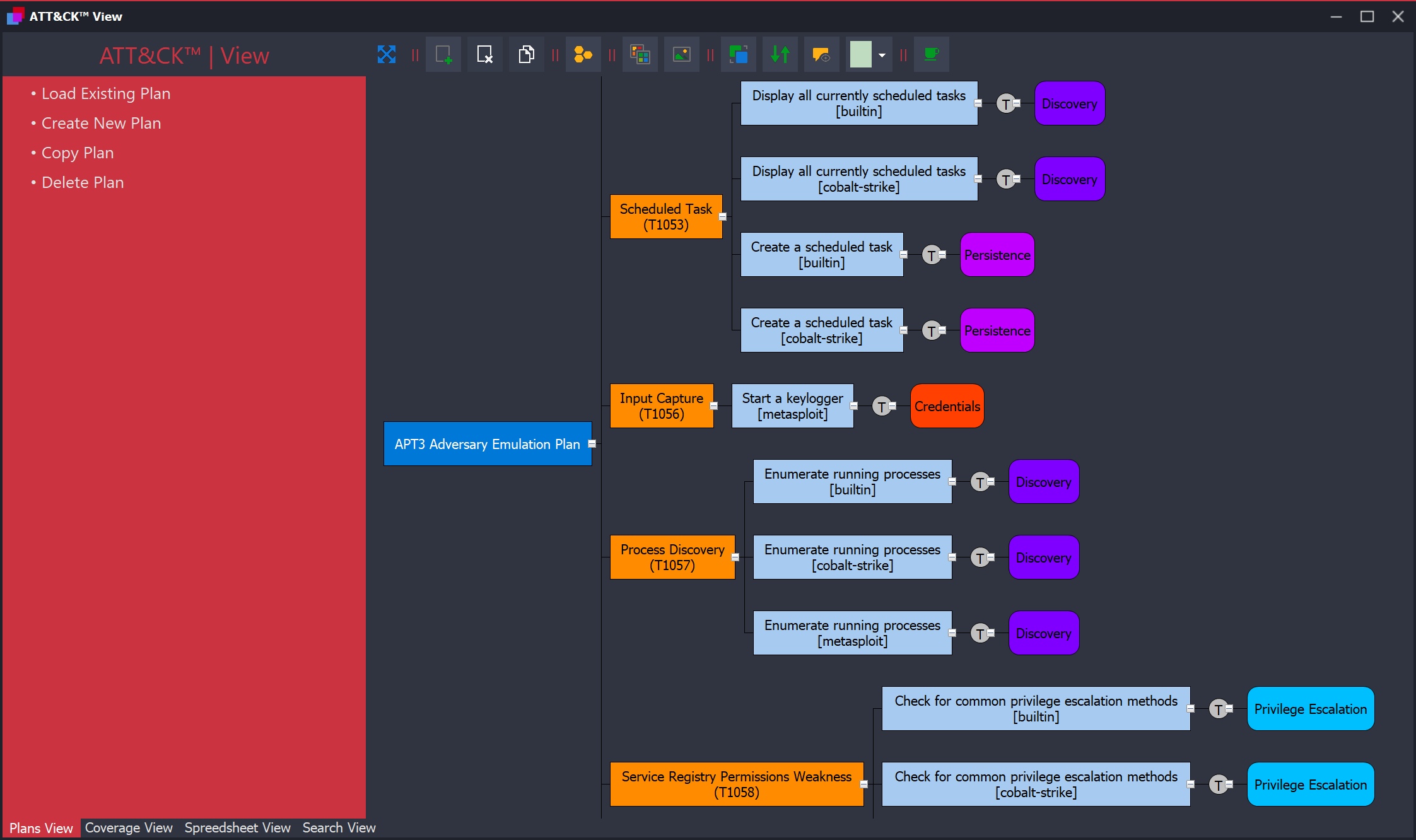
→ Project Page
The repository contains the following:
- ATT & CK View: an adversary emulation planning tool;
- ATT & CK Data Model: relational data model.
View is designed to assist advocates in developing enemy emulation plans based on the ATT & CK structure. As a visual example, there is a complete enemy emulation plan for APT3, developed by MITER. This will help to get started with the project faster.
The main task of the Data Model is to simplify the integration of ATT & CK into new projects. The database is based on SQLite for simplicity and portability, examples of queries to it can be found on the project page.
Purple Team ATT & CK Automation
→ Project Page
A project of the Praetorian company, which implements tactics, techniques and methods from the MITRE ATT & CK matrix as post-modules of the Metasploit Framework. The project is designed to automatically emulate enemy tactics.
Red Team Automation (RTA)

→ Project Page
RTA is a set of 38 scripts and supporting executable files that attempt to perform malicious activity in accordance with the methods of the ATT & CK matrix. At the moment, RTA provides coverage for 50 tactics. Where possible, the RTA attempts to perform the malicious activity described by the scripts; in other cases, it will emulate it.
EDR-Testing-Script
→ Project Page
This repository contains a simple script for testing EDR solutions based on Miter ATT & CK / LOLBAS / Invoke-CradleCrafter platforms. In fact, it is difficult to verify how many different malicious attacks are correctly identified and prevented by the EDR. For this purpose, this script was created, run it and watch what messages come to the EDR console. Most of the tests will simply execute calc.exe, but they can be easily modified (for example, try downloading and running Mimikatz). This script only works on Windows and should work with most EDR solutions.
The project is now in its infancy.
Splunk apps
Splunk is a system for storing and analyzing logs; has a web interface and the ability to create panels (dashboards) - its own Splunk application.
Threat hunting
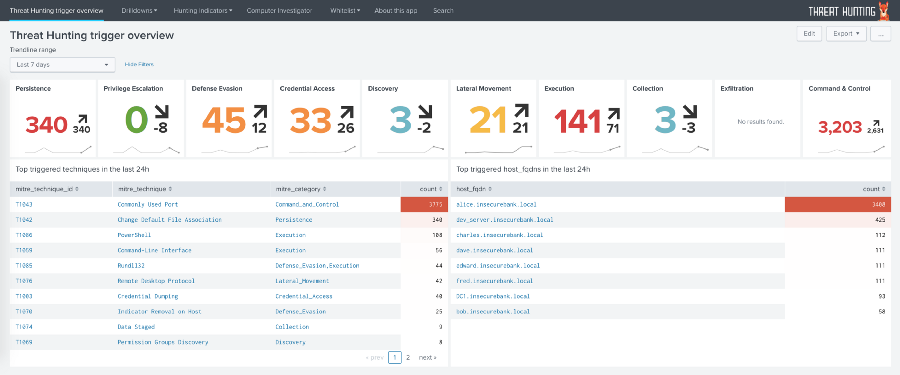
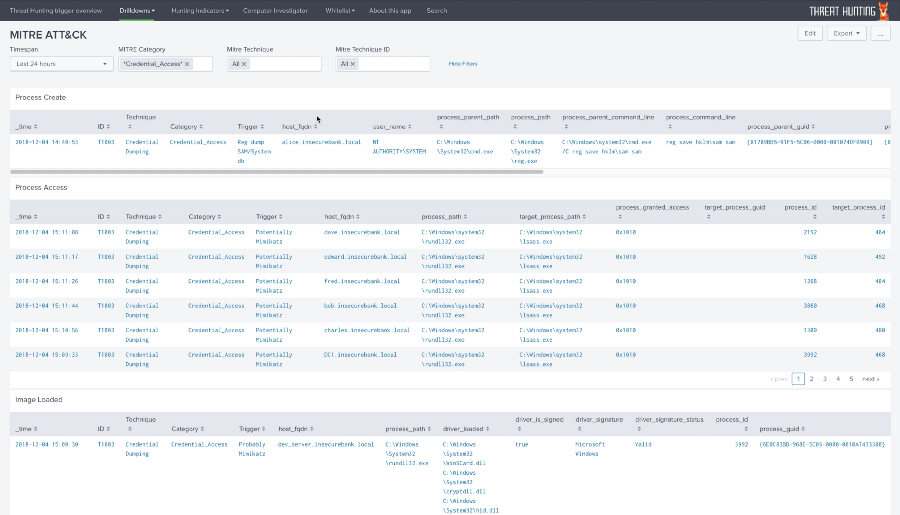
→ Project Page
ThreatHunting is an application for Splunk, created to monitor threats according to the ATT & CK matrix. The application is based on Sysmon data — a free, powerful, host-level trace tool that uses a device driver and a service that runs in the background and loads very early in the boot process. This service also allows you to customize what will be registered. By opening the ThreatHunting application, you will be taken to the overview page with a count of all the triggers for each ATT & CK category in the last 24 hours, and you will also see the technicians with the highest number of positives and the most vulnerable hosts. The application allows you to track events related to ATT & CK, build an event tree based on the data and collect a report. For more information, please refer to the author's blog .
DarkFalcon, InfernoAuger
→ Project page DarkFalcon
→ InfernoAuger Project Page
DarkFalcon is a dashboard system that helps to work with the ATT & CK Framework in your Splunk. There is also an updated version of InfernoAuger - reassembled DarkFalcon, which can automate many components in the FireDrill application and send reports to Splunk. FireDrill provides a library of customizable attacks that can help determine if your protection systems can stop or detect them. Scenarios from this library are placed in sets of customized tests (“assessments”), with which the InfernoAuger modules already interact. Currently there are five modules:
- Main - a module that can create or update a test suite based on the configuration file of the main assembly;
- Detection - the module puts the evaluation results in Splunk for further correlation or analysis;
- Status - checks the status of the current or previous test suite run and provides basic statistics on the results;
- Scenarios - retrieves a list of all MITER ATT & CK scripts in FireDrill and displays information about them;
- Update - checks for the presence of new MITRE ATT & CK scripts since its previous launch and sends an email with those found.
miscellanea
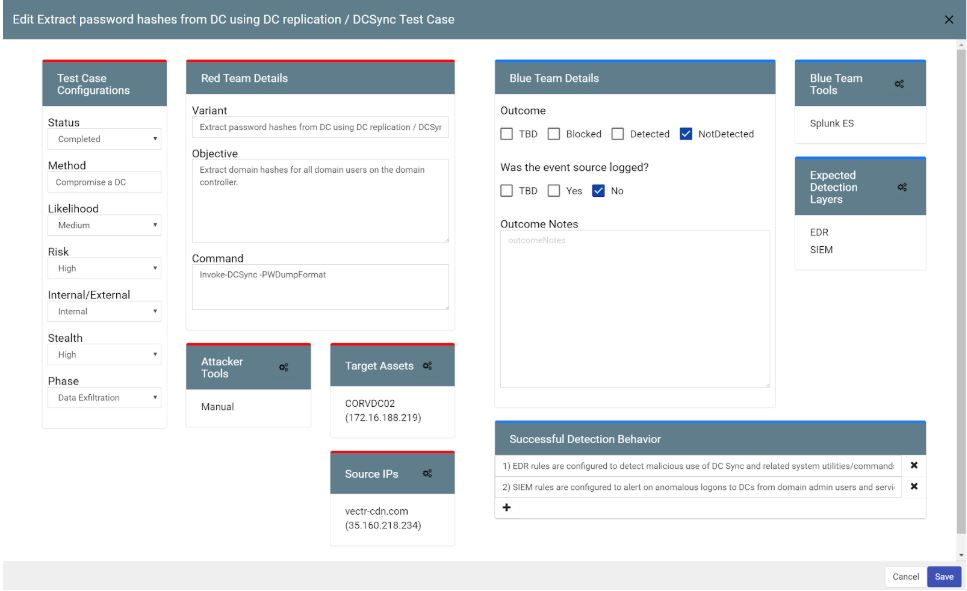
VECTR

→ Project page on github
→ Project Page
This is a centralized dashboard that makes it easy to track RedTeam and BlueTeam testing activities to measure the detection and prevention of attacks under various scenarios, according to data from the MITER ATT & CK matrix. It has including the following features:
- Tracking testing in real time;
- Measuring the progress of tests performed;
- Centralize RedTeam methods and BlueTeam features;
- Add custom test scripts;
- Create detailed test reports.
VECTR documents RedTeam tasks and tools, BlueTeam first and second detection levels, successful detection criteria and test results. Based on the results obtained, recommendations are provided on the overall performance and specific configurations of the toolkits that can be used to further improve the detection and response capabilities.
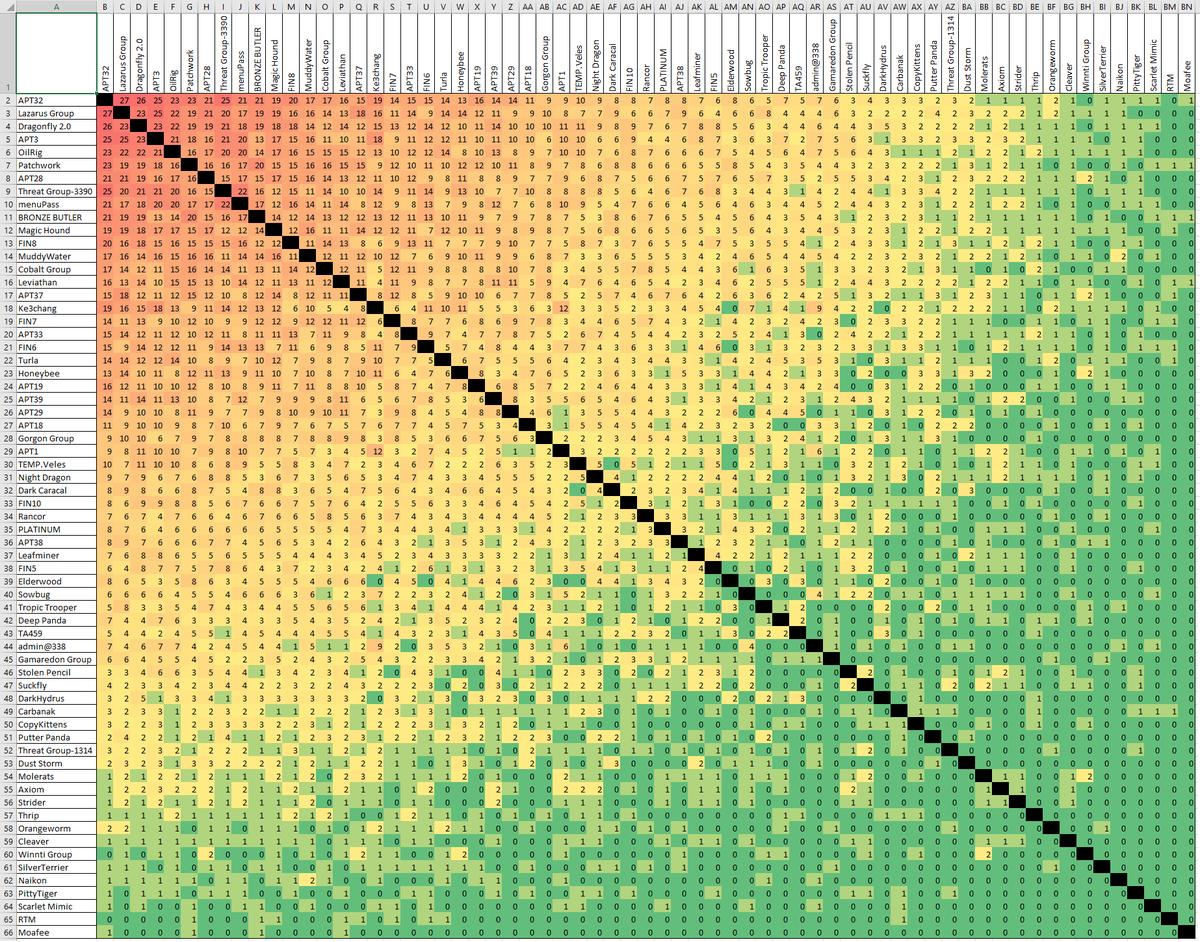
ATT-CK_Analysis
→ Project Page
Scientific and analytical repository containing data analysis from MITER ATT & CK. Independent analysts are looking for answers to a number of questions, for example:
- Are there previously unknown connections between groups that use a large proportion of methods?
- Is the number of methods used by each group a reasonable indicator of how advanced the capabilities of these groups are?
- If it is possible to establish some hierarchy of possibilities, either directly from a dataset or from external sources, is there evidence that certain groups avoid (and not just do not use) certain methods?
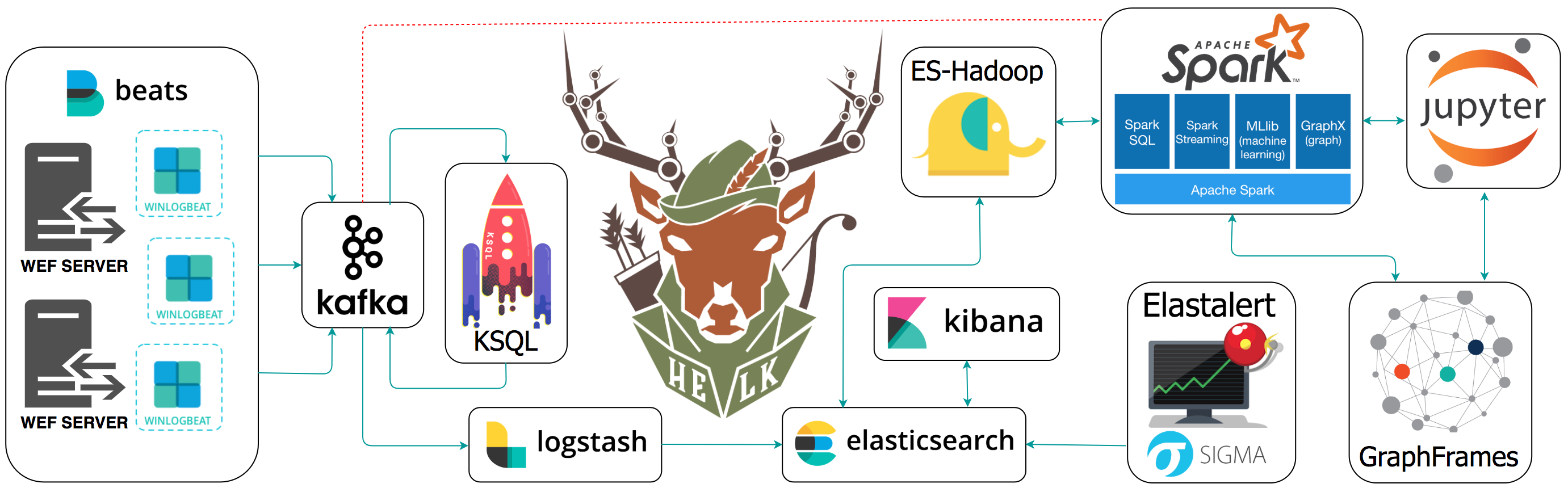
The Hunting ELK (HELK)
→ Project Page
New project Hunting ELK (Elasticsearch, Logstash, Kibana). It is an ecosystem consisting of several open source platforms working together with the main goal of extending the threat detection capabilities of the Elastic ELK stack. Analytical search capabilities provided by the introduction of technology Spark & Graphframes. This is one of the first publicly available assemblies, allowing for free use of data processing functions in the ELK stack. In addition, Jupyter Notebook is integrated into the project for prototyping using big data and / or machine learning. This stack provides a full-text search engine, mixed with visualizations, graphical relational queries and advanced analytics. The project is at the development stage, the code and functionality will change. In the near future we will add dashboards with data from ATT & CK. More information about the project can be found in the author's blog .
Conclusion
The number of projects actively using the MITRE ATT & CK matrix continues to grow. It should be noted that this is a good knowledge base for analysts, a fresh look at the model of information security threats. However, some researchers have noted some drawbacks of the matrix. For example, there are cases of a very vague description of techniques, which makes it difficult to work with them.
The main thing you should not forget: this matrix is built on the basis of successful attacks. Those. By and large, this is a historical background of what techniques and methods were used. Undoubtedly, this is a good knowledge base, convenient in operation, but still it will never fully describe all possible enemy vehicles.
Source: https://habr.com/ru/post/460097/
All Articles