Solving a task with pwnable.kr 02 - collision. Hash collision

In this article, we will recall the colises in the hash functions, and solve the second task from the site pwnable.kr .
Organizational information
Especially for those who want to learn something new and develop in any of the areas of information and computer security, I will write and talk about the following categories:
')
In addition, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, pentesting and writing exploits.
So that you can learn about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of i & kb. I will also personally consider your personal requests, questions, suggestions and recommendations and answer all .
All information is presented solely for educational purposes. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using the knowledge and methods obtained as a result of studying this document.
')
- PWN;
- cryptography (crypto);
- network technologies (Network);
- reverse (Reverse Engineering);
- steganography (Stegano);
- search and exploitation of WEB-vulnerabilities.
In addition, I will share my experience in computer forensics, analysis of malware and firmware, attacks on wireless networks and local area networks, pentesting and writing exploits.
So that you can learn about new articles, software and other information, I created a channel in Telegram and a group to discuss any issues in the field of i & kb. I will also personally consider your personal requests, questions, suggestions and recommendations and answer all .
All information is presented solely for educational purposes. The author of this document does not bear any responsibility for any damage caused to anyone as a result of using the knowledge and methods obtained as a result of studying this document.
Hash Collisions
A hash function collision is such a pair of x and y blocks, the result of the hash function of hash () from which results in the same block z .
hash (x) = hash (y) = z
Collisions are possible absolutely for any hash function, since the set of inputs is much higher than the number of outputs of the hash function.
Therefore, the persistence of the hash function is determined by three characteristics:
- irreversibility - the inability to hash to recover the message;
- resistance to collisions of the first kind - for one message it is impossible to find a second message that will give the same hash as the first;
- Resistance to collisions of the second kind - it is impossible to pick up such a pair of posts, the hash of which will be the same.
Solution to the collision job
We click on the second icon with the signature collision, and we are told that we need to connect via SSH with the guest password.
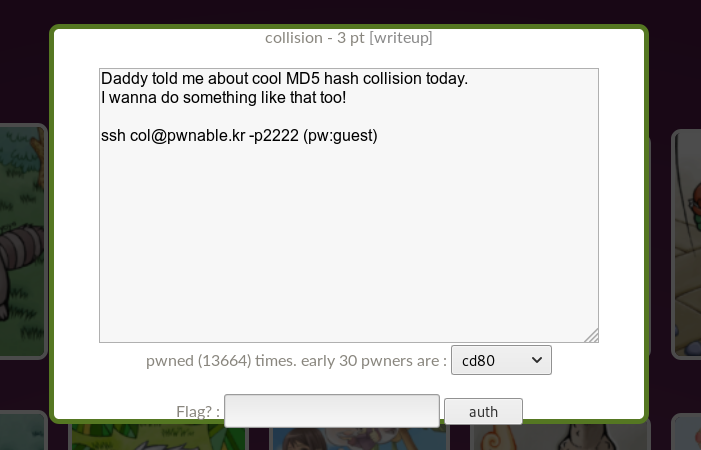
When connected, we see the appropriate banner.
Let's find out what files are on the server, as well as what rights we have.
ls -l 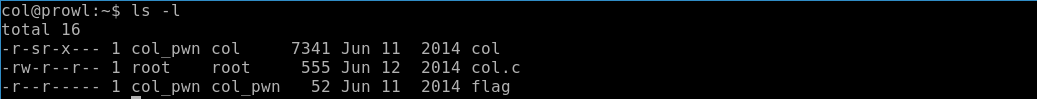
Thus, we can read the source code of the program, since there is a right to read for everyone, and execute the col program with the owner's rights (the sticky bit is set). Let's review the outcome code.
From the code it follows that the program takes as a parameter a string of 20 characters, passes it to a function that calculates the hash and compares it with the reference value.
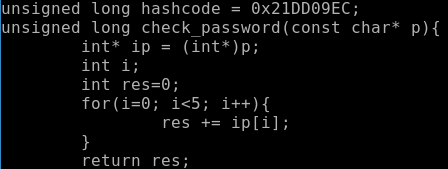
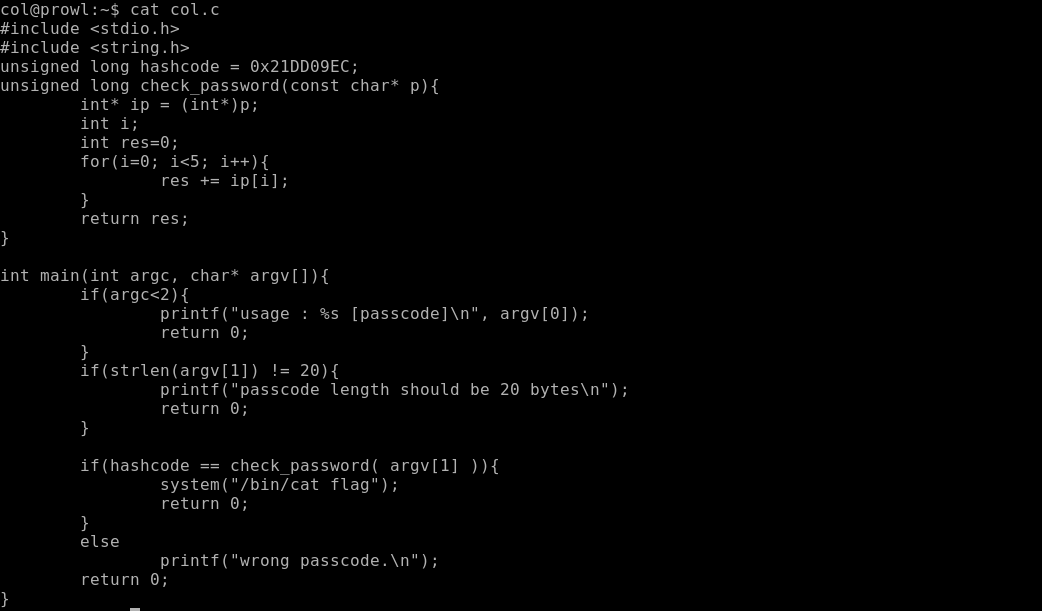
Inside the function, our string is divided into 5 blocks of 4 bytes each, which are converted into numbers, after which these numbers are added together. Thus, we need 5 numbers, which together will give 0x21dd09ec. Satisfy the condition: 0xd1d905e8 and 0x01010101.
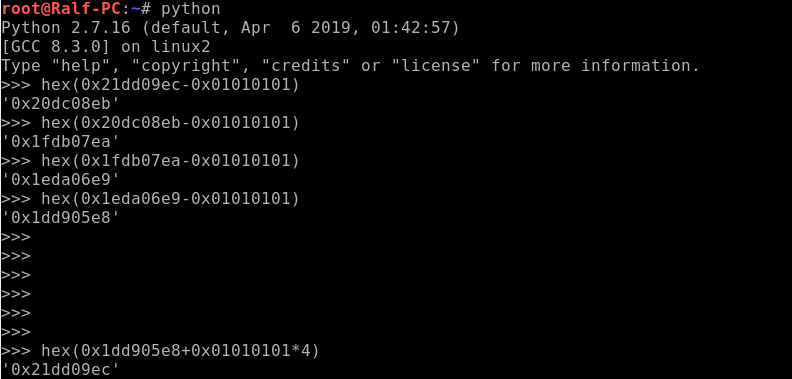
Now you need to pass unprintable characters to the command line as a parameter for the program. To do this, use the bash syntax and the python interpreter. It is important to note that when in memory of a computer these numbers will be stored in the reverse order, therefore we will turn them over.
./col $(python - “print('\x01\x01\x01\x01'*4 + '\xe8\x05\xd9\x1d')”) 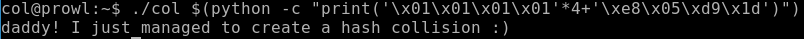
As a result, we get three points.
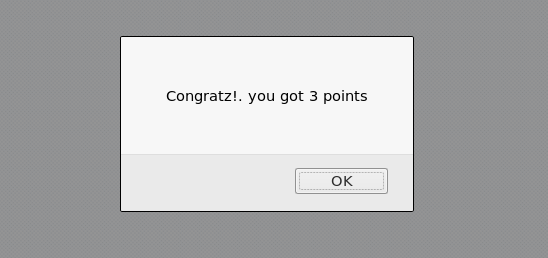
Now we have considered a very simple example of a collision, and in the next article we will solve the third task and analyze such vulnerabilities as buffer overflow in the stack. See you in the next articles.
Source: https://habr.com/ru/post/459866/
All Articles