Interoperability of Cisco Solutions at GosSOPKOY and FinCERT
The last note about our Cisco Threat Response Threat Search Platform led me to get a few questions about how to integrate CTR with state services GosSOPKA and FinCERT? And so I decided to write another small note and show how you can get the most out of the indicators of compromise sent to you by the FSB and the Central Bank. In fact, there is nothing supernatural and difficult in such integration - our regulators use machine-readable and standardized indicators of compromise all over the world (I'm afraid to imagine what will happen if hashes for malicious samples are sent out according to GOST R 34.11-2012, not MD5 / SHA1 / SHA256), but do not yet provide an API to automate working with them. In any case, they are not so difficult to use in Cisco Threat Response. In order not to take a screenshot of this procedure, but to show it in dynamics, I recorded a small video that demonstrates on a real example with an attack on the vulnerable RDP protocol how easy it is to organize the interaction of GOSEPKA with Cisco security solutions.
Exactly the same procedure can be done with any other Threat Intelligence source - BI.ZONE, Kaspersky Lab, Group-IB, Anomali, Cisco Talos, etc. Here is a small animated video about how this is done with US-CERT.
')
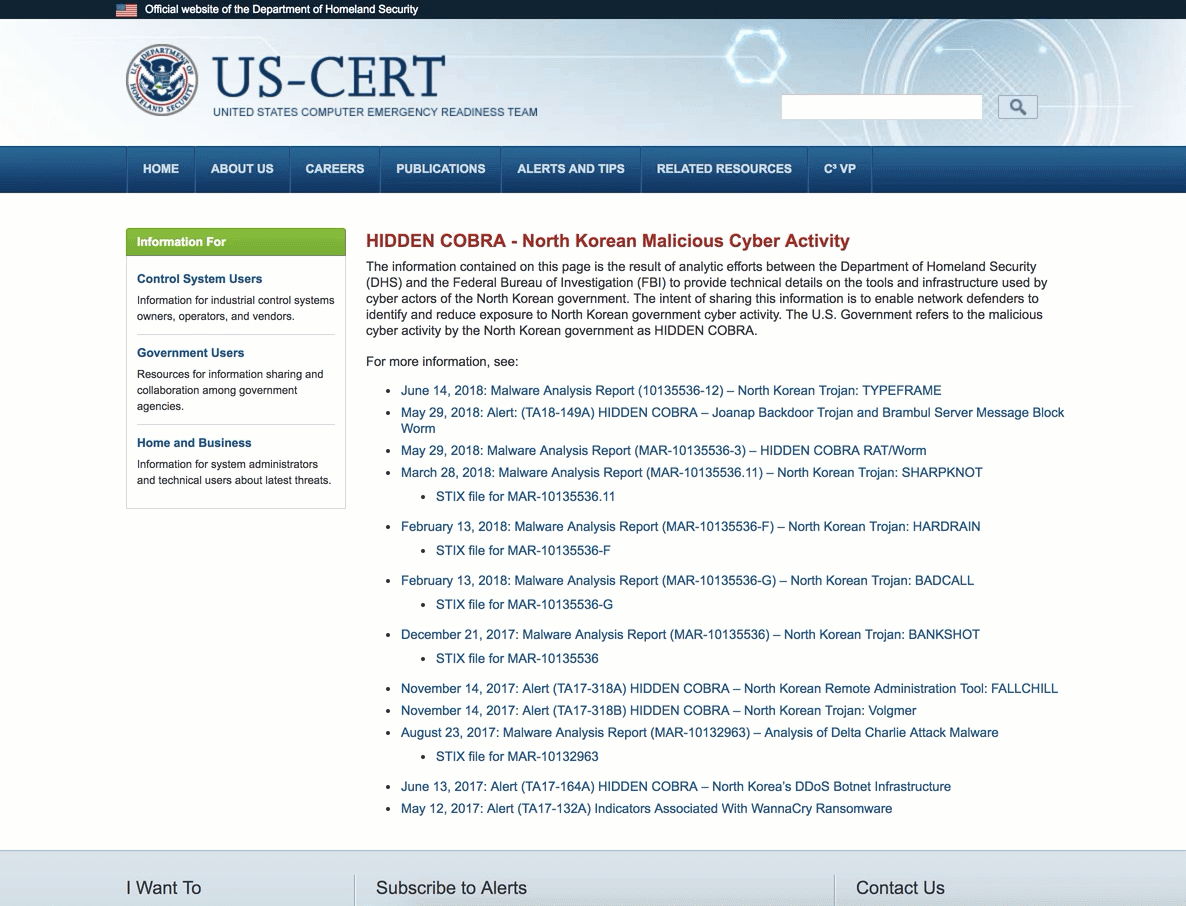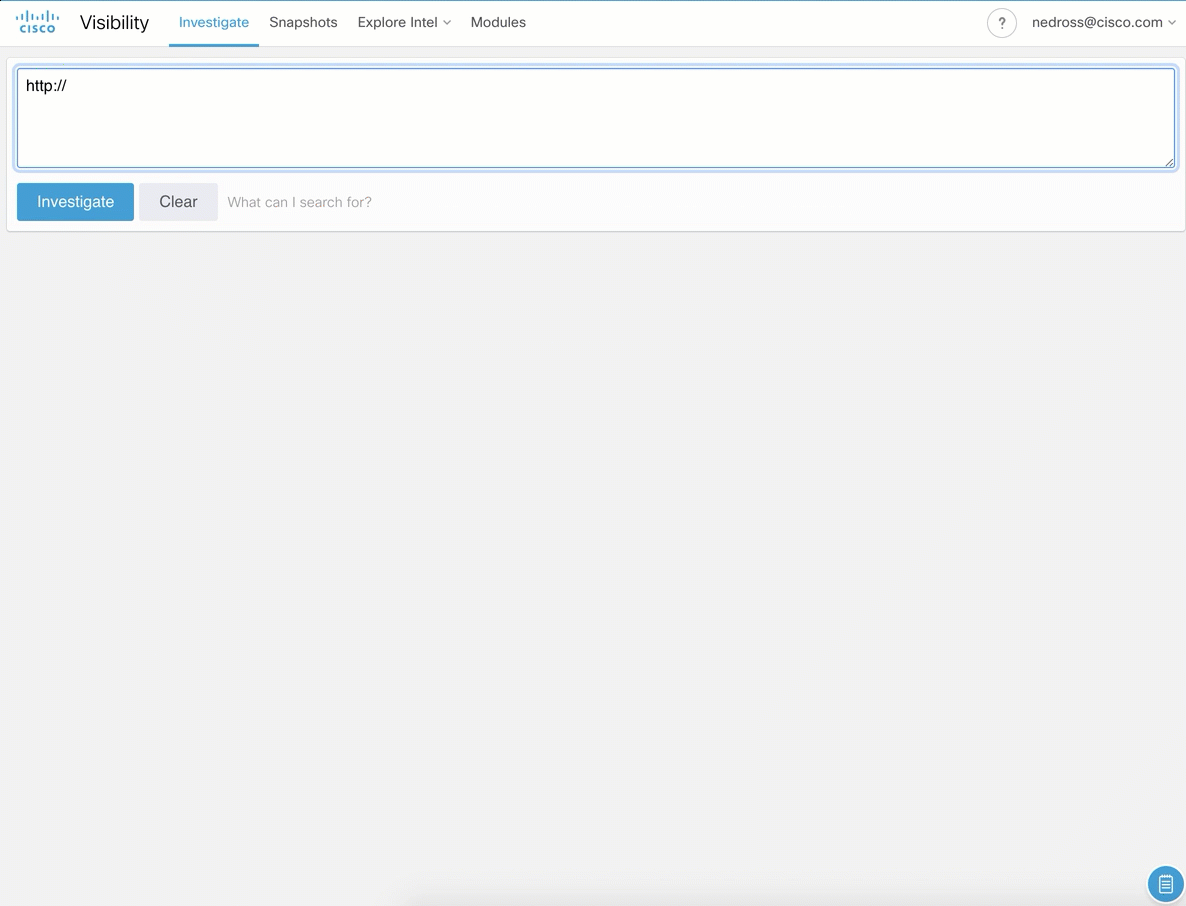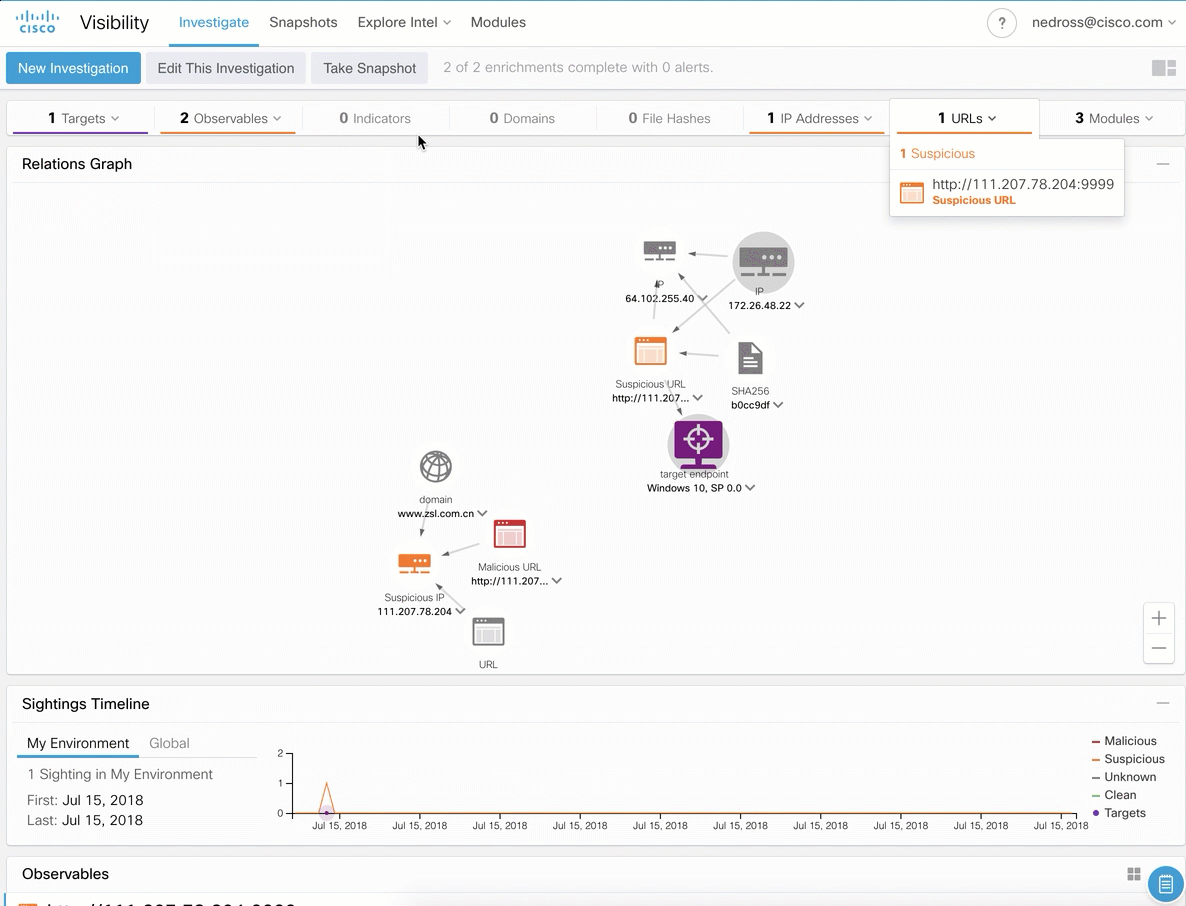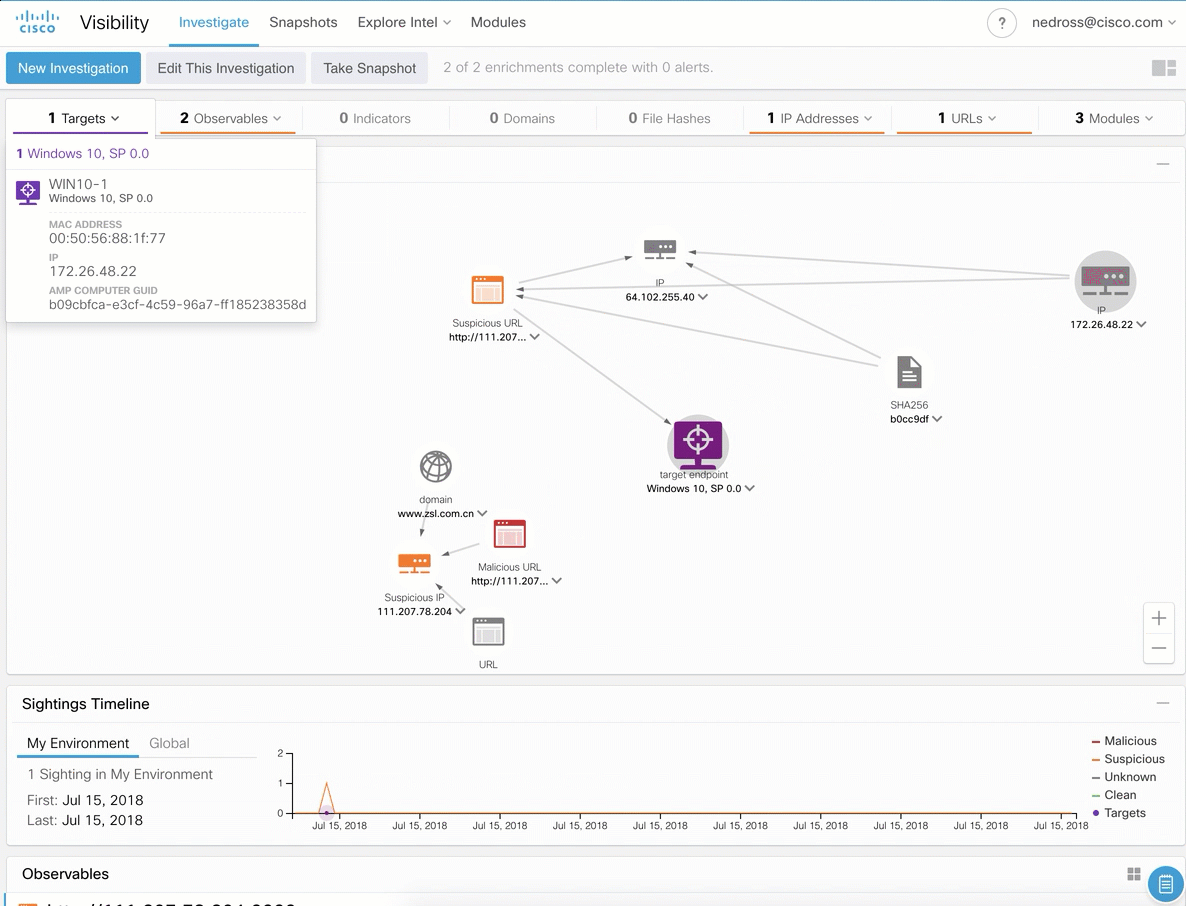
After investigating and identifying traces of unauthorized activity in our network, we are faced with the task of its operational blocking, for which we need to make the appropriate rules in the means of protection working at the nodes, at the borders, in the clouds. Cisco Threat Response can do that too.
But how profitable is it for us to use Cisco Threat Response to investigate incidents? Isn't it easier to use the same solutions that CTR works with - AMP for Endpoints, E-mail Security Appliance, Cisco Firepower, etc., but without CTR? Why do we need another additional system? I tried to conduct an investigation procedure on each of these decisions and received interesting figures that speak for themselves.
For AMP for Endpoints, the CTR-like investigation procedure takes at least 30 seconds. During this time, I can create the policy I need and put the indicators of compromise I need in it, and then start their search in the results of the Cisco AMP4E.
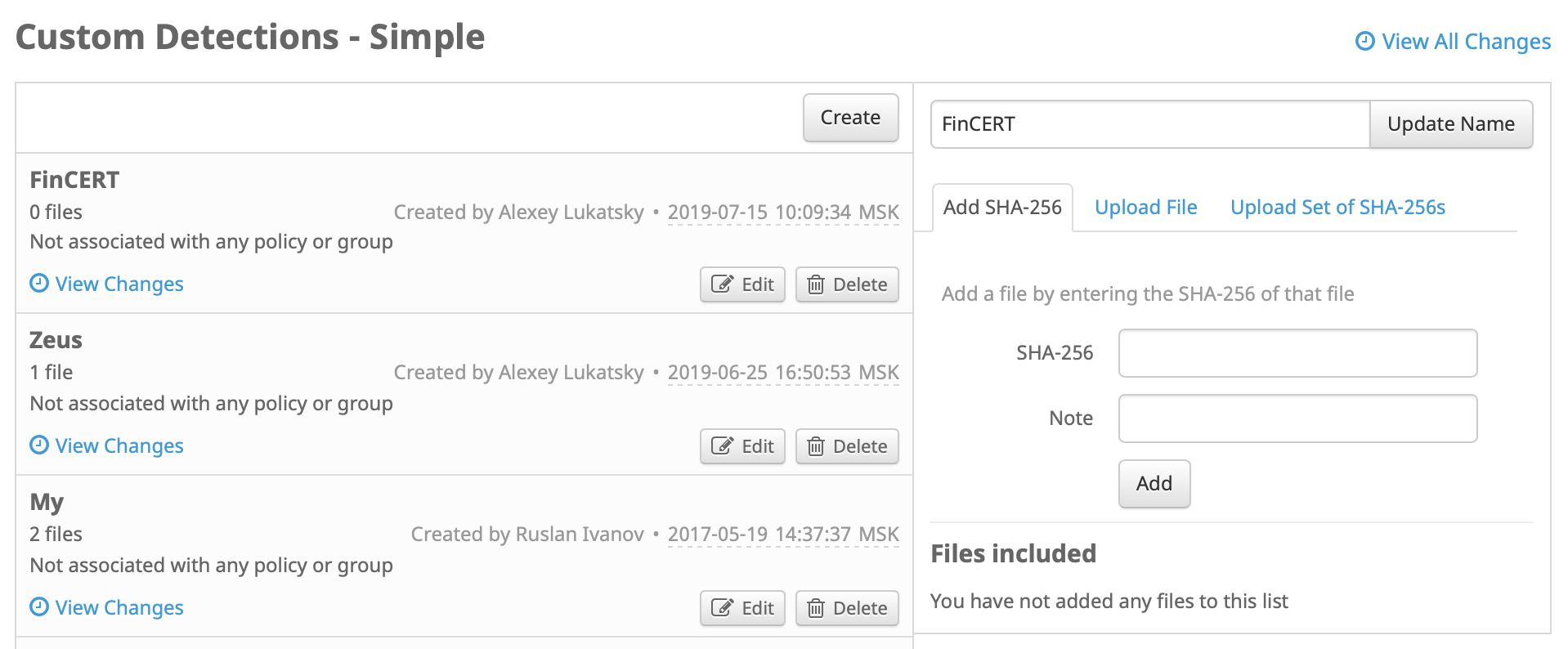
In fact, it will take even a little more time, since it depends on the number of compromise indicators that I need to set in the management console interface (or I need to pre-prepare the file with indicators, which I just load into the system).

In the case of the Cisco Firepowe NGIPS, the same procedure takes at least 40 seconds (depending on the number of compromise indicators I’m looking for).
Finally, in the case of Cisco E-mail Security, a recently integrated with CTR solution, it takes at least 11 seconds to find the occurrence of indicators of compromise in email messages through the Cisco SMA (Security Management Appliance) for at least 11 seconds. investment

and not less than 18 seconds, if I indicate the source of indicators of compromise, whence the data will be loaded automatically.

In general, for each solution it turns out not so much, but if I conduct a comprehensive investigation at once in several products and on different types of indicators, then I will need at least 120 seconds. If you watch the video again, you will see that in the case of using Cisco Threat Respone, the time to investigate will only take 10 seconds. And this time is almost independent of the number of required indicators. Twelve times gain and no hassle with preparing indicators of compromise for uploading to the system - just copy everything we need into the clipboard (or into the browser's Casebook plugin) and paste it into the CTR. So if you are faced with the task of promptly investigating incidents, then the free Cisco Threat Respone allows you to solve this more than effectively.
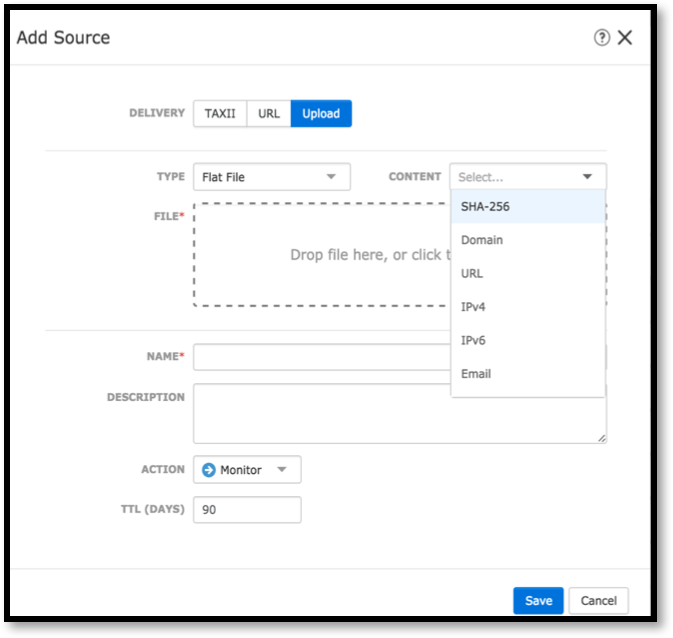
This is just one example of integrating Cisco solutions with government Threat Intelligence systems. In fact, there are more. For example, we can automate not only the incident investigation process, but also the automatic blocking of those artifacts that we receive from GosSIPKI or FinCERT - it is enough to use the APIs that are, for example, in Cisco AMP for Endpoints or Cisco Firepower. However, it is necessary to do this (automatically block) with caution.
Exactly the same procedure can be done with any other Threat Intelligence source - BI.ZONE, Kaspersky Lab, Group-IB, Anomali, Cisco Talos, etc. Here is a small animated video about how this is done with US-CERT.

')
After investigating and identifying traces of unauthorized activity in our network, we are faced with the task of its operational blocking, for which we need to make the appropriate rules in the means of protection working at the nodes, at the borders, in the clouds. Cisco Threat Response can do that too.
But how profitable is it for us to use Cisco Threat Response to investigate incidents? Isn't it easier to use the same solutions that CTR works with - AMP for Endpoints, E-mail Security Appliance, Cisco Firepower, etc., but without CTR? Why do we need another additional system? I tried to conduct an investigation procedure on each of these decisions and received interesting figures that speak for themselves.
For AMP for Endpoints, the CTR-like investigation procedure takes at least 30 seconds. During this time, I can create the policy I need and put the indicators of compromise I need in it, and then start their search in the results of the Cisco AMP4E.

In fact, it will take even a little more time, since it depends on the number of compromise indicators that I need to set in the management console interface (or I need to pre-prepare the file with indicators, which I just load into the system).

In the case of the Cisco Firepowe NGIPS, the same procedure takes at least 40 seconds (depending on the number of compromise indicators I’m looking for).

Finally, in the case of Cisco E-mail Security, a recently integrated with CTR solution, it takes at least 11 seconds to find the occurrence of indicators of compromise in email messages through the Cisco SMA (Security Management Appliance) for at least 11 seconds. investment

and not less than 18 seconds, if I indicate the source of indicators of compromise, whence the data will be loaded automatically.

In general, for each solution it turns out not so much, but if I conduct a comprehensive investigation at once in several products and on different types of indicators, then I will need at least 120 seconds. If you watch the video again, you will see that in the case of using Cisco Threat Respone, the time to investigate will only take 10 seconds. And this time is almost independent of the number of required indicators. Twelve times gain and no hassle with preparing indicators of compromise for uploading to the system - just copy everything we need into the clipboard (or into the browser's Casebook plugin) and paste it into the CTR. So if you are faced with the task of promptly investigating incidents, then the free Cisco Threat Respone allows you to solve this more than effectively.
This is just one example of integrating Cisco solutions with government Threat Intelligence systems. In fact, there are more. For example, we can automate not only the incident investigation process, but also the automatic blocking of those artifacts that we receive from GosSIPKI or FinCERT - it is enough to use the APIs that are, for example, in Cisco AMP for Endpoints or Cisco Firepower. However, it is necessary to do this (automatically block) with caution.
Source: https://habr.com/ru/post/460052/
All Articles